WannaCry: guidelines
Following the WannaCry (WCry, WanaCrypt, WanaCrypt0r, Wana DeCrypt0r, etc.) mass cyberattack launched on May 12, 2017, Positive Technologies has been inundated with requests for advice asking how to detect and counter the threat.
We decided to create a list of recommendations to help combat this malware. This document does not contain a complete and detailed description of the WannaCry virus, since we expect new modifications to appear over the coming week(s) with other indicators of compromise.
At least three different versions of WannaCry are currently known to exist. Given the modular structure of the virus, Positive Technologies expects new modifications to emerge shortly. Therefore, the propagation of the virus in the corporate network must be pre-empted as a matter of urgency.
Computers running versions of the Windows operating system from XP/2003 up to and including 10/2016, that have not been updated with the MS17-010 update, are vulnerable to WannaCry.
Our basic recommendations will help counter an attack at all stages:
- Guidelines for preventing an infection
- Guidelines for detecting an infection
- Guidelines for localizing and neutralizing an infection
Guidelines for preventing an infection
Important! On May 12–14 copies of the WannaCry virus spread through a vulnerability in Windows SMB Server (TCP port 445), and not only internally, but externally at the penetration stage.
To guard against infection, you should carry out all five tips listed below. They can be performed in parallel, but if time is short, we recommend implementing them in the order listed.
- Block all external connections to TCP port 445 in the outer perimeter. It is recommended to use a gateway firewall (GF) on the network boundary. If there are numerous external subnets (for example, the infrastructure is distributed nationwide with multiple Internet access points) and it is difficult to take stock of the perimeter, you can contact Positive Technologies for help taking an inventory of external services available via the Internet (email us at: abc@ptsecurity.com). We require only a list of dedicated networks from the operator and consent to perform a scan.
- Update all antivirus databases on all network nodes. Ensure that the AV behavioral analysis component is enabled for servers and workstations.
- Identify all vulnerable nodes within the network. You can use one of these methods:
a. Vulnerability scanner.For MaxPatrol 8 users, detailed guidelines on how to detect vulnerable nodes on the network and create a corresponding report are given in the Appendices:
• Appendix 1.Creating a report on nodes with the vulnerability CVE-2017-0145
• Appendix 2. Detecting the vulnerability CVE-2017-0145 in Audit mode
Additionally, Positive Technologies has released a special update (build 8.25.5.25482), which allows MaxPatrol 8 users to detect the vulnerability CVE-2017-0145 in lightweight Pentest mode. Detailed instructions are provided in Appendix 3. Scanning for the vulnerability CVE-2017-0145 EternalBlue in Pentest mode.
b. SCCM, WSUS иor other patch management and inventory system. A report must be created checking whether the 4013389 (MS17-010) update or a newer version is installed. A full list of KB numbers for verification depending on the operating system is available at: https://technet.microsoft.com/en-us/library/security/ms17-010.aspx. The latest updates include all the previous ones, so it is sufficient to check if just the latest update is installed.
c. Local check. To check for updates locally, use the command:
> wmic qfe get HotfixId | findstr KB_for_OS.
For example, for Windows 10 the latest security update, as of today [16 May 2017] is KB4019472 (includes the MS17-010 patch):

- Immediately install the MS17-010 update on all vulnerable nodes, including Windows XP and Windows Server 2003. Updates for different operating systems are available at: https://blogs.technet.microsoft.com/msrc/2017/05/12/customer-guidance-for-wannacrypt-attacks/.
- After installing the update, repeat the scan for vulnerable nodes across the entire infrastructure (point 3).
Important! If there are too many vulnerable nodes, and it is not possible to install the update quickly:
a. Disable SMBv1 on all nodes where it is not a critical function. It can be disabled manually or using SCCM/GPO. See here for details:https://support.microsoft.com/en-us/help/2696547/how-to-enable-and-disable-smbv1,-smbv2,-and-smbv3-in-windows-vista,-windows-server-2008,-windows-7,-windows-server-2008-r2,-windows-8,-and-windows-server-2012
b. For nodes on which SMBv1 cannot be disabled, it is recommended to set up a dedicated closed segment. Connections to this segment via the SMB protocol should be allowed only from nodes with the security update and invulnerable to attack.
Guidelines for detecting an infection
The spread of the virus can be detected in the following ways:
- Multiple connections to different nodes on port 445. The task can be handled by IDS/IPS and SIEM systems. Activity can also be observed through a firewall.
- Multiple connections to the TOR network on ports 9001 and 9003. Before encrypting files, all modifications of the virus have so far attempted to install TOR and then connect to the C&C servers. The browser’s basic TOR settings have been used, allowing the virus to be detected via TCP ports 9001 and 9003 with a high degree of probability.
- Monitoring of "kill-switch domain" DNS queries.Analysis of DNS server logs and/or proxy server. Samples without a "kill-switch domain" have already appeared, but in the event of older virus samples spreading, queries addressed to these domains will serve as a good indicator. As of today, the following domains are known:
www[.]iuqerfsodp9ifjaposdfjhgosurijfaewrwergwea[.]com
www[.]ifferfsodp9ifjaposdfjhgosurijfaewrwergwea[.]com
www[.]ayylmaoTJHSSTasdfasdfasdfasdfasdfasdfasdf[.]com - Monitoring of antivirus verdicts. There are already hundreds of names of verdicts from various AV products. The most common are:
a. Kaspersky:
• Exploit.Win32/64.ShadowBrokers.*
• Trojan-Ransom.Win32.Gen.*
• Trojan-Ransom.Win32.Scatter.*
• Trojan-Ransom.Win32.Wanna.*
• Trojan-Ransom.Win32.Zapchast.*
• MEM:Trojan.Win64.EquationDrug.*
b. ESET NOD32 – Win32/Filecoder.WannaCryptor.*, Win32/Exploit.CVE-2017-0147.*.
c. Dr.Web – predominantly the signature Trojan.Encoder.11432, also BACKDOOR.Trojan and Trojan.Encoder.10609
If questions arise when implementing recommendations 1–4, MaxPatrol SIEM users can contact Positive Technologies directly via their dedicated manager or dedicated technical specialist. - Intrusion detection system (IDS). For products that accept signatures in Snort format, the following rules can be used:
alert udp $HOME_NET any -> any 53 (msg:"ET TROJAN Possible WannaCry? DNS Lookup"; content:"|01 00 00 01 00 00 00 00 00 00|"; depth:10; offset:2; content:"|03|www|29|iuqerfsodp9ifjaposdfjhgosurijfaewrwergwea|03|com|00|"; nocase; distance:0; fast_pattern; reference:url,www.bleepingcomputer.com/news/security/telefonica-tells-employees-to-shut-down-computers-amid-massive-ransomware-outbreak/; classtype:trojan-activity; sid:2024291; rev:1;)
alert smb any any -> $HOME_NET any (msg:"ET EXPLOIT Possible ETERNALBLUE MS17-010 Heap Spray"; flow:to_server,established; content:"|ff|SMB|33 00 00 00 00 18 07 c0 00 00 00 00 00 00 00 00 00 00 00 00 00 08 ff fe 00 08|"; offset:4; depth:30; fast_pattern:10,20; content:"|00 09 00 00 00 10|"; distance:1; within:6; content:"|00 00 00 00 00 00 00 10|"; within:8; content:"|00 00 00 10|"; distance:4; within:4; pcre:"/^[a-zA-Z0-9+/]{1000,}/R"; threshold: type threshold, track by_src, count 5, seconds 1; classtype:trojan-activity; sid:2024217; rev:2;)
alert smb any any -> $HOME_NET any (msg:"ET EXPLOIT Possible ETERNALBLUE MS17-010 Echo Request (set)"; flow:to_server,established; content:"|00 00 00 31 ff|SMB|2b 00 00 00 00 18 07 c0|"; depth:16; fast_pattern; content:"|4a 6c 4a 6d 49 68 43 6c 42 73 72 00|"; distance:0; flowbits:set,ETPRO.ETERNALBLUE; flowbits:noalert; classtype:trojan-activity; sid:2024220; rev:1;)
alert smb $HOME_NET any -> any any (msg:"ET EXPLOIT Possible ETERNALBLUE MS17-010 Echo Response"; flow:from_server,established; content:"|00 00 00 31 ff|SMB|2b 00 00 00 00 98 07 c0|"; depth:16; fast_pattern; content:"|4a 6c 4a 6d 49 68 43 6c 42 73 72 00|"; distance:0; flowbits:isset,ETPRO.ETERNALBLUE; classtype:trojan-activity; sid:2024218; rev:1;) - Disconnect the infected nodes from the network by pulling out the network cable or disconnecting the network interface or port on the switch.
- Block inter-segment traffic on ports 139 and 445 inside the network, apart from essential non-infected nodes inside the network, using firewalls and access control lists (ACLs) on the switches.
- Block incoming requests to ports 139 and 445 on workstations and servers that do not require the SMB service, using Windows Firewall or an AV component firewall.
- Ensure that the domains
www[.]iuqerfsodp9ifjaposdfjhgosurijfaewrwergwea[.]com
www[.]ifferfsodp9ifjaposdfjhgosurijfaewrwergwea[.]com
are accessible from the local network. Being able to connect to these domains prevents infection by earlier versions of the virus. Only the availability of the address on port 80 (HTTP) is verified, so it is sufficient to redirect requests to the specified domains for any internal web server. This can be configured on the internal DNS server. - For encrypted computers, if files cannot be restored, we recommend that you save the encrypted files on an external drive or keep the computer’s hard drive for at least six months just in case a data decryption tool appears later. In this case, the computer must be switched off immediately.
- 6. To neutralize the virus, you must stop the execution of the service mssecsvc2.0 with a description of Microsoft Security Center (2.0) Service (the service created by the virus is needed for further propagation through the network), as well as the service that runs tasksche.exe. Typically, the service has the name of a random directory marked as hidden or system, beginning with 8–15 characters [a–z] and ending with three figures created in one of three locations: %SystemDrive%\ProgramData\, %SystemDrive%\Intel\, %Temp%\. Next, update the AV databases, run a full scan of the infected node and implement the recommendations in the Guidelines for preventing an infection section.
- Go to the Reports tab.
- Add a new report.
- Give the report a name and define the type as SIEM integration
- In the Task section, select the task created in Step 3.
- Enable filtering using the field CVE = CVE-2017-0145; this will allow only vulnerable nodes to be selected.
- Save the report and run it.
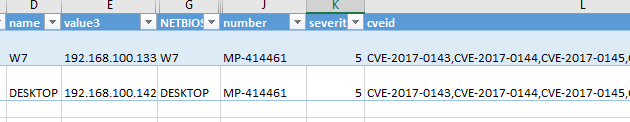
- The report is generated as an XML file. Save it and open in Microsoft Excel, for instance.
- Export the list of vulnerable nodes (NETBIOS columns or value3).
- Disable all scanning modes except Audit.
- In the Scan settings in Audit mode, disable the use of LDAP, SSH, Telnet, MSSL, Oracle, Lotus Notes RPC, SAP DIAG, SAP RFC.
- Go to Scan.
- Select Profiles.
- Create a profile on the basis of Fast Pentest, and give the profile a name.
- In the Scan settings, leave only port 445/tcp in the list of ports.
- Also in the settings, completely disable UDP scanning.
- Save the profile, and go to Tasks.
- Create a task that uses the profile, and perform a scan.
- If the node is vulnerable, this will be shown in the scan results.
- Go to report creation (Appendix 1)
Guidelines for localizing and neutralizing an infection
When infected nodes are detected:
APPENDIX No. 1. Preparing a report on nodes with the vulnerability CVE -2017-0145 EternalBlue
Information about the vulnerability CVE-2017-0145 (Windows SMB Remote Code Execution Vulnerability) is available in the MaxPatrol 8 knowledge base, starting with build 8.25.5.25279 (if an earlier build is used, an update is required). The vulnerability is detected when scanning the node in Audit mode. If scan results for build 8.25.5.25279 are already available (and the systems were not updated after scanning), you only need to prepare a report to obtain a list of vulnerable nodes. The most convenient report is in table view containing only the nodes with this vulnerability. You can export it to another system and install the update.
To create a report:

APPENDIX No. 2. Detecting the vulnerability CVE-2017-0145 EternalBlue in Audit mode
Scanning in Audit mode requires an account with administrator rights on the network nodes. A reduced profile can be used to speed up the scanning process:


If the computer is vulnerable, the entry "Remote code execution associated with Windows SMB"appears in the scan results.
APPENDIX No. 3. Scanning for the vulnerability CVE-2017-0145 EternalBlue in Pentest mode
To perform a quicker and simpler scan for all nodes vulnerable to CVE-2017-0145, the update 8.25.5.25482 was released for detecting the vulnerability in Pentest mode. Instructions for creating a lightweight Pentest profile:
0. Check that you are using version 8.25.5.25482 or higher; if not, update to the required version.




