In Q3, the total number of incidents went down only slightly (by 2%) when compared to the previous quarter. Social engineering remained the top threat to individuals (92%). Cybercriminals were eager to improve their malicious methods and use new tools, including neural networks. In attacks on organizations, cybercriminals continued to use malware (in 45% of cases), but the share of encryption malware dropped from Q2 2023, with some ransomware operators now stealing data without encrypting systems. Exploitation of vulnerabilities accounted for a significant share (37%) of successful attacks on organizations. The third quarter also saw multiple cyberattacks that caused serious consequences, such as data breaches (56% of successful attacks on organizations and 61% of attacks against individuals).
Key figures and trends
In Q3 2023, total incidents were down only slightly (-2%) when compared to the previous quarter. Exploitation of vulnerabilities accounted for a significant share (37%) of successful attacks on organizations, with bad actors still taking advantage of flaws in popular IT solutions. Cybercriminals continued to use malware (in 45% of cases), but we have seen the share of ransomware drop by 6 percentage points from Q2 2023. Social engineering remained the biggest (92%) threat to private individuals and a major (37%) vector of attacks on organizations. More than half of organizations (56%) suffered a data breach as a result of successful attacks. Disruption to core business functions was relatively rare, dropping by 8 percentage points to 36% from Q2. We assume this is due to several ransomware gangs switching to stealing data without encrypting systems.
Evolution of social engineering techniques
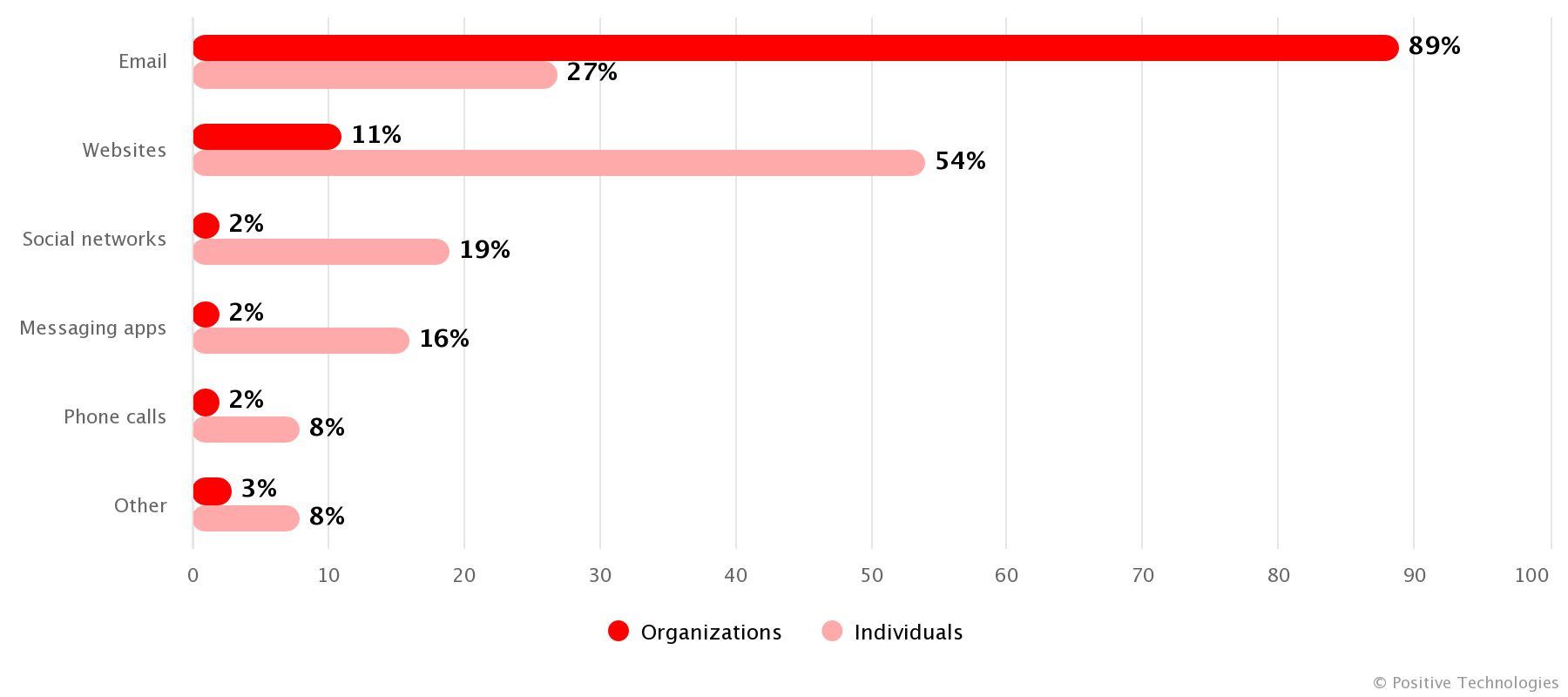
In Q3 2023, bad actors used various social engineering channels in successful attacks on individuals: phishing websites (54%), email (27%), social media scams (19%), and instant messaging hoaxes (16%).
ЗPhishing scams continued to exploit the themes of employment, deliveries, political turmoil, and making a quick buck, such as by investing in crypto. Q3 2023 saw scammers use phishing-as-a-service platforms: for example, Proofpoint reported a large-scale EvilProxy campaign that in which more than 120,000 phishing messages were sent. We mentioned the new platform last year, and now we are seeing cybercriminals use it to target the management of more than 100 companies, with 65% of the victims being top managers and the remaining 35% having access to corporate financial assets or confidential data.
Cybercriminals increasingly turning to PDF files for hidden phishing
Cybercriminals are increasingly using files with the .pdf extension to bypass email security. The researchers at Vipre report that the use of malicious PDF files has increased fivefold since 2023 began. According to Netskope data, PDF attachments were the number-one format for spreading malware throughout Q3. Bad actors embedded malicious links into PDF files, while additionally disguising these with QR codes in some of their attacks. In August, JPCERT/CC reported on a new technique, MalDoc, being used to circumvent detection by embedding malicious Word files within PDFs. These are files with the .pdf extension that open in Word, triggering malicious macros.

Social engineering techniques growing more sophisticated
Bad actors used highly elaborate tactics to give their victims a false sense of security. Scammers' arsenals contained both modular tools for crafting convincing phishing sites and email reply chains, as well as multi-stage attacks that saw the hackers follow a sequence of steps to get to their objectives by combining several cyberfraud techniques. Imperva in August reported on a large-scale campaign that employed more than 800 phishing domains imitating those operated by 340 major companies around the world. The bad actors created high-quality single-page applications in 48 languages to steal bank card details. The cybercriminals combined various fraudulent techniques within one attack. As an example, the Letscall malware toolkit, which targeted users in South Korea in July, is a combination of phishing websites and vishing (voice phishing, a social engineering technique). The cybercrooks used a fraudulent site made to look like Google Play to spread spyware. Besides collecting data on the infected device, the spyware redirected calls to a fake call center if the victim noticed the suspicious activity and tried to call their bank. The call center operator used the previously collected details to lull the victim into a false sense of security, manipulating them into revealing further data or making a money transfer.
Several attacks relied on compromised corporate IT systems to attack customers and business partners. Researchers at Perception Point discovered a multi-stage phishing campaign where the malicious actors attacked hotels listed on Booking.com, trying to both steal data and hijack the hotel’s booking account. The scammers used the perfectly credible official hotel accounts to attack the hotels’ customers, taking advantage of the guests’ absolute trust in the service.
Neural networks in cybercriminal service
Cybercriminals have been busy looking for ways to leverage neural networks for attacks. AI helps malicious actors to maintain fake meaningful conversation with their victims, generate convincing phishing emails, and create audio, image, and video deepfakes. We predict that AI-powered attacks will grow in number as more cybercriminals add the tool to their arsenals. Besides trying to trick ChatGPT into generating malware, they create their own toolkits. For example, WormGPT, a generative neural network designed for phishing and BEC attacks, is based on the GPT-J open-source language model. Armed with WormGPT, even a hacker with very basic skills can automate the creation of convincing fake emails and sustain prolonged attacks that make use of meaningful messaging in any language.

All eyes on secure data transfer systems
Managed file transfer (MFT) solutions are a staple of corporate networks, so it is little wonder hackers immediately home in on these systems' security flaws. Companies tend to place great value on the data stored in this type of applications, which encourages cybercriminals to demand a hefty ransom for not making public the information they steal.
Reverberations from the Cl0p epidemic
Last quarter, we covered the multiple attacks perpetrated by the Cl0p ransomware gang, which explored vulnerabilities in the MOVEit Transfer MFT product by Progress Software. Unsurprisingly, more attacks followed in Q3, exacerbating the effects of successful hacks in the second half of Q2. Cl0p continued to publish regular data leak announcements, demanding a ransom. According to Emsisoft, the total number of organizations affected by the MOVEit hack at the end of October exceeded 2,500, which translated into more than 66 million affected users worldwide.
Other IT solutions now at risk
More cybercrime groups joined the game, with the trend catching the attention of threat researchers, who discovered new vulnerabilities in data transfer systems in Q3. Researchers are racing to fix these new security holes before hackers start to exploit the zero-day vulnerabilities.
In mid-August, CISA issued a warning about ongoing exploitation of CVE-2023-24489, a critical vulnerability in the ShareFile application. This cloud product from Citrix helps customers and employees to securely upload and download files. ShareFile published security tips back in June, and a patch was released in the form of a private recommendation in May, which allowed customers to remediate the flaws even before information about the vulnerability became public knowledge. According to Citrix, more than 83 percent of its ShareFile customers were able to complete the appropriate steps to protect their systems in advance.
In September, Rapid7 researchers discovered a number of vulnerabilities in the Titan MFT and Titan SFTP systems by South River Technologies. Active exploitation was avoided through coordinated disclosure.
In an interesting turn of events at the end of the quarter, the aforementioned Progress Software published security tips relating to multiple vulnerabilities in WS_FTP Server, another secure file transfer solution. Three days later, Rapid7 analysts observed as the WS_FTP security flaws were widely exploited in the wild.
The increasing number of MFT vulnerabilities underscores the need for a comprehensive assessment and a management process.
Malware: tricks old and new
The share of malware incidents in Q3 2023 remained at the previous quarter's level. Ransomware was still the most widely used type of malware in successful attacks, but its share shrank by 6 percentage points from Q2. The use of ransomware diminished due to newly released decryption tools as well as extortion gangs' gradual forgoing of system and data encryption in favor of threatening to publish victims' data. The share of spyware in attacks on private individuals increased to 65%, but its share in successful attacks on organizations remained at 20%. More than half (57%) of all corporate infections with various types of malware occurred through malicious attachments and links received through email. Websites remained the main technique used in attacking individuals at 49%, up by 9 percentage points from Q2.
Expanding attack geography
Bad actors are taking proven malware tools to new countries and regions. At the end of Q3, Threat Fabric reported that new versions of popular MaaS (malware-as-a-service) tools were crossing the Atlantic: a new campaign involving the complex Xenomorph malware was detected in the United States in August. Xenomorph previously circulated in Europe and the Middle East.
VMs for bypassing security
In Q3 2023, bad actors used virtual machines to hide ransomware activity from security systems, specifically by starting a different operating system inside the target host's own with the help of virtualization software. This embedded OS receives access to system resources and then launches the ransomware. The malware can then execute all of its illegal functionality while staying under the radar of the host's security systems. This is an approach used by the creators of the BlackCat ransomware, also known as ALPHV. The hackers released a new tool, Munchkin, as an instance of Alpine Linux designed for spinning up virtual machines with ransomware inside, on networked devices.
The USB removable media threat is back from the dead
Researchers from Mandiant in September reported on a campaign that targeted international organizations operating in Africa. A group named "UNC53″ managed to damage 29 companies around the world by using an attack chain that began with infected USB removable media. The media was typically infected with the Sogu malware after being inserted into public computers located in Internet cafés or photocopying centers.
We predict that these legacy attack techniques will grow in popularity, as they remain relevant in developing cybersecurity markets. Our past reports analyzed the level of cybersecurity maturity throughout Africa, Asia, and the Middle East. Regions that are experiencing rapid growth in information technology may be affected by inadequate user awareness and laws that are still taking shape, as well as IT system hardware and software shortcomings.
Extortion gangs adopt new techniques
Throughout Q3, cyberextortionists continued to demand a ransom for not disclosing information, while refraining from encrypting the data in several cases. We have observed a number of other notable trends.
New players means new techniques
In September, researchers at Malwarebytes pointed to increasing activity by RansomedVC. This group has hacked more than a dozen organizations, including Japan's Sony. RansomedVC presents its malicious activities as a pentesting service. Ironically, the group is abusing the European Union's General Data Protection Regulation (GDPR): should the victim refuse to pay up, the hackers publish the data they stole from the organization, which results in it being fined for failure to protect the data. The group likely sets ransom amounts below the level of the penalty to incentivize their victims.

Austria's A1-Telekom was among the first to be hit. The hackers managed to compromise vendor systems in Austria, as well as Serbia, Bulgaria, Croatia, and North Macedonia. According to RansomedVC itself, it received a partial payment that amounted to a quarter of the demanded ransom. Experts hypothesized that the group accepted ransom payments in installments, which is not typical cybercriminal behavior.

Consequences affecting customers
With a significant percentage of hacked organizations refusing to accept the demands and pay the amount stated in the ransom note, in some cases, the hackers reach out to affected customers of the victim company directly, suggesting that they pay for their data to be deleted.
An attack on a community behavioral health center in Alabama is an example of that tactic. The center, Highland Health Systems, provides treatment for individuals with a substance abuse problem. In July, BlackCat stole patient data from the center, and then announced that they were going to call every patient and employee and suggest that they pay to have their data deleted.
Double posting
Double posting is another notable trend, where two ransomware gangs announce that they have successfully attacked the same organization, and each demands a ransom. In July, Yamaha Canada Music said that it had become the victim of a cyberattack. It had already been posted by BlackByte in June, but several days later, its name appeared on a DLS belonging to the Akira ransomware gang.
This was not the year's first case of double posting. A February attack on the City of Oakland's IT systems was reported by both Play and LockBit. Experts believe that the announcements might have been made by affiliates working for two different gangs that were trying to both draw more attention to their victims and boost the reputation of a group that offered its tools under a RaaS (ransomware-as-a-service) model.
Trending vulnerabilities
Exploitation of vulnerabilities again led among productive attack techniques. In addition to the aforementioned MOVEit case, we have observed several other vulnerabilities that may be of interest to bad actors:
- CVE-2023-3519. In July, Citrix published a security bulletin that warned users about three new vulnerabilities affecting NetScaler ADC and NetScaler Gateway. These included CVE-2023-3519, a critical remote code execution (RCE) vulnerability rated 9.8 on the CVSS scale. It saw exploitation by cybercriminals even before being published, and one of the first systems to be attacked was the network of a U.S. organization in the critical infrastructure sector. After the Citrix bulletin was released, hackers ramped up exploitation, compromising a total of 1,800 systems by August 14 according to a Fox-IT report.
- CVE-2023-28121. Back in March 2023, researchers at RCE Security found a security recommendation that detailed a critical flaw in WooCommerce Payments, a WordPress plugin. Wordfence said that wide-scale attacks targeting the vulnerability, designated as CVE-2023-28121, kicked off on July 14 and continued for several days, peaking at 1.3 million attacks on 157,000 websites. The vulnerability was assigned a CVSS score of 9.8; it enables an unidentified attacker to gain administrator privileges. The consequences of the attacks are currently unknown. We believe that the interest from hackers may be linked to their campaign-priming efforts in anticipation of approaching sales. The affected plugin, used on e-commerce websites, allowed them to use the compromised site to attack shoppers.
- CVE-2023-42793. In September, the Sonar team published a report on a critical authentication bypass vulnerability in TeamCity, a continuous integration and continuous deployment (CI/CD) platform by JetBrains. Successful exploitation allows an unauthenticated intruder to execute an RCE attack, gaining control of the server and potentially running a successful supply chain attack. Several days after this disclosure, cybercrime groups began to exploit the issue. Since then, according to a report by PRODAFT, several ransomware gangs have added CVE-2023-42793 exploits to their arsenal and are actively using these to hack affected TeamCity servers.
Attack consequences
Just like in Q2, a data breach was the most common consequence of successful attacks on organizations (56%) and individuals (61%). Direct financial loss was the second most common consequence (35%). For organizations, this was disruption to core business functions (36%), although its share decreased by 8 percentage points from Q2 due to a decline in the use of data encryption by ransomware gangs. That being said, we recommend keeping an eye on ransomware attacks, as these tend to cause severe consequences. For example, several Sri Lankan government agencies lost access to email from May 17 till August 26 as a result of a ransomware attack. As there were no backups, some of the emails were permanently lost.

The top five attacks in Q3 to cause a negative impact and wide repercussions
- In late August, due to cyberattacks on Ecuador's National Electoral Council, approximately 120,000 citizens residing abroad could not cast votes before polls closed. Voters located in Europe were the most affected. Ecuadorans who were unable to vote staged a street protest in the Spanish capital of Madrid.
- In mid-September, Caesars Entertainment, a major hotel and entertainment company, lost an estimated $15 million to a cyberattack. The company agreed to pay a ransom to cyberextortionists who were threatening to leak a stolen customer database that contained information for a loyalty program.
- A September cyberattack on the telecommunication service provider IFX Networks impacted Colombia, Chile, and Panama. The attackers caused damage to 762 Spanish-American companies, multiple websites and web portals became inaccessible, and government websites and online services had to suspend operations. Some of the affected organizations were Colombia's Supreme Court, the Panama America publishing house, and Chile's Government Procurement System platform. A significant volume of data on IFX Networks clients landed in the hands of cybercriminals.
- The National Optical-Infrared Astronomy Research Laboratory NOIRLab had to suspend its Gemini North in Hawaii and Gemini South telescopes in Chile to avoid damage due to a cyberattack on August 1. The telescopes were only able to resume observations two months later, on September 29.
- The US healthcare company Prospect Medical Holdings was attacked by the Rhysida ransomware gang in August. Hospitals were forced to shut down their IT networks to prevent the attack from spreading, revert to paper charts, and suspend several services including testing. The hospitals in Connecticut suffered the most damage. August 3, the day of the attack, saw the authorities place hospitals in Code Orange, the second highest state of emergency. Ambulances had to be rerouted to other hospitals at least 29 times, and some had to travel as far as the neighboring state of Massachusetts. Hospitals were forced to cancel almost half of scheduled procedures including critical CT scans and X-rays. The attackers insist that they stole the data of 500,000 patients and medical corporate documents.
In attacks that led to confidential data leaks, the cybercriminals most often targeted personal data (47%) and intellectual property (15%). Attacks on individuals largely aimed at stealing their account credentials (34%) and personal data (24%).


The most infamous leaks in Q3 were the following:
- A data breach that impacted Indonesia's Immigration Directorate General and exposed the passport data of 34 million individuals. ДThe data included full names and genders, passport numbers, issuance and expiry dates, and dates of birth. The attack is attributed to the hacktivist identified as Bjorka.
- An HCA Healthcare data breach impacted 11 million patients. The US company said the data had been stolen from an "external storage location exclusively used to automate the formatting of email messages". HCA is facing at least five class-action lawsuits.
- A ransomware attack on Canada's Alberta Dental Service Corporation exposed the data of nearly 1.5 million of its customers. The leaked data included the personal and medical records as well as the banking information of some 7,000 members of the seniors program.
- Human error resulted in the surnames, initials, ranks, roles, and locations of the whole Northern Ireland police force, that is, 10,000 employees of the Police Service of Northern Ireland (PSNI), being available online for three hours.
- When publishing a bucket of open-source training data, Microsoft's research team accidentally exposed 38 TB of additional private data including backups of two employees' workstations. The copies contained confidential private data, passwords for Microsoft services, secret keys, and more than 30,000 Teams messages from 359 Microsoft employees.
To protect against cyberattacks, we recommend following our general guidelines on personal and corporate cybersecurity. In view of the events in Q3, we strongly recommend remaining vigilant online, and refraining from opening suspicious links or downloading attachments from unverified sources. Be suspicious of any urgent requests and offers that are too good to be true. It is always preferable to spend five minutes analyzing a situation than to lose your money and/or data.
Organizations should be more careful when selecting their software vendors and work on improving their vulnerability management processes. We recommend that software developers get involved in bug bounty programs and follow the coordinated vulnerability disclosure process. We also recommend using web application firewalls (WAFs) to harden the network perimeter. To protect devices against malware infection, we recommend using sandboxes that allow file behavior analysis in a virtualized environment, detecting any malicious activity, and acting in time to prevent damage to the company. Ransomware remains a serious threat, leading to the conclusion that backing up your data is a must.
Statistics

Targeted attacks accounted for 74% of successful cyberattacks
14% of successful attacks targeted individuals






About the report
This report contains information on current global information security threats based on Positive Technologies' own expertise, investigations, and reputable sources.
We estimate that most cyberattacks are not made public due to reputational risks. As a consequence, even companies specializing in incident investigation and analysis of hacker group activity are unable to calculate the precise number of threats. Our research is aimed at companies and ordinary individuals who care about the state of information security to the key motives and methods of cyberattacks, as well as highlighting the main trends in the changing cyberthreat landscape.
This report considers each mass attack (for example, phishing emails sent to multiple addresses) as one incident, not several. For explanations of terms used in this report, please refer to the glossary on the Positive Technologies.
