In Q3 2018 research Positive Technologies experts show that data theft is the main driver of cybercrime. Cases of data theft grew by 5 percent as compared to the previous quarter and by 20 percent as compared to Q3 2017; however, hackers were less driven by profit (only 33% compared to 53% at the beginning of 2018). Stealing money in cyberspace is becoming increasingly difficult; it is much easier to steal commercial secrets, private data, personal correspondence, photographs, or video recordings and demand enormous ransom for non-disclosure of information, or simply sell these data on the dark web.
Contents
Symbols used

Trends and forecasts
Positive Technologies keeps monitoring the most important IT security threats. Although Q3 is considered vacation time, hackers do not take a break and keep inventing new cyberattacks.
Summarizing our findings from the third quarter of 2018, we note the following trends:
- The number of unique cyberincidents exceeded the equivalent year-ago period (Q3 2017) by 24 percent.
- The number of attacks aimed at stealing information also continued to grow, almost reaching 50 percent of the total number of cybercrimes. Personal data, credentials, and credit card information remain the three favorite targets of attackers.
- The use of social engineering drastically increased over Q3. In vast majority of cases, hackers attacked individuals, reaching them via phone calls, SMSs, email, and even through ordinary post.
- Cases of malware infection also became quite widespread. Unlike cryptolockers that became less popular in Q3, the number of cases involving malware infection increased up to 20 percent (12% in Q1 and 9% in Q2). This is probably linked to the GandCrab operators' aggressive policy: discovered in early 2018, this ransomware evolved to the fifth version by September. Infection by miners keeps decreasing, which is apparently related to the drop in exchange rate of several cryptocurrencies.
- Attacks against financial institutions became more popular compared to Q2. This is mostly linked to a surge in phishing attacks performed by Cobalt group. In total, financial institutions lost $18 million to attacks in Q3 2018.
Q4 will be a time to take stock. We predict the growing number of phishing attacks against employees dealing with annual accounts and budget planning. These attacks will likely target government and financial institutions. As we approach the New Year, people will buy a lot of stuff online. We expect more cases of malware infection via websites and more thefts of credit card information. Despite an increasing number of attacks against cryptocurrency exchanges in Q3, we expect that they will become less widespread in Q4 as bitcoins are falling in price.
Statistics
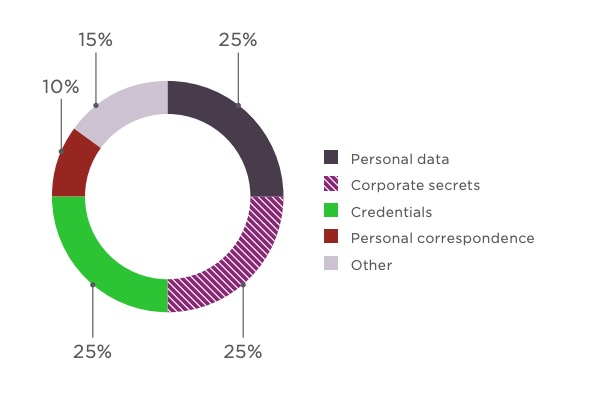
The most common motive behind cyberattacks in Q3 2018 was data theft. Cases of data theft grew by 5 percent as compared to the previous quarter and by 20 percent as compared to Q3 2017; however, hackers were less driven by profit (only 33% compared to 53% at the beginning of 2018). Stealing money in cyberspace is becoming increasingly difficult; it is much easier to steal commercial secrets, private data, personal correspondence, photographs, or video recordings and demand enormous ransom for non-disclosure of information, or simply sell these data on the dark web.

Personal data, credentials, and credit card information continue to tempt criminals, accounting for more than a half of all the compromised information. A lot of incidents involving personal data theft can be explained by poor digital literacy of victims. People very often provide personal data for a small compensation in online services or publish them in social media, without understanding how precious this information could be for attackers.
Every fifth data theft involved stealing account credentials. Oftentimes, attackers steal passwords used for online services and web applications in order to gain access to other systems where a more precious information is processed, for example medical data. Credential stuffing attacks are much effective than simple bruteforcing, as people often use the same credentials for accessing various systems.

As in the previous quarter, targeted attacks prevailed over mass attacks in Q3 accounting for 55 percent of the total number of incidents. Targeted attacks were mainly aimed at government institutions. We saw a growing number of attacks against financial institutions (9% compared to 6% in Q2). Medical and education institutions also remained a popular hacking target. Every fifth attack was aimed at individuals. Later in this report, we will more closely consider these categories of attacks. Large-scale cyberattacks affecting more than one industry (most often, malware outbreaks) have been placed in the "Multiple industries" category.

The percentage did not significantly change in comparison with Q2. However, it is worth mentioning a small decrease in the number of attacks compromising websites and an increase in attacks against users.

Q3 2018 saw a growing number of social engineering and malware attacks. Quite often attackers used these two methods simultaneously. Incidents involving hacking (exploitation of vulnerabilities without using social engineering and malicious software) increased as compared to Q2, reaching 23 percent. In 3 percent of cases attacks were conducted through abusing legitimate software. In July, PT ESC experts investigated cases in which attackers used publicly available utilities, such as PortScan, GsecDump, and Mimikatz in addition to their proper tools.


Attack number
In July, we observed the highest number of attacks since the beginning of 2018. Over 40 percent of all the unique attacks registered in Q3 were performed in July. This can be explained by the FIFA World Cup held in Russia from June 14 to July 15. During this period, our experts counteracted about 38,000 attempts to disrupt the Transport Directorate services.


Attack methods
We will take a closer look at each attack method and indicate which targets and industries were most affected.
Malware use

Malware use remained the most widespread method of attacks in Q3. The number of incidents involving malware increased up to 56 percent in Q3 as opposed to 49 percent in Q2. Infections by cryptolockers also increased from 9 to 20 percent, outrunning spyware attacks. Ransomware attacks hit government and education institutions, medical centers, industrial companies, and individuals. Thus, the GandCrab ransomware discovered in early 2018 evolved to the fifth version by September. Illicit cryptocurrency mining, on the contrary, decreased, with only 8 percent of cases in Q3, compared to 15 and 23 percent in Q2 and Q1, respectively. It is quite difficult to discover a hidden miner, whereas illicit file encryption is normally detected on the first day of the incident. Users are simply not aware of helping attackers earn money by illicit cryptocurrency mining.
The decreasing number of cases involving illicit cryptocurrency mining can be explained by the fact that attackers themselves are losing interest in this business. Cryptocurrency mining is becoming more and more difficult (due to the increase in the hashrate). In addition, the exchange rate of several cryptocurrencies has been falling since the early 2018. All these reasons make illicit mining unprofitable. At the same time, a first-ever prison sentence in cryptojacking case was issued in July 2018.1 A Japanese man was sentenced for a year in prison for illicit cryptocurrency mining despite making only $45.
Cases involving infection via official app stores grew from 4 percent in Q2 to 9 percent in Q3 2018. In August, Doctor Web experts detected2 over 100 fraudulent Android applications on Google Play. These applications subscribe users to paid services and spread advertisement. In late September, ESET found3 a banking Trojan, an even more dangerous malware. The banker was introduced into QRecorder—an application used to record phone calls—and allowed attackers to steal victims' credentials and credit card information. By using this data, hackers stole over €78,000 from the victims' accounts.


In 31 percent of cases malware was spread by email. This is the easiest and therefore the most popular method of delivering malware to a victim's computer. In September, PT ESC experts discovered a new surge in continuous APT attacks. By using the CMstar downloader, hackers exploited the vulnerability CVE-2017-11882.
Social engineering

At a time of permanent cyberwar between criminals and information security experts, hackers aspire to not only upgrade their technical skills, but also get a deeper knowledge of human psychology. Q3 2018 saw a significant increase in cases of deceiving people in order to gain profit. Thus, a 20-year-old U.S. student performed numerous SIM hijacking attacks. The student convinced mobile providers of having lost his mobile phone and thus got hold of the SIM cards belonging to the people he chose as victims. He then got access to various services, including cryptocurrency wallets. The criminal hijacked more than 40 phone numbers and stole several million U.S. dollars in cryptocurrency.
Hacking

To conduct attacks, hackers use business logic errors in applications, flaws in security mechanisms, and known vulnerabilities in non-updated software. Attackers use the found vulnerabilities to get profit, a process we call hacking.
oT vulnerabilities allow attackers to create botnets in order to conduct powerful DDoS attacks. Routers remain a popular hacking target. eSentire Threat Intelligence experts detected4 an attempt to exploit the vulnerability CVE-2018-10562 in Dasan and D-Link devices. Recently, attackers started using vulnerable routers as a point of entry to mine cryptocurrency in users' browsers. For this end, in Q3 they exploited5 a zero-day vulnerability in hundreds of thousands of MikroTik devices. The manufacturer released a patch the next day after the vulnerability was detected; however, a lot of router owners still have not updated their firmware.
Errors in the software code can be extremely detrimental. Cryptocurrency platforms are especially attractive for attackers, as they have numerous logic errors, for example in transaction mechanisms. In July, Livecoin crypto exchange lost more than $1.8 million because of a Monero code vulnerability. In September, hackers exploited the vulnerability CVE-2018-17144 in a Bitcoin protocol. The vulnerability was found in a little-known pigeoncoin cryptocurrency that was not timely patched by its developers. The hackers made off with $15,000 in cryptocurrency.
Web attacks

Attacks against web applications not only allow hackers to gain control over the apps and penetrate a company's internal network, but can also be used for political purposes. Websites remain a favorite target of hacktivists, allowing to quickly communicate ideas to millions of people. In July, hackers hit the website of the Taiwan's Democratic Progressive Party leaving political messages on the compromised pages.6
Hackers usually exploit vulnerabilities in applications to use them as a platform for spreading malicious software. In July, hackers replaced7 the links on the VSDC Video Editor website. After following the modified links, a spyware was installed into victims' computers collecting data and sending them to the hacker's server. People in more than 30 countries suffered from the incident.
Web application code errors may lead to major data leaks due to insufficient user authorization. An error8 on the website of Telefónica, a telecommunication provider, led to the disclosure of personal and financial information of the Movistar TV customers. The company faces a fine of 2–4 percent of the annual turnover for the GDPR violation. A similar fine threatens Facebook for compromising tens of millions of user accounts because of a coding error.9
Credential compromise

In Q3 2018, we observed a small decrease in the number of attacks aimed at bruteforcing credentials. In early July, weak passwords and the absence of two-factor authentication allowed attackers to steal personal data of 21 million Timehop users.10 Users are well aware of the requirements for strong passwords. Unfortunately, even people working in the IT industry can fall victim to credentials bruteforcing. Thus, hackers gained access to a developer's npm account, which allowed them to inject malware directly into the JavaScript library code.11 In September, the developers of AdGuard, a famous ad blocking software, reset passwords to all user accounts because of a bruteforce attack.12
DDoS

The beginning of the school year was marked by a surge in DDoS attacks against education institutions. Thus, the University of Edinburgh website was hit on September 12 and was unavailable for more than 24 hours.13
It is no secret that unscrupulous entrepreneurs hire hackers to disrupt competitors' infrastructure or to disable their websites. In July, two major game developers, Blizzard Entertainment and Ubisoft, were hit within days of each other with DDoS attacks. The attacks were probably initiated by competitors or disgruntled gamers, unhappy with the companies' policy.
Another popular reason for DDoS attacks is hacktivism. Thus, politically motivated hacktivists disabled the website of the Swedish Social Democratic Party,14 shut down for almost 24 hours the website of Bryan Caforio, a Californian candidate for U.S. Congress,15 hit a Dutch government website,16 and attempted cyberattack on the website of South Africa Department of Labor.17
Victim categories
Here we will analyze the most important attacks against particular sectors in Q3 2018.
Government


In order to get hold of secret government data, hackers keep searching for new ways of penetrating government information systems. In one such case, the attackers found an unusual way to deliver malware to the U.S. government agencies, playing up curiosity of potential victims. Employees received letters via mail that included malware-laden compact discs.18

Hackers take an increasing interest in government institutions in the run-up to important political events. Thus, in the run-up to the Swedish elections, hacktivists spread nationalist slogans and deceptive information in Twitter via botnets.19
Oftentimes, hackers use their skills to cyberspy government agencies. TEMP.Periscope, a Chinese espionage group previously known for its attacks against maritime entities, sent20 a phishing message to the Deputy Director General of an opposition party in the run-up to the general elections in Cambodia. The message purported to come from LICADHO, a non-governmental organization promoting human rights. A malicious attachment in the message contained a downloader that installed spyware on the victim's computer.

Finance



Q3 was marked by attacks against financial institutions performed by the APT groups. Thus, MoneyTaker attack21 against network infrastructure of PIR Bank (Russia) resulted in the theft of over 58 million rubles (about $850,000). Another major attack hit22 Cosmos Bank (India) resulting in the damage worth approximately $13 million. The crime was allegedly performed23 by the North Korean hacking group APT38. In Q3 2018, we observed an increasing number of attacks against banks performed by Cobalt group. PT ESC experts registered 12 such attacks from July to September. In July, the attackers generally used JavaScript backdoor; since August, however, they started spreading CobInt malware. In August and early September, phishing messages were sent from fake domain addresses that were supposed to belong to the Interkassa payment system, the European Central Bank, BBVA Compass Bancshares, Unibank, Alfa-Bank, and Raiffeisenbank.
Cobalt group uses different methods to deliver malware. Thus, in early 2018, the criminals sent documents containing exploits. Since May, however, they switched to sending documents with obfuscated macros that made it difficult to detect attacks by antivirus solutions. Since September, the group started sending PDF files with malicious links, exploiting the Open redirect vulnerability.24


Healthcare



Healthcare institutions keep attracting criminals, as stolen medical data can bring huge profits, especially data of top-ranking government officials. An attack against SingHealth group in Singapore resulted in the theft of personal data of over 1.5 million people and medical data of about 160,000 patients, including the country's prime minister and other government officials.25 Phishing attacks usually allow hackers to get hold of medical employees' credentials and to access closed databases. Thus, an attack against the Guardant Health medical center in California resulted in the leak of personal and medical data of over a thousand of clients.26
Despite the decrease in the number of attacks against medical institutions (33% as compared to 38% in Q2), several medical centers still got hit by attackers. Thus, hackers attacked medical institutions in the U.S., Canada, India, and Hong Kong, infecting computers with ransomware. In most cases, infection becomes possible when companies do not timely upgrade their software. Software upgrading can take a lot of time and effort, and any failure or error may put patient lives and health at risk. Thus, a vulnerability in the software of CarePartners, a Canadian healthcare company, allowed attackers to conduct a ransomware attack compromising medical and contact data of tens of thousands of clients.27 The company now faces substantial fines.
Education


As mentioned, education institutions suffered from numerous attacks at the beginning of the school year. In late August, Cloquet schools (U.S.) were hit by a ransomware attack second time in the past three years.28 Monroe County School District was also hit by a ransomware campaign.29
A large-scale campaign by Cobalt Dickens spread during summer vacation hit 76 universities in 14 countries all over the world.30 The attackers sent phishing messages to the university employees with links to spoofed websites and login pages. By stealing the account credentials, hackers got access to intellectual property of education institutions.
Individuals



Q3 was marked by an increasing number of attacks involving social engineering (60% as opposed to 38% in Q2). By manipulating people's feelings, hackers hit individuals who are often not security-savvy. In August, an extortion email campaign took place with attackers claiming that the recipients' phones were hacked and that people were recorded over their webcam.31
In addition to credit card information, hackers also steal private data, correspondence, and photographs, using this information to demand ransom. In Q3, criminals hacked numerous user accounts in messengers and social networks. In August and September, large-scale attacks targeted Instagram users.32 Thousands of people lost their accounts, many of them having over 10,000 subscribers. The victims were often ready to pay a ransom to get their accounts back, as they had largely invested in promoting their accounts in the first place. If attackers fail to get ransom, they can try selling the accounts or using them to send spam messages.
What companies can do to stay safe
Use proven security solutions:
- Implement centralized management for timely installation of updates and patches.
- Use antivirus protection solutions with embedded isolated environment (sandbox) for dynamic file testing, capable to detect and block malicious files in corporate emails before the messages are opened by employees, and to eliminate other viruses. The most effective approach is to use antivirus software solutions developed by different manufacturers, capable to detect hidden malware and block viruses in data flows, including email, network, and web traffic, file storages, and web portals. The solution must not only check files in real time, but also automatically analyze files that have already been checked; this will allow detecting new threats when signature bases are updated.
- We also recommend using the SIEM solutions to timely detect and effectively respond to information security incidents. This will help identify suspicious activity, prevent infrastructure hacking, detect attackers' presence, and take prompt measures to neutralize the threats.
- Use automated software audit tools to identify vulnerabilities.
- Use web application firewalls as a preventive measure to protect websites.
- Implement systems allowing deep network traffic analysis in order to detect complex targeted attacks in real time and in backup copies. You will be able to detect attacks that have not been found earlier and to monitor network attacks in real time, including malware run and hacking tools, exploitation of software vulnerabilities, and attacks against the domain controller. This approach will allow you to quickly identify attackers' presence in the infrastructure, minimize the risk of losing critical data and disrupting business systems, and to decrease financial damage caused by attackers.
- Use specialized anti-DDoS services.
Protect your data:
- Encrypt all sensitive information. Do not store sensitive information where it can be publicly accessed.
- Perform regular backups and keep them on dedicated servers that are isolated from the network segments used for day-to-day operations.
- Minimize the privileges of users and services as much as possible.
- Do not use identical username–password combinations for multiple systems.
- Use two-factor authentication where possible, especially for authenticating privileged accounts.
Do not allow weak passwords:
- Enforce a password policy with strict length and complexity requirements.
- Require password changes every 90 days.
- Replace all default passwords with stronger ones that are unique.
Monitor and stay current:
- Keep software up to date. Do not delay installing patches.
- Test and educate employees regarding information security.
- Monitor the network perimeter for any new insecure resources.
- Regularly perform penetration testing to identify new vectors for attacking internal infrastructure and evaluate the effectiveness of current measures.
- Regularly audit the security of web applications, including source-code analysis, to identify and eliminate vulnerabilities that put application systems and clients at risk of attack.
- Track the number of incoming requests per second. Configure servers and network devices to resist typical attacks (including TCP/UDP flooding and database overloading).
- Filter traffic to minimize the number of network service interfaces accessible to external attackers.
Keep clients in mind:
- Improve security awareness among clients.
- Regularly remind clients how to stay safe online from the most common attacks.
- Urge clients to not enter their credentials on suspicious websites and to not give out such information by email or over the phone.
- Explain what clients should do if they suspect fraud.
- Inform of security-related events.
How vendors can secure their products
- All of the preceding recommendations for companies ("What companies can do to stay safe"), plus:
- Implement a secure development lifecycle (SSDL).
- Regularly audit the security of software and web applications, including source-code analysis.
- Keep web servers and database software up to date.
- Do not use libraries or frameworks with known vulnerabilities.
How users can avoid falling victim
Invest in security:
- Use only licensed software.
- Maintain effective antivirus protection on all devices.
- Keep software up to date. Do not delay installing patches.
Protect your data:
- Back up critical files. In addition to storing them on your hard drive, keep a copy on a USB drive, external disk, or a backup service in the cloud.
- Use an account without administrator privileges for everyday tasks.
- Use two-factor authentication where possible, such as for email accounts.
Do not use weak passwords:
- Use complex passwords consisting of at least eight letters, numbers, and symbols. Use a password manager to create and store passwords.
- Do not reuse passwords. Set a unique password for each site, email account, and system that you use.
- Change all passwords at least once every six months, or even better, every two to three months.
Be vigilant:
- Scan all email attachments with antivirus software.
- Beware of websites with invalid certificates. Remember that data entered on such websites can be intercepted.
- Pay close attention when entering passwords or making payments online.
- Do not click links to unknown suspicious sites, especially if a security warning appears.
- Do not click links in pop-up windows, even if you know the company or product being advertised.
- Do not download files from suspicious sites or unknown sources.
- zdnet.com/article/for-the-first-time-remote-cryptojacker-sentenced-for-exploiting-coinhive/
- news.drweb.com/show/?i=12797&lng=en
- lukasstefanko.com/2018/09/banking-trojan-found-on-google-play-stole-10000-euros-from-victims.html
- esentire.com/security-advisories/increase-in-attacks-on-gpon-routers/
- trustwave.com/en-us/resources/blogs/spiderlabs-blog/ mass-mikrotik-router-infection-first-we-cryptojack-brazil-then-we-take-the-world/
- taiwannews.com.tw/en/news/3473203
- videosoftdev.com/news/attacks-successfully-stopped
- facua.org/es/noticia.php?Id=13025
- newsroom.fb.com/news/2018/09/security-update/
- timehop.com/security
- bleepingcomputer.com/news/security/compromised-javascript-package-caught-stealing-npm-credentials/
- adguard.com/en/blog/adguard-security-notice/
- edinburghnews.scotsman.com/our-region/edinburgh/edinburgh-university-hit-by-crippling-cyber-attack-1-4798612
- https://www.thelocal.se/20180822/swedens-social-democrats-website-hacked
- thehill.com/policy/cybersecurity/407608-california-democrat-hit-with-ddos-attacks-during-failed-primary-bid
- nltimes.nl/2018/08/01/ddos-attack-leaves-digid-site-unreachable
- mybroadband.co.za/news/security/274161-hackers-did-not-compromise-our-servers-department-of-labour.html
- krebsonsecurity.com/2018/07/state-govts-warned-of-malware-laden-cd-sent-via-snail-mail-from-china/
- bloomberg.com/news/articles/2018-08-30/ sweden-sees-increase-in-cyber-attacks-seeking-to-disrupt-vote?cmpId=flipboard
- fireeye.com/blog/threat-research/2018/07/chinese-espionage-group-targets-cambodia-ahead-of-elections.html
- bankingtech.com/2018/07/pir-bank-in-russia-victim-of-domestic-1m-hack/
- hindustantimes.com/india-news/15-000-transactions-in-7-hrs-cosmos-bank-s-server-hacked-rs-94-crmoved-to-hong-kong/story-wazUXZs3LRhcbPLg7LYx5O.html
- content.fireeye.com/apt/rpt-apt38
- openbugbounty.org/reports/81002/
- moh.gov.sg/news-highlights/details/singhealth's-it-system-target-of-cyberattack
- mddionline.com/guardant-exposed-cybersecurity-threat-phishing-scheme
- cbc.ca/news/technology/carepartners-data-breach-ransom-patients-medical-records-1.4749515
- spamfighter.com/News-21734-Cloquet-School-District-Again-Targeted-by-a-Ransomware-Attack.htm
- scmagazine.com/home/news/new-gandcrab-variant-attacks-florida-school-district/
- secureworks.com/blog/back-to-school-cobalt-dickens-targets-universities
- twitter.com/secguru_otx/status/1028364785631617025
- mashable.com/2018/08/13/instagram-hack-locked-out-of-account/?europe=true#KzywbMs8rqq6