This study examines the evolution and security implications of IoT as a cyber-physical system integrating operational and IT infrastructures. We focus on how IIoT optimizes production, enables predictive maintenance, and provides real-time data monitoring. We also evaluate the manufacturing industry's vulnerability to cyberthreats amid increasing digitalization and explore the potential consequences of attacks on IIoT systems and devices.
Ekaterina Snegireva
Senior analyst, Research Group of PT Cyber Analytics
Summary
- Companies are adopting the Industrial Internet of Things (IIoT) to address a range of challenges. Whether monitoring production, tracking IT equipment, or automating process adjustments, IIoT has proven transformative.
- Cyberthreats to edge devices, sensors, and controllers include hardware vulnerabilities, firmware flaws, botnet infections (which exploit company resources for DDoS attacks), and malware designed to cause service disruptions or equipment failures. Weak passwords and unsecured internet connections also present significant risks.
- Data transfer protocols and IoT gateways are vulnerable to flaws in both the protocols themselves and vendor solutions. As IIoT platforms expand and data storage and processing centers grow, these systems become prime targets for cybercriminals. Cloud data centers are also at risk.
- The manufacturing sector is a primary target for APT (Advanced Persistent Threat) groups, primarily for cyberespionage, along with hacktivists and ransomware operators. APT-related attacks accounted for 19% of all breaches in manufacturing during the first three quarters of 2024.
- Aimed at raising awareness, hacktivist attacks tend to make incidents as high-profile as possible. Though the immediate impact is generally limited, the increasing sophistication of these attacks suggests more serious risks ahead.
- Ransomware operators, motivated by financial gain, pose a major threat. In the first three quarters of 2024, ransomware was involved in 52% of malware attacks on the manufacturing sector.
- Most successful attacks target sensitive data. In 2024, 65% of breaches involved stolen information, with trade secrets making up 37% of the stolen data and operational disruptions accounting for 33%.
- Our core defense strategy focuses on proactive, result-driven cybersecurity, an approach that consists in defining non-tolerable events for the organization and verifying these cyberthreats. This includes maintaining a current asset inventory, patching vulnerabilities promptly, segmenting networks, and training staff. Companies should also secure their hardware and software supply chains and participate in bug bounty programs.
- The industry is increasingly adopting automated, smart manufacturing. Key trends include streamlining technological workflows, integrating AI into existing systems, adopting digital twins, and scaling IIoT solutions.
- However, the lack of standardization in IIoT remains a major challenge for organizations looking to adopt the technology. In response, some countries have enacted laws and programs to secure not only the devices and data but also the systems to which these devices are connected.
Introduction
The term Internet of Things (IoT) describes a domain where physical and virtual objects converge into a unified cyber-physical system. "Things" refers to any object that can be identified and integrated into communication networks, from everyday devices like smartphones, smart bracelets, home electronics, video cameras, and medical equipment, to machines and sensors in manufacturing and transportation.
The IoT is about more than collecting data; it's about shaping it. IoT devices are quickly being integrated into sectors like smart cities and various industries. In 2023, Statista reported 15.9 billion active IoT devices, with the number expected to grow to 32.1 billion by 2030. Similarly, IoT Analytics forecasts a 13% increase in connected devices by the end of 2024.
The IoT ecosystem is divided into domains based on device application. Consumer IoT enhances daily life through devices like smart speakers and home automation systems.
Extended Internet of Things (XIoT) is an umbrella term that encompasses domains such as the Internet of Medical Things (IoMT), smart buildings (building management systems), Industrial IoT (IIoT), and Operational Technology (OT) networks. Today, IoT meets diverse organizational needs across industries. According to Fortune Business Insights, in 2023, IoT adoption was highest in healthcare, manufacturing, telecommunications, and agriculture.
This study examines the evolution and security implications of IoT as a cyber-physical system integrating operational and IT infrastructures. We focus on how IIoT optimizes production, enables predictive maintenance, and provides real-time data monitoring. We also evaluate the manufacturing industry's vulnerability to cyberthreats amid increasing digitalization and explore the potential consequences of attacks on IIoT systems and devices.
How IIoT works and why it's essential
The inner workings of IIoT
IIoT systems vary, but they all share key components: peripheral devices, communication tools, data processing platforms, and user applications. The IIoT framework operates as follows: end devices, which control physical objects or collect environmental data, connect to data storage centers via a network. These centers then link to a unified control system, which serves as an analytical platform accessible to users.
Given the diversity of IIoT architectures, no single model fits all. In 2014, leading industry players—AT&T, Cisco, General Electric, IBM, and Intel—formed the Industrial Internet Consortium (IIC) to bridge the gap between the physical and digital worlds. The IIC created a guide for IIoT architects, enterprise leaders, and developers, outlining common architectural patterns. These include gateway-mediated edge connectivity1, system-of-systems (SoS) orchestration2, and the three-tier architecture. The latest model features three levels: Edge, Platform, and Enterprise, connected by data exchange networks.
1. The gateway-mediated edge connectivity and management architecture pattern comprises a local connectivity solution for the edge of an IIoT system, with a gateway that bridges to a wide area network. The gateway acts as an endpoint for the wide area network while isolating the local network of edge nodes.
2. The system-of-systems (SoS) orchestrator pattern is a collection of systems, each capable of independent operation, coordinated by the orchestrator. The IIoT system may be configured as distributed systems remote from each other (for instance, turbine engines at a wind power plant or oil rigs at an oil field), and powerful computing capabilities may be required on or near the assets for local analytics and management.
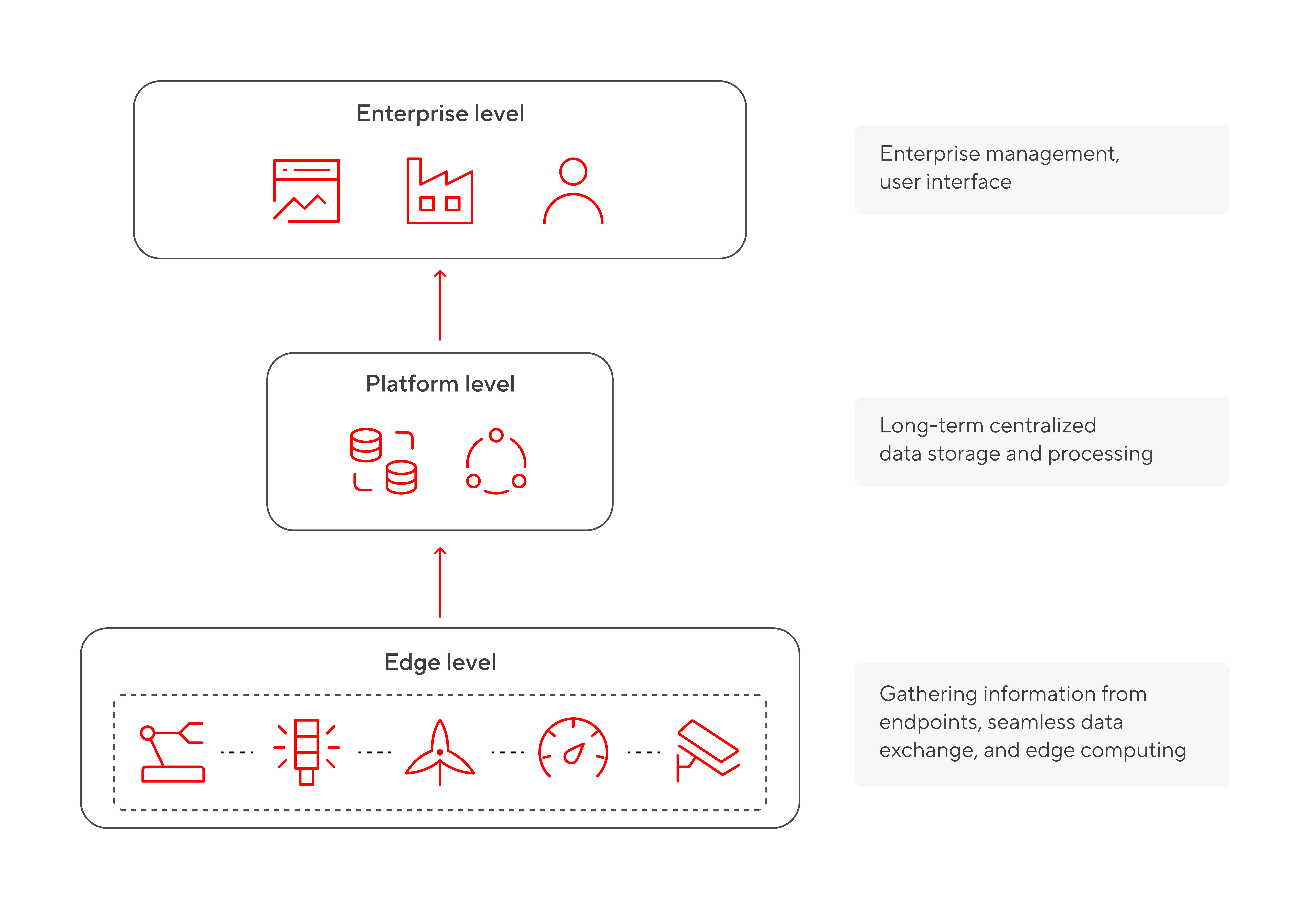
Edge level
Edge devices collect data on physical parameters, such as spatial positioning, voltage, pressure, and applied force, enabling interaction with the physical world. Sensors gather data, while actuators enable interaction. Devices can be simple or smart, with smart devices capable of performing computations and processing data locally. At this level, edge computing technology allows data processing and storage close to the device generating the data.
Platform level
At the platform level, data from the edge and enterprise levels is analyzed. Long-term, centralized data storage is maintained, and business analytics are generated based on the collected data. Machine learning and big data technologies are also utilized. Cloud platforms and data centers are commonly used for storage.
Enterprise level
The enterprise level provides an interface for users to interact with the IIoT system. Industry-specific applications and decision support systems are implemented. A system orchestrator—unified management system—is also deployed to integrate distributed IIoT systems.
Data exchange networks
The levels are connected by networks that ensure device operation across these tiers. At the edge level, data is transferred between sensors, actuators, and the local edge computing center, often wirelessly, which expands the attack surface. IoT gateways facilitate data transfer from the physical to the digital environment by supporting essential communication protocols. Corporate networks are typically used for data exchange between different levels.
Why embrace IIoT technology?
According to our data3, IoT adoption spans multiple areas, with companies using it to address various tasks simultaneously. IIoT is primarily adopted to monitor production and technological processes, track IT equipment, and automate decision-making for process adjustments.
In power engineering, IIoT upgrades power supply channels and implements smart grids. IoT-powered systems collect energy consumption data, enabling precise resource allocation and efficient use. The power engineering sector leads in IIoT adoption and ranks second in smart manufacturing implementation.
In the petrochemical industry, companies like Sibur use their own IIoT platforms. For example, wireless sensors monitor water temperature at treatment facilities, connected to a unified network. Hundreds of similar sensors across the factory detect overheating sources, enabling timely responses. Video analytics, powered by machine learning, also automatically detects process deviations such as leaks, smoke, or poor-quality raw materials.
In metallurgy, the Magnitogorsk Iron and Steel Works (MMK) has launched a wireless IIoT network to collect data from hard-to-access sensors or those not connected to digital systems.
Mechanical engineering also benefits from IIoT. United Engine Corporation (UEC) was recognized as Russia's leader in digital transformation for its IoT implementation. UEC's IIoT system monitors equipment workload, performance maintenance, downtime, and staff activity, providing real-time machine operation analysis. The operation of machines is monitored and analyzed in real time.
How hackers target the industrial internet of things
Modern technological processes demand seamless interaction between physical objects, production equipment, software components, and IT systems. While digitalization enhances efficiency in both technological and business processes, it also introduces significant cybersecurity risks.
Cyberthreats to edge devices, sensors, and industrial controllers
Exploiting hardware vulnerabilities and firmware flaws
When connected, even simple actuators and sensors become targets for cyberattacks, as they are integral parts of the IIoT system. But cybercriminals don't stop there—they often focus on industrial controllers. Hardware and firmware vulnerabilities in these devices can lead to hijacking, service denial, and major disruptions, including production halts at critical industrial sites.
In 2024, Positive Technologies identified five vulnerabilities in Mitsubishi Electric's MELSEC System Q and MELSEC System L PLC processor modules. These modules, used in sectors such as chemicals, semiconductor production, and building automation, were vulnerable to exploitation. In 2022, two vulnerabilities were discovered and fixed in Mitsubishi's MELSEC iQ-F controllers. The controllers are used in food production, manufacturing, building automation, shipping, water management, and many other sectors.
In 2023, Positive Technologies helped eliminate vulnerabilities in OMRON controllers (CVE-2023-22357). This flaw allowed attackers to access and modify any memory area of the controller without authentication, enabling firmware overwrite, denial of service, or arbitrary code execution. OMRON PLCs control systems such as conveyors, machine tools, power plant pipelines, farm microclimates, product quality control, and automated packaging—critical functions that could be severely disrupted if compromised.
Exploiting vulnerabilities in IoT devices does more than disrupt operations. It undermines the quality of the data these systems collect. Organizations are increasingly integrating video analytics and CCTV systems into their workflows, which raises the stakes. Cybersecurity researchers recently uncovered a vulnerability in Dahua CCTV cameras that allows hackers to manipulate timestamps on recorded footage. This manipulation compromises the reliability of video analytics systems by altering critical date and time data.
Legacy vulnerabilities continue to be a major entry point for cybercriminals. A 2023 ThreatLabz report revealed that 34 of the 39 most exploited IoT vulnerabilities were over three years old. These flaws remain unpatched in many systems, making them easy targets for attackers who rely on outdated weaknesses.
IoT devices often share similar hardware and software, which magnifies the risks of a single vulnerability, meaning a single vulnerability could expose multiple vendors to the same hacking risk. In October 2024, Germany's CERT@VDE reported vulnerabilities in mbNET.mini industrial routers by MB connect line. These routers are widely used as VPN gateways for remote industrial maintenance. The vulnerabilities also affected Helmholz's REX100 industrial routers.
The dark web adds fuel to this fire. Hackers use it to share exploit information, making it easier and faster to launch attacks. Addressing vulnerabilities quickly is not just a best practice; it is essential for protecting critical systems from exploitation.
Botnets
The ThreatLabz report revealed a 400% increase in cyberattacks using malware targeting IoT devices in 2022. Analysts attributed most of this surge to botnet activity, including the spread of the Sality botnet, which was analyzed by Dragos experts.
Our surveys indicate that organizations rank the use of IIoT devices in large-scale DDoS attacks among the most dangerous cyberattack scenarios.
Weak passwords and unsecured internet access
IoT devices often come with default passwords that are difficult or impossible to change. For example, NETGEAR XR1000 router software versions prior to 1.0.0.58 had a vulnerability that prevented users from changing these passwords. Another critical issue is that many IoT devices automatically connect to available networks as soon as they are powered on. This behavior, combined with unchangeable default passwords, creates a significant security risk for certain models. Using specialized search engines designed to detect internet-connected devices, cybercriminals can locate IoT devices and exploit default passwords published online. Templates for these search requests, including those tailored for the Shodan browser, are widely distributed on dark web forums, often for free or at minimal cost.
Some tools enable cybercriminals to connect to device control panels by scanning for weak passwords and basic vulnerabilities. Although these tools are often created for legitimate use, they are frequently misused by malicious actors to carry out attacks. Their accessibility on dark web forums lowers the barrier for entry, allowing even low-skilled hackers to exploit industrial systems.
Security challenges at the end device level
Key security issues at the end device level include:
- Insufficient standardization. Many IoT device components function as "black boxes," offering little transparency into their internal workings These devices may contain hidden features that pose significant security risks.
- Insufficient security update support. Many manufacturing companies rely on outdated devices that do not support critical security updates. Even when vulnerabilities are identified, organizations are often reluctant to update firmware due to the potential for supply chain disruptions or operational downtime. However, ignoring updates can lead to far more serious risks. For example, in 2023, Forescout researchers identified 21 vulnerabilities in Sierra Wireless routers, which are widely used in healthcare and energy. Over 86,000 vulnerable devices were found to be accessible from the internet, some beyond their lifecycle and unable to receive updates. A particularly concerning case arose in October 2024, when vulnerabilities were reported in tens of thousands of traffic lights in the Netherlands. Attackers could exploit emergency radio signals to manipulate traffic lights, such as triggering a green light. Fixing this issue requires physically replacing the traffic lights, a process expected to take until 2030.
- Difficulty detecting external attacks. IoT devices often lack the ability to identify malicious files or commands. Although newer models include some protective features, vulnerabilities still exist and remain exploitable by attackers.
Vulnerabilities in data transfer protocols and IoT gateways
IIoT networks enable data exchange between central systems and devices, but cybercriminals often exploit weaknesses in the underlying protocols. In 2022, Rockwell Automation reported an increase in attacks targeting port 502 Modbus TCP, a widely used industrial protocol. Control over this port allows attackers to manipulate end devices and disrupt operations. In April 2024, Dragos identified FrostyGoop malware, written in Go, which directly interacts with industrial control systems via Modbus TCP.
Although new sensors, drives, and automation systems use modern internet protocols, many industrial controllers still depend on outdated protocols. IoT gateways are often deployed to bridge communication between legacy and modern infrastructure. However, these gateways are not immune to vulnerabilities. In December 2023, researchers revealed that Digital Communications Technologies had failed to fix a bug in the Syrus4 IoT gateway, which had been discovered months earlier. This flaw allowed unauthenticated attackers to execute arbitrary code on Syrus4 devices connected to the cloud service, potentially disrupting entire fleets of vehicles. Cybercriminals continue to exploit gateway vulnerabilities, developing malware specifically designed to target industrial communications. In April 2024, Fuxnet malware was used to attack TMSB and MPSB gateways, demonstrating how these tools remain a focus for attackers.
Exploits and hacking tools are commonly traded on dark web forums. For example, a zero-day vulnerability in an IoT gateway using protocols such as IEC-104, Modbus, or MQTT can sell for as little as $1,000. These exploits allow attackers to hijack gateways and deliver malicious commands to all connected devices, amplifying the scope of potential damage.
Hackers also distribute universal tools that exploit vulnerabilities in widely used protocols and end devices.
Vulnerabilities extend beyond communication protocols to include converters that link industrial controllers, meters, and sensors to local networks. In 2024, Positive Technologies identified and eliminated a critical vulnerability in Moxa's NPort W2150a and W2250a wireless industrial converters. If left unaddressed, this flaw could have given attackers full access to connected equipment, enabling them to disrupt technological processes.
Threats to analytical systems and end-user software
Attacks on specialized industrial software
Data shows that 37% of successful cyberattacks on manufacturing companies in Q1–Q3 2024 involved exploiting vulnerabilities. In most cases (71%), attackers focused on software vulnerabilities, including flaws within the code of industrial control systems.
Rockwell Automation identified SCADA systems as the most common targets in the industrial sector. Like many other types of software, SCADA systems often contain exploitable vulnerabilities. In 2024, Positive Technologies discovered and patched flaws in the MasterSCADA 4D platform, which is widely used to develop automation and dispatching systems for technological processes. MasterSCADA (versions 3 and 4D) is implemented in tens of thousands of projects across more than 40 industries. Exploiting this vulnerability could have allowed attackers to access the system and potentially disrupt operations.
Hackers often lack a deep understanding of industrial systems. To compensate, dark web forums provide not only attack tools but also detailed guides explaining how these systems operate and how their vulnerabilities can be exploited.
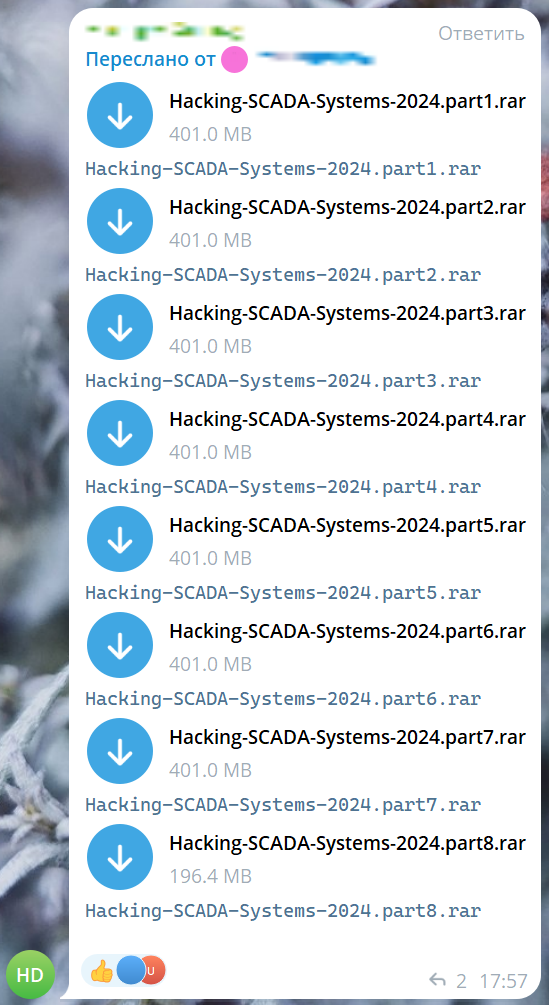
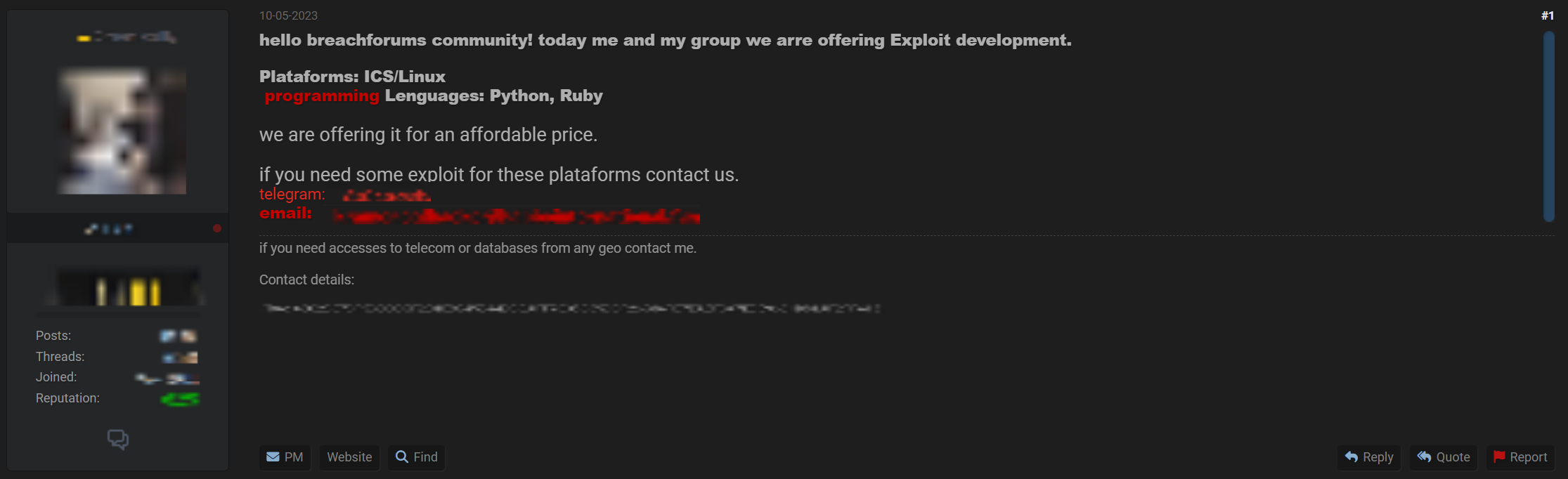
In addition to guides, the dark web hosts posts offering to develop custom exploits tailored to specific industrial systems.
Modern IIoT platform solutions include advanced analytics and process control systems. These solutions are expected to become key targets for malicious actors in the near future.
Attacks on cloud resources and data centers
The storage and analysis of large data sets almost always depend on cloud infrastructure. In attacks targeting manufacturing companies, cybercriminals are increasingly expected to focus on cloud solutions to steal sensitive data, often as part of ransom demands. In September, Microsoft researchers reported an attack by the Storm-0501 group that compromised hybrid cloud environments. This campaign resulted in data exfiltration, persistent access to the affected infrastructure, and ransomware deployment. It targeted multiple U.S. sectors, including government, manufacturing, and transportation.
Key players targeting the industrial sector and their impact
The industrial sector has been one of the top five most targeted industries for the past five years, with no indication of this trend slowing. In the first three quarters of 2024, manufacturing companies were the focus of 9% of all successful cyberattacks on organizations globally.
Figure 12. Percentage of successful attacks on manufacturing companies (of the total number of attacks on organizations)
According to Rockwell Automation, the energy sector faced the highest number of attacks in 2024. Ransomware operators and hacktivists often succeed in this sector due to the destructive nature of their attacks. Cybercriminals are also increasingly targeting organizations that provide water supply and wastewater services.
In the first three quarters of 2024, most attacks on the industrial sector involved malware (79%), social engineering (58%), and vulnerability exploitation (37%). The use of legitimate software by attackers is also on the rise. By the end of 2023, this tactic accounted for just 1% of incidents, but by the end of Q3 2024, it had surged to 8%. Legitimate tools make attacks harder to detect and are easily accessible, making them popular among hacktivists, APT groups, and ransomware operators.
Figure 13. Attack methods (Q1–Q3 2024)
Attacks by APT groups
Attacks on the industrial sector by advanced persistent threat (APT) groups are on the rise. In the first three quarters of 2024, APT groups were responsible for 19% of successful attacks, up from 13% in 2023. These attacks are marked by their precision and stealth, often employing customized social engineering, specialized malware, zero-day exploits, and other advanced methods to infiltrate and maintain control over systems. Custom malware is frequently tailored to bypass corporate security measures, including antivirus tools. Once inside a network, attackers can operate undetected for months or even years, harvesting sensitive data and maintaining persistent access to critical systems.
The goals of APT groups range from cyberespionage and financial theft to disrupting vital infrastructure. Intellectual property, proprietary technologies, business plans, and other confidential data are prime targets. Stolen information can be sold, ransomed, or used to gain a competitive advantage or accelerate technological progress. Prominent APT groups targeting the industry for cyberespionage purposes include Kimsuky, APT31, and Mustang Panda. Research by the Positive Technologies Expert Security Center (PT ESC IR) has also linked groups such as Cobalt, APT31, Dark River, Lazarus, Space Pirates, IAmTheKing, and XDSpy to incidents involving manufacturing companies, industrial sites, and the fuel and energy sectors.
The geography of APT attacks on manufacturing companies
Geopolitical, economic, and technological factors heavily influence where APT groups focus their efforts. Manufacturing companies in specific regions are especially vulnerable:
- Industrially advanced countries. Enterprises in leading economies such as the U.S., China, Japan, Germany, South Korea and others, are prime targets due to their cutting-edge technologies and valuable industry data. Countries with abundant natural resources are also high on the list, as cybercriminals seek to exploit economic advantages.
- Politically unstable regions. Manufacturing companies in areas affected by political unrest, military conflicts, or economic instability face elevated risks. APT groups often target these regions to access critical infrastructure or extract sensitive information for political, economic, or military purposes.
Hacktivism
Hacktivists launch cyberattacks to pursue political, social, or ideological agendas. Their methods include exploiting known vulnerabilities, using social engineering, and deploying common malware like ransomware.
Groups such as Cyber Partisans, GhostSec, Team-Network-Nine, Cyber Av3ngers, Electronic Tigers Unit, DragonForce, Hunt3r Kill3rs, Byte Blitz, STUCX TEAM, and LulzSec frequently target manufacturing companies. Their focus is often on industrial systems with unsecured internet access. By bruteforcing default passwords or exploiting vulnerabilities, hacktivists gain unauthorized access to device web panels or industrial control systems.
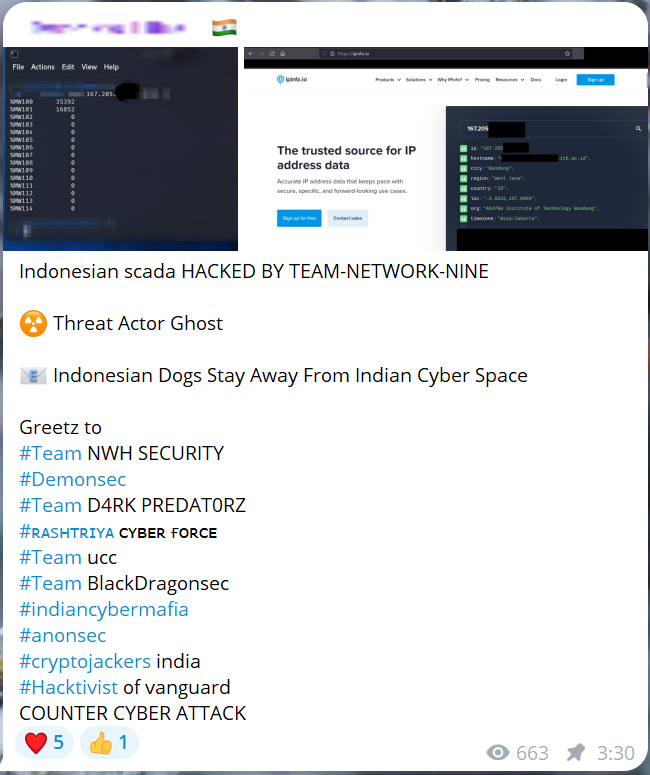
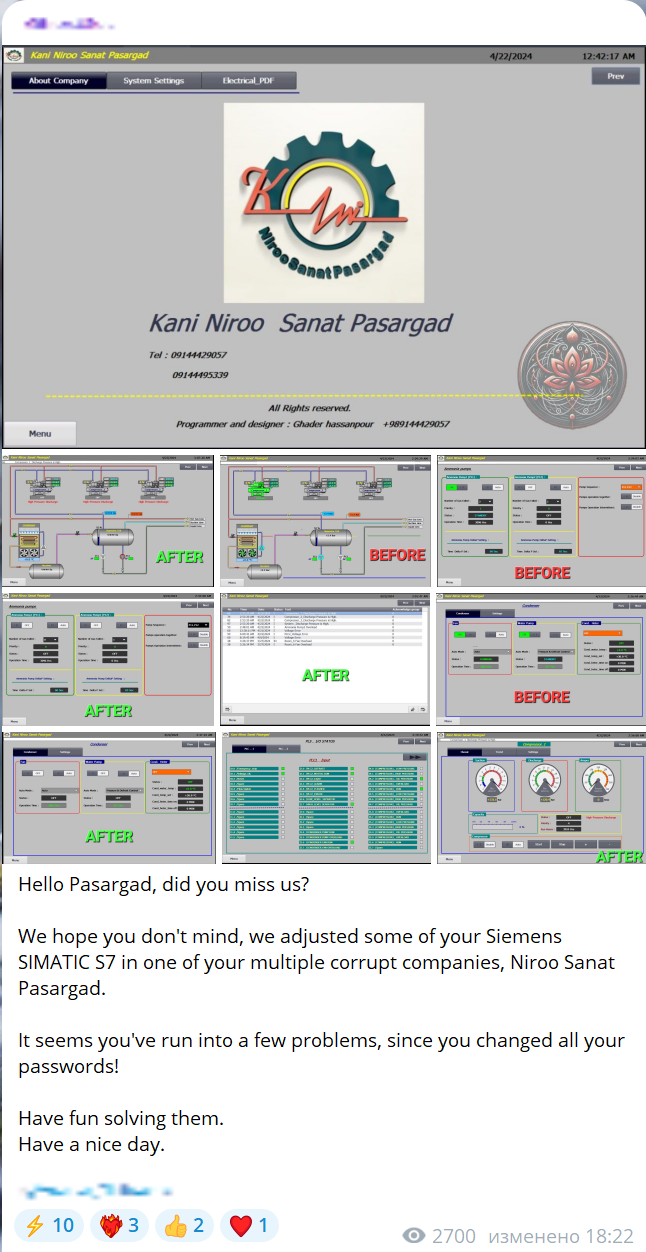
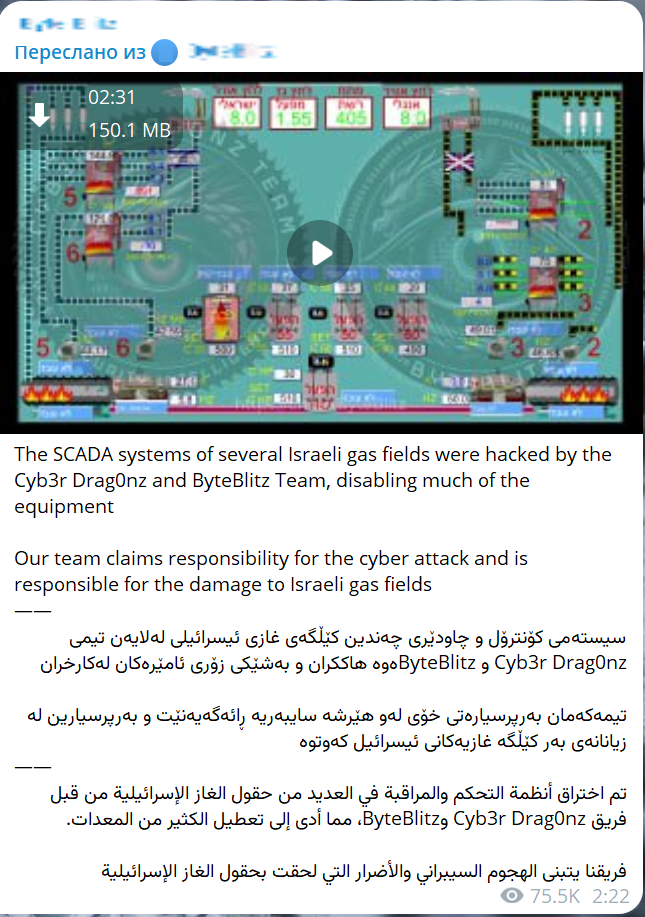
Cybercriminals often demonstrate access to infrastructure by issuing threats to shut down equipment or disrupt operations. In April 2024, hacktivists targeted Belarus's state-run fertilizer manufacturer, Grodno Azot, claiming they could halt the plant but refrained from doing so.
However, access to a control panel does not always mean attackers can directly interfere with industrial processes. For example, the hacktivist group GhostSec announced a successful breach of 55 Berghof PLCs, gaining full admin panel access. Investigators found the devices were publicly exposed online and protected by weak passwords. While access to the admin panel enables control over certain functionalities, it does not provide full authority over the industrial process. Nonetheless, as hacktivists refine their techniques, the risk of more severe consequences from such attacks is growing.
Hacktivists are particularly active in regions with political instability. A study on cyberthreats in Iran, covering early 2021 to mid-2024, revealed significant interest from hacktivist groups in the industrial sector. Many successful attacks exploited the widespread use of vulnerable IoT devices in industrial systems, which remain critical weak points in cybersecurity.
Ransomware operators
Ransomware continues to dominate as the most widely deployed malware in industrial cyberattacks. In the first three quarters of 2024, it was used in 52% of incidents targeting the sector. Attackers are increasingly shifting their focus toward specialized industrial systems, amplifying the potential for disruption. In May 2024, the ransomware group Ransomhub claimed to have breached the SCADA system of a Spanish bioenergy plant. This attack highlights the growing trend of targeting industrial control systems directly, where the stakes extend beyond financial losses to include operational paralysis and safety risks.
Figure 17. Types of malware (percentage of successful attacks)
The impact of ransomware attacks on IT infrastructure and technological networks is severe, with financial and operational consequences that can cripple businesses. According to Claroty, ransomware attacks on technological networks are on the rise, and their financial and operational impacts remain significant for businesses. While earlier attacks primarily targeted IT systems, ransomware operators have shifted focus, increasingly threatening industrial processes. This shift is reflected in data trends. In 2021, 32% of ransomware attacks targeted IT infrastructure alone, while 27% affected both IT and technological systems. By 2023, these numbers had changed significantly—only 21% of attacks focused solely on IT, whereas 37% disrupted both IT and operational technologies.
In July 2023, TOMRA faced a major ransomware attack that forced the company to isolate affected systems. The recovery process was massive in scope, requiring the restoration of core data centers, over 5,000 user accounts, and the underlying IT and network infrastructure. According to TOMRA, 82% of reverse vending machines (RVM) within its IoT network were impacted. While no evidence of data encryption or leaks was found, it took two months to fully restore operations, costing the company NOK 120 million in response efforts.
Consequences of cyberattacks
A successful cyberattack can wreak havoc on a manufacturing company, triggering financial losses from production stoppages, supply chain disruptions, raw material delays, and even environmental damage. Core operations grind to a halt, service delivery fails, and the ripple effects can extend far beyond the initial incident.
The aftermath of an attack is rarely isolated to a single issue. Companies often face cascading consequences, where one disruption amplifies others, compounding the damage and escalating recovery costs.
Figure 18. Consequences of attacks on manufacturing companies (percentage of successful attacks, Q1–Q3 2024)
Confidential data breaches
Data breaches continue to dominate as the most frequent outcome of cyberattacks on manufacturing companies. In 2023, 68% of successful attacks resulted in the exposure of confidential information. This trend has held steady, with breaches accounting for 65% of incidents in the first three quarters of 2024.
The primary target for cybercriminals is trade secrets and other critical business data. In 2023, trade secrets made up 42% of all stolen information, underscoring their value to attackers. By Q3 2024, this share had declined slightly to 37%, yet the theft of proprietary data remains a top threat.
Figure 19. Types of stolen data (Q1–Q3 2024)
Cybercriminals exploit stolen confidential data in several ways, with double extortion being one of the most common tactics. In these attacks, data is both encrypted and held hostage, with attackers threatening to leak it publicly unless a ransom is paid. Beyond extortion, stolen data frequently appears for sale on the dark web, where it fuels further criminal activity and amplifies the impact of the initial breach.
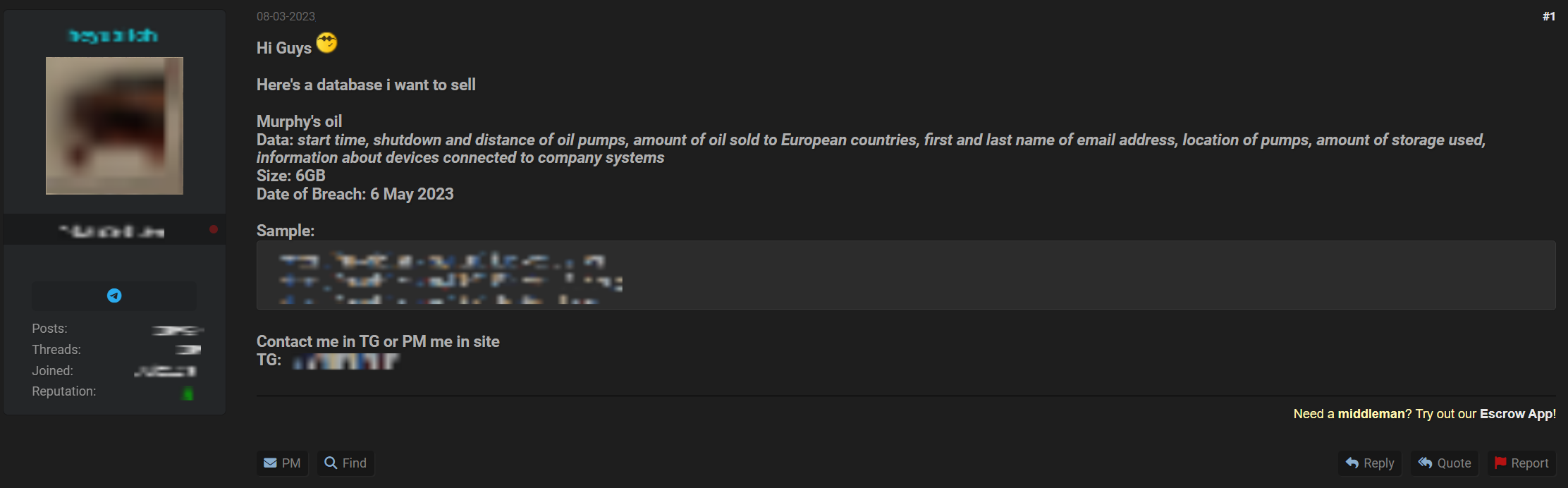
On a dark web forum, a user claimed to have access to confidential data from an unnamed company. The offering included control over switches, routers, and internal cameras, along with a file server containing 11 terabytes of sensitive information. The scale and diversity of the stolen data highlight the depth of the breach and the significant risks posed to the compromised organization.
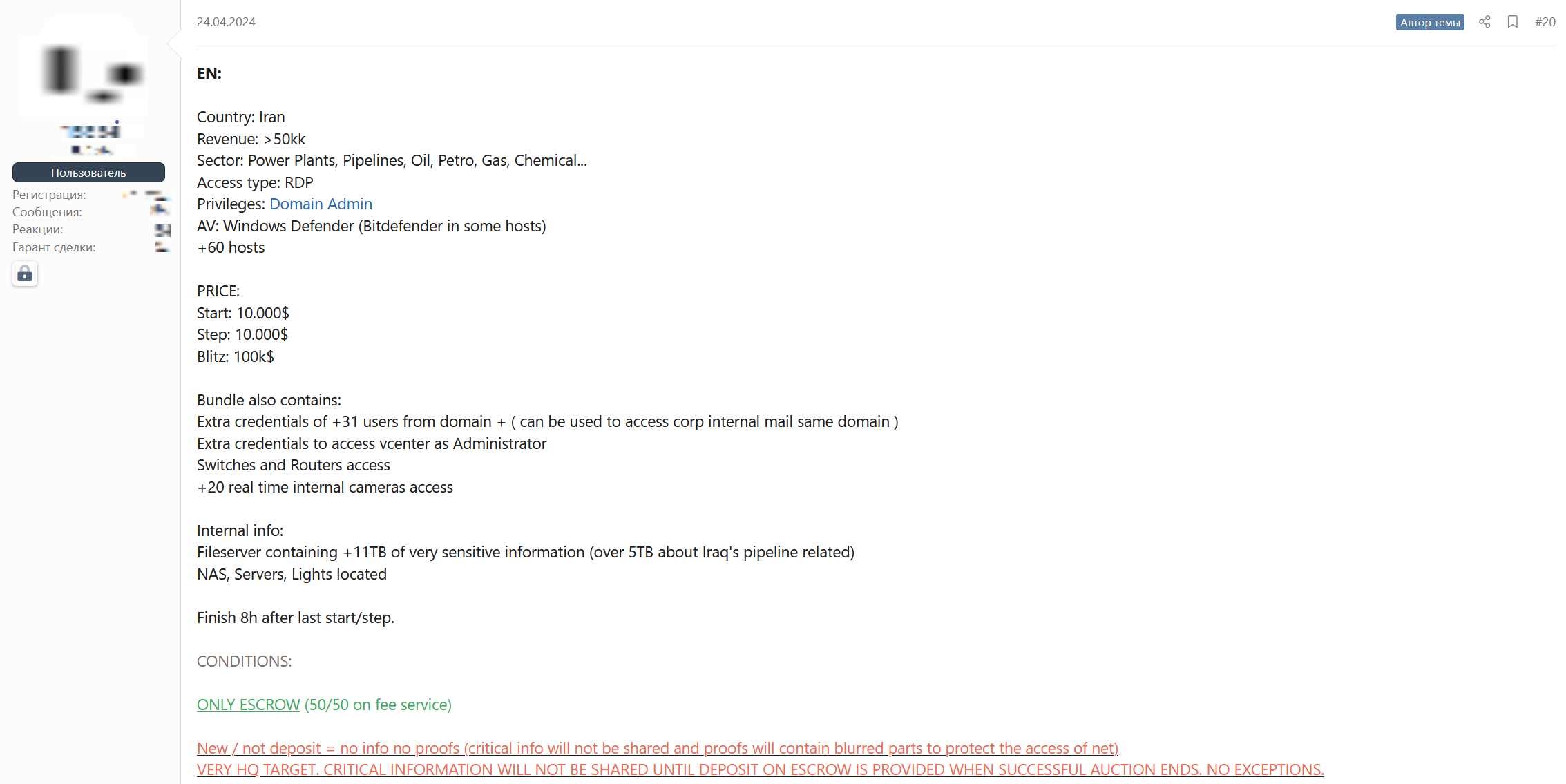
Core activity disruption
In 2023, 48% of cyberattacks on manufacturing companies disrupted production processes. By Q1–Q3 2024, this figure fell to 33%, suggesting a shift in attacker strategies. Cybercriminals are increasingly deploying remote access trojans (RATs) and spyware instead of ransomware, which was a major driver of disruptions in previous years. Despite this decline, the impact of production-targeted attacks remains significant. In February 2024, a cyberattack on German battery manufacturer VARTA AG disrupted operations at five production units.
How to protect yourself
Manufacturing companies face a host of security vulnerabilities, from unauthorized communication channels and unprotected access points to poorly segmented networks and insecure remote connections. Default passwords and outdated operating systems further weaken defenses, while limited hardware resources and proprietary technologies make it nearly impossible to deploy modern security tools across all devices. Additionally, businesses frequently struggle to maintain an accurate inventory of devices and their status, as performing inventories and tracking changes in IT infrastructure is a complex task.
In a 2023 Claroty survey, the top initiatives planned by manufacturing companies for 2024 were risk assessments (43%), asset management improvements (40%), and vulnerability management programs (39%).
Result-driven cybersecurity for identifying and preventing non-tolerable events
Non-tolerable events are events that result from a cyberattack and prevent an organization from achieving its operational and/or strategic goals or lead to a significant disruption of its core business.
To build result-driven cybersecurity, organizations must prepare a comprehensive list of non-tolerable events and identify potential attack paths that could lead to them. This method has already been applied effectively in the transportation sector by listing critical outcomes and addressing potential triggers. The key steps include preparing a list of non-tolerable events and identifying potential attack paths a malicious actor might take to trigger these events.
The process begins with identifying non-tolerable consequences specific to each industry. In the power sector, these may include disruptions to normal energy operations, grid or generator disconnections, malfunctions in automated systems that lead to shutdowns or outages, and interruptions in logistics chains.
For manufacturing companies, non-tolerable events often involve technological process disruptions, operational downtime, breaches of confidential information, unauthorized financial withdrawals, data corruption or loss, and the exploitation of computing resources for attacks on other organizations.
Positive Technologies' surveys on IoT cybersecurity reveal that 70% of respondents consider disruptions to IIoT-based processes their top concern. Other significant risks include downtime in IIoT platform solutions, data distortion within IIoT infrastructures, and loss of control over IIoT devices and processes. Additional threats include loss of control over IIoT-based technological processes and the management of IIoT devices; device compromise or failure; data leaks; and the use of IIoT systems as entry points for attacks on internal IT networks.
Asset inventory and vulnerability management
Protecting IoT devices starts with knowing exactly what is connected to your network and understanding their roles. Effective asset management forms the backbone of operational resilience, but this is often easier said than done in industrial environments. Proprietary protocols, which are frequently incompatible with standard inventory tools, add layers of complexity to the process. Previously, we shared recommendations on mitigating vulnerabilities and avoiding non-tolerable events. A well-maintained inventory provides visibility into the network, allowing organizations to identify vulnerabilities and address them proactively.
Equally critical is protecting end devices. Preventing public access to online assets and enforcing a strict password policy, including the immediate replacement of default credentials, are straightforward yet effective measures. These steps significantly reduce the risk of breaches by low-skilled attackers attempting to exploit exposed endpoints.
Bug bounty programs
Bug bounty programs have become a cornerstone of effective vulnerability management. These initiatives reward independent security researchers for identifying vulnerabilities in a company's software, systems, or infrastructure. By leveraging the expertise of the global cybersecurity community, organizations can dramatically improve their vulnerability detection and remediation efforts.
Leading industrial and technology companies are increasingly turning to bug bounty programs as a proactive measure to strengthen their security. Siemens, a global leader in manufacturing automation and industrial products, offers a notable example. The Siemens Bug Bounty Program engages independent researchers to uncover vulnerabilities across a wide range of products, solutions, and infrastructure components. The program accepts vulnerabilities regardless of product lifecycle status or service contracts, making it a comprehensive effort to identify and mitigate potential threats.
Looking ahead, bug bounty programs may evolve beyond traditional models. Emerging programs could incentivize ethical hackers not only to identify vulnerabilities but also to simulate the execution of non-tolerable events
Securing hardware and software supply chains
The supply chain for smart technologies introduces unique risks that organizations must manage proactively. These risks encompass both hardware and software components, requiring companies to adopt a comprehensive approach to security. Partnering with trusted suppliers is critical, but this responsibility doesn't rest solely on the end user. Vendors must also uphold security-by-design principles, embedding robust protections throughout the design and development process.
Securing platform solutions begins with a detailed analysis of how components are delivered, integrated, and assembled. Each step in this chain presents potential vulnerabilities that must be identified and addressed. Equally vital is understanding how devices store, transmit, and process data. Ensuring robust encryption and secure data handling practices at every stage minimizes exposure to potential breaches and attacks.
Network segmentation
Historically, industrial systems relied on physical separation and isolation to secure vulnerable network components. Complex system designs and restrictive access rules further limited attack opportunities. Today, proper network segmentation builds on these principles, preventing the lateral movement of cyberattacks and stopping hackers from spreading through a system.
Network segmentation divides a network into smaller, more secure sections, improving both performance and security. By isolating network segments, malware in one area cannot infiltrate others, limiting the potential damage. Segmentation also protects devices without built-in security features from malicious traffic. For example, hospital infusion pumps, which often lack advanced defenses, can be secured through proper network segmentation.
Even with segmented networks, regular software updates remain critical to safeguarding industrial systems. Analysts at SektorCERT reported that the critical vulnerability CVE-2023-28771 in Zyxel firewalls was exploited to attack 22 energy companies in Denmark. This incident has been described as the most extensive cyberattack in Denmark's history.
Staff education
Even in isolated industrial networks, cybercriminals can penetrate industrial control systems by exploiting internal access points.
Malware typically infiltrates devices through malicious email links, infected attachments, downloaded files, or hardware and software vulnerabilities. In the first three quarters of 2024, ransomware made up 53% of malware attacks on the industrial sector, with email attachments as the leading delivery method.
Figure 22. Malware delivery methods (percentage of successful malware attacks, Q1–Q3 2024)
Protecting systems from malicious software requires a multifaceted approach. Employees must be trained to recognize phishing messages and stay informed about evolving hacking techniques. Specialized tools, such as sandboxes, should be deployed to analyze and block suspicious files before they can cause harm.
Industry 4.0 and smart manufacturing
Industry 4.0 integrates advanced digital technologies like IoT, AI, and big data into manufacturing and industrial processes. This approach enhances productivity, improves efficiency, and supports smarter decision-making across manufacturing and supply chain operations.
At its core is the Industrial Internet of Things (IIoT), often used interchangeably with Industry 4.0. The IIoT drives process optimization and minimizes equipment downtime by leveraging sensors and RFID tags. These devices provide real-time data on environmental conditions, as well as the status, performance, and location of physical assets.
Industrial process autopilot as the leading trend
Industrial leaders are moving toward fully automating production and business processes to create truly "smart" operations. Smart manufacturing harnesses technologies like AI, cloud computing, and IIoT to improve efficiency and flexibility in production. The National Institute of Standards and Technology (NIST) defines it as a fully integrated, collaborative process where manufacturing systems respond in real time to shifting demands and conditions in factories, supply chains, and customer needs.
This trend extends beyond manufacturing, with the transportation sector also embracing smart processes. In our analysis of cyberthreats in transportation, we examined the "smart port" concept, which integrates IT systems into industrial and business processes to improve operations. Demand for advanced technologies in transportation and logistics continues to grow, driven by self-driving vehicles, robotic automation, and the need to track passenger and cargo movements, locations, and driver performance. The IoT now plays a critical role across transportation infrastructure, spanning road management, seaports, airport terminals, warehouses, and railways. In the railway industry, IoT systems monitor rolling stock, tracking the movement and location of passenger cars, freight cars, containers, locomotives, and electric trains. Sensors gather real-time data on technical conditions, enabling predictive maintenance, preventing breakdowns, and reducing repair costs. These systems ensure a proactive approach that enhances safety, boosts efficiency, and reduces operational expenses.
Artificial intelligence integration
AI technologies are a top priority for industrial leaders, driving innovation in IoT systems. Key 2024 trends include the rise of Generative AI (GenAI) and Edge AI, both transforming manufacturing processes. The booming market for GenAI has progressed from experimentation to production, with examples like the Siemens Industrial Copilot showcasing its capabilities.
Edge AI has also gained prominence as a critical tool for improving security, precision, and efficiency in IoT applications. By processing data locally, it minimizes latency and enables real-time decision-making, making it indispensable in industrial operations.
Optimizing technological processes with predictive analytics
The integration of IoT sensors and data analytics into manufacturing has revolutionized equipment monitoring. Predictive maintenance algorithms identify potential failures before they occur, enabling proactive measures that can cut downtime by up to 50% and extend asset life cycles by up to 40%.
Motor Oil, a leading oil refiner in Greece and the Eastern Mediterranean, demonstrates the value of predictive analytics. By analyzing historical sensor data, the company achieved over 77% accuracy in predicting abnormal events 20–120 hours in advance, enabling effective failure prevention.
Similarly, the Russian chemical company Kazanorgsintez (KOS) enhanced equipment reliability with IIoT integration. KOS deployed over 1,700 wireless IIoT sensors across its industrial site to monitor parameters such as vibration, temperature, pressure, gas levels, and tank levels. The company expects these solutions to generate approximately one million dollars annually starting in 2024 by reducing downtime and improving operational efficiency.
Digital twins
Digital twins are a cutting-edge technology that creates virtual replicas of real-world physical objects, capturing their condition and performance. These digital models enable advanced analytics, optimizing production and operational processes across industries.
Digital twins have diverse applications, including:
- Verifying the functionality of IoT systems under specific conditions, such as software versions, configuration parameters, or untested operating modes
- Testing hypotheses about IoT system behavior in artificially created scenarios
- Evaluating the effectiveness of functional and information security measures
- Conducting cyber exercises
In the oil and gas industry, digital twins solve complex challenges such as determining production potential, planning operations, and monitoring hydrocarbon output. One notable example is the Vatyegan field digital model, launched by Lukoil as part of its Intelligent Field project. This initiative created digital twins for over 3,000 wells, 12 development sites, and the entire production chain, making it the most extensive digital model of an oil field in Russia.
Metallurgical companies are also leveraging digital mines to optimize raw material extraction and processing. For instance, the Pipe Metallurgical Company increased profits by nearly five million dollars by implementing digital twins for rolling mills at its Volzhsky and Seversky plants.
As digital twins become more widespread, they are likely to attract cybercriminal attention. These virtual models can expose critical information about a company's systems and processes, which attackers could resell, use in ransom demands, or exploit to train for and launch sophisticated attacks.
Conclusions
Today, advanced all-in-one solutions for IIoT ecosystems are being developed at an unprecedented pace. A key challenge for manufacturers is the lack of standardization across IIoT devices and software solutions. In response to the growing threat of cyberattacks, some countries are enacting laws and initiatives aimed at securing not only IoT devices and the data they process but also the broader systems connected to them.
The integration of IT technologies into OT infrastructure is driving the evolution of platform solutions and cybersecurity products. To tackle emerging threats, manufacturing companies require sophisticated security tools that support asset inventory management and deliver robust protection against cyberattacks.
About this report
This report contains information on current global cybersecurity threats based on Positive Technologies own expertise, investigations, studies of the darknet markets, and reputable sources.
This report considers each mass attack (for example, phishing emails sent to multiple addresses) as one incident, not several. We assume that most cyberattacks are not made public due to reputational risks. As a consequence, even companies specializing in incident investigation and analysis of hacker group activity are unable to calculate the precise number of threats. For explanations of terms used in this report, please refer to the Positive Technologies glossary.