The Dark Web is often perceived as a world without rules, but in reality the industry operates according to the principles of the legal market. For example, high competition encourages sellers to constantly improve products and services, build trusting relationships with customers, and strengthen their business positions. In the analytical review, we will analyze the economics of threats, methods of competition, as well as the future and trends of shadow sites.
Dmitry Streltsov
Analyst, Research Group of PT Cyber Analytics
About this study
This study analyzes the dark web market from 2023 to Q3 2024, focusing on cybercriminal interests, popular topics, trends, and cybersecurity forecasts. We examined the costs of tools and services, initial expenses for attacks, and key aspects of the shadow market, including its ecosystem, participant motivations, transaction principles, competition, and client attraction strategies.
We analyzed 40 sources, including major dark web platforms (forums, marketplaces) and Telegram channels in various languages covering a wide range of topics. We reviewed over 20,000 messages related to malware, vulnerabilities, exploits, corporate network access, infrastructure, and cybercriminal services (hacks, traffic redirection, malware distribution, carding, and DDoS attacks).
This study targets information security professionals, threat intelligence analysts, as well as organizations and individuals concerned about the current cybercrime landscape.
Summary
- Cybercriminal business looks a lot like the legitimate one: maintaining reputation, marketing, competition strategies (including aggressive ones), bug bounties, and employee support.
- The most popular type of malware on the dark web is infostealer (19%).
- The priciest type of malware is ransomware, with an average cost of $7,500.
- A third of the exploits for sale are zero-day vulnerabilities1.
- The cost of exploits can reach up to several million dollars.
- In (62%) of all cases, access to compromised resources is priced up to $1,000.
- The highest number of access sale ads is related to the service sector (20%).
- Almost half of the listings (49%) concern hacks of resources.
- The net profit from a successful cyberattack can be five times the cost of organizing it.
Diving into the dark web
The darknet is a hidden part of the internet, inaccessible through regular search engines. The dark web is not regulated by the government, allowing users to remain anonymous through special encryption and routing methods, which makes it attractive to cybercriminals. Anonymity means that users can evade responsibility for their actions, which further fosters illegal activities.
As technology advances and the open internet faces increasing scrutiny, alternative spaces like the dark web attract a growing number of users. This hidden corner of the internet draws a diverse crowd, from hardened criminals to the simply curious, each attracted by different aspects of the network.
Broadly speaking, dark web users fall into two categories: sellers and buyers. Sellers are key players, meeting the high demand for illegal goods and services. Like their counterparts in the legitimate business world, they focus on retaining existing customers and attracting new ones to maximize profits. Buyers, often motivated by financial gain, create the demand that fuels this underground marketplace. Both groups are considered cybercriminals.
Cybercrime encompasses a range of illegal activities conducted using digital technologies, including phishing and malware attacks. The goals of these attacks vary widely, from financial profit to disrupting systems for personal or political reasons. Cybercriminals themselves are diverse, ranging from hacktivists and novice attackers to sophisticated Advanced Persistent Threat (APT) groups, each with their own unique methods and motivations.
Hacktivists
Hacktivists are individuals who use cyberattacks to express their political, ideological, or social views and draw attention to specific issues. Driven by motives beyond personal gain, they aim to influence public opinion or political processes. Hacktivists often target governments and organizations they perceive as engaging in harmful or unethical practices. Leveraging both dark web resources and more accessible platforms like Telegram, they organize attacks on government systems, leak stolen data, and disseminate information intended to discredit their targets. Hacktivists also offer training courses on techniques such as DDoS attacks and website defacement—altering website content for political protest or other purposes.
Novice cybercriminals
Inexperienced hackers often rely on pre-built tools to carry out attacks. Lacking the deep technical knowledge of seasoned hackers, they use readily available malicious software found on dark web marketplaces. This allows them to launch cyberattacks with minimal effort. On the dark web, unskilled hackers can buy or download malicious tools to attack websites, networks, and other resources. The dark web also serves as a venue for them to boast about their exploits and connect with more experienced cybercriminals, seeking recognition and validation. For many in this group, cyberattacks are driven more by a desire for entertainment than by an intent to cause harm.
APT groups
Advanced Persistent Threat (APT) groups are highly organized and well-funded hacker collectives that conduct long-term, targeted cyberattacks. Often linked to or sponsored by governments, these groups possess advanced technologies and resources to achieve their objectives. APT groups can remain undetected within a victim's network for extended periods, sometimes months or even years. Their goals typically include intelligence gathering and espionage, disrupting critical infrastructure, and inflicting damage on corporate systems. Notorious examples of APT groups include Calypso and Bronze Union. On the dark web, APT groups purchase access to corporate networks and other services (discussed below in more details).
Ransomware groups
Ransomware gangs are cybercriminal groups specializing in attacks using ransomware—malicious software that encrypts victims' data and demands a ransom payment for its decryption and restoration. The dark web is an important platform for ransomware operators, where they publish the names of their victims and stolen data, seek affiliates, and sell ransomware as a service (RaaS, Ransomware-as-a-service model), a business model where they lease their ransomware tools to other criminals.
Malware developers
Malware developers are essential players in the dark web ecosystem, creating the software for cyberattacks. Their goal is to develop programs that achieve commercial success within the underground market. These developers build their reputations on underground forums and within hacker communities to generate demand for their products.
Other stakeholders
While often associated with criminal activity, the dark web also attracts users with non-illegal intentions, including cybersecurity professionals, students, and researchers. Each group has distinct goals, but they often involve collecting and analyzing data. Driven by curiosity rather than criminal intent, some visit dark web forums to explore cybersecurity and hacking, expanding their knowledge or simply observing discussions and debates.
The dark web, like any marketplace for goods and services, represents a lucrative, though illegal, business. Cybercriminals thrive in this environment, where a robust market for illicit goods and services fuels both demand and supply. Profit-making on the dark web extend beyond direct sales to include affiliate programs, scams, custom malware development, and the sale of instructions and consultations for carrying out cyberattacks.
A Chainalysis study highlights the financial resilience of this underground economy. Despite a significant drop in darknet cryptocurrency revenues after a 2021 peak, a recovery began in 2023. Even after the shutdown of Hydra, the major dark web marketplace, in 2022, other illegal platforms saw their revenues increase to nearly two billion U.S. dollars in 2023—a growth of almost 25% over the previous year. This growth is attributed to new players filling the void left by Hydra, aggressive marketing strategies, and the integration of anonymous cryptocurrency payment systems like the Universal Anonymous Payment System (UAPS).
Facilitating these transactions are payment processors offering white-label services to dark web markets, ensuring seamless financial operations for their criminal clients.

In July 2024, TRM Labs, a cryptocurrency analysis and security firm, reported that the three largest Russian-speaking dark web marketplaces processed $1.4 billion in transactions during 2023, dwarfing the $100 million total transacted on Western dark web markets during the same period.

The dark web constitutes a unique ecosystem where users exchange information, buy and sell illegal tools, and even coordinate cyberattacks. This interconnected network includes forums for discussing new attack methods, marketplaces for illicit goods and services, and secure messaging platforms like Telegram. Hidden from view, these resources form the backbone of the darknet economy.
Dark web forums serve as hubs for a range of illicit activities. Users communicate, exchange information, and trade illegal tools and services, including stolen payment card data, malware, hacking tools, and access to compromised accounts. They also discuss current events, share attack methods, and offer tips on staying anonymous online. These forums are hidden from regular search engines and require specialized software to access. However, discussions about hacking can also be found on the open internet (clearnet).

Dark web forums often organize content into categories like "web application vulnerabilities" and "malware" to facilitate navigation.

Dark web forums generate revenue by taking commissions on transactions. They use automated guarantee systems for smaller transactions and offer human intermediaries, or "live guarantors," for larger, higher-risk deals. Another significant revenue source is advertising. Through advertising, attackers can more effectively promote their services, for example, using cryptomixers and background checks. The cost of such ads can start at $50 per month.

The forum also generates revenue through premium memberships. These upgrades unlock various bonuses, including access to all hidden content, priority placement for commercial topics, and the ability to sell products directly on the marketplace. For a hefty $2,000 annual fee, users can even extract data from the forum without fear of being blocked.
Subscription prices vary from forum to forum, starting at $10 per month.

To keep out casuals, some hacking forums only allow access to those with paid subscriptions or a solid reputation on reputable platforms. This results in a more focused community of like-minded hackers.

Underground forums, like any online community, have a structured hierarchy to ensure smooth operation. Crucial to the forum's operation are administrators, guarantors, and arbitrators. At the top sit the administrators, the forum owners responsible for everything from technical maintenance to fostering user trust and maintaining the platform's popularity. They delegate day-to-day management to moderators, their trusted allies who enforce rules, moderate content, and keep an eye out for scams. Moderators are also active participants in discussions, often sharing tips on anonymity and security.
The lifeblood of these forums are the buyers and sellers. Sellers, often requiring verification through a deposit system, provide the supply, while buyers—ranging from newcomers to seasoned criminals—drive the demand for illicit goods and services. Beyond these core members, you'll find privileged users who've earned their status through high engagement, a solid reputation, or sometimes simply by paying for an upgrade. This privileged status often grants access to exclusive forum sections. Finally, regular users make up the bulk of the forum's population. They represent the broad audience engaging with the content.

The dark web operates on a unique set of unwritten rules. These regulations govern everything from user interactions to the trade of illicit goods and services. Most dark web forums maintain standard prohibitions against spam, toxic behavior, the spread of malicious links and files (designed to infect other users), and doxing (revealing personal information).
Interestingly, on Russian-speaking forums, malicious activities targeting Russia and CIS countries are prohibited. For example, the seller of the Meduza Stealer malware was banned because the tool was used against Russian organizations.

Dark web marketplaces function much like legitimate e-commerce platforms, offering a digital storefront for vendors selling illicit goods and services like stolen data, malware, and customized hacks. Like their legitimate counterparts, dark web marketplaces profit by taking a commission on each sale. Some marketplaces even require a membership fee for access.

Telegram is essential for cybercriminal markets, facilitating communication, marketing, and transactions. While ads might offer a glimpse of available goods and services, the finer details of agreements are often discussed in private conversations. Messaging apps like Telegram, Tox, Element, and Briar are the preferred channels for these negotiations.
Telegram's popularity among cybercriminals extends beyond simple communication. It's a powerful marketing and distribution platform for malicious services. Sellers create Telegram channels to promote their illicit goods, posting updates, discounts, and special offers. These channels also serve as a direct line to customers, allowing sellers to quickly address service interruptions and gather feedback to refine their offerings. The broad reach of Telegram makes it easy to advertise and attract new clientele. Furthermore, unlike the dark web, accessing Telegram doesn't require specialized software.

Our research on Telegram's cybercriminal market revealed a wide range of illicit services offered on the platform. This growth was fueled by the shutdown of large dark web marketplaces, leading to Telegram becoming a thriving hub for distributing illegal goods.
However, this dynamic is evolving. On September 23, 2024, Telegram's CEO Pavel Durov announced that the messenger would increase moderation and share user data upon government requests. Meanwhile, bad actors on the dark web began exploring alternative communication channels such as Tox, Signal, and Matrix. It's likely that cybercriminals will shift back to forums or develop their own platforms similar to Telegram or existing forums.
While most platforms used by cybercriminals, including forums, marketplaces, and messaging apps like Telegram, adhere to similar general rules, details can vary, especially if the platform is linked to a specific region.
Shadow economy: mirroring the legitimate world
While often perceived as lawless, the dark web economy mirrors many aspects of the legitimate business world. Underground platforms rely on principles familiar to any business, including reputation management, marketing, and customer service. Furthermore, these platforms often employ security measures like bug bounty programs to protect themselves from critical events.
Reputation is key in the underground economy. Facing intense competition and numerous challenges, sellers prioritize building trust to attract and retain customers. A good reputation allows them to charge higher prices and ensures a steady stream of business. This translates to a strong focus on customer service, often including 24/7 support. Increasingly, this support extends to team members as well, with sellers recognizing the importance of both technical support and emotional well-being. Caring for team members becomes a crucial part of the overall success strategy, fostering stronger teams. This evolving business model within the dark web increasingly resembles legitimate corporate structures, where professional skills and employee support are both valued.

Dark web users can leave feedback and suggestions, requesting product updates or improvements. Developers often respond to this feedback, tweaking their offerings to meet customer expectations and boost satisfaction.

Users might also complain about pricing. Negative feedback on price can certainly drive customers away, encouraging them to find cheaper alternatives. However, if developers justify the higher cost, they might successfully position their product as "premium".

Landing pages are crucial for a successful competitive strategy. A well-designed, structured landing page can effectively capture buyer attention and drive purchases.

A user-friendly interface is now essential: a visually appealing, intuitive design minimizes the time users spend learning complex tools, allowing quicker product adoption. A user-friendly interface is also an important way to stand out among competitors. Even with limited features, user-friendly products often gain traction faster than complex tools, particularly among less tech-savvy buyers. Simply put, the easier a product is to use, the more appealing it becomes to customers. However, experienced attackers prioritize functionality and reliability over simplicity.

Holiday promotions are a powerful competitive tactic on the dark web. For example, one dark web forum advertised a Black Friday sale on its Telegram channel, offering half-price subscriptions and account upgrades. This illustrates how cybercriminals readily adapt traditional marketing techniques.

Platforms that streamline cryptocurrency payments and employ bold marketing strategies gain a competitive edge. One darknet market even went so far as to place ads on billboards in Moscow—how the criminals managed to engage an advertising agency remains a mystery, but it demonstrates their willingness to leverage legitimate marketing channels. In another unusual campaign, the LockBit ransomware group offered $1,000 to anyone willing to tattoo their logo on themselves and post a photo online. This audacious move bolstered their image as a powerful player, increasing brand recognition, attracting potential partners, and setting them apart from other ransomware gangs.

The recent rebranding of the now-defunct BlackCat ransomware group provides a compelling example of how cybercriminals pursue brand recognition and notoriety. While rebranding is common among ransomware gangs, this case stands out. In June 2024, a ransomware gang started advertising their services on a dark web forum. In June 2024, gang started advertising their services on a dark web forum using the name and logo of the enigmatic and highly publicized Cicada 3301. From a competitive perspective, appropriating a well-known name offers instant, free advertising, boosts recognition, and potentially lends an air of credibility. This tactic can be particularly effective when recruiting partners, as a prominent name and reputation are highly valued by those aspiring to reach the upper echelons of the cybercriminal world.

Competition on the darknet extends far beyond typical business practices. With profits directly tied to reputation and success, some resort to aggressive, even overtly hostile, tactics. Cyberattacks are a prime example. DDoS attacks, designed to overwhelm servers and disrupt operations, are a common weapon used to erode customer trust in rival platforms.
In this hyper-competitive environment, everyone fights to maintain their position and sabotage the competition. However, such attacks are not always successful. Many underground vendors possess the technical expertise to quickly recover from these attacks, minimizing any lasting damage.
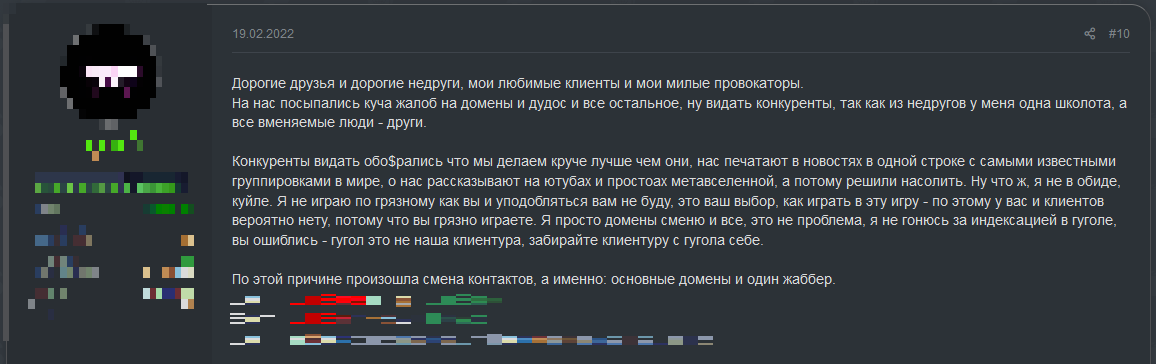
Of course, DDoS attacks are just one tool in the arsenal. Other methods are used to disrupt rivals. For example, in June 2023, a data breach exposed the personal information of 4,000 members of a dark web forum. A competing platform claimed responsibility for the breach on social media. The attackers aimed to damage the forum's reputation within the criminal community. Moreover, identities of the forum's members may be exposed to law enforcement agencies, making it easier for authorities to track them.

The shadow market often mirrors legitimate businesses, and bug bounty programs are no exception. Dark web platforms are implementing their own bug bounty programs, offering payments in cryptocurrency. This helps protect the platforms and user data from external threats, such as attacks from rival criminal groups. The primary goal of these programs is to enhance platform resilience and prevent data leaks or hacks that could lead to incidents like cryptocurrency theft from user accounts.

The prominent ransomware group LockBit launched a bug bounty program in 2022, offering both ethical and unethical hackers rewards for identifying vulnerabilities in their infrastructure. The group was particularly focused on discovering Cross-Site Scripting (XSS) vulnerabilities that could allow unauthorized access to their decryption tool or victims' chat logs. They were also interested in finding bugs in Locker (malware designed to block system access) that might allow victims to recover their files without paying a ransom. Rewards for discovered vulnerabilities ranged from $1,000 to $1,000,000.

Just as in legitimate commerce, fraud is prevalent on the dark web. Criminals deceive each other, sometimes distributing malware disguised as legitimate software (like spyware, discussed in our quarterly research). To minimize risks and ensure some level of deal integrity, cybercriminals frequently rely on guarantor or escrow services.
An escrow service acts as a trusted third party between buyer and seller. It holds the buyer's funds until the buyer confirms receipt of the goods or services, then transfers the money to the seller.
Many forums also use a deposit system, often mandatory, where sellers must deposit funds to demonstrate their good faith. In cases of fraud, this deposit is forfeited to the affected buyer.
The growth of dark web forums has spurred the development of automated escrow systems, which speed up transactions by automating the deposit process.

Most dark web platforms maintain their own escrow services, typically managed by a forum administrator or a reputable user. Guarantors generally receive a commission of around 4% of the transaction value, although this can vary depending on the platform.
When disputes arise, the arbiters step in. Acting as a kind of regulatory body within the platform, arbiters help resolve conflicts between transaction participants, making decisions about fund allocation or compensation. They play a vital role in maintaining trust and stability within shadow markets. To resolve disputes, the affected party must provide evidence, which the arbiter then verifies before issuing a judgment. However, the platform administration retains the authority to make the final decision.

auctions
On dark web marketplaces, prices are either fixed or determined through auctions. Fixed prices are set by the seller and aren't open to negotiation. This is a practical approach for high-volume sales when a criminal needs to sell a product quickly without lengthy negotiations. Auctions allow buyers to bid on items, giving the seller the opportunity to select the most profitable offer. Auctions are often used for selling rare or unique items like zero-day exploits, exclusive data, or access to organizational infrastructure. A seller establishes a starting price and specifies the bidding increments.

Cryptocurrencies, like Bitcoin (BTC) and Monero (XMR), are the dominant payment method on the dark web for several reasons. First, they offer a high degree of anonymity, crucial for users operating in illicit markets. While Bitcoin transactions are recorded on the public blockchain, users can employ cryptomixers (discussed later in the "Laundering cybercrime money" section) or other privacy coins. For example, Monero and a few other cryptocurrencies are designed to obscure transaction details, making it significantly more difficult to trace.
Moreover, the decentralized nature of many cryptocurrencies, free from government control, makes them particularly appealing to dark web users. Cryptocurrencies also provide security and convenience for international transactions. By bypassing traditional banking systems and enabling direct transactions between parties, they reduce the risk of arrest and simplify operations.
The anonymity and lack of control facilitate market expansion, attract new participants, and stimulate further growth. This, in turn, complicates law enforcement efforts, as the anonymity of transactions and the use of mixers make identifying and apprehending criminals extremely challenging.
If cryptocurrency tracking becomes more effective and poses a greater threat to dark web users, they will likely seek new, more obscure payment methods. A potential trend could be the wider adoption of cryptocurrencies like Monero, or the emergence of entirely new cryptocurrencies designed for maximum anonymity. These might incorporate advanced encryption techniques and methods for concealing transaction information.
Another possibility is the increased use of trustless swap technology. This technology allows direct peer-to-peer exchange of cryptocurrencies across different blockchains without relying on centralized exchanges or intermediaries. Smart contracts ensure that the exchange only occurs if all predefined conditions are met; otherwise, the assets are returned to their owners.
Looking further ahead, entirely new payment concepts may emerge, such as decentralized, encrypted communication networks or quantum payment systems offering near-absolute protection from tracking.
Financially motivated attackers often receive ransoms and payments for services in cryptocurrency and need to convert these funds into usable cash. Money laundering on the dark web is the process of transforming illegally obtained cryptocurrency into legitimate assets using various methods and services.
One popular tool is the cryptomixer. Cryptomixers blend a user's cryptocurrency with that of other users, creating a large number of small, obfuscated transactions. This makes it extremely difficult, if not impossible, to trace the final destination of the funds. After using a cryptomixer, criminals frequently convert their assets into privacy-focused cryptocurrencies like Monero. Once the funds are sufficiently obfuscated, they can be exchanged. One dark web forum hosts services that exchange cryptocurrency for fiat currency (such as dollars or euros) or other cryptocurrencies. This stage often involves a "drop" or "money mule"—an individual who transfers or cashes out the illicit funds, typically through their personal bank accounts, in exchange for a percentage of the transaction.

Cybercriminals sometimes employ complex schemes involving multiple decoy wallets to further complicate tracing efforts.
A crucial step is integrating the laundered funds into the legitimate economy. Some criminals establish networks of shell companies, using fabricated contracts and invoices to funnel dark web money into legitimate businesses. Dedicated sections on dark web forums offer turnkey money laundering services, further facilitating this process.

Investing in real estate with cryptocurrency is another method for laundering money. Some websites specialize in real estate investments using virtual currencies.

Many criminals actively seek ways to cash out and legitimize their earnings. They often consult more experienced members of the dark web community or share information about money laundering techniques and strategies.


Online casinos and betting platforms also offer opportunities for money laundering. Cybercriminals deposit funds into these platforms, many of which readily accept cryptocurrency, simplifying the process. The funds can then be withdrawn through one or more casinos to avoid suspicion. Once the funds have passed through the online casino system, criminals can deposit them into bank accounts or cryptocurrency wallets. Some criminals use strategies involving guaranteed-outcome bets. By betting on all possible outcomes of a single event using multiple accounts, they guarantee a win on at least one account. This allows them to withdraw the winnings, disguising them as legitimate gambling proceeds.
Shadow economy
Malware
Malware remains a primary weapon in a hacker's arsenal. By the end of Q3 2024, it was used in 65% of successful attacks on organizations. Cybercriminals use malware for various purposes, from stealing sensitive information to encrypting files for ransom.
Figure 32. Various types of malware advertisements
Among all malware ads we analyzed, more than half (53%) are for sales. This indicates a commercially driven malware market, where developers and hackers monetize their tools.
Purchase requests comprise 41% of these ads, reflecting a strong demand for ready-made solutions. Buyers typically seek proven tools that meet specific needs. For instance, a buyer might require an Android RAT with real-time screen recording capabilities or a stealer capable of extracting information from all current cryptocurrency wallets. Only 1% of ads mention the distribution of malicious tools, possibly indicating an attempt to enhance the author's reputation within the community.
Figure 33. Sales announcements by the type of malware
Figure 34. Malware types by median cost
Some malware categories are more preferred by criminals than others. Infostealers lead the market, accounting for 19% of advertisements. Their popularity might be due to relatively low price, with costs starting at $20, with a median value of $400. A skilled cybercriminal can use the stolen information for a significantly higher profit.
Crypters and obfuscation tools follow closely, representing 17% of the total. These tools, available from as little as $10, help cybercriminals evade antivirus detection, increasing the effectiveness of their attacks.
Loaders round out the top three, comprising 16% of ads. Loaders serve as an initial entry point into a victim's system, bypassing security measures and deploying other malware like stealers or Remote Access Trojans (RATs). According to ANY.RUN, loader detections increased by 49% in Q3 2024. Loader prices typically start at $50, with a median price of $400.
RATs, popular among hackers throughout the first three quarters of 2024, account for 12% of ads. RATs provide covert and persistent control over infected systems, enabling espionage, data theft (passwords, personal information, and business data), and other malicious activities. RAT prices start at $80, with a median price of $1,500.
Malware prices vary considerably depending on the type and functionality. Most malware is sold on a subscription basis (weekly, monthly, quarterly, or annually).
Ransomware is the most expensive type of malware, with a median price of $7,500, reaching as high as $320,000. The prices are so high because most ransomware sale ads offer the source code itself. Ransomware is primarily distributed through affiliate programs (Ransomware-as-a-Service, or RaaS), where participants typically receive 70-90% of the ransom. Joining such a program often requires a substantial fee (from $5,000 to as high as 1 BTC, or approximately $96,000) and a strong reputation on dark web forums.
However, not all cybercriminals, especially newcomers, possess the required funds or reputation. Consequently, these tools and guides are often leaked online.
RaaS: from rookie to cybercriminal
As previously mentioned, ransomware gangs often use manuals within their partner programs. These manuals cover various aspects of ransomware attacks, including infrastructure setup, gaining initial access to an organization, and methods for escalating privileges within a compromised system. These manuals are sometimes sold by criminals as another revenue stream. For example, a LockBit affiliate once listed a guide for sale on a dark web marketplace for $10,000. This manual provided instructions on system compromise and other attack techniques, all based on real-world attacks against companies. In one cited attack against a major organization, the corporate VPN password consisted solely of numbers, and system administrators had left test accounts open.
The leaked materials from the Conti ransomware gang provide another compelling example. In 2021, a disgruntled affiliate leaked training guides and technical manuals used in Conti's partner program onto a dark web forum. Similar to the LockBit partner's guide, these leaked instructions detailed methods for navigating within a victim's network, escalating privileges, and disabling antivirus software. The Conti guide also cataloged attacks exploiting incorrect parameters, known vulnerabilities (such as PrintNightmare, EternalBlue, and Zerologon), and provided advice on which data to target. Furthermore, the manual included a comprehensive guide on using the CobaltStrike tool.

Leaked ransomware builders2 provide another noteworthy example. A builder allows attackers to customize ransomware by modifying parameters like the process name, ransom note filename and text, and the targeted file extensions for encryption. Builders also enable attackers to generate the decryption tool needed to recover the encrypted data.

Although these leaks date back to 2022, the leaked builders are still actively used by cybercriminals and remain of significant interest on the dark web. Our incident investigation reports indicate that LockBit ransomware, often customized using leaked builders, was the most frequently used ransomware in cybercrime attacks (typically involving ransomware, legitimate encryption software, and wipers) with a 37% share. Such ransomware leaks can contribute to the emergence of new Ransomware-as-a-Service (RaaS) operators.

Ransomware builders are readily available on the dark web. Leaked manuals and builders make it easier for people to become cybercriminals and help them learn the ropes. Even experienced hackers use these tools, sometimes to attack government agencies. In those cases, they're often more interested in destroying data and systems than making money.
MalDev community
The dark web isn't just a place to buy ready-made hacking tools. There's a whole community of malware developers3 (called "MalDev") doing much more sophisticated work. They offer custom-built malware, tweaked and refined to a client's exact needs. For example, customers can pay extra to have experienced developers modify or enhance existing malware.
The MalDev community isn't just for experts, though. It also attracts beginners who want to learn the basics of malware development. Just like in the real world, newcomers look for mentors to guide them. They ask for advice on which programming languages, like Python or C++, are best for creating different types of malware.

The community also shares manuals and code examples to help beginners create simple malicious tools like loaders, stealers, or RATs. These resources help less experienced users learn the fundamentals and understand how malware works. Newcomers can learn step-by-step, following the examples of more experienced developers. This constant learning means the overall skill level of malware developers is always improving, and we're likely to see more new faces in this field.

Hackers are increasingly using languages like Rust and Golang (Go), in addition to the more common C++ and others. Golang, in particular, has become popular for creating many different types of malware, including remote access tools, stealers, cryptominers, and botnets. A key advantage of using Go and Rust is that the same code can easily target multiple operating systems like Windows, Linux, and even VMware ESXi. Major ransomware groups like BlackCat, Hive, and RansomHub have noticed this and are starting to use Rust and Go more often. We expect this trend to continue growing because these languages offer malware developers so many advantages.
Vulnerabilities and exploits
Every system vulnerability as a doorway for hackers to break into a network, disrupt services, or steal important data. Hackers develop exploits to take advantage of these weaknesses.
An exploit is a piece of code or a program that leverages software or hardware vulnerabilities to perform malicious actions, such as launching denial-of-service attacks or installing malware.
Both criminals and security researchers look for vulnerabilities. Criminals build exploits to attack, while cybersecurity professionals develop them as proofs of concept (PoCs) to demonstrate system weaknesses.
Figure 41. Ads in the category "Vulnerabilities and exploits"
Seven out of ten ads we analyzed advertised exploits for sale. Nearly a third (27%) of messages discussed purchasing malware, indicating high demand among malicious actors.
Figure 42. Types of exploits available for sale
Figure 43. Exploits by price
Vulnerability and exploit information is highly valuable on the dark web. One-third (32%) of exploits sold are zero-day exploits, sometimes fetching millions of dollars. Buyers often receive detailed instructions on how to exploit such vulnerabilities.

A quarter of the ads (25%) concern known vulnerabilities. Remote Code Execution (RCE) and Local Privilege Escalation (LPE) are among the most dangerous vulnerabilities , appearing in 26% and 12% of ads, respectively.
RCE is a vulnerability that allows attackers to remotely run any code on a victim's system, granting full control. It's frequently used in targeted attacks and to spread ransomware and other malware. In October, an RCE vulnerability was exploited to attack over 22,000 CyberPanel servers with PSAUX ransomware, taking most of them offline.
LPE allows attackers to gain higher-level system privileges, like administrator or root access. This is crucial for taking full control of a compromised system. Attackers often initially gain limited access; exploiting an LPE vulnerability allows them to escalate privileges and advance the attack.
See the trending vulnerability digest on our website.
Corporate access
Selling access to corporate networks is a lucrative business on the dark web, dominated by Initial Access Brokers (IABs). These criminals obtain and sell access to compromised networks. IABs employ various methods, including exploiting software vulnerabilities, phishing emails to steal credentials or deploy malware, and brute-force attacks (using common passwords to hack accounts). In 2023 penetration tests, brute-force techniques were used in 56% of external attacks aimed at gaining LAN access.
Once IABs have the necessary data, they offer their services to ransomware groups and other criminals, including advanced persistent threat (APT) groups. Less experienced hackers might find a vulnerability using a legitimate scanner but be unable to fully exploit it. However, they can still profit by selling this access to more experienced cybercriminals.
Figure 45. Ads in the category "Access"
Most access-related messages are sales offers (72%), while purchase requests make up only 14%. This prevalence of sales ads reflects a growing division of labor on the dark web, with some specializing in gaining access and others in exploiting it. Free access giveaways account for the remaining 13% of ads.
Figure 46. Access by cost
The majority of ads (62%) list prices below $1,000. Cost is often tied to company revenue, resulting in some high-priced offers (7%) reaching tens of thousands of dollars. Targeted organizations are typically financial institutions, manufacturing companies, and service companies.

Various access types are sold on the dark web. One-third ads offer VPN or RDP connections. Access via Shell (11%) and remote access programs like AnyDesk and Citrix (10%) is also a common option.
Figure 48. Types of access available on the dark web
Of all ads analyzed, 20% target the commerce sector, followed by services (17%) and industry (16%).
Figure 49. Access sale messages by industry
Services
The dark web isn't just a marketplace for selling malware, exploits, and system access; it also offers various illicit services. Infrastructure services, including dedicated servers, VPNs, and proxies, are also in high demand.
Figure 50. Messages about cybercriminal services
Nearly a third (29%) of ads relate to carding, offering stolen card numbers, expiration dates, CVV codes, cardholder information, phone numbers, addresses, and emails. Criminals use this data for fraudulent purchases or cashing out money. Due to its relative simplicity, carding is often used by beginners.
Traffic redirection and installs (boot traffic) account for 16% of messages. By using such services, attackers redirect users to malicious resources, such as phishing sites or malware-laden pages. Users clicking on ads are redirected to phishing sites and tricked into installing malware disguised as legitimate software.

Reliable infrastructure is essential for cyberattacks. Infrastructure-related messages (5%) advertise services ranging from hosting and proxies to VPS, VPNs, and dedicated servers.
VPNs create secure, anonymous connections by encrypting traffic and masking location. Dark web VPN services can start as low as $4 per month. Cybercriminals have varying VPN preferences: using legitimate commercial products, renting dark web VPNs, or creating their own tools. Proxy servers also provide anonymity by hiding IP addresses, but unlike VPNs, they don't encrypt traffic.
Dedicated servers, starting at $100 per month, are crucial for cyberattacks, serving as command centers or hosting platforms.

To appear legitimate, phishing websites require hosting and domain names. Domain names can start at $2, with prices varying by domain zone. An SSL certificate4, which enhance a site's perceived trustworthiness, can be included in the service cost or sold additionally.

Hacking services are highly sought after on the dark web, comprising 49% of all advertisements. These ads rarely feature high-profile attacks against organizations. Instead, they typically offer simpler services like accessing personal data, hacking social media and messenger accounts, identifying website vulnerabilities, or compromising corporate email. The clients for such services aren't just individual fraudsters; businesses also seek a competitive edge by accessing competitors' confidential information Compromising a personal email account can cost as little as $100, while corporate email accounts can fetch around $200.
Prices vary depending on the likelihood of success. For instance, one dark web forum offered Telegram account hacking services priced at $70 for a 50% success rate and $90 for a 70% success rate.

Rising demand for hash cracking
Requests for hash cracking on dark web forums hit a record high at the end of 2023, before dropping by 29% in Q1 2024. However, demand surged again by Q3 2024, reaching a new peak. Hashes are used for various tasks, including verifying data integrity during transmission and protecting files. However, their most common use is for storing passwords. When you create an online account and enter a password, the website doesn't store it in plain text. Instead, it converts the password into a unique string of characters—a hash. Even if hackers steal the database, they only obtain these hashes, not the actual passwords.
Figure 55. Number of messages related to hash cracking (by quarter)
Several factors contribute to the increasing demand for hash cracking. Users often choose weak, predictable passwords. NordPass researchers, analyzing a 2.5 TB database compiled from open sources, created a list of the worst passwords. These include examples like "123456" and "password", whose hashes are easily cracked.
Let's not forget about cryptocurrencies. Attackers can steal funds from cryptocurrency wallets by cracking cryptographic hashes.
Cryptocurrencies rely on hashes to verify transactions and protect wallet access, making hashes a prime target of attackers.
The demand is also due to an increasing number of confidential data breaches. Our research shows that over half of the successful attacks on organizations in 2023 and 2024 resulted in data breaches. If attackers crack a hash and obtain the password used to access critical systems within a company, they gain access to confidential data and resources.
This service can cost as little as $10.
Attack costs
While cyberattacks might appear inexpensive at first glance, the preparation and purchase of tools, especially for novice criminals, can be expensive. The figure below outlines the costs associated with preparing a common attack vector (assuming the attacker is a beginner).

Criminals must acquire all the necessary tools and services to conduct a cyberattack. The first step is infrastructure setup. This involves purchasing proxy servers and VPNs, and renting dedicated servers to create a secure, anonymous environment for managing attacks. Next, attackers acquire essential tools like loaders and the Cobalt Strike framework for post-exploitation. To make malware fully undetectable (FUD) and bypass antivirus software, attackers purchase crypters and Extended Validation (EV) certificates for code signing.
Criminals, particularly beginners, often lack the necessary skills for infrastructure setup and Cobalt Strike usage, leading them to seek consultations on the dark web. They might also join a ransomware gang to use existing malware instead of creating new tools. However, joining a gang requires more than just desire; it often involves an entry fee and an established reputation on the dark web. Alternatively, criminals can purchase ransomware source code or builders.
Gaining access to a target organization's infrastructure involves various methods. Criminals might send phishing emails, probe for vulnerabilities on the network perimeter, or purchase access on dark web marketplaces. They might also scan open ports for vulnerabilities or outdated software. If no known vulnerabilities are found in the system, hackers can use privilege escalation services available on dark web markets.
This preparation phase is expensive, with total costs for infrastructure, tools, services, and consultations sometimes reaching $20,000. However, this price may vary depending on the specific products acquired. If attackers opt for Ransomware-as-a-Service (RaaS), they typically share 10–30% of the ransom with the malware developers.
According to Coveware, the average ransom in Q2 2024 was $391,015 (a 2.4% increase from Q1 2024), while the median ransom decreased to $170,000 (a 32% decrease from Q1 2024).
For companies, the real cost of cyberattacks goes far beyond just ransom payments. In June 2024, technology company CDK Global fell victim to a ransomware attack that paralyzed the company's servers for two weeks. The incident disrupted around 15,000 of auto dealerships across the U.S. that used the company's software. While CDK paid a ransom of $25 million, the estimated financial losses for the affected dealerships during the initial two weeks of downtime exceeded $600 million.
Evolution of the shadow market
Since 2015, the dark web has adopted the subscription model from the legitimate business world. Various subscription-based services have appeared, including Malware-as-a-Service (MaaS), Ransomware-as-a-Service (RaaS), Phishing-as-a-Service (PhaaS), and DDoS-as-a-Service (DaaS). Thanks to subscription, attackers no longer need to develop their own tools. Today's underground market mirrors legitimate businesses, offering customer support and regular updates.
Every quarter brings new services, such as phishing kits distributed under the PhaaS model, like Tycoon 2FA or ONNX. Some of these pose significant threats to organizations. In the summer of 2023, Proofpoint warned of a large-scale campaign in which one phishing kit was used to send around 120,000 fraudulent emails to hundreds of organizations worldwide. Proofpoint experts also mentioned the use of this tool by the TA4903 group.
The following section will explore the ongoing evolution of the dark web market.
A ransomware monopoly exists on the dark web, attracting many high-profile cybercriminals. Access to this forum is restricted, requiring either a strong reputation on other dark web forums or a $500 fee, filtering out casual users. However, many other English-speaking underground platforms permit ransomware advertising and sales, creating a separate market for low-cost ransomware. Low-cost malware programs are readily available to a wider range of attackers. Unlike ransomware requiring complex infrastructure, cheaper variants enable criminals to target small and medium-sized businesses (SMBs) that often lack the resources for cybersecurity defenses or incident response. Successful attacks against SMBs may lead to smaller ransom demands (compared to those of more sophisticated groups), often amounting to a few thousand dollars. Companies are more likely to pay these smaller ransoms, as the alternative—forensic investigation and data recovery—could be much more expensive.

Malware source code prices vary. One dark web forum listed ransomware source code for $8,000, which is 38 times less than the price of its more sophisticated counterpart INC Ransom.
On one dark web forum, the median price for basic ransomware source code is around $400, with some available for as little as $50.
Cybercriminals are constantly evolving their tactics to make attacks more effective. One example is the creation of dark web versions of popular file-scanning services. Legitimate platforms let users upload files to be checked for viruses by multiple antivirus engines. These platforms share data with antivirus developers, helping them improve their software. However, their underground counterparts analyze files for antivirus detection without sharing the results. This allows criminals to test their malware without alerting security companies. The existence of these platforms highlights how the dark web market adapts legitimate technologies to improve efficiency and cater to the needs of cybercriminals.
Individual file checks cost just $0.10. For frequent scanning, monthly subscriptions are available starting at $25.

In January 2024, cybersecurity firm Trellix analyzed a ransomware program advertised on a dark web forum. What's notable is that the hackers offered to customize the malware for each attack. Using a builder, they could tailor the ransomware to a specific victim, significantly increasing the chances of a successful breach and maximizing potential damage.

Services also exist for modifying malicious files to bypass VirusTotal checks. This means antivirus software won't detect the file as malicious.
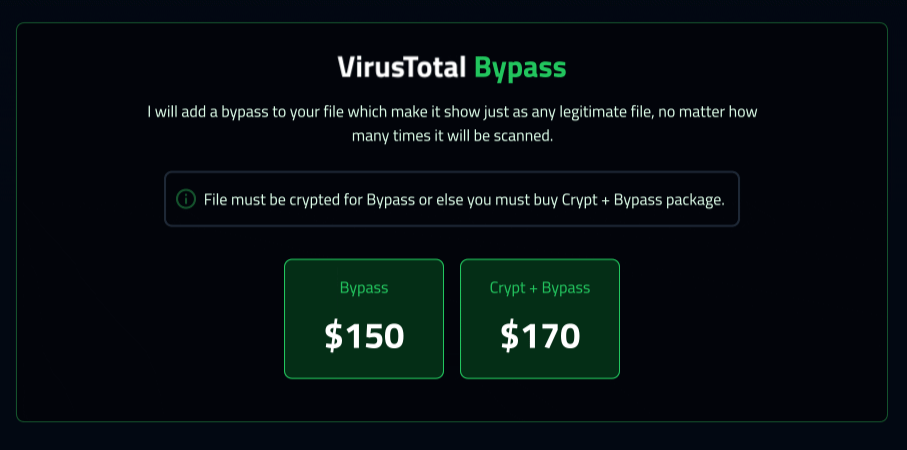
A significant innovation on the dark web is the increasing use of trial periods and demo versions. Free trials lower the barrier to entry for potential buyers. With no upfront payment required, they can evaluate products with minimal risk, which is particularly appealing given the abundance of competing offers on the dark web. This approach allows hackers to expand their customer base and drives the market toward a service-oriented model.

The dark web economy continues to evolve, incorporating new technologies to enhance fraudulent schemes. In a novel development, malware operators launched their own cryptocurrency and NFT5 on the TON (The Open Network) blockchain in April 2024. This represents a potential new revenue stream for criminals and allows them to build a unique ecosystem around their coin. For example, the cryptocurrency could be used to purchase products or access exclusive offers unavailable to regular users.

A new feature has emerged on a dark web forum: a log store integrated directly into ransomware control panels. These logs are datasets collected by hackers after a breach, including bank app accounts, social media profiles, cryptocurrency wallets, and VPN configurations. This data is collected using a stealer (malicious software designed to steal data). For cybercriminals, these logs are a treasure trove of monetizable information. They can contain highly valuable data such as website admin panel access, credentials for major social media accounts, or payment card details. Furthermore, logs can include sensitive data exploitable in attacks against organizations, including VPN configurations, repository access keys, SSH keys, and two-factor authentication (2FA) details.
Stolen logs can be bought on the dark web. However, hackers often sell outdated and already-used data that is no longer relevant (passwords changed, sessions expired, funds withdrawn). The integrated log store addresses this issue by allowing criminals to sell partially-used or discarded logs that still hold potential value. This new feature enables cybercriminals to attract more clients, increase profits, and ultimately target more victims.

Looking ahead
The service model's ongoing development is lowering the bar for cybercriminals, thus increasing the number of cyberattacks. The number of incidents in 2024 was 16% higher than in 2023.
Figure 64. Number of incidents in 2022–2024
In the near future, new types of services will likely emerge, enabling hackers to launch cyberattacks with just a single click. Thanks to the development of AI6, an attacker will probably only need to select a target and click "Launch attack." This would open the door for those who previously couldn't carry out attacks due to a lack of knowledge or skills.
The dark web may evolve, with single providers offering integrated services: payment processing, log stores, exploits, and malware modules.
EaaS
Exploit-as-a-Service (EaaS) represents another potential development in the cybercrime landscape. Zero-day vulnerabilities are expensive, often costing millions of dollars, putting them out of reach for many attackers. The EaaS model will allow cybercriminals to rent out exploits, instead of selling them to one person. This could lead to a significant increase in the number of attackers capable of exploiting vulnerabilities, while enriching exploit developers.
Existing exploit kits offer a glimpse into this future service model. These software packages automate the exploitation of website and web application vulnerabilities. According to PRODAFT, the RIG Exploit Kit (RIG EK) was widely used in 2022 (a third of successful attacks), with hackers making around 2,000 hacking attempts daily.
A notable recent development on the dark web is the sale of accounts to a major dark web forum. Since December 2023, numerous advertisements for accounts to a popular dark web platform have appeared. Traditionally, joining such forums required demonstrating technical skills and possessing a reputation within the cybercriminal community. The market for selling accounts to popular dark web platforms is expected to grow, which may lead to an increase in the number of attackers and cyberattacks. After all, now even less skilled hackers have access to closed forums.

C4
Throughout H1 2024, we heard about attackers using the Sliver framework. Sliver, an open-source penetration testing framework, enables the creation and management of implants capable of performing various malicious actions on compromised systems, including privilege escalation, credential theft, and lateral movement. By Q3 2024, Sliver had become a notable trend within the cybercriminal community. Currently, interest in the Nighthawk7 framework is surging on dark web forums. While it remains unclear whether Nighthawk has been leaked, the high level of interest and the substantial sums offered for access (with one advertisement offering $50,000) suggest its potential use by both sophisticated APT groups and less-experienced hackers, particularly if a leaked version appears on the dark web.

Cybercriminals are increasingly interested in Brute Ratel C4, a tool with similar capabilities to Cobalt Strike8, designed to bypass security solutions like EDR9 and antivirus software. Unlike Nighthawk, Brute Ratel C4 has seen wider distribution, with version 1.4.5 leaked onto the dark web in July 2024. This leak has resulted in its active use in cyberattacks, as evidenced by Knownsec 404 Advanced Threat Intelligence's discovery of a potential attack targeting Bhutan in July 2024, attributed to the Patchwork group (APT-C-09) using Brute Ratel C4.

We've seen a steady rise in cybercriminal interest in AI-powered tools throughout 2024, and this trend is expected to continue. AI can automate various tasks, from vulnerability scanning and phishing email creation to data analysis. We also highlighted in Q2 2024 the increasing use of optical character recognition (OCR) by malware developers. In September 2024, McAfee researchers discovered a new type of SpyAgent malware for Android, which uses OCR to steal mnemonic key phrases (used as a backup key for recovering access to a crypto wallet) by scanning for images on devices.
Interestingly, malware using machine learning algorithms was also found on the dark web. This malware, according to its seller, can self-propagate across a network and replicate itself onto connected external drives.

Legitimate automated tools are also being used by criminals. RidgeBot, a penetration testing tool developed by Ridge Security for identifying and exploiting system vulnerabilities, was leaked onto the dark web with a price tag of $1,000. The consequences of this leak could be severe. Cybercriminals can use RidgeBot to steal sensitive data and hold it for ransom, or inflict significant system damage, potentially costing companies millions in recovery expenses.
The availability of such tools on the dark web may also intensify competition, pushing malware developers to integrate more AI modules into their creations, including less experienced cybercriminals.

The sale of Extended Validation (EV) certificates10 on the dark web is another concerning trend. Legitimate publishers and software developers undergo extensive vetting by Certificate Authorities (CAs) to obtain EV Code Signing certificates, providing proof of their physical and legal existence. Cybercriminals are increasingly acquiring these certificates to bypass security measures like and evade antivirus detection. The demand for such certificates within the cybercriminal community is expected to rise, increasing the offer. In August 2024, Intrinsec released a report on the growing market for EV certificates.

As demand increases, so does the opportunity for fraud. This leads to various scams where malicious actors take payment without delivering the promised goods or services.

Just like legitimate businesses use mystery shoppers to evaluate service and product quality, dark web forums, where sellers compete for buyers, are likely to adopt similar practices. Competition among sellers will rise, leading to an increase in the quality of services.
Rudimentary forms of this already exist. For example, one dark web forum uses live vendor verification. Sellers submit their offerings and complete a test task to demonstrate the quality of their services. A platform auditor (a trusted representative) then evaluates this task. If the seller meets the required standards, they are permitted to conduct business on the forum.

Conclusion
The dark web has evolved into a sophisticated ecosystem with its own set of rules, enforcement mechanisms, and regulated transactions designed to minimize fraud.
It has become a marketplace for cybercriminal services and attack tools, with a service model that caters to attackers of all skill levels, thanks in part to leaked tools and guides. Various criminal groups use these readily available resources, making attribution more difficult for investigators. Mirroring legitimate businesses, dark web sellers employ marketing strategies like customer reviews, polished landing pages, and user-friendly interfaces to attract and retain customers.
The focus on bypassing security measures has fueled the trade in crypters and EV certificates, while malware developers constantly adapt their tools to changes in browsers and other systems, increasingly incorporating AI modules to stay competitive.
A trend towards service integration is also apparent, with some sellers bundling log stores into malware control panels and even creating their own cryptocurrencies. This points towards a future where a full suite of attack tools and services, from logs and exploits to complete attack packages, could be accessible within a single integrated platform.
The initial investment for tools and services needed to launch a cyberattack can be around $20,000 (assuming the attacker has no existing tools). However, a successful attack can yield returns far exceeding initial costs, posing a significant financial risk to targeted organizations. Beyond ransom payments, the disruption of business processes can lead to substantial losses, potentially reaching millions of dollars.
Organizations need to adopt a proactive defense strategy. Regular dark web analysis and threat intelligence are crucial for identifying emerging threats like exploits, vulnerabilities, and new attack tools. A result-driven cybersecurity approach, focusing on preventing non-tolerable events identified by top management, allows organizations to prioritize their defenses against the most critical risks.
Organizations should consider implementing a multi-layered security approach incorporating:
- Web Application Firewalls (WAFs): to protect web applications from various attacks.
- Sandboxes: to analyze suspicious files in a safe environment and prevent malware execution.
- Email security testing: to evaluate the effectiveness of existing email security measures.
- Security information and event management (SIEM): to collect and analyze security events.
- Extended Detection and Response (XDR): to detect advanced attacks, investigate incidents, and quickly respond to threats.
- Vulnerability management: to identify and remediate vulnerabilities.
- Network traffic analysis (NTA): to detect anomalous network behavior indicative of malicious activity.