
Vybornov Alexey
Analyst, International Analytics Group of PT Cyber Analytics

Vybornov Alexey
Analyst, International Analytics Group of PT Cyber Analytics
This study analyzes the digital profile of SEA countries during Q1–Q3 2025 and examines the regional cyberthreat landscape. The countries covered are Brunei, Vietnam, Indonesia, Cambodia, Laos, Malaysia, Myanmar, Singapore, Thailand, and the Philippines. Special attention is given to the rapid development of digital technologies and how this is reflected in the region's expanding digital space.
Research objectives:
To describe the SEA cyberthreat landscape, the study draws on open-source intelligence combined with dark web data, including information from five major specialized forums, over 400 Telegram channels, websites aggregate defacements, ransomware reports, and DDoS activity.
In our assessment, most cyberattacks remain undisclosed due to reputational risks. Therefore, it is impossible to determine the exact number of threats, even for organizations specializing in incident investigation and threat-actor analysis.
Our incident database is regularly updated. Information about some attacks may appear in public long after the actual incident. Therefore, the data in this report reflects the situation as of the publication date.
The terminology used in this study is provided in the Glossary on the Positive Technologies website.
The technological landscape of Southeast Asia is rapidly evolving, spanning key sectors of the economy, the social sphere, public administration, and culture. Countries such as Singapore, Malaysia, Vietnam, Indonesia, and Thailand are actively investing in digital technologies, viewing them as tools for modernizing infrastructure and accelerating economic growth. Digitalization has become one of the key national priorities, while the adoption of artificial intelligence, the Internet of Things (IoT), and blockchain technologies is laying the groundwork for a new stage of regional development. This process is also tied to efforts to reduce socio-economic inequality, expand access to public services, and strengthen the region's position in the global digital economy.
However, along with rapid technological progress, the importance of cybersecurity is also increasing. Southeast Asian countries are facing a growing number of attacks targeting government institutions, financial organizations, and manufacturing facilities. Threats range from ransomware attacks to large-scale campaigns aimed at destabilizing society. In response, countries in the region are developing national cybersecurity strategies, establishing incident response centers (CERT/CSIRT), strengthening regulatory frameworks, and enhancing international cooperation in the field of information security.
According to DataReportal, over the past five years the region has seen rapid growth in internet penetration. Even so, internet accessibility in Southeast Asia remains highly uneven. While Singapore and Malaysia show a high level of digitalization and virtually universal internet access (with over 90% of the population connected), countries such as Indonesia, Vietnam, the Philippines, and Cambodia continue to face challenges related to the deployment of broadband infrastructure needed for stable, high-speed connectivity.
The issue of internet accessibility is particularly acute in archipelagic countries such as Indonesia and the Philippines. Their geography, consisting of numerous islands, makes laying undersea cables extremely costly. To address this, Indonesia launched a large-scale national initiative, the Palapa Ring project, aimed at creating a national fiber-optic "ring" to provide broadband connectivity to remote islands and rural areas.
A complex landscape has become a serious challenge for Laos. According to the ASEAN Research Institute, its mountainous terrain significantly complicates the development of network infrastructure, while existing solutions remain expensive and offer relatively low connection speeds.
However, cybercriminals in countries with low internet penetration may use this fact as a cover to organize scam centers. Reports indicate that such centers are widespread in Cambodia, Laos, and Myanmar, are part of a single criminal network. According to an Amnesty International report, at least 53 such centers were operational in one of the region's country. People deceived into "employment," then held against their will and forced to participate in criminal activities under threats of violence.

As part of an investigation into scam centers in Cambodia, local police raided 43 locations over three weeks, detaining more than 2,000 people directly involved in their operations.
The activity of scam centers also harms Southeast Asia's overall image by undermining international trust and the region's attractiveness to investors. In response, the U.S. government imposed sanctions on 19 organizations based in Myanmar and Cambodia, which were allegedly involved in supporting the illegal operations of scam centers.
A characteristic feature of Southeast Asia's digital landscape is the dominance of mobile internet. For a large part of the population, a smartphone remains the primary (and often the only) means of accessing the web. According to DataReportal's 2025 statistics, the number of mobile connections in most countries in the region exceeds 100% of the total population. The exception is Laos, where the rate is 86.7%, which may indicate difficulties in building base stations.
At the same time, Singapore—the regional leader in digitalization—demonstrates one of the highest mobile connection rates, with more than 179% of the total population. Such high figures do not reflect the actual number of users but rather the widespread practice of one person owning multiple SIM or eSIM cards or devices.
This trend is driving the rapid growth of the mobile services market. Super apps such as Grab, Gojek, and ShopeePay play a special role, offering users a wide range of features, from ride-hailing and food delivery to purchasing insurance policies and applying for loans. As more services and processes move into the digital space, its structure becomes increasingly complex and interconnected, which expands the number of potential vulnerabilities and poses additional cybersecurity challenges.
In June 2025, researchers from Unit 42 (Palo Alto Networks) recorded a series of attacks targeting telecommunications companies in Southeast Asia. According to their findings, the hackers gained access to telecom equipment by compromising authentication mechanisms, installed the NoDepDNS backdoor, and launched the Cordscan utility to collect geolocation data from mobile devices.
According to experts, the campaign's objective was not to steal user data or affect mobile devices. Based on the tools exploited, the attackers' primary goal appears to have been cyber espionage and the collection of information about subscriber movements.
The analysis of the hackers' behavior demonstrated a high level of sophistication—timestamps and security policies were altered, and traffic was disguised. These indicators indirectly point to the involvement of an APT group and possible involvement of Liminal Panda, known for its operations in this industry.
The development of digital technologies in Southeast Asian countries has significantly improved the quality of services available to visitors. Solutions like online booking, electronic visas, autonomous transport, and other digital tools have enhanced the convenience of travel and contributed to economic growth. These initiatives are part of the region's digitalization strategy, formalized in the ASEAN Declaration on Digital Tourism.
However, as this sector becomes increasingly digitalized, the attack surface expands as well. Online booking platforms, mobile applications, contactless payment systems, and elements of critical infrastructure like airports are becoming Potential targets for cybercriminals
Cyberattacks targeting the tourism industry can undermine the region's reputation as a safe travel destination, deter both international and domestic visitors, and potentially disrupt the operation of critical infrastructure.
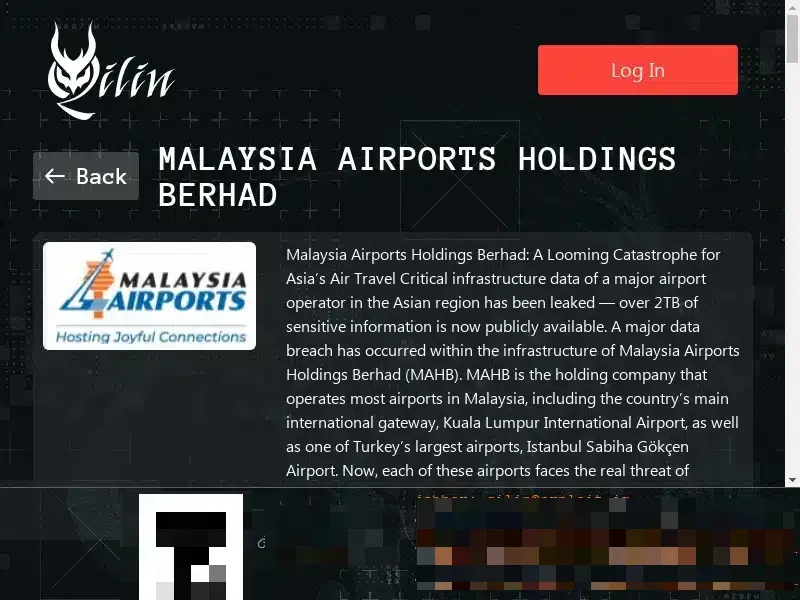
For instance, on March 23, as a result of a cyberattack on Kuala Lumpur International Airport, hackers managed to steal 2 TB from Malaysia Airports Holdings Berhad, and to disrupt the operation of the airport’s infrastructure itself. Airport staff were forced to manually display flight schedules on whiteboards, indirectly indicating that core digital systems were unavailable. Later, the Prime Minister of Malaysia reported that the hackers had demanded a ransom of $10 million for restoring the airport's systems.
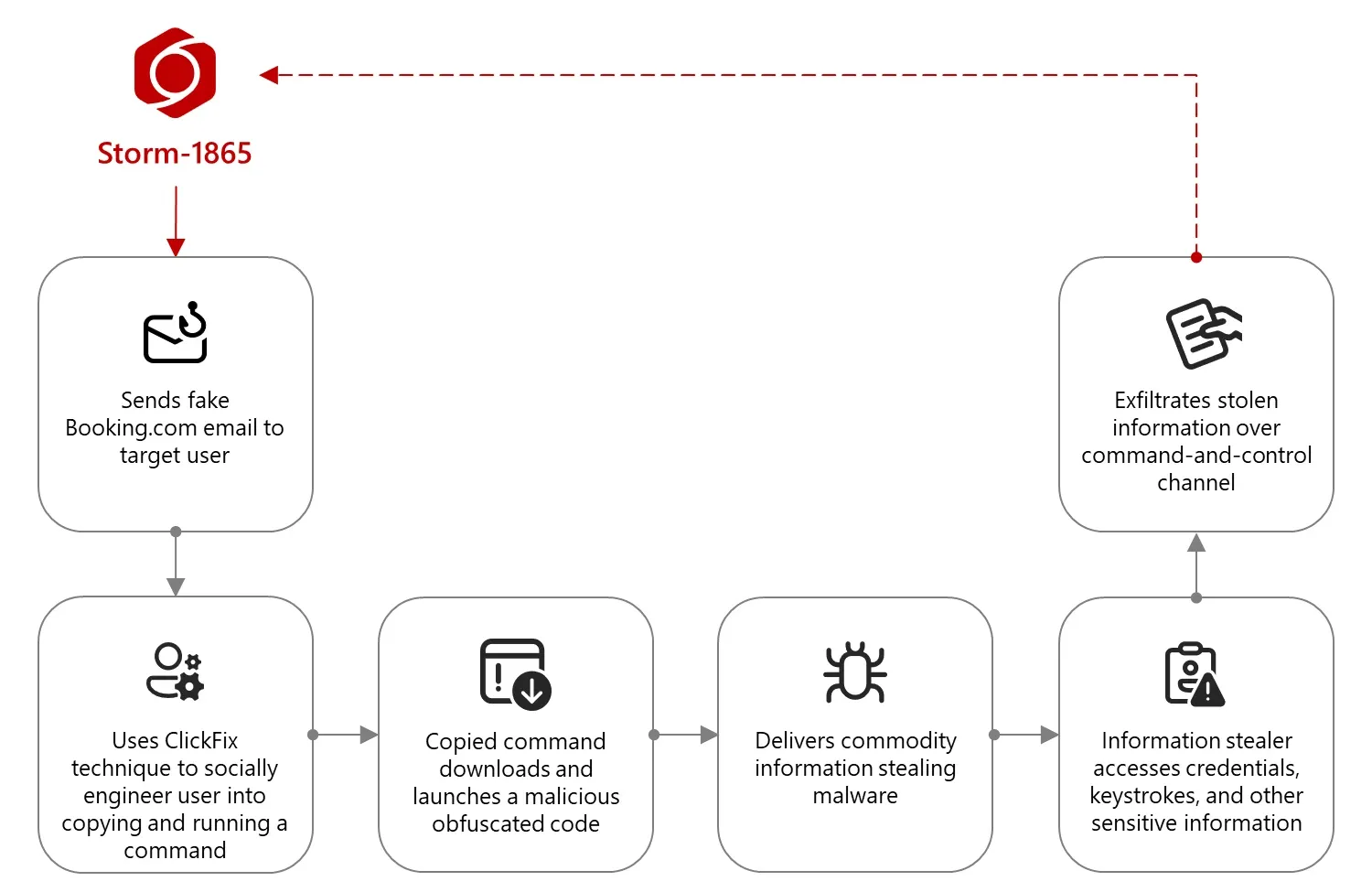
Also in March 2025, Microsoft Threat Intelligence identified a large-scale phishing campaign conducted by the Storm-1865 group that targeted the hospitality industry. The hackers sent emails impersonating Booking.com and employed a ClickFix social engineering technique designed to trick users into manually executing malicious code. The campaign affected the hotel sector worldwide, including Southeast Asia, and involved the distribution of several types of malware, such as XWorm, Lumma Stealer, VenomRAT, and AsyncRAT—aimed at stealing financial data and account credentials.
The tourism sector in Southeast Asian countries is undergoing an active phase of recovery after the COVID-19 crisis. Governments across the region are implementing both national and regional initiatives aimed at restoring tourist flows to pre-pandemic levels.
However, as tourism and related industries become increasingly digitalized, cybercriminal activity is also rising. Cyberattacks can slow down the recovery of the tourism industry, undermine Southeast Asia's attractiveness as a travel destination, and extend beyond the industry itself, affecting critical infrastructure across the region.
Digitization has also impacted the education system. Distance learning, which had actively developed during the COVID-19 pandemic, has become the norm not only in the Southeast Asia region but worldwide too. Open online courses like SEAMEO and MOOCs have made education more widespread and accessible for both — students and teachers, even for those in remote locations.
However, the development of digital education platforms in the region has also been accompanied by cyberattacks. For instance, in Indonesia, a data breach was reported in the student admissions system, resulting in unauthorized access to the personal information of more than 13,000 users. According to some media reports, the hackers exploited SQL injection vulnerabilities in the university's web application, allowing them to extract records from a database containing applicants' personal data. Part of the stolen information was later published on a hacker forum.

By analyzing closed Telegram channels and dark web forums, we identified evidence of ransomware attacks on educational institutions in Thailand, DDoS attacks on the Vietnam National University, and a data leak involving the MJQ Education institute in Cambodia.
Southeast Asian countries recognize the strategic importance of digitalization of education system and set a primary goal - to equip people with the necessary skills and knowledges that will be relevant in the future. However, cyberattacks on educational institutions undermine these efforts, posing threats to digital development.
Digital transformation in Southeast Asia is progressing through both regional ASEAN initiatives and national strategies developed by individual countries.
At the regional level, the key framework is the ASEAN Digital Masterplan 2025, which aims to:
In practice, this translates into developing telecommunications infrastructure, creating cross-border digital payment systems, promoting e-government services, building regional sandboxes for testing innovative solutions, and initiatives to improve digital literacy among the population.
The rapid development of the region's digital landscape also requires a solid theoretical foundation and the training of qualified specialists capable of supporting and advancing new technological projects. Therefore, education in Southeast Asian countries is a pressing issue. Governments in the region are striving not only to improve digital literacy among the population, but also to build a learning system that encompasses school, university, and professional education.
By the end of 2025, ASEAN member states plan to complete all initiatives outlined in the ASEAN Digital Masterplan 2025, as confirmed at the latest meeting of the region's digital ministers. Although a new plan has not yet been officially presented, the association is already working on the ASEAN Digital Economy Framework Agreement (DEFA) and the long-term ASEAN Digital Community 2045 concept, which will serve as the next stages in advancing the region's digital integration.
Alongside regional programs, each country implements its own national digital transformation strategy, taking into account national development priorities, economic maturity, infrastructure conditions, and local challenges such as limited resources, complex geography, and climatic conditions that make internet connectivity and, consequently, access to public digital services difficult in certain areas.
Below is a top five ranking of Southeast Asian countries by level of digitalization, according to the United Nations E-Government Development Index (EGDI), which measures how effectively governments use digital technologies to provide public services and engage with citizens.
Country | Global index EGDI 2024 | Key areas and initiatives |
| Singapore | 3 | Smart Nation: digital economy, e-government, society; smart city, AI, and cloud technologies; high level of online services. |
| Thailand | 52 | Thailand 4.0: expansion of digital services and platforms, smart cities, and the development of telecom infrastructure and 5G coverage |
| Malaysia | 57 | MyDIGITAL and Malaysia Digital Economy Blueprint: deployment of 5G; development of the fintech ecosystem, digitalization of government services, enhancement of digital skills among the population, and development of a professional talent pool |
| Indonesia | 64 | Indonesia Digital Roadmap / Vision 2045: development of a unified system for identification, authentication, and data exchange across all government services. Support for small and medium-sized businesses in digital transformation.Promotion of digital literacy among the population |
| Vietnam | 71 | Vietnam's National Digital Transformation Program: trilateral digital development, including digital economy, digital government, and digital society. Ensuring access to fiber-optic internet for over 80% of the population and 5G coverage for 99%. Focus on the application of AI, blockchain, and IoT technologies in industry, tourism, and cybersecurity. |
An analysis of the top five countries in the region by the level of digitalization shows that Singapore, Thailand, Malaysia, Indonesia, and Vietnam form the digital core of Southeast Asia. These nations are actively investing in digital infrastructure, developing e-government systems, and integrating advanced technologies into public administration and the economy.
However, such rapid digital progress inevitably expands the digital landscape, increasing its vulnerability to cyberattacks. As a result, Southeast Asian countries pay particular attention to cybersecurity and incident response, which has become especially critical amid the growing number of online fraud cases. A key role in this process is played by Computer Emergency Response Teams (CERTs), which operate in every country in the region.
At the international level, cooperation is coordinated within APCERT (Asia Pacific Computer Emergency Response Team)—a regional platform for sharing experience, publishing indicators of compromise, and conducting regular cyber exercises. The latest exercise, held in July 2025, focused on current defense methods against APT group attacks.
To strengthen coordination within the region, in Singapore launched the ASEAN Regional CERT initiative in 2024. Later that year, ASEAN member states signed a cooperation agreement under the new initiative to jointly enhance the region's cyber resilience. The development of such initiatives reflects the countries' shared commitment to building mutual trust and establishing a unified approach to countering modern сyberthreats.
The rapid integration of digital technologies across various sectors of government and society in Southeast Asia has brought not only greater efficiency and more convenient services but also new vulnerabilities. Hackers quickly adapt to local development trends and exploit weaknesses both to inflict maximum damage on key sectors of the economy (for example, by disrupting critical information infrastructure (CII) and destabilizing societies) and to maximize profit, such as by selling access to internal information systems of organizations.
According to our statistics, compiled from open-source data, the most frequently targeted sectors during the reporting period were government institutions (32%), financial organizations (16%), and manufacturing facilities (12%).
The prominence of these sectors in dark web and Telegram discussions indicates heightened interest in them and indirectly correlates with the number of real attacks.
The popularity of these sectors stems from high concentration of data and financial flows, as well as their strategic importance to national economies—a finding repeatedly confirmed by previous studies1,2. The public sector, industry, and financial organizations form the foundation of economic stability and national security in the region, which also makes them priority targets for cybercriminals Cyberattacks can disrupt critical services and undermine trust in government institutions and the financial system. Moreover, the deeper hackers can penetrate the internal segments of these organizations' infrastructure, the higher the likelihood of non-tolerable3 events occurring.
1 Reasearch: Cybersecurity threatscape in Southeast Asia
2 Research: Exploring cybercrime on the dark web in Southeast Asia
3 A non-tolerable event is an event caused by a cyberattack that prevents the organization from achieving its operational or strategic goals or leads to significant disruption of its core business.
The digitalization of the public sector in Southeast Asia is one of the region's key development priorities. The implementation of digital government services enhances the efficiency of state–citizen and state–business interactions, reduces bureaucratic barriers, and ensures service accessibility even in remote areas.
All countries in the region are developing e-government (e-gov) initiatives, with their scale determined by national circumstances and available resources. The main goal is to digitize as many public services as possible using modern technologies, including artificial intelligence.
However, the expansion of the digital landscape within government institutions is accompanied by a range of cybersecurity risks, driven by factors such as:
During the period under review, cyberrisks in the public sector can extend beyond isolated incidents, escalating into threats that endanger the entire system of public administration. The execution of non-tolerable events in this area may lead not only to financial losses but also to violation of public trust in government, infringements of citizens' rights and freedoms, and threats to national security.
Examples of non-tolerable events for government organizations include:
Government digital platforms accumulate huge amounts of digitized information about citizens, organizations, and critical infrastructure, making them highly attractive targets for cybercriminals. On one dark web forum a database was offered for sale, allegedly associated with the Bekasi Regency universal portal—an integrated public service platform in Indonesia.

According to the listing, the leak includes more than 20,000 rows of confidential information. Although there are no official confirmations from government bodies or platform operators, the appearance of such offers on the dark web already demonstrates hackers' interest in this sector and can undermine citizens' trust in both digital platforms and the state itself.
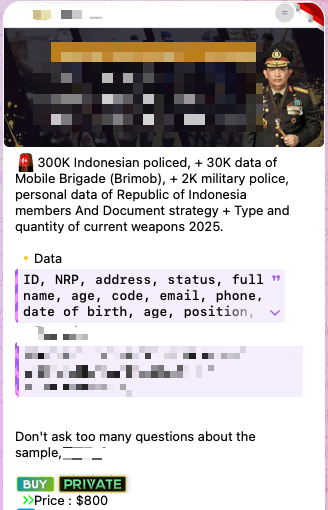
Additionally, numerous posts were found in closed Telegram channels in which authors claimed to have compromised resources of Indonesian law-enforcement agencies. One post offered over 300 000 rows of data for $800, including personal data of police officers, information on the composition of mobile brigades and military police units, as well as specifics on the types and quantities of weapons.
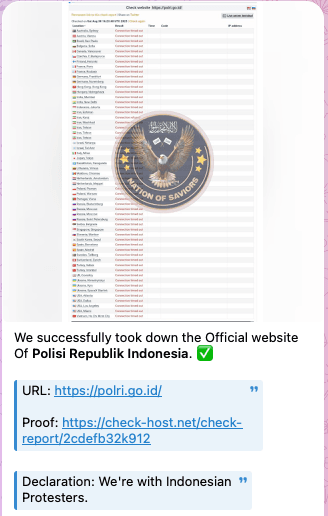
In addition to the listings offering stolen data, threat actors also claimed to have disabled the official website of the Indonesian police. Although no public statements were made in open sources, the monitoring platform Check-host confirmed that on August 30, 2025, the site was indeed unreachable. The report is no longer available as the data retention period on the website has expired, but site's inaccessibility coincided with a wave of protests.
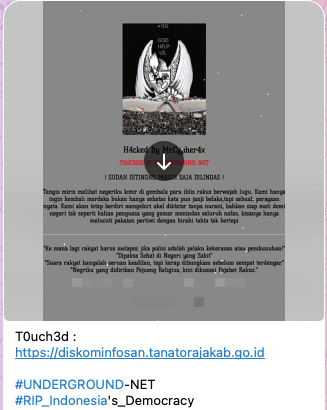
Furthermore, in cybercriminals' Telegram-channel we managed to find a post discussing the Tana Toraja Regency government portal in Indonesia, which was defaced. According to the message, site's content was replaced with provocative messages bearing the hashtag "RIP_Indonesia's Democracy."
Similar attacks affected Cambodia and Thailand during a local crisis between the two countries due to territorial disputes, when the digital environment of both countries became a space for escalation and the expression of dissent. Between July 24 and August 7, 2025, Group-IB analysts recorded 139 cyberattacks carried out by 19 hacktivist groups, including attacks from Southeast Asia. The primary targets were government systems, defense-industrial facilities, critical information infrastructure, and media organizations. This information can also be supported by posts in hacktivist Telegram channels, which claimed successful DDoS attacks on government resources.
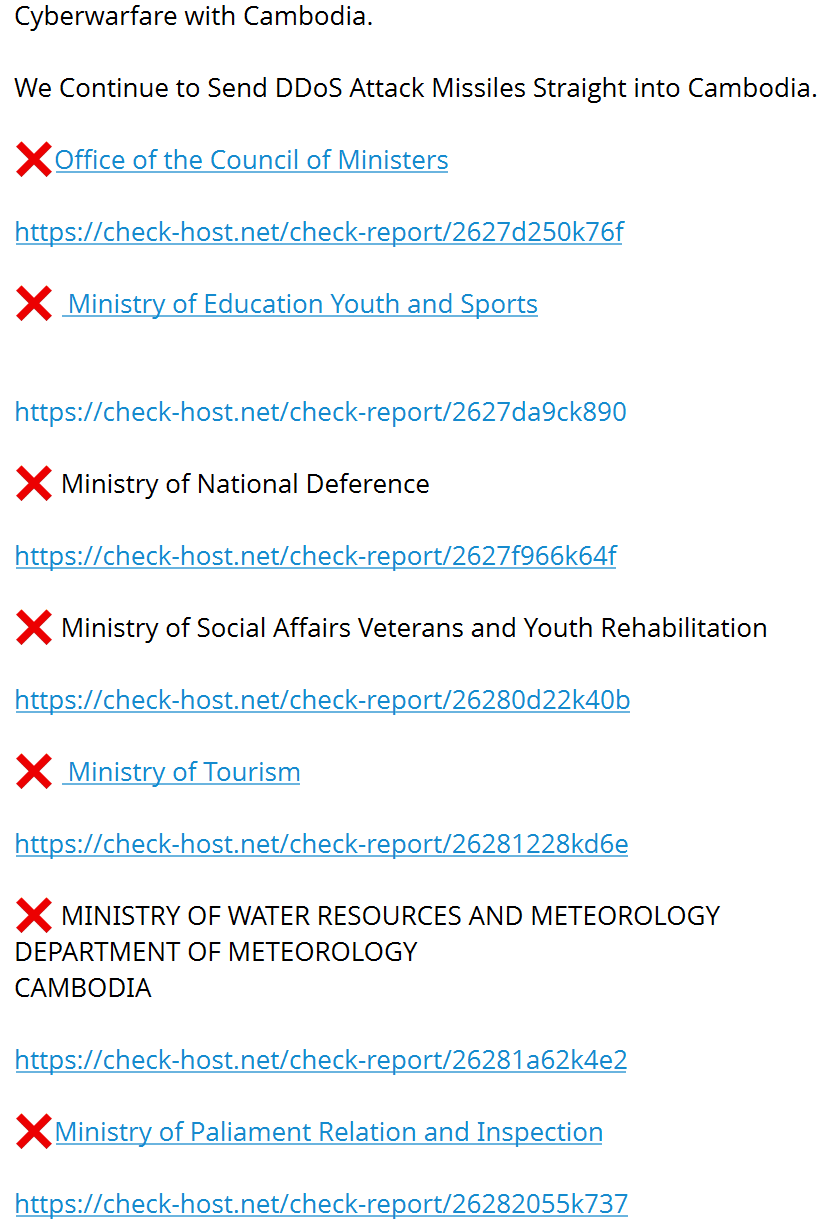
The cyberattacks were accompanied by a large number of disinformation materials, including content generated using deepfake technologies, distributed via messengers and social media platforms. Such campaigns aim to destabilize society and intimidating citizens, ultimately undermining trust in institutions and complicating the authorities' response to real incidents.
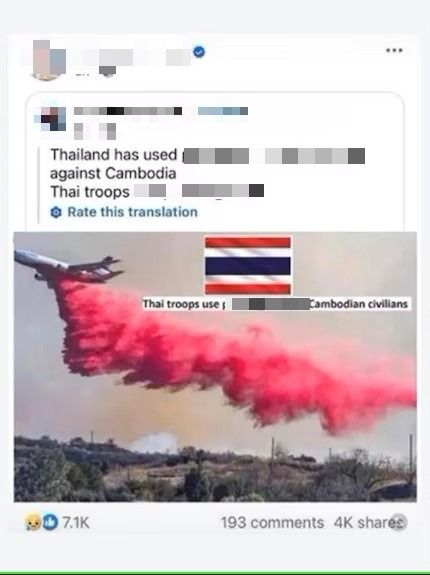
The spread of disinformation and provocative content in the digital space led to heightened social tensions, resulting in mass protests and, in some cases, human casualties. This confirms that even without serious technical consequences, cyberattacks can have significant socio-political effects, posing threats to national security and the well-being of citizens.
Digitalization in financial sector has given rise to the fintech sector—an area that integrates digital technologies with financial services. Driven by growing internet penetration, expanding mobile connectivity, and the increasing volume of electronic payments, fintech has become the platform on which new models of financial services are being built.
According to PwC's 2024 assessment, funding for fintech projects in Southeast Asia has increased more than tenfold since 2015, attracting over $20 billion in investments. The report highlights three key technologies as major industry drivers:
A distinct trend in the regional fintech sector is the adoption of new payment methods. To standardize cross-border transactions within ASEAN, the ASEAN Integrated QR Code Payment System was launched. This initiative aims to harmonize QR payments across member states, allowing users to make instant transfers and pay for goods or services through familiar national systems. In the long term, it is expected to reduce dependence on U.S. dollar settlements and strengthen regional financial integration, laying the groundwork for a unified digital market in Southeast Asia.
The growing use of QR technologies has also been mirrored in cybercriminal tactics. Previous research highlighted an upward trend in QR-based attacks targeting organizations. With the widespread adoption of QR codes among ordinary users, this technology could become a vector for mass-scale fraud and social engineering schemes.
From the perspective of non-tolerable events in the financial sector, the following can be considered:
As countries intentionally expand the boundaries of the digital financial space, the number of potential attack vectors increases—raising the likelihood of non-tolerable events.
In early September 2025, the ShinyHunters group claimed responsibility for breaching Vietnam's National Credit Information Center, allegedly stealing more than 160 million records, including clients' personal data, credit histories, and other identifying information.
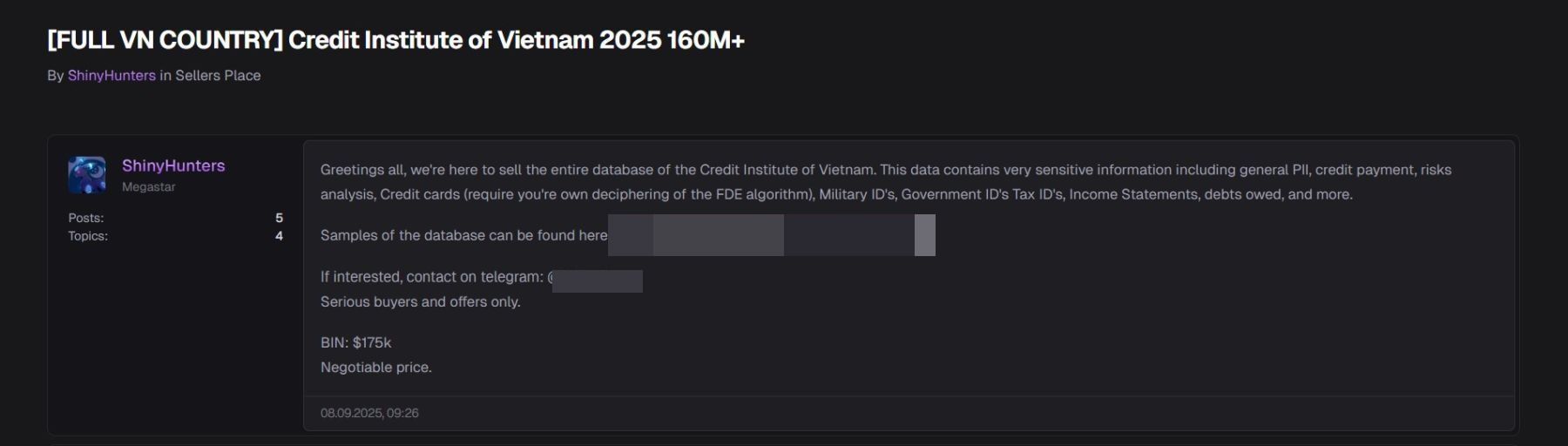
The stolen database was put up for sale on the dark web, with price negotiations conducted via the hackers' Telegram channels. Experts believe the perpetrators exploited a vulnerability in outdated software lacking recent security updates. Vietnamese authorities confirmed the incident and launched an investigation, emphasizing that CIC's core services were not disrupted.
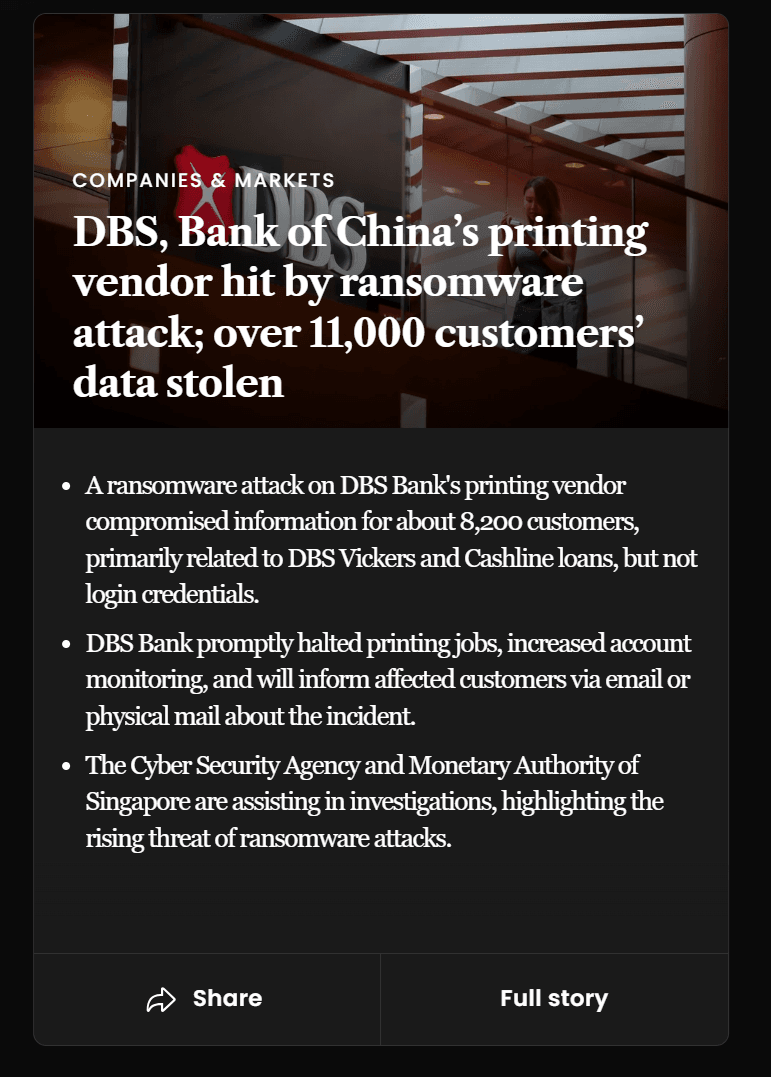
Earlier, in April 2025, a major incident occurred in Singapore, when DBS Bank was affected by a ransomware attack targeting its contractor, Toppan Next Tech (TNT)—the company responsible for printing client documents. The attack exposed data belonging to approximately 8,200 DBS clients and 3,000 Bank of China (Singapore) clients. The compromised documents included names, addresses, and account details; passwords, balances, and passport numbers were not affected. Although the files were transmitted in encrypted form, DBS suspended cooperation with TNT, enhanced transaction monitoring, and notified affected clients. The investigation is being conducted jointly with the Monetary Authority of Singapore (MAS) and the Cyber Security Agency of Singapore (CSA).
This incident illustrates that the cybersecurity resilience of financial institutions depends not only on their internal protection measures—attacks on more vulnerable third-party contractors can pose equally serious risks to data security.
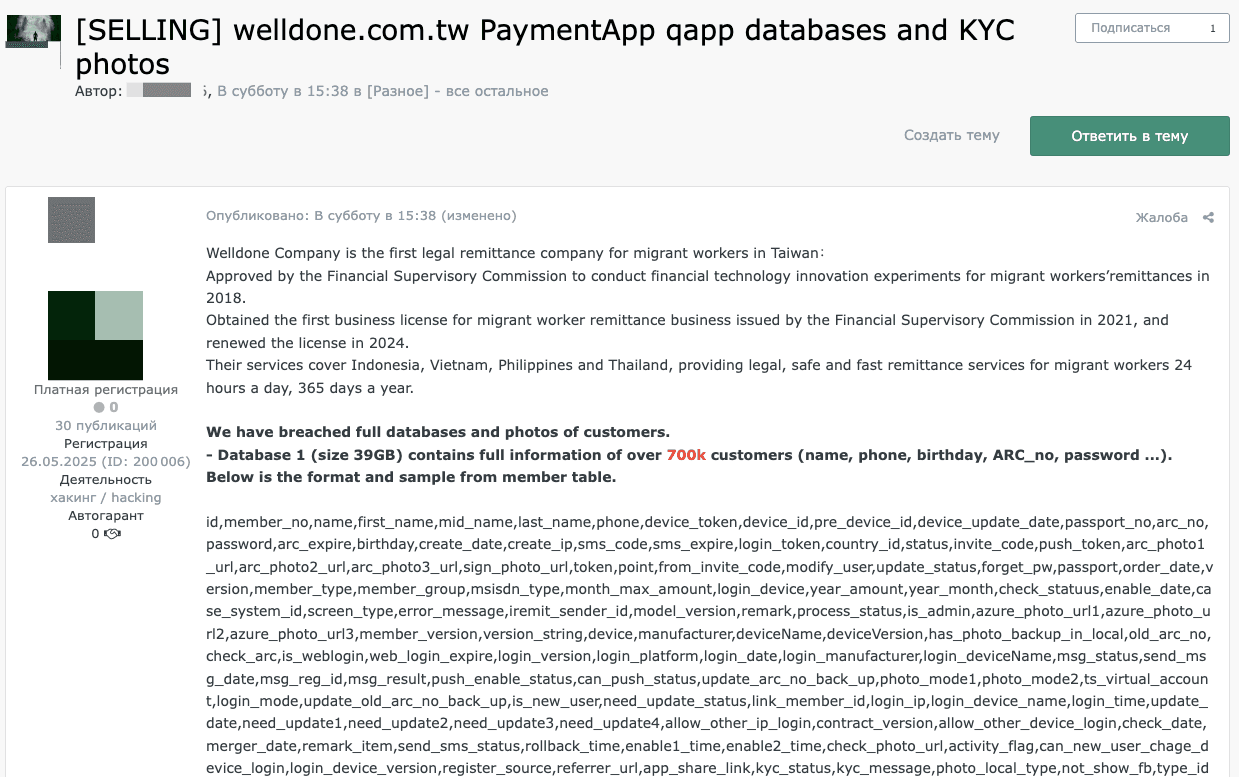
An analysis of dark web listings revealed that offers to sell databases from payment platforms containing user information appear regularly. For example, one listing advertised a 39 GB database allegedly belonging to the WellDone payment application, which included users' full names, details of authorized devices, passwords, and other sensitive data.
The post's authors emphasized that the application is used not only in its home region (East Asia), but is also widely adopted in Indonesia, Vietnam, the Philippines, and Thailand. Such blurring of national boundaries significantly complicates cybersecurity efforts, as incidents of this kind immediately take on a cross-border dimension, violating investigations and coordination among regulators.
Cryptocurrencies have become a notable part of Southeast Asia's digital economy, shaping new models of financial transactions and investment. Both individuals and businesses are showing growing interest in digital assets, while governments are taking diverse approaches to regulating and integrating cryptocurrencies into national financial systems.
Singapore stands out as one of the region's leading cryptocurrency hubs. Financial activity, including crypto operations, is regulated by the Monetary Authority of Singapore (MAS) under the Payment Services Act. MAS also promotes innovation-oriented initiatives such as Project Ubin and Ubin+, focused on exploring the use of blockchain and central bank digital currencies (CBDCs) in cross-border settlements. As a result, Singapore has become a key testing ground for global pilot projects under the mBridge initiative, which is developing a multilateral CBDC-based settlement system.
However, the expansion of cryptocurrency transactions has also led to a rise in сyberthreats. Non-tolerable events in this domain largely mirror those in the broader financial sector. Competition among crypto exchanges is particularly intense, forcing them to emphasize security and user trust.
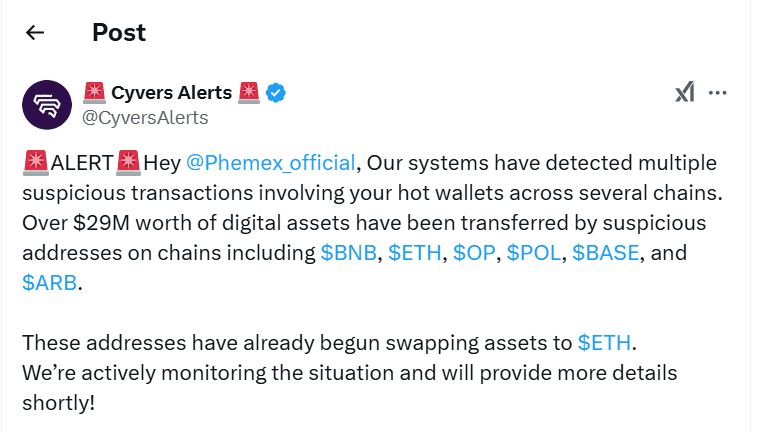
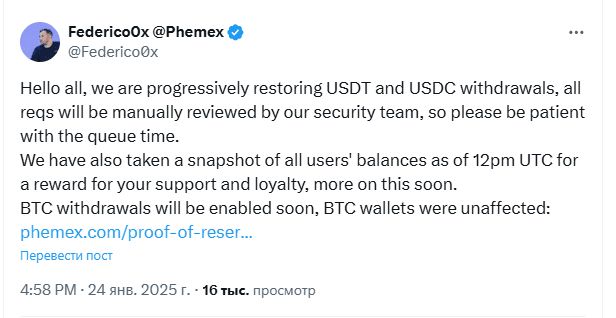
One example is the cyberattack on the cryptocurrency platform Phemex. In January 2025, the Singapore-based exchange suffered a breach in which digital assets worth over $69 million were stolen, including Ethereum, Bitcoin, and Binance Coin. After detecting suspicious transactions, Phemex temporarily suspended certain operations. Experts noted the attackers' sophistication and linked the incident to North Korean threat groups previously involved in other major cryptocurrency breaches.
Initially, the losses were estimated at $29 million. Later, MetaMask raised the figure to $70 million, and according to third-party sources, the total amount of stolen funds may have exceeded $85 million.
Despite the theft of digital assets, the company managed to quickly contain the incident and freeze customer account balances to ensure compensation in case any users were affected.
The financial sector remains one of the most targeted industries in the digital space. Not only traditional financial institutions are exposed, but also cryptocurrency services. The high concentration of sensitive information and the direct potential for monetary theft make this sector a prime target for cybercriminals who can exploit a wide range of vulnerabilities through the scale and variety of their tools.
In recent years, Southeast Asian countries have been undergoing intense industrialization closely tied to digital transformation and the rapid growth of the IT sector. Just as smart cities widely use IoT and AI, the industrial sector is increasingly adopting smart factories and the Industrial Internet of Things (IIoT).
For example, Infineon, a major semiconductor manufacturer in Singapore, announced the launch of a smart factory. Toyota is adapting solutions originally developed for smart cities to its production warehouses in Thailand. In Vietnam, FPT Software is integrating IoT, AI, and cloud technologies into manufacturing processes.
These technologies help to optimize production, reduce labor costs, and increase investment efficiency, but they also strengthen cybersecurity challenges. Сybersecurity in the industrial sector is critically important for each country. Disruptions caused by cyberattacks can lead not only to economic losses and supply chain interruptions but also to consequences affecting national security and even cause the loss of human life. Such incidents may stem from one or more non-tolerable events, for example:
Among actual incidents in the region's manufacturing sector is a statement made in summer 2025 by hacktivist group, claiming to have obtained unauthorized access to HMI/SCADA interfaces used at metallurgical, construction, and food-processing enterprises in Vietnam.
Unauthorized access to a facility's control systems enables manipulation of manufacturing processes with potentially severe consequences. Altering temperature setpoints in metallurgy may lead to equipment damage and life-threatening accidents. In the construction industry, disrupting automated control systems for production lines can cause supply disruptions and project shutdowns; in the food sector it can threaten product safety. If the same HMI/SCADA interface is used across multiple facilities, hackers can standardize and scale their operations by exploiting the same vulnerability. Cybersecurity specialists should pay close attention to the widespread use of standardized solutions—both on production lines and within the security architecture itself.
Another incident in the region’s heavy industry sector was discovered on a portal that publishes cases of ransomware attacks. Toyomi, a subsidiary of the major metalworking firm MSM International, likely fell victim to the Akira group, known for its double-extortion tactics—where attackers not only encrypt data but also exfiltrate confidential information and demand a ransom to prevent disclosure.
According to the announcement, the hackers stole more than 6 GB of corporate data, including employee documents, accounting records, and project documentation, threatening to publish it However, no subsequent updates were issued by either the group or Toyomi.
Such incidents can lead to the disclosure of confidential information, loss of trust and key clients, and the loss of key clients—collectively causing significant damage to the company's reputation and resilience.
Among dark web listings, we identified an offer to sell access (via Palo Alto network equipment) to the internal infrastructure of a major automaker. The company's name was not disclosed, but its profit for the previous year is estimated at $13–22 billion. The access was priced at $3.000.
Such a sale could trigger a range of incidents, including unauthorized access to corporate systems, compromise of production networks, and leakage of confidential data—disrupting manufacturing and inflicting significant economic losses on the company.
Manufacturing remains one of the most critical and vulnerable targets for cyberthreats. The high level of automation, adoption of IIoT technologies, and dependence on digital control systems make manufacturing enterprises potential targets for cybercriminals. Attacks on manufacturing facilities can lead not only to economic losses and production downtime for individual organizations but also pose threats to public safety and national stability—especially when energy or defense enterprises are involved.
The analysis of the current state of Southeast Asia's digital landscape, the dynamics of сyberthreats, and the rollout of national initiatives reveals several trends already shaping the region:
Cyberspace as a tool of socio-political influence
Domestic political processes, social tensions, and regional conflicts are increasingly mirrored in the digital environment. The chances that government and media resources will become less attractive targets are slim—if anything, the opposite is true. Information campaigns, DDoS attacks, and intrusions aimed at shaping public opinion and exerting pressure on state institutions have proven to be effective instruments of social manipulation.
Use of AI into attacks
The use of generative AI and large language models significantly facilitates attacks. Guides for jailbreaking LLMs and bypassing built‑in safeguards are circulating on the dark web, enabling the generation of convincing phishing messages in local languages, broadening the geographic reach of attacks, and providing guidance for beginning threat actors.
Evolution of phishing schemes: QR phishing
With the spread of alternative mobile payment methods across Southeast Asia, hackers can exploit this technology to steal funds by tampering with payment QR codes. The risk is heightened by the fact that national payment systems in several countries (Thailand, Indonesia, Malaysia, Singapore) are being integrated with one another, which facilitates cross-border settlements while simultaneously expanding the attack surface. Consequently, QR-phishing may soon become a new social-engineering tool in the region.
Expansion of supply chain attacks
Growing digital interconnectedness makes supply chains a key attack vector. Many organizations, particularly in the financial sector, are building sustainable, multi-layered defense systems. However, strong security of an organization does not guarantee the safety of its contractors, equipment suppliers, or software vendors. Even large companies with high cybersecurity standards can be compromised through a partner's breach or a malicious software update from a third party. Such attacks are difficult to detect, and their cascading effects can impact dozens of organizations.
The digitalization of Southeast Asian countries is actively advancing, though this process is uneven. This is largely due to the limited access of some countries to resources and technologies. Despite differences, most governments are steadily investing in e-government services, the fintech industry, industrial digitalization, and the development of digital platforms. Such progress enhances the region's competitiveness in the global digital economy but simultaneously broadens the attack surface, making SEA's information infrastructure more attractive to cybercriminals.
Comparing forecasts with current data confirms the persistence of previously identified trends. The number of cyberattacks in the region continues to grow, and hacktivists are actively responding to political developments, shifting internal and regional conflicts into the digital domain. The public sector, finance, and industry remain the most vulnerable areas, as ongoing digitalization continues to expand the attack surface.
Singapore remains a priority target due to its developed financial infrastructure and regulated cryptocurrency operations. Despite the disruption of several scam centers and a decline in publicly reported incidents, we cannot rule out that their operations have persisted in less visible forms and may re-emerge through new, more sophisticated online fraud schemes.
Our analysis shows that as the region becomes more digitally interconnected, the boundaries of the digital landscape blur, making the overall environment more vulnerable. Ensuring cybersecurity under such conditions is increasingly challenging and requires new comprehensive approaches.
To strengthen an organization's cyber resilience, technical protection measures are not enough. Organizations should adopt a strategic approach that prevents hackers from conducting attacks threatening critical business processes.
Such a strategy may include the following elements: