
Darya Lavrova
Senior Analyst, International Analytics Group, PT Cyber Analytics

Darya Lavrova
Senior Analyst, International Analytics Group, PT Cyber Analytics
Despite difficult economic and geopolitical conditions, the Islamic Republic of Iran (hereafter, Iran) is implementing its digital development strategy and strengthening technological sovereignty. The country aims to become a technological leader in the Middle East. This includes the digitalization of financial assets, healthcare, and manufacturing, as well as the development of a wide range of digital services, software solutions, and platforms. This expansion increases the attack surface, making Iran's digital infrastructure more attractive to cybercriminals whose goals may range from financial gain to the disruption of key facilities across sectors.
This study analyzes Iran's current digital profile, with emphasis on changes from H2 2024 through H1 2025. It also examines the country's cyberthreat environment, with particular attention to the period of heightened geopolitical tension in June 2025.
Key research objectives:
Analyze Iran's digital environment for H2 2024–H1 2025, identifying key areas of development.
Map the country's cybersecurity threat environment for the same period, based on open-source data, dark web forums, and Telegram channels.
Examine how the period of heightened geopolitical tensions was reflected in cyberspace.
Identify cyberthreat trends characteristic of the state and outline their likely evolution.
Propose recommendations to improve the country's cybersecurity posture.
To describe Iran's threat environment, data from open sources was combined with information obtained from the six most popular dark web forums, more than 300 Telegram channels, and platforms that aggregate data on website defacements and ransomware attacks. The selection included the largest multilingual dark web sites covering various topics. The study covered the period from July 1, 2024, to June 30, 2025.
The following categories were analyzed:
Database: leaks containing personal data, user credentials, or confidential corporate documents.
Access: credentials enabling unauthorized access to devices or services in a company's infrastructure.
Vulnerability: publicly disclosed vulnerabilities and exploits.
Ransomware: posts by hacker groups about successful ransomware attacks.
DDoS: posts by hacker groups about successful DDoS attacks.
Defacement: announcements of successful attacks that altered website homepages.
A comprehensive analysis of public data and dark web data enables us to draw conclusions about current cybersecurity issues, as well as emerging and observed trends in cyberthreats. Examining the country's cybersecurity posture and digital development allows us to assess their influence on each other and to evaluate the nature of future threats and the feasibility of countermeasures.
The data and findings presented in this report are based on Positive Technologies own expertise and analysis of publicly available resources, including government and international publications, research papers, and industry reports.
We assume that most cyberattacks are not made public due to reputational risks. As a result, even companies specializing in incident investigation and the analysis of hacker group activity cannot quantify the precise number of threats. This research aims to draw the attention of organizations and individuals concerned with information security to the key motives and methods of cyberattacks and to highlight major trends in the evolving cyberthreat environment.
This report treats each mass attack (for example, a phishing email sent to multiple recipients) as one incident rather than several. For explanations of terms used in this report, see the Positive Technologies glossary.
Our incident database is updated regularly. Some incidents may become public well after the actual time of the attack, so the data in this study are current as of the publication date.
Iran's digital environment shows the state's ability to adapt by using innovative, high-tech solutions to replace global digital platforms, software, and hardware. It also reflects the state's ambition to achieve a leading technological position in the region. The foundations of Iran's digital development are the pursuit of technological sovereignty, expansion of cryptocurrency infrastructure, growth of a startup ecosystem (particularly in technology), and significant investment in the research and development of artificial intelligence.
The most active steps in developing the country's digital profile during the review period concerned artificial intelligence, including measures to expand the talent pool and build technological infrastructure.
In June 2025, Iran's cyberthreat environment was largely shaped by heightened geopolitical tensions.
According to open-source data, finance (30%), transport (17%), and manufacturing (13%) accounted for the largest share of successful cyberattacks. These sectors are attractive to attackers due to the potential for financial gain from monetizing large volumes of confidential data and the possibility of causing reputational damage on a national scale because of their strategic importance.
In June 2025, a series of cyberattacks aimed at disrupting key infrastructure assets and influencing public opinion—by disabling major media outlets and spreading misinformation on social media—marked an escalation in geopolitical conflict. Based on publicly available data, the financial sector was the target of most successful attacks (83%). This suggests an intent to undermine public confidence in digital financial infrastructure by suspending payment processes within the country, causing significant damage to Iran's economy and the defense industry by limiting the use of both conventional currencies and cryptocurrencies for trade and the financing of military programs.
Cyberattacks on media organizations often accompany escalations in political tension because media shape public understanding of events. Consequently, 53% of dark web posts in June concerned media, primarily declarations about DDoS attacks.
As in H2 2023–H1 2024, the most common method of attack remained the use of malicious software. However, its share decreased by 15 percentage points, from 63% in H2 2023–H1 2024 to 48% in H2 2024–H1 2025. This decline was presumably influenced by events in June, when cybercriminals sought to disrupt large industrial facilities by launching DDoS attacks and defacing websites. The most frequently used malware types also shifted: ransomware replaced the wipers that prevailed in the same period last year, with attackers using ransomware in 80% of cases.
As in the previous period, the predominant consequence of cyberattacks on Iranian organizations (61% of all consequences) during the review period remains the leakage of confidential information. However, viewed in six-month intervals, the statistics shifted in H1 2025. Disruption of core organization activities became a key issue, accompanied by an increase in cases affecting state interests. This was likely linked to the deterioration of foreign policy relations and hacktivist1 cyberattacks.
During periods of heightened geopolitical tension, cyberattacks were primarily aimed at disrupting key infrastructure and influencing public opinion. In the first case, methods included DDoS attacks, website defacements, and the exploitation of vulnerabilities to penetrate company infrastructure. In the second case, attackers used artificial intelligence to generate deepfakes and distribute them widely on social networks.
The largest share of dark web posts came from the Unknowns cyberteam (60%), with Predatory Sparrow and the Islamic Hacker Army accounting for 9% each, and Anonymous Syria Hackers accounting for 8%. According to dark web data, no activity by these groups was recorded in the other quarters of the review period (Q3 and Q4 of 2024, and Q1 of 2025). This suggests their activity emerges during escalations in interstate conflict.
Forecasts regarding future cyberthreats to Iran point to an increase in the number of attacks on the finance and transport sectors, given their importance to the state. Successful attacks on these sectors have exposed vulnerable points, suggesting that similar attempts may follow. For example, attackers may focus on centralized systems that provide access to multiple client companies simultaneously. Information about successful attacks may also stimulate interest in targets within the same industry. Cyberattacks using malware are expected to prevail, with ransomware predicted to be used more frequently than wipers. Additionally, there is a growing trend toward the implementation of artificial intelligence in cyberattacks, which is particularly concerning given its effectiveness in social engineering schemes.
1 Hacktivists are cybercriminals who carry out attacks for political, ideological or personal reasons, rather than for financial gain. They may aim to destabilize a country's internal state, among other things.
The formation of a country's digital profile is influenced by internal objectives such as economic development, digitizing key industries, and fostering innovation, as well as foreign policy goals such as ensuring digital sovereignty.
Iran's digital environment shows the state's ability to adapt by using innovative, high-tech solutions to replace global digital platforms, software, and hardware. It also reflects an ambition to be a technological leader in the region. On average, Iran's digital sector has grown faster than other sectors of the economy. Currently, the digital economy currently accounts for almost 7.4% of GDP, and the government plans to increase this to 15% by 2028.
The state is pursuing a policy to make Iran a key hub of the digital economy, using legislative measures and targeted initiatives to achieve this. For example, the country recently enacted the "Law on Production Financing and Infrastructure," which recognizes intangible assets, including intellectual property and digital products, as legitimate sources of financial support for businesses. The government is also working to improve digital literacy and expand the number of IT specialists. A notable initiative is a project launched by the Ministry of Information and Communications Technology to engage the public. Under this program, 500,000 residents will have the opportunity to develop digital skills. The initiative is being implemented in collaboration with the Iranian Organization for Vocational and Technical Training (IRTVTO) and the private sector.
Key characteristics of Iran's digital landscape today:
The development of the digital sector is largely driven by the growth of local high-tech companies. This report analyzes Iran's startup ecosystem and AI innovations from H2 2024 to H1 2025.
2 A strategic imperative refers to a critical, non-negotiable priority that an organization must act on to remain competitive, future-ready, or successful. It's not just a goal or an initiative, it's a focused action area that directly supports the long-term vision and sustainability of the business.
Iran seeks to develop its digital economy by strengthening economic ties with Gulf countries and creating a wide range of investment opportunities for businesses. Its startup ecosystem is growing rapidly and now includes more than 5,000 startups, many specializing in e-commerce, software-as-a-service (SaaS[1]) development, financial technology (fintech) solutions, and other digital services. This growth aligns with Iran's nationwide digitalization policy and the adoption of local digital solutions and platforms.
3 SaaS (Software as a Service) solutions are cloud applications available to users via the Internet on a subscription basis.
The development of Iran's startup ecosystem is influenced by key economic, demographic, and financial factors. Specifically, the ecosystem is shaped by:
1. State incentives for technological entrepreneurship. The government exempts innovation-focused startups from corporate tax and allocates grants for research and development (R&D4). It also provides subsidized5 loans and exclusive access to government-supported incubators and accelerators. Innovation is further supported by the creation of science and technology parks, of which there are currently more than 50 in Iran. For example, Iran's largest technology park has attracted more than 400 startups and over $500 million in investment.
2. High demand for technology solutions combined with the availability of qualified specialists. Iran's population provides a strong consumer base focused on digital solutions. This is largely due to the population's youth; at the beginning of 2025, the average age was about34. At the same time, the country has a large number of STEM6 specialists, which is growing by 500,000 people annually.
3. Sustainable financing for early-stage startups through multiple channels: venture capital (Iranian venture capitalists such as Sarava, Shenasa, Fanap, and Kian Capital invest in fast-growing local startups), corporate financing (large companies such as Digikala and Snapp acquire startups, expanding their operations), and business angels7.
4 R&D (Research and Development) refers to systematic, creative, and innovative activities undertaken to discover new knowledge, improve existing products, processes, or services, and generate strategic advantages for companies, industries, or nations.
5 Subsidized loan — a loan provided on preferential terms with an interest rate lower than normal market rates.
6 STEM disciplines — a group of educational fields combining science, technology, engineering, and mathematics (STEM), which are studied not in isolation but in conjunction with each other to develop critical thinking skills, problem solving, and the practical application of knowledge in today's technological world. Engineering, Mathematics), which are studied not in isolation but in relation to each other in order to develop critical thinking skills, problem solving, and the practical application of knowledge in today's technology-driven world.
7 A business angel is a private individual, often with a high net-worth, and usually with business experience, who directly invests part of their assets in new and growing private businesses.
Key areas of startup activity during the review period include fintech, e-commerce, AI, medicine, and biotechnology.
The AI startup ecosystem is growing rapidly. By 2025, Iran was the second-ranked country in the region by the number of AI solution developers and the fourth-ranked by the number of companies creating intelligent solutions. This growth is partly due to government initiatives. In early 2025, the government allocated about $115 million from the national budget to fund AI development. Key areas include research and development, particularly the modernization of computing infrastructure and support for strategic projects. Promising areas for startups include intelligent business automation tools and SaaS platforms offering personalized training in modern technologies.
Fintech innovation reflects Iran's unique economic environment, where there is demand for local digital payment systems, online banking solutions, and alternative financial services. Investment in this area is also driven by high mobile penetration. At the start of 2025, the country had 152 million active mobile connections, representing 166% of the total population, which is increasing demand for secure and efficient digital payment solutions.
Eighty-five percent of the country's financial transactions are now conducted digitally, prompting banks to implement fintech innovations. E-commerce startups are targeting the country's young population, many of whom are turning to online shopping. More than 9 million Iranians use online banking and digital wallets every day. Specialized e-commerce sites are being developed to meet specific consumer demands and to provide effective delivery and logistics services.
Iran's advanced medical sector offers opportunities for technology companies developing HealthTech (digital healthcare) solutions. Startups are focusing on medical diagnostics, telemedicine services, and biotechnological innovations. Iranian biotech products have also become strategic commodities in recent years due to high demand from neighboring countries seeking affordable alternatives to Western pharmaceuticals.
Consequently, Iran's startup ecosystem is developing rapidly and is highly technology-focused.
In June 2024, the Supreme Council of the Cultural Revolution approved the "National Document on Artificial Intelligence," a strategic plan for developing AI in Iran. The document was published in the country's official newspaper in August 2024. Its key provisions set the following strategic goals:
teach the population relevant skills
increase the share of scientific and technological products produced in this field
improve the country's competitiveness in domestic and global technology markets
cooperate with friendly countries in science and technology
use AI to preserve the country's digital sovereignty
The National AI Plan, approved by the Iranian parliament in May 2025, complements this measure by aiming to expand the country's human resources and develop its technological infrastructure. Substantial investments in AI by regional competitors, Saudi Arabia and the UAE, and their collaborations with Western technology firms may have served as a catalyst for adopting the plan.
One major initiative is a flagship program to teach AI to one million schoolchildren aged 7 to 15, beginning in the 2025–26 academic year. AI-related courses for higher education students will be expanded, and non-computer science programs will be adjusted so that every student graduates with an understanding of AI tools and ethics. These changes affect teachers as well: Iran plans to train 100,000 AI teachers in 2025. Iran has adapted its educational programs based on the experience of China and Russia with AI technology, incorporating elements of their curricula and educational models into the country's education system.
Iran has a strong academic foundation in AI. Its leading universities—Sharif University of Technology, University of Tehran, Amirkabir University of Technology, and Iran University of Science and Technology—are actively engaged in AI research. In January 2025, Tehran hosted an international conference on "AI and the future civilization," attended by representatives from more than 20 Chinese universities and 30 leading global institutions (including invited experts from China, Italy, Russia, Malaysia, and Singapore).
Thirteen of the country's universities are also participating in the "Smart Assistants for the Government and Ministers" project, which uses AI to improve decision-making and administrative processes.
The key technological achievement in H2 2024–H1 2025 was Iran's development of a national open-source AI platform. The prototype was first demonstrated publicly on 15 March 2025. The project is presented as a step toward "technological justice," ensuring broad access to AI. The platform does not rely on foreign APIs. It provides AI services, including language models and data analytics, for use by developers, companies, and government agencies on Iran's national network.
According to the platform's roadmap for 2025–2026, the creators will iteratively improve the system.
In spring 2025, the team began internal testing and optimization of AI solutions.
By mid-2025, selected scientists and knowledge-based companies received limited access for beta testing and validation.
The public beta release is scheduled for September 2025, with the final stable version expected in March 2026.
The platform was developed through an open competition involving Iranian universities and 38 knowledge-based companies. This demonstrates the integration of practical commercial experience with scientific innovation in Iran.
The state's pursuit of technological sovereignty and leadership in AI is also reflected in infrastructure projects. By 2027, the government plans to build its first specialized AI Park in Tehran to showcase developments and provide publicly available intelligent services.
Iran continues to develop and improve technological infrastructure while raising digital literacy across the population. The focus on AI reflects its broad applicability, from digitizing leading industries to strengthening defenses against cyberthreats. The overarching goal is to help preserve national sovereignty, which is especially relevant amid heightened geopolitical tensions.
Iran's digital profile and development strategies are designed to counter both existing and emerging cyberthreats. The next section examines the country's cyberthreat environment over the selected period, with particular attention to June 2025, a time of elevated geopolitical tension that also affected cyberspace.
During this period, financial organizations were the most frequently targeted (30%), followed by transport companies (17%) and industrial companies (13%). These sectors are of strategic importance to the state. Successful attacks on major infrastructure could allow hacktivists and politically motivated actors to disrupt internal processes. Financial and industrial organizations also store significant volumes of sensitive information, including credentials, payment card data, personal data, and trade secrets. Access to this data can generate financial gain for cybercriminals. Non-tolerable events8 that halt financial transactions, disrupt logistics, or cause production downtime would negatively affect the country's economy. If attackers were to take control of industrial facilities, the result could be a technological disaster. Taken together, these factors make the financial sector an attractive target for cybercriminals.
8 A non-tolerable event is an event that results from a cyberattack and prevents an organization from achieving its operational and strategic goals or leads to a significant disruption of its core business.
Financial institutions are important for any country, but they are particularly significant for Iran, given that sanctions have complicated its trade and economic relations. Iran's financial system uses both conventional currencies and cryptocurrencies, enabling the country to stabilize its economic situation. Although domestic cryptocurrency payments are prohibited, digital assets may be used to import sanctioned goods, including medical equipment, and for operations in the oil sector. However, all receipts must pass through the Central Bank's channels at official exchange rates.
A comparative analysis of the half-years (H2 2024 and H1 2025) showed that financial organizations experienced the largest increase in successful cyberattacks (36 percentage points), followed by the telecommunications and media sectors, each up by 8 percentage points.
The main changes occurred in June 2025 due to geopolitical tensions, when cybercriminals shifted focus from financial gain to undermining public confidence in the country's digital infrastructure.
The financial sector was hit hardest, suggesting an intent to paralyze payment processes by disabling key banks and cryptocurrency institutions and services, putting the economy under strain.
Attacks on telecommunications infrastructure disrupt other industries that rely on data networks to operate. These include the financial sector, which depends on functioning e-commerce processes; the public sector, which provides digital services to citizens; and manufacturing, where facilities require continuous monitoring and control of technological processes. Disrupted communications also fuel public discontent and can destabilize domestic politics.
Cyberattacks on media organizations are often associated with external and internal political conflicts, as reflected in H1 2025 data. In these attacks, malicious actors aim to shape negative public opinion by disrupting major state media outlets and then spreading misinformation via alternative channels.
Cybercriminal activity targeting the media is especially visible in dark web data: posts in this category lead, accounting for 13% of the total. Media organizations enjoy broad public trust, making them attractive targets for hacktivists and novice attackers. Some posts are politically motivated; others aim to showcase newcomer technical capabilities. Such posts tend to emphasize the fact of a successful attack on a media organization rather than the scale of the damage.
The next section examines the three industries with the highest number of victims—finance, transport, and manufacturing—based on public cases and dark web data.
Any disruption in financial services harms the reputation and profits of institutions. Attacks on large organizations can create problems at the state level. The impact attracts both hacktivists, who commonly use DDoS attacks, and ransomware operators.
For hacktivists and foreign pro-government groups, financial institutions are a strategic target. Disrupting their operations—including cryptocurrency organizations—can damage the country's standing, affecting trade, economic relations, and defense financing.
Dark web analysis shows the financial sector among the top three categories of posts, with an 8% share. Posts about financial organizations are common on shadow markets because these platforms attract audiences seeking financial gain and status in the cybercriminal community. Trading companies and financial institutions store large volumes of confidential information (trade secrets, customer personal data, and more) that can be monetized if stolen.
A comparison of H2 2024 and H1 2025 shows a significant increase in successful attacks on financial organizations. This reflects the participation of both profit-motivated criminals stealing and selling confidential data and hacktivists or pro-government groups from other countries seeking to showcase vulnerabilities in Iran's strategic financial sector. Successful attacks on banks, cryptocurrency exchanges, and other firms can disrupt services for individuals and businesses and potentially destabilize the national currency. Compromising financial companies can also enable follow-on attacks on their contractors and information service providers, expanding the attack surface.
The first major incident in the review period occurred in August 2024. It was reportedly carried out by the irleaks group, known for prior hacks of Iranian companies. The attack, delivered through an Iranian digital infrastructure provider serving a large share of the banking sector, affected up to 20 banks. The attackers initially demanded a $10 million cryptocurrency ransom; the final payment to restore services was just over $3 million. The incident highlights the risk of centralizing critical services and the need to protect central infrastructure; in this case, the provider became the weak link, exposing multiple financial entities at once.
Not all attacks on the financial industry result in direct monetary losses. Some focus on reputational harm or effects on defense capability. In March 2025, one of Iran's largest banks—reported on social media to have close ties to the military and security forces—was attacked by the Codebreakers group. More than 12 TB of data was leaked, including financial and identification information on 42 million customers, as well as residential details.
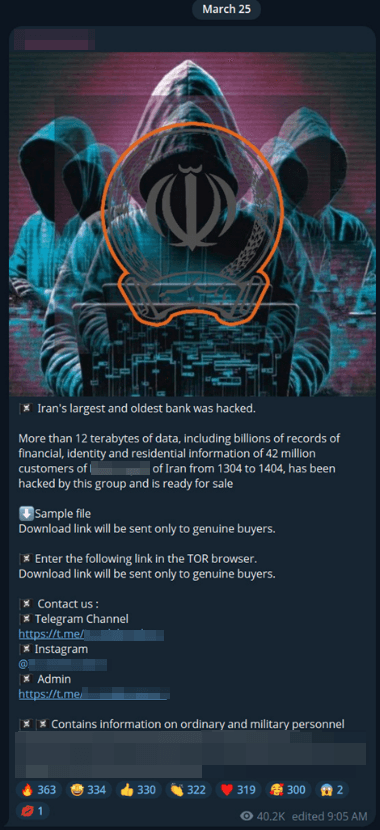
Experts note that this incident appears ideologically motivated rather than financial. The following factors support this view:
the unrealistically large ransom demand of $42 million.
the dissemination of information about the successful attack in Persian, indicating a regional focus and the likely motivation of attackers.
the use of atypical channels for dissemination, such as WhatsApp9 and Instagram10. Given that the latter is one of the most popular platforms in Iran, the attackers likely sought to reach an Iranian audience.
9 A product from Meta, a company that has been designated as an extremist organization and banned in Russia under Russian law.
10 A product from Meta, a company that has been designated as an extremist organization and banned in Russia under Russian law.
Therefore, this incident was most likely aimed at attracting the attention of the Iranian public and undermining trust in state institutions.
In Q2 2025, cyberattacks also affected a significant number of Iranian financial organizations, but the primary goal of attackers appears to have been the destabilization of Iran's financial infrastructure rather than direct financial gain. This pattern is consistent with attacks aimed at disabling key industry facilities in the second quarter.
Serious disruptions in the transport sector were observed in October 2024 following cyberattacks. On October 12, attacks disrupted the work of the Iranian government.
In March 2025, the Lab Dookhtegan group—known for previous attacks against Iran's military and intelligence services—carried out an operation affecting 116 oil tankers simultaneously. These vessels belonged to major Iranian companies that own a range of tankers, landing craft, and container ships. The attackers claimed to have disrupted communications between these vessels, cutting off contact between crews and the outside world, including ports. This endangered crew safety and increased risks to maritime navigation for the affected ships and others in nearby waters. The attack also reportedly had a negative impact on the sale of Iranian oil transported by tankers. Furthermore, the attack allegedly had a negative impact on the sale of Iranian oil transported by tankers.
Although the group did not publicly disclose the tactics, techniques, and procedures used, it is believed that Lab Dookhtegan exploited vulnerabilities in the maritime satellite communication systems on which the ships depend. According to the group, they gained complete control of the communication system through privilege escalation, accessed ship networks, and gained the ability to execute malicious code remotely. A screenshot published by the group shows successful remote access via SSH with administrator (root) privileges.
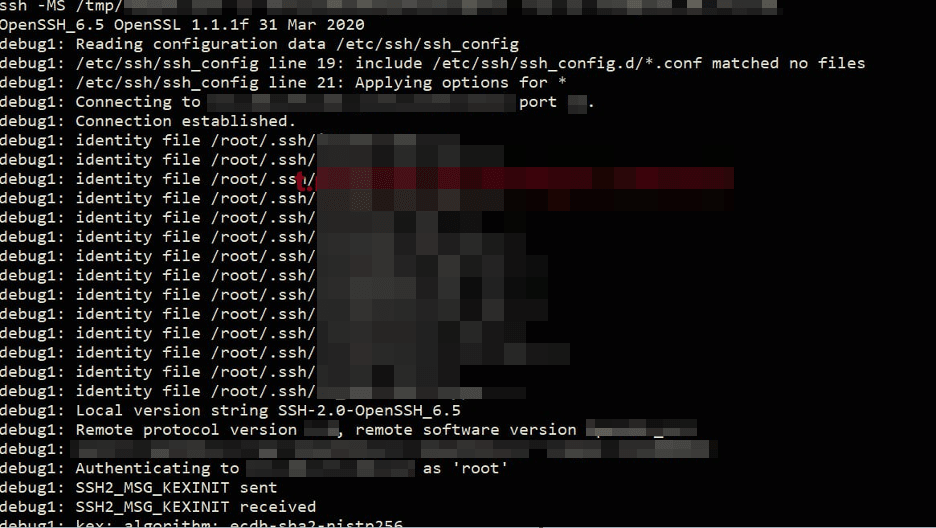
Experts note that the operation was likely highly coordinated and automated, as indicated by malware delivery to 116 ships simultaneously.
The successful execution of such attacks highlights the vulnerability of maritime facilities to information influences and demonstrates the potential impact of cyber operations on the real economy. The transport sector is highly sensitive to cyberattacks because it underpins supply chains essential to trade and economic relations and provides regular passenger transport. Attacks on transport facilities can cause financial and reputational damage due to logistical disruption, as well as casualties.
Open-source analysis indicates that in most cases (67%), cyberattacks on industrial organizations during the review period led to the leakage of confidential information as a result of ransomware. Such attacks are popular because criminals can demand a ransom or sell leaked confidential data (for example, trade secrets). Many industrial organizations—particularly oil, gas, and petrochemical companies in Iran—carry out strategically significant activities with major social and economic impact. Successful ransomware attacks on such companies could expose or irretrievably destroy confidential information, given the observed trend of using ransomware as wiper malware. They can also cause significant financial losses by halting production and damage the state's reputation if exports are affected. For these reasons, ransomware attacks are also carried out by hacktivists and pro-government groups from other countries.
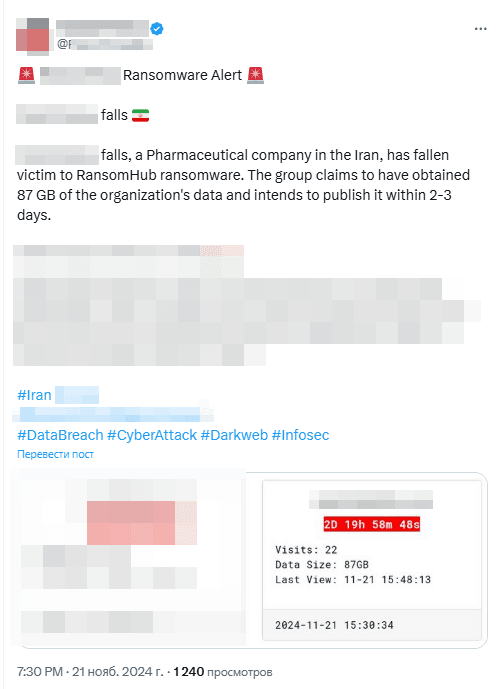
Victims include Iranian energy and pharmaceutical companies, manufacturers of welding materials and automotive electronics, and firms in the ceramics industry. For instance, 87 GB of data belonging to an Iranian pharmaceutical company was obtained by RansomHub, a group that develops ransomware and operates on a ransomware-as-a-service model with a distinctive prepaid scheme for partners.
Another way to monetize attacks on industrial organizations is to sell access to the infrastructure of breached companies. Depending on the type of access purchased (RDP, VPN, etc.), attackers can carry out various operations, including influencing internal technological processes across the targeted organization.
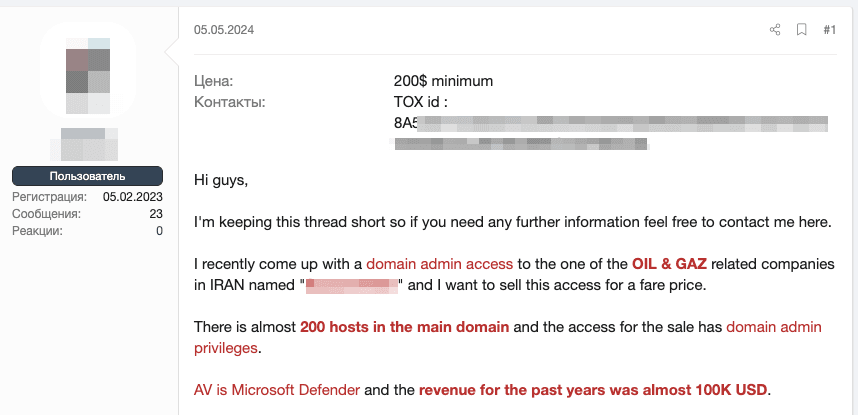
Domain administrator access is the highest level of privilege in a domain environment. Obtaining it gives an attacker near-complete control over resources, users, and security settings. Despite the significant number of hosts in the domain (200 computers), the company's revenue is relatively low at approximately $100,000, which may explain the low cost of access (the seller's minimum price is $200).
Larger industrial organizations have also been targeted. In April 2024, a large company in the oil, gas, and energy sectors with revenues of around $50 million was compromised. RDP access to its infrastructure (with domain administrator rights) was offered at a much higher price, starting at $10,000. The offer also included:
credentials for 31 domain users
credentials for administrator access to VMware vCenter Server
access to network equipment
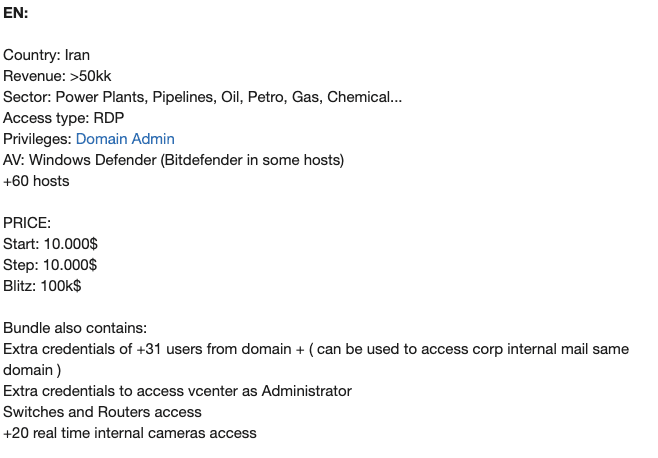
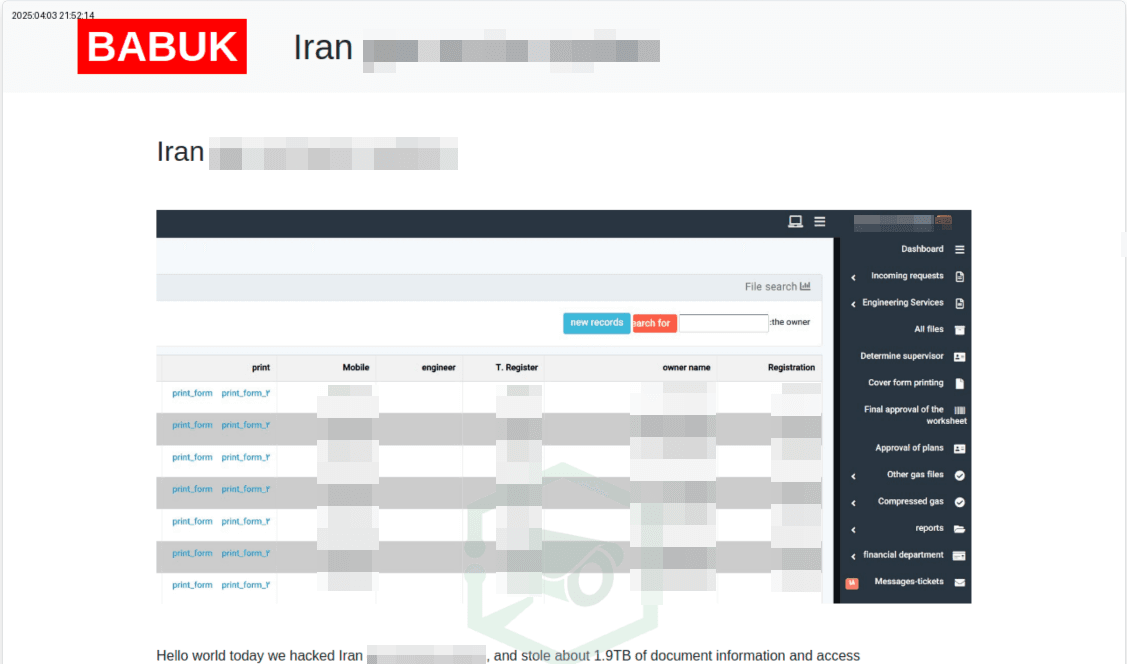
Analysis of dark web forum posts suggests that H2 2024–H1 2025 was less about direct financial gain from industrial organizations and more about maximizing publicity. For example, in April 2025, a post announced a successful attack on critical Iranian gas services and the theft of about 1.9 TB of data, including credentials and documents. The Babuk2 ransomware group claimed responsibility.
Announcements on dark web resources about successful defacements of industrial organization websites may also indicate hacktivist activity. Among those affected were an Iranian electronics manufacturer and a steel company.
Cyberattacks carried out by hacktivists and politically motivated actors are often followed by the leakage of confidential information and indirect damage to the state. One example is the Anonymous PRANA Network's breach of an energy company's infrastructure, resulting in the theft of 6 GB of confidential data, including business documents and emails about the company's operations.
Overall, the industrial sector is one of the most frequently targeted in Iran. During the review period, heightened geopolitical tension influenced both the nature and methods of attacks on industrial facilities.
Throughout the review period (H2 2024–H1 2025), cybercriminals used malware in almost half of all attacks on Iranian organizations (48%), with ransomware involved in 80% of those cases. This pattern is characteristic not only of Iran but of the Middle East as a whole.
The second most common method was vulnerability exploitation. In October 2024, a series of attacks used this approach against nuclear facilities and the Iranian government, including the judicial, legislative, and executive branches. These incidents led to leaks of confidential information and serious operational disruptions.
The use of ransomware aligns with the targets of cyberattacks. The category Computers, servers, and network equipment predominates among these targets, accounting for 87%.
Credential compromise, which ranked among the top three methods with a 13% share, may be indirectly linked to the rise in attacks on web resources (increasing from 20% to 46%). Rapid digital expansion and the proliferation of new services can depress security standards, including the continued use of weak passwords and insufficient adoption of multi-factor authentication.
Another major incident involving credential compromise occurred when attackers breached the customer database of Iran's largest mobile operator. The April 2025 breach exposed personal data for 30 million users. Stolen data included full names, dates and places of birth, national identification numbers, birth certificate numbers, and full postal addresses. Technical data included SIM card identifiers, IMSI12 numbers, network types, and subscriber identifiers. The data structure suggests that both current and former subscribers were affected.
To gain a fuller view of attacks on Iranian organizations, we also examined dark web data. A half-year analysis of ad topics shows a decrease of 30 percentage points in defacements, an increase of 19 percentage points in posts selling or distributing databases, and a marked rise in DDoS attacks to 21%.
The prevalence of defacements and DDoS attacks indicates active hacktivist activity in the region, as these methods are central to their toolkit. This is supported by the fact that the proportion of databases distributed free of charge exceeds those offered for sale (63% versus 31%). Hacktivist activity is predominantly destructive, as seen in DDoS attacks and defacements of popular or significant websites. Typically, hacktivists do not seek financial gain but aim to maximize publicity, which is why they distribute stolen organizational data for free.
Attackers often circulate stolen data across multiple platforms (dark web forums and Telegram channels) to inflict indirect damage on targeted organizations. Their political motivation is also reflected in the industries most frequently targeted: defense, energy, and government.
Notably, all DDoS attacks referenced on dark web sources during the review period relate to June 2025. They are discussed in the relevant section of this study.
As in H1 2023–H1 2024, the predominant consequence of cyberattacks on Iranian organizations is the leakage of confidential information, followed by disruption of core activities. This aligns with the most frequently used method (malware) and the type most often deployed (ransomware). Activity by politically motivated groups and hacktivists who disseminate compromised data also contributes to these outcomes.
During this period, trade secrets (29%) and personal data (21%) were most frequently compromised. User credentials and payment card details were also common targets, each accounting for 14%. These figures indicate that organizations faced both financially motivated attackers and hacktivists. The former primarily seek credentials and payment card data that can be sold or used to steal funds, while hacktivists tend to prioritize personal data and commercial information.
A half-year comparison shows marked shifts: the share of incidents disrupting core activities rose by 22 percentage points, and cases damaging state interests increased by 15 percentage points, while confidential information leaks declined significantly (by 52 percentage points).
The rise in attacks causing operational disruption and harm to state interests reflects heightened geopolitical tensions in Q2 2025, accompanied by hacktivist activity. Broadly, changes in the country's threat environment mirror geopolitical events. Excluding June, Iran's threat picture resembles H1 2023–H1 2024.
However, methods used in Q2 2025—possibly for the first time—are likely to shape future attacks in the region and beyond, and to influence Iran's digital environment through regulatory and technological responses. To identify trends and anticipate future threats, we now turn to data from June 2025.
According to experts at the international cybersecurity company NSFOCUS, cyberattacks on Iran's infrastructure peaked on June 10, 2025. These attacks affected several socially significant areas, including finance, media, the internet, and telecommunications. While publicly available data did not show a notable surge in attacks during this period, dark web data more closely reflected the geopolitical situation. Of all messages posted during the review period, 41% appeared in Q2 2025, with June accounting for the highest share (58% of Q2 posts).
These figures highlight the value of analyzing open and dark web sources together to better understand threats and the actors targeting Iran. The dark web also provides a larger volume of information for analysis, including details on conducted and planned attacks, largely because hacktivists publicize their operations.
In this section, we examine:
which industries were most affected
which methods were used
Based on public data, 83% of successful attacks affected financial organizations. This included a large-scale attack by the Predatory Sparrow (Gonjeshke Darande) group on Iran's largest bank, which led to the shutdown of online banking, ATMs, mobile banking apps, and gas stations serviced by the bank. The impact was severe, temporarily paralyzing a key artery of the national financial system and undermining confidence in banks and their digital infrastructure.
The same group attacked an Iranian cryptocurrency exchange one day later, withdrawing about $90 million and sending the funds to inaccessible blockchain addresses. According to experts at the consulting company Elliptic, this effectively "burned" the assets, preventing their recovery.
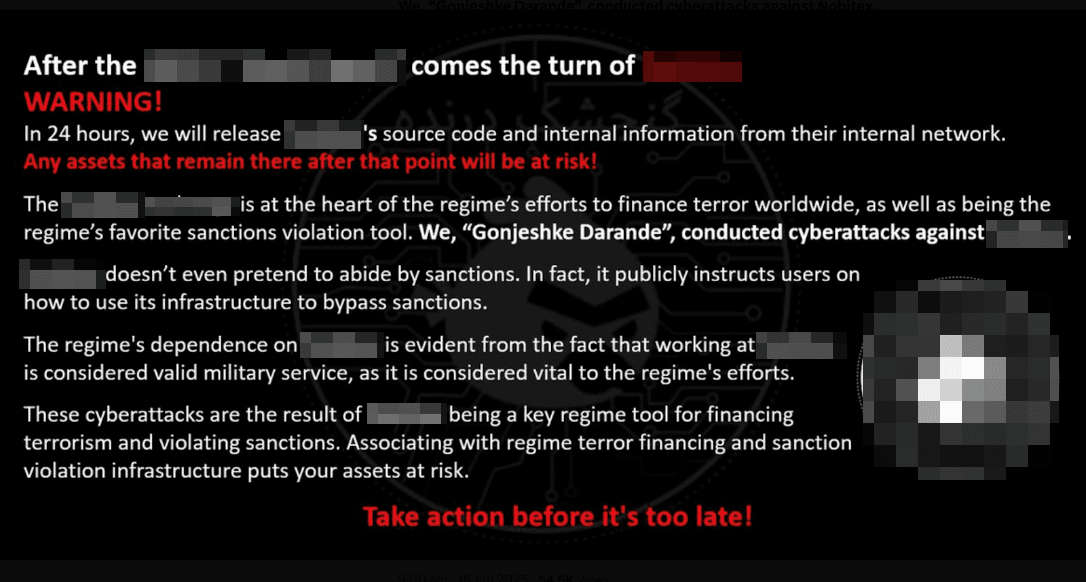
Several other Iranian banks were affected by cyberattacks in June. Customers experienced account-access issues, prompting authorities to warn the public about withdrawing funds. The Tapandegan hacktivist group claimed responsibility for one bank attack.
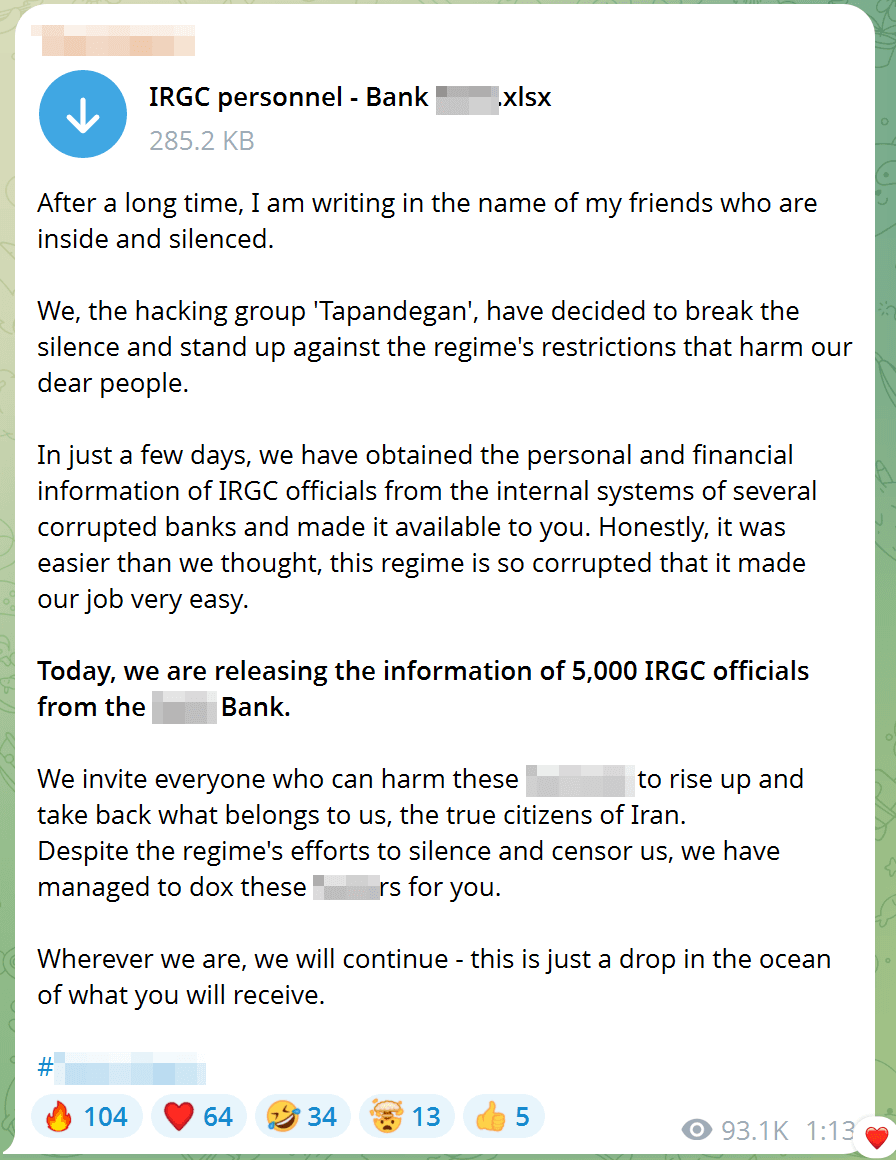
Amid escalating foreign policy conflicts, media organizations play a critical role in informing the public and shaping opinion. This makes them prime targets for groups aligned with countries hostile to Iran. One major June incident involved replacing a state television video stream with footage of the 2022 protests, accompanied by a voiceover urging the public to take to the streets.
Media-related posts accounted for almost a third (30%) of all dark web items in Q2 2025. In June specifically, 53% of posts concerned media. These included a news agency website defacement and DDoS attacks on Iranian radio stations and various information portals.
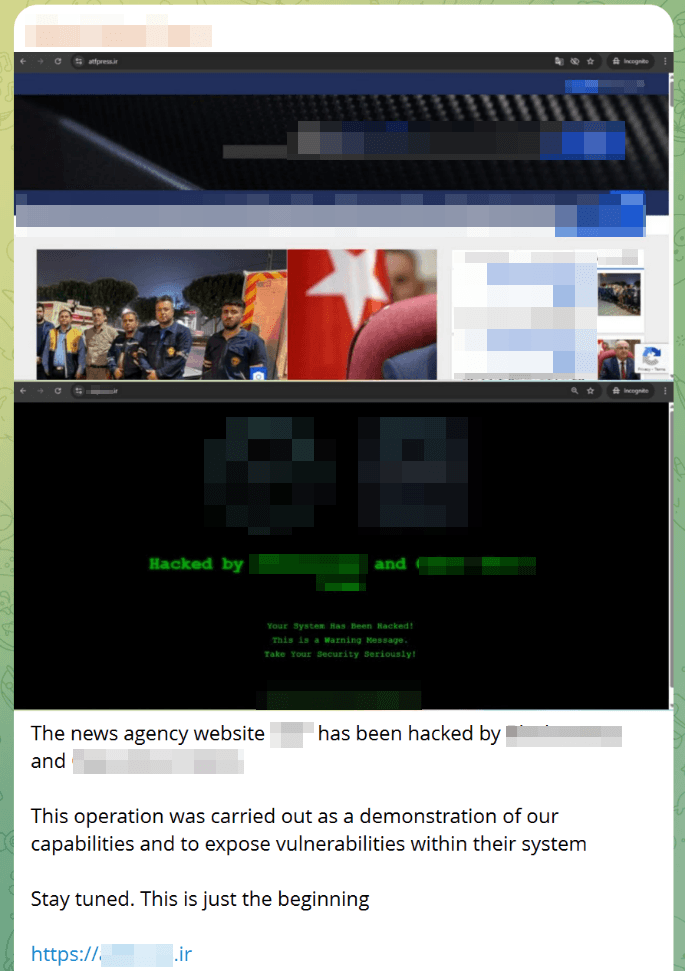
According to dark web data, 11% of announcements related to government agencies, the second most frequent category after media.
Overall, the industry-wide picture of attacks in June 2025 shows that adversaries primarily targeted entities with high economic and reputational significance. The disruption of Iran's largest bank and the subsequent hack of a cryptocurrency exchange were intended to demonstrate vulnerabilities in critical infrastructure serving a large share of the population and to undermine confidence in digital assets. The latter are particularly important for Iran given the role of cryptocurrency in its economy.
Disruption of media organizations erodes trust in state institutions and opens opportunities for social-engineering campaigns against social media users, since social platforms function as both communication channels and alternative news sources.
During periods of heightened geopolitical tension, cyberspace becomes a venue for demonstrating offensive capability and shaping public perception. Next, we consider the methods used to conduct these attacks.
Attacks by cybercriminals fall into two broad categories:
Public data indicate that about 63% of June incidents disrupted the core activities of Iranian organizations, with malware used in nearly half of the cases. Dark web data show a high share of DDoS activity promoted on underground platforms (33% of all announcements in Q2 2025 and 55% in June).
Notably, the Declaration category dominated all publications in Q2 2025, accounting for 57%. This supports the assessment of elevated hacktivist activity during this period and reflects a broader pattern in geopolitical conflicts, where offensive actions occur both offline and online. Pro-government groups and individual hackers aligned with either side can coalesce into ad hoc teams based on shared goals.
These cyberattacks also affected telecommunications infrastructure, cutting off citizen access to communication services and operator websites, provoking domestic discontent.
In response to the attacks, the Iranian government restricted most internet access. According to Cloudflare, national internet traffic fell by 97%. Although intended to protect the population from cyberthreats, this measure also deprived residents of access to essential services and information. Large-scale destructive attacks therefore hampered many digital processes both directly and indirectly.
In most cases (68%), the victims of DDoS attacks in June were media organizations. This led Iranians to turn to social networks for updates on the conflict.
Cases of active dissemination of disinformation on social media were reported, mainly involving old photographs. The perpetrators sought to pass these off as images of current anti-government protests. This included the publication of an image of an allegedly downed Iranian drone on social media, which turned out to be from an earlier incident.
Radware experts have noted a trend toward fake media materials created using artificial intelligence techniques. The danger of this tactic lies in synthetic content's high similarity to real photos and videos and its ability to spread quickly on social media. Such attacks are coordinated and strategic, aimed at undermining public trust in the authorities, shaping outside observer views of the conflict, and manipulating political narratives abroad.
Next, we will analyze the cybercriminal groups that were most active in June 2025.
NSFOCUS has identified the following groups whose activities were observed in the June cyberattacks: the Islamic Hacker Army (carrying out 43.75% of attacks), the Unknowns Cyber Team (31.25%), Predatory Sparrow (12.5%), Blackswamp (6.25%), and Jetimbek (6.25%). Most of these groups are hacktivist, which is typical of escalating foreign policy conflicts and their reflection in cyberspace.
Analysis of dark web forums and Telegram channels reveals similar statistics, albeit in a different order. The Unknowns Cyber Team posted the largest number of announcements on the dark web (60%), Predatory Sparrow and the Islamic Hacker Army posted approximately the same number (9% each), and Anonymous Syria Hackers accounts for 8%.
Almost all of the DDoS attacks on media outlets in June were carried out by the Unknowns Cyber Team. In addition to posts about cyberattacks on a major bank and a cryptocurrency exchange, Predatory Sparrow distributed various databases and access details for Iranian government agencies.
The group follows a key dark web market trend, shifting to public platforms to increase the visibility of claims, particularly Telegram and X.
The Islamic Hacker Army primarily conducts DDoS attacks against government agencies, whereas Anonymous Syria Hackers focus less on strategic targets and aim for broader reach. Their operations seek to affect as many Iranian targets as possible, widening the scope of threats. Reported victims include an Iranian IT company and an educational platform.

Interestingly, according to dark web data, no activity by the Unknowns Cyber Team, Predatory Sparrow, or the Islamic Hacker Army was recorded in the remaining quarters of the review period (Q3 and Q4 of 2024 and Q1 of 2025). This suggests that their geopolitical alignment and operating patterns surface during escalations in interstate conflict.
Iran is one of the Middle East's leading countries in technological development. Unique economic conditions have pushed the state to adapt and build a foundation for leadership in the digital economy. Large-scale government measures to position Iran as a regional technology hub span education, science, regulatory oversight of emerging technologies (particularly artificial intelligence), import substitution, and the provision of modern technical equipment to state institutions. These measures also seek to safeguard digital sovereignty.
They are intended to protect critical state infrastructure from cyberthreats, yet Iran's strained geopolitical relations complicate that task. The threat landscape is shaped by a technological race between Iran and its adversaries that is advancing faster than the state can fully implement countermeasures, such as improving digital literacy, training people to work with AI, and deploying new cyber defense technologies.
Events in June 2025 significantly affected Iran's threat landscape, and conclusions about attacker methods during that period should inform future planning. The state should consider two scenarios for future risks: in the absence of foreign policy tensions, and in their presence. Forecasts focus on targeted industries and attacker methods:
Recommendations for improving Iran's cybersecurity taking into account the region's specific digital environment and threat profile. Recommendations are comprehensive, covering both regulatory and technological measures.