
Darya Lavrova
Senior Analyst, International Analytics Group, PT Cyber Analytics

Darya Lavrova
Senior Analyst, International Analytics Group, PT Cyber Analytics
Brazil is the largest economy and one of the most influential countries in Latin America. Key economic sectors such as automotive manufacturing, petrochemicals, metallurgy, and agriculture are undergoing rapid digital transformation. While this process streamlines critical industry operations, it also creates new opportunities for cybercriminals to exploit vulnerabilities.
This study explores the shadow markets for cybercrime services targeting government institutions, private organizations, and Brazilian citizens.
Study objectives:
Analyze Brazil's digital landscape and identify key areas of growth and development.
Examine the current cyberthreat landscape, including digital literacy, regulatory frameworks, organizational and technical cybersecurity measures, and trends in cyberattacks.
Investigate major underground platforms hosting advertisements targeting Brazilian organizations and individuals, identify trends and patterns specific to the country.
Forecast future trends in Brazil's shadow market.
Provide recommendations for ensuring cybersecurity for the government and businesses.
We analyzed nine of the most popular underground forums and over 400 Telegram channels. The research covered large, multilingual shadow platforms across various topics during the period from January 1, 2024, to April 1, 2025.
The following categories were analyzed:
Database: leaks containing personal data, user credentials, or confidential corporate documents.
Access: credentials for unauthorized access to devices or services in a company's infrastructure.
Vulnerability: vulnerabilities and exploits.
Carding: information related to bank cards.
Ransomware: posts by hacker groups about successful ransomware attacks.
DDoS: posts by hacker groups about successful DDoS attacks.
Brazil as a key player in Latin America, boasting the largest economy and a rapidly growing portfolio of digital services and solutions across all sectors. The digital transformation of government agencies, industries, finance, healthcare, and other areas has made Brazil a key target for cybercriminals. Their motivations range from gaining recognition in the cybercrime community to monetizing stolen data and unauthorized access via underground forums.
Brazil is experiencing a surge in investments in information technology, data centers, cloud computing, biometrics, communication and networking technologies, and cryptocurrencies. This highlights the country's ongoing shift toward digitalization, with vast volumes of data now being stored online. Digital government services are also being developed and deployed at federal, state, and municipal levels.
Brazil is one of the top global targets for cyberattacks and financial fraud. In 2023–2024, Brazilian organizations accounted for nearly 19% of all cyberattacks in Latin America. The current cyberthreat landscape is defined by a high percentage (26%) of attacks targeting government institutions, low levels of digital literacy among the population, and a shortage of skilled cybersecurity professionals. These challenges, combined with the rapid adoption of new technologies, give cybercriminals more and more opportunities to conduct attacks.
Government institutions remain one of the top targets for cybercriminals, as highlighted by both public data and underground forum activity. Government institutions rank among the top three most targeted sectors in categories such as ads for selling leaked databases and access credentials, as well as announcements of successful attacks — like website defacements. This suggests that hacktivists and cybercriminals are actively pursuing campaigns to build their reputation and credibility on the cybercrime market.
For Latin America as a whole, the most common outcome of successful cyberattacks on organizations is the breaches of confidential information, which accounted for 53% of incidents in 2024. This trend is also evident in Brazil. Ads frequently feature combolists1, alongside a rising trend in the sale of scanned documents, such as passports and driver's licenses, often paired with selfies or videos used for account verification. Given Brazil's significant investment in biometric technologies, this trend suggests a growing risk of future cyberattacks aimed at bypassing biometric systems and carrying out targeted phishing campaigns.
Brazil also reflects the global trend of a growing service-based model in the cybercrime market. Services that simplify cyberattacks for inexperienced users — such as phishing kits, tools for intercepting SMS messages, access to multimedia subscriptions (including Netflix and Spotify), and server rentals for anonymization — are becoming increasingly prevalent. Within the cybercrime ecosystem, there is also a clear "division of labor." Ads for selling access credentials dominate, as these provide extensive opportunities to target a victim company's infrastructure. Free access credentials, on the other hand, are usually of little value and are often shared either because they are no longer useful to hackers or as a way for hacktivists and novice cybercriminals to showcase their skills.
Databases and combolists dominate underground forums, accounting for 38% of all ads, with a ratio of roughly 2:1. Databases are generally more valuable, as they often contain login credentials and critical documents. Their price depends on the uniqueness of the information and the size of the affected company, ranging from a few hundred to tens of thousands of dollars. Both databases and combolists play a central role in the early stages of cyberattacks, such as reconnaissance and social engineering.
The sale and distribution of access credentials is one of the most prominent categories on underground platforms, comprising 12% of all ads. Credentials belonging to industrial companies are particularly expensive, ranging from $4,000 to $70,000, as ransomware attacks on such companies can disrupt production processes and lead to significant financial losses. Lower-priced credentials, typically ranging from $100 to $1,000, tend to have limited utility, such as Remote Monitoring and Management (RMM) access to desktops ($100).
As Brazil's financial infrastructure continues to digitalize, the share of carding activities in the shadow market is expected to grow. The service-based model of cybercrime is also likely to strengthen further. Attacks on government institutions, along with the sale and distribution of access credentials, databases, and documents, are likely to remain prevalent, as are announcements of successful cyberattacks.
1 A combolist is a text file containing usernames or email addresses paired with passwords. Cybercriminals compile such lists from data breaches or security incidents, then sell or distribute them for free on the dark web.
2 A non-tolerable event is an event that results from a cyberattack and prevents an organization from achieving its operational and strategic goals or leads to a significant disruption of its core business.
Brazil's GDP is expected to grow by 2.3% in 2025, reflecting the country's efforts to close the gap with developed economies.
Brazil is implementing its E-Digital Strategy for 2022–2026, a comprehensive approach to leveraging digital technologies to drive sustainable economic and social development. Key components of the strategy include expanding access to high-quality internet services throughout Brazil, fostering research, development, and innovation, building public trust in the digital environment, and improving education and professional training in information and communication technologies (ICT).
The implementation of the strategy has already led to the following results:
Despite these advancements, Brazil's Network Readiness Index (NRI)3 underscores that the country's use of technology has not yet reached an advanced level, with Brazil ranking 44th globally. The index reveals shortcomings such as insufficient government incentives for investment in new technologies, a low volume of ICT patents, and limited development of ICT skills within the education system. However, Brazil is clearly moving toward digital transformation. This is underscored by the IT sector's robust growth — 13.9% in 2024, surpassing the global average of 10.8%. Brazil has solidified its status as the largest IT market in Latin America, accounting for 34.7% of regional investments. According to Crunchbase, global investments in software accounted for 10% of total investments in science and engineering during Q1 2023–Q1 2025, while local investments stood at 8%. The resilience of Brazil's IT sector is driven by advancements in AI, corporate digitalization, and cloud infrastructure development, according to data from the Brazilian Software Companies Association (ABES).
3 Network Readiness Index (NRI) is a composite indicator measuring the development of ICT and the digital economy across countries.
Several trends are shaping Brazil's digital landscape, as evidenced by market and investment analysis:
Since 2023, investments in data centers and cloud computing have accelerated, driven by the digitalization of industry and business processes as well as growing interest in AI technologies.
Brazil is making significant progress in the biometrics sector. In 2023, the country accounted for 2% of global biometric technology revenue, with the market generating $832.8 million USD. By 2030, Brazil is expected to lead the Latin American biometrics market, with projected revenue of $3.6 billion. Biometric boarding4 technology has already been implemented at major airports like Congonhas and Santos Dumont, improving both pre-flight security and passenger throughput.
Investments in cryptocurrency remain strong. In 2024, Latin America became the second-fastest-growing cryptocurrency market globally, with a 42.5% annual growth rate. Brazil, where cryptocurrency is recognized as legal tender, ranked 10th in the 2024 Global Crypto Adoption Index. In addition, Brazil was one of the first countries in the world to enact legislation regulating the cryptocurrency and virtual assets market.
Brazil's rapid digitalization presents new opportunities but also creates vulnerabilities. Sectors undergoing the fastest digital transformation are likely to become prime targets for cyberattacks if adequate organizational and technical cybersecurity measures are not implemented.
4 Biometric boarding is a system that uses biometric technology to automate passenger check-in and boarding. These systems aim to streamline security and control processes while improving the passenger experience.
Cybersecurity measures and processes in Latin America differ significantly from those adopted in the most technologically advanced countries. While the region has achieved a relatively high level of digitalization, this also provides cybercriminals with greater opportunities. Cyberthreats in Latin America are growing faster than anywhere else in the world. As of early 2025, companies in the region face an average of 2,569 attacks per week — nearly 40% higher than the global average of 1,848.
Brazil is unsurprisingly one of the primary global targets for cyberattacks and financial fraud. From 2023 to 2024, Brazilian organizations accounted for nearly one-fifth (19%) of all cyberattacks in the region. Brazil's struggle to counter cyberthreats is also reflected in its position in the Cyber Defense Index 2022/23, where the country ranked second to last, in 18th place.
The success of cyberattacks in Brazil is largely due to a gap between the widespread adoption of digital technologies — such as mobile banking apps, social media, and email — and the low level of digital literacy among the population. Additionally, as part of ongoing digitalization, Brazilian organizations increasingly rely on cloud computing, mobile apps, and API-based platforms to optimize operations and drive innovation. While this digital boom is critical for transforming traditional business models, it has significantly expanded the attack surface for cybercriminals.
Brazilian organizations face several challenges, including outdated systems and fragmented IT infrastructures, which make it difficult to integrate modern security measures and leave vulnerabilities exposed. Moreover, there is a persistent shortage of qualified cybersecurity professionals. According to a February 2025 survey by the consulting firm Rooby, 50% of Brazilian cybersecurity leaders believe universities fail to adequately prepare specialists for the industry, and 30% say that university degrees provide only "minimal" preparation. Furthermore, 56% of leaders reported difficulties finding qualified professionals in cybersecurity, and 38% struggled to recruit specialists in niche fields like threat analysis and cloud application security.
Brazil's rapidly digitizing government institutions are among the most targeted by cybercriminals. From 2023 to 2024, government institutions accounted for the largest share (26%) of cyberattacks in Brazil. This is due both to the sector's insufficient security measures and the growing number of digital services, which expand the attack surface.
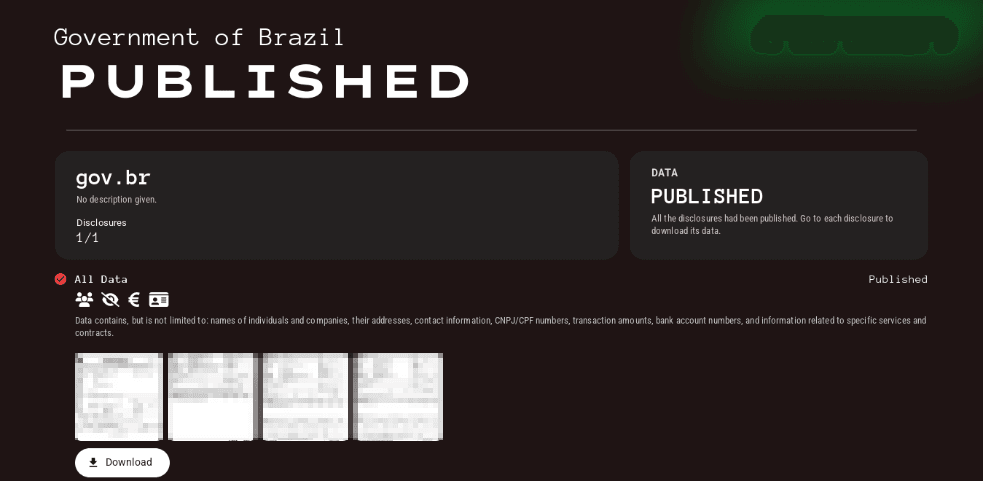
For instance, underground forums feature listings of successful breaches of government services and ransom demands for restoring access to data. One notable example was an attack on Brazil's largest government service platform, gov.br, by the ransomware group killsec. In 2024, the group announced the release of its own subscription-based ransomware tool (Ransomware-as-a-Service, or RaaS). In late October 2024, killsec published details of its attack on gov.br, disclosing information about individuals and businesses, including addresses, contact details, taxpayer identification numbers (CNPJ for companies and CPF for individuals), as well as service and contract information. The listing indicated that the data had been published, suggesting that the ransom was not paid.
As for biometric development, Brazil's National Data Protection Authority (ANPD) published a study on June 24, 2024, discussing the use, risks, and advancements of biometric data and facial recognition technologies. The study highlighted the sensitivity of biometric data, the potential for identification errors, and risks of discrimination. While acknowledging AI technologies as effective tools for improving facial recognition accuracy for security purposes, the report also raised concerns about issues related to accuracy and data privacy.
The growing reliance on biometric systems in Brazil, combined with a lack of qualified cybersecurity professionals, increases the risk of targeted attacks aimed at compromising data and disrupting operations. In March 2025, a major incident affected FacePass, a Brazilian identification app. A cyberattack exposed over 1.6 million files containing confidential user information and corporate system credentials. The breach occurred due to misconfigurations in an open Amazon Web Services (AWS) cloud storage container, putting the personal data of many Brazilians at risk. The compromised data included national ID cards, selfies for verification, AWS access credentials, full names, CPF numbers (Brazilian tax IDs), and phone numbers. The breach also revealed AWS credentials for FacePass, potentially allowing unauthorized access to the company's systems.
Financial institutions remain one of the primary targets for cybercriminals worldwide, and Brazil is no exception. One high-profile incident involved a data breach at Banco do Brasil, which exposed sensitive client information, including personal identification and financial data. A lack of digital literacy among employees managing and securing banking IT infrastructure can lead to serious security risks. Similarly, insufficient cybersecurity measures at Banco Inter led to the exposure of client account details and transaction histories.
In Brazil, cryptocurrency is recognized as legal tender, significantly expanding the threat surface for the financial sector. In 2024, Google Cloud's Threat Intelligence team discovered that cybercriminals were actively targeting Brazilian cryptocurrency exchanges and fintech companies.
The Brazilian government has made concerted efforts to address cyberthreats:
In December 2023, Brazil's Institutional Security Office (GSI) updated the country's National Cybersecurity Policy (PNCiber) and established the National Cybersecurity Committee (CNCiber). The committee focuses on developing national technologies, combating cybercrime, enhancing organizational resilience to cyberthreats, and promoting international cooperation in digital security.
To address security issues related to biometrics, Brazil established the Federal Biometric Service to oversee the issuance of biometric national ID cards (Carteira de Identidade Nacional). A new law requires the Federal Biometric Service to implement systems capable of one-to-many and one-to-one biometric checks using its database.
Brazil's cybersecurity market is also growing rapidly. Forecasts predict it will reach $5.46 billion by 2029, with an average annual growth rate of 10.3%.
However, cybersecurity significant challenges remain. For instance, Brazil's ANPD (National Data Protection Authority) is not part of CNCiber, which could be a critical oversight given the importance of protecting personal data from cyber threats. It is essential that technical experts with relevant experience and competencies are included in key government bodies responsible for implementing the national cybersecurity policy. The shortage of skilled professionals remains one of the most significant barriers to the growth of Brazil's cybersecurity market.
As Brazil's economy becomes increasingly digital, it is now a prime target for cybercriminals both domestically and internationally. From 2023 to 2024, the most common consequences of successful cyberattacks on organizations in Latin America were data breaches (53%) and disruptions to core operations (35%). Brazil plays a significant role in these statistics.
An analysis of major shadow forums and Telegram channels reveals the following trends specific to Brazil, which will be explored in more detail below:
Databases and combolists account for the largest share (38%) of shadow forum listings related to Brazil, with a ratio of approximately 2:1.
Databases tend to be more detailed and valuable than combolists, which are often created from outdated databases by stripping all information except email-password pairs and similar credentials. Databases may include personal details, account credentials, and confidential corporate information.
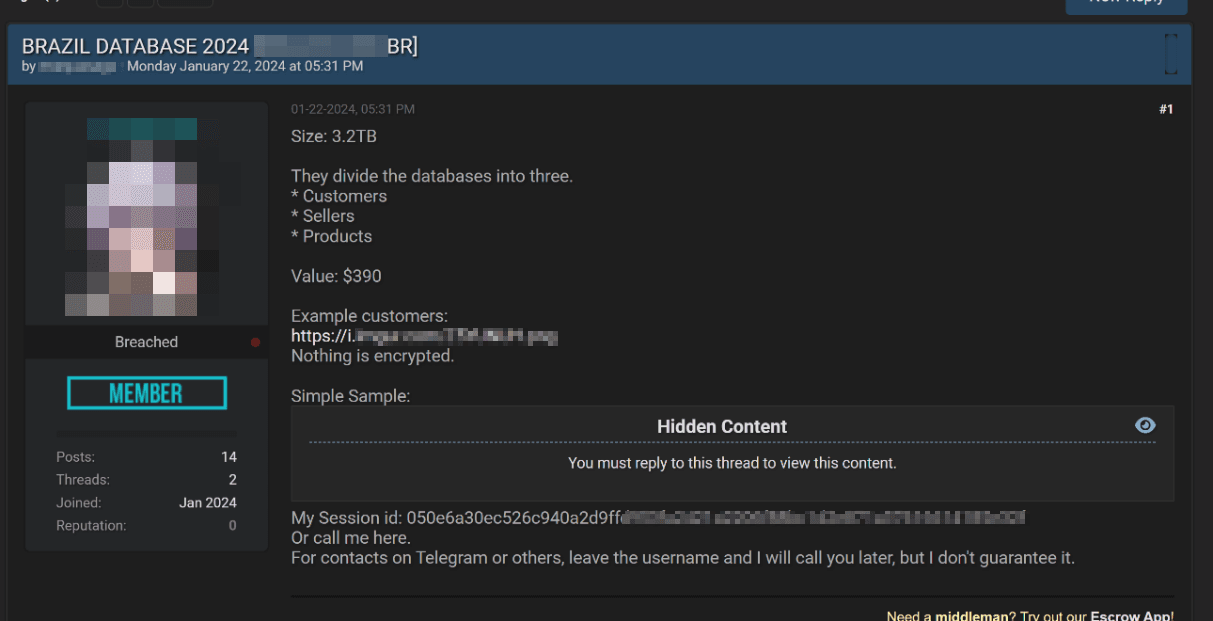
Listings often specify the source, type of compromised data, and price. For example, one listing advertises a database from a Brazilian online marketplace containing customer, seller, and product information for $390. The customer data includes phone numbers, email addresses, CPF numbers, photos, and other details. Such data can be used for further attacks targeting the company's customers.
The price of data depends on its uniqueness and the size of the company. For example, a database from a Brazilian IT company, compromised in February 2025, contained employee names, phone numbers, and email addresses and was priced at $100. Meanwhile, other leaks can cost tens of thousands of dollars.
Older databases are also common. For instance, data from a 2021 breach affecting over 533 million Facebook5 users — including names, phone numbers, and email addresses — continues to circulate. Even outdated databases retain value, as users often fail to update their credentials after a breach, allowing the data to remain useful for years.
5 A product by Meta (designated an extremist organization in Russia and banned under local law)
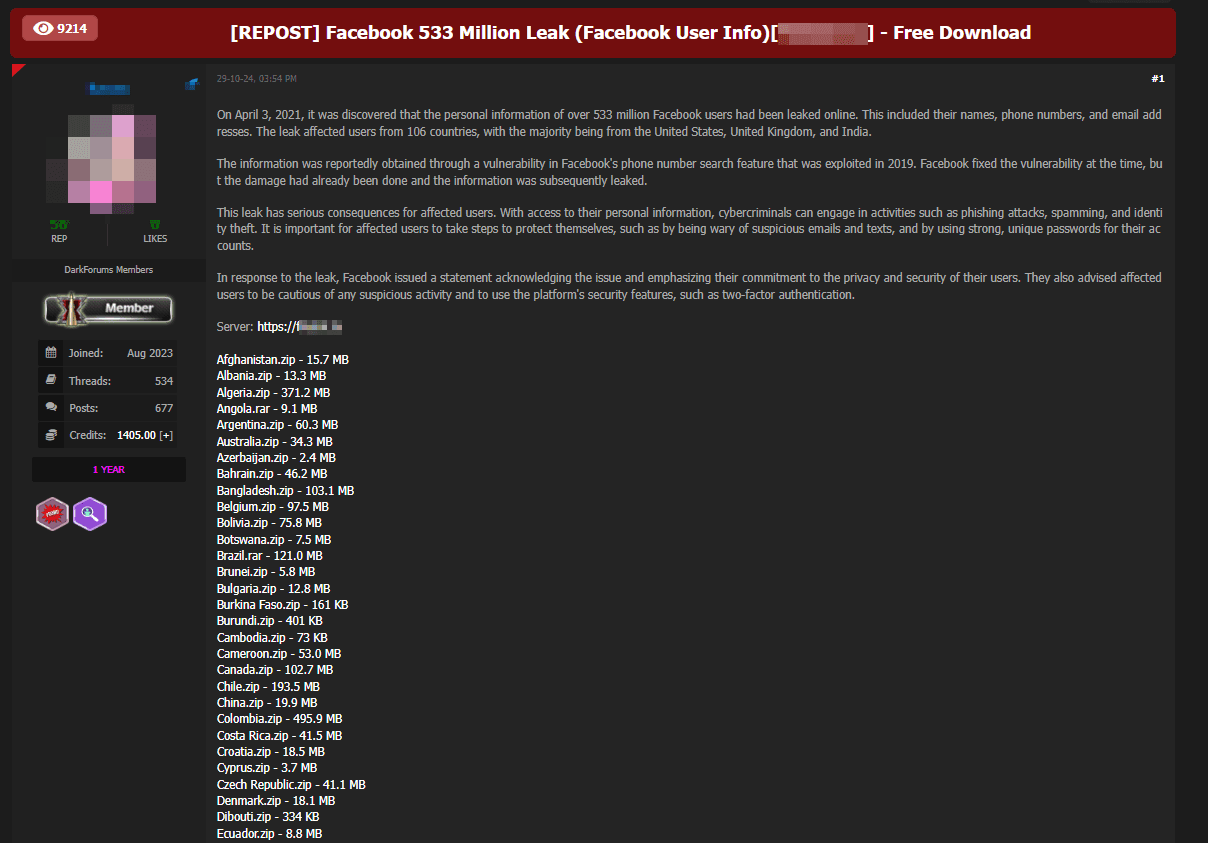
Similarly, the price of combolists varies depending on their size and how fresh they are. For example, a combolist with nearly 3 million email-password pairs was listed for $300.
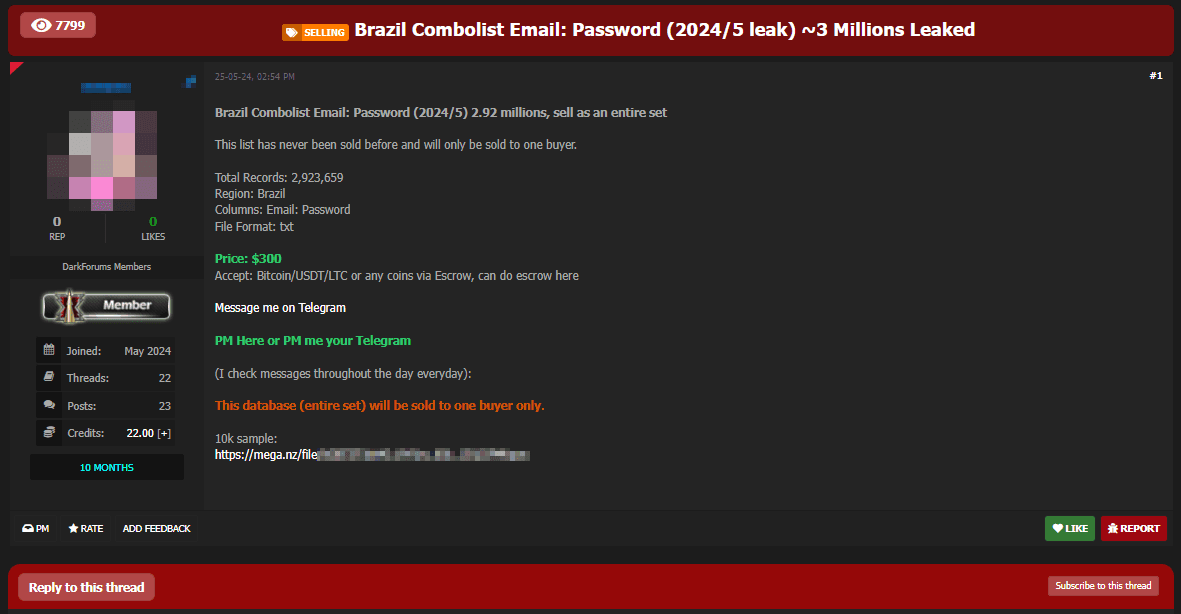
The abundance of low-value databases and combolists likely reflects how easily this data is obtained. Brazil's relatively low level of digital literacy is characterized by frequent use of weak passwords and insufficient safeguards for transmitting, processing, and storing sensitive information.
Competition on shadow resources is intense, and sellers of goods or services must show high engagement and maintain strong trust by responding promptly to buyers and meeting their needs. Free data distribution can help cybercriminals build reputation in dark web communities.
Databases and combolists can be used to carry out cyberattacks in the following ways:
1. Databases and combolists are often used to automate attacks like brute force, credential stuffing, and account takeovers. Cybercriminals test stolen credentials across multiple websites and applications, attempting to gain unauthorized access to sensitive data or infrastructure. This strategy is effective because many users reuse passwords across different services.
2. Targeted social engineering attacks. Leaked corporate email addresses, combined with data from databases and social media, allow cybercriminals to identify key individuals within a company (executives, IT staff, or finance personnel). They can then launch highly targeted phishing campaigns against these individuals.
In general, databases tend to offer cybercriminals more valuable insights and resources than combolists, which are typically lower-value commodities on the shadow market. However, both are primarily used in the early stages of cyberattacks, helping criminals save time on reconnaissance and enabling social engineering tactics.
A global trend in the shadow economy — the rise of service-based models — is also evident in Brazil. Listings increasingly offer tools and services designed for those without the technical skills to hack infrastructure or steal data themselves.
These services include tools for phishing attacks, SMS interception, and access to multimedia subscriptions (such as Netflix and Spotify). Cybercriminals without technical expertise use these services to achieve their goals. Phishing attacks and intercepted SMS messages can be used to gain unauthorized access to applications and services installed on a victim's device, such as banking apps, government e-services, or personal accounts on healthcare portals. In Brazil, this is particularly widespread due to the relatively low level of digital literacy among users who can now manage their finances and other resources via smartphones.
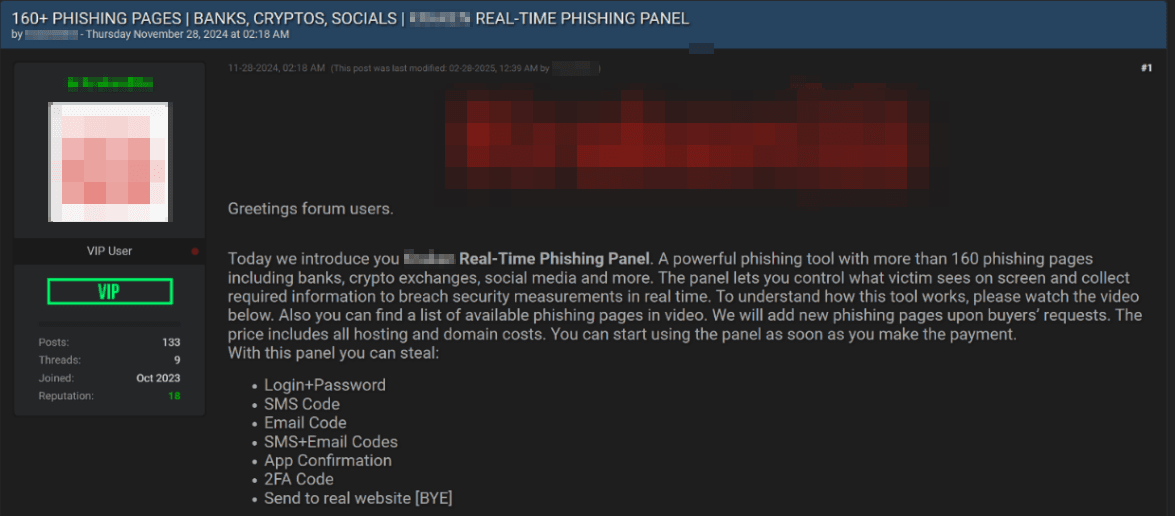
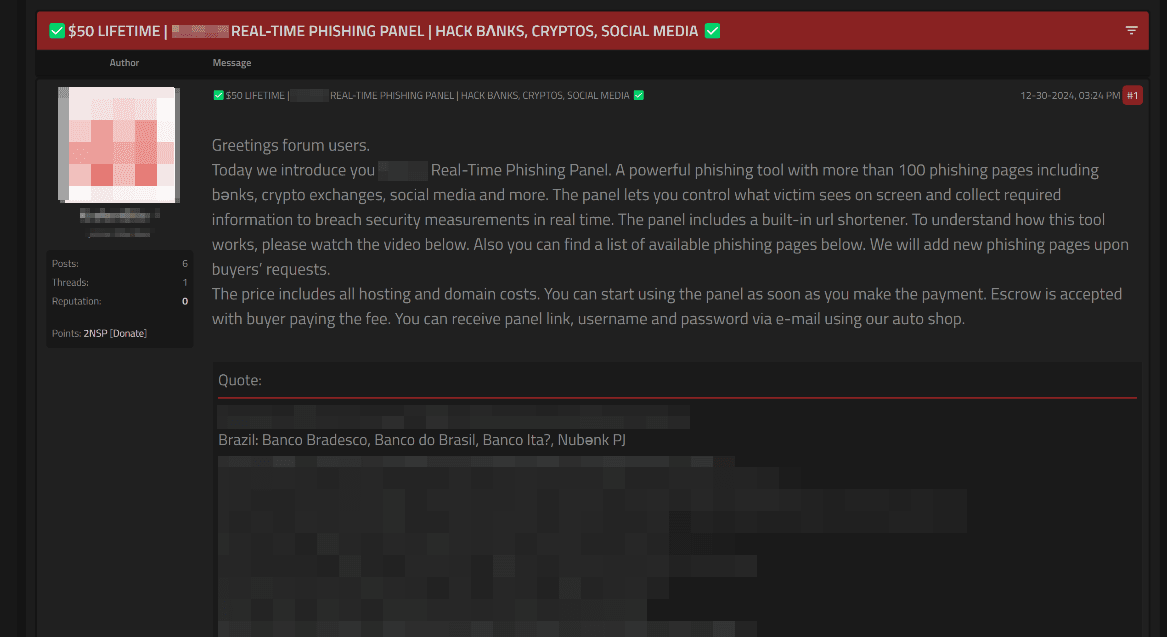
One shadow market listing offers a real-time phishing panel, highlighting its functionality with more than 160 phishing pages designed to mimic banks, cryptocurrency exchanges, social networks, and other platforms. These phishing pages can be customized to specific targets, and the panel allows buyers to request additional phishing templates to expand the range of available options. The panel enables users to collect login-password pairs, SMS codes, and two-factor authentication (2FA) codes. According to the listing's author, the panel already includes phishing pages for major banks in several countries. For Brazil, the panel includes phishing pages tailored to major banks like Banco Bradesco, Banco do Brasil, Banco Itaú, and Nubank PJ.
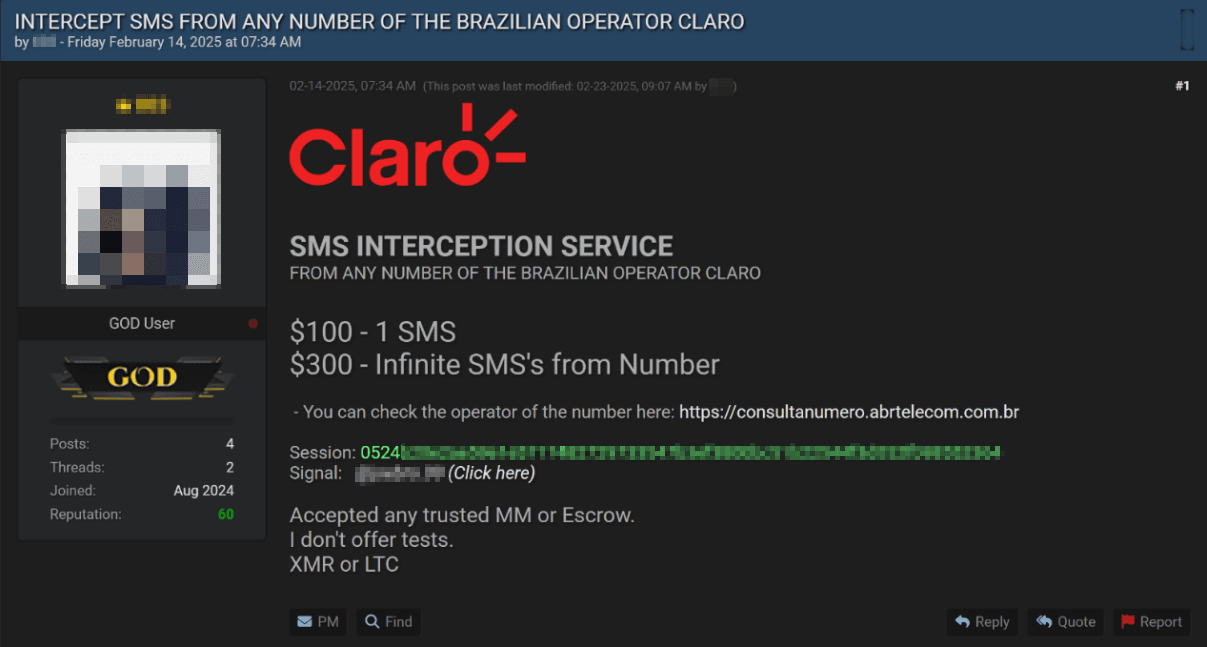
Another listing advertises an SMS interception service, specifying that it works for any phone number associated with Claro, the largest telecommunications group in Latin America and a key multiservice operator in Brazil. Claro's network serves over 4,800 municipalities and covers about 98% of the Brazilian population. Intercepting a single SMS costs $100, while unlimited access to one number is priced at $300. Criminals can use such services to hack user accounts, steal money from victims' bank accounts by intercepting transaction confirmation codes, and access sensitive personal or medical information. This stolen data can then be exploited for fraud, blackmail, or social engineering attacks.
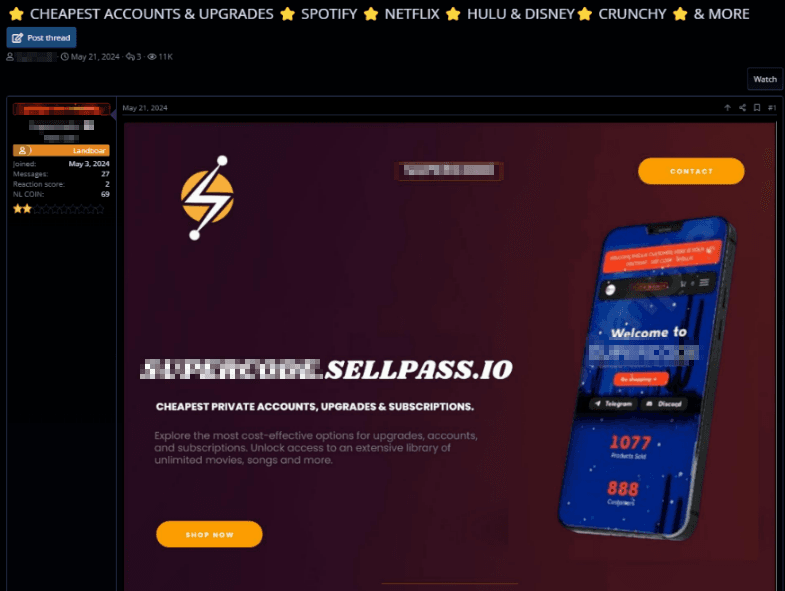
Although listings for account sales may not directly facilitate attacks, the accounts themselves are often the result of illegal activities, such as data breaches, ransomware campaigns, or service exploitation. For example, the listing below offers access to an unlimited number of movies and songs on various platforms.
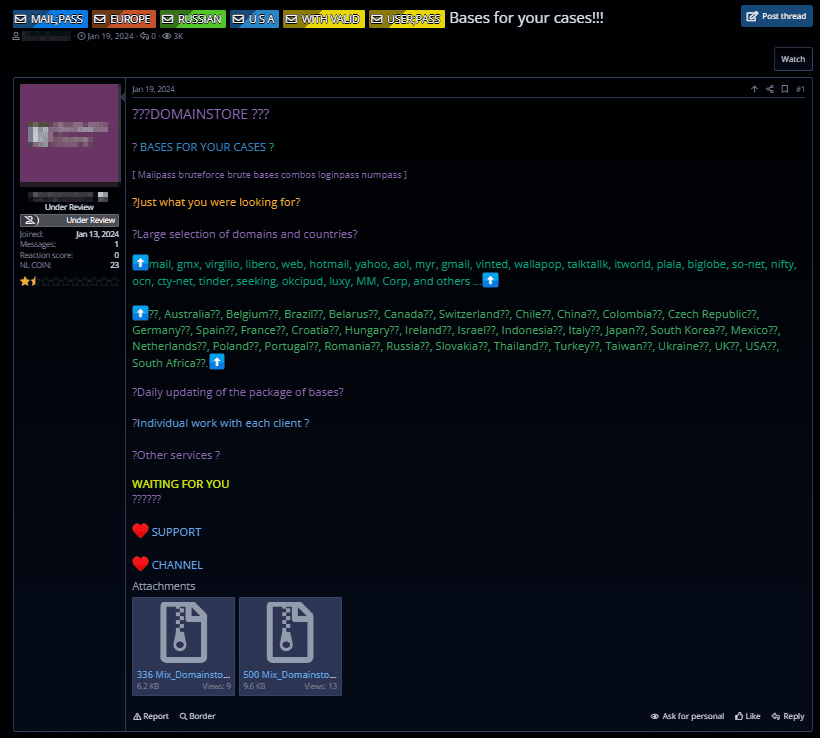
Cybercriminals offer a wide range of data and access credentials for multiple countries. They go beyond simply listing stolen data or credentials they already possess. Many data brokers also offer custom services to locate specific data requested by their clients. This has transformed the shadow market into a fully developed ecosystem, where any stage of a cyberattack can be outsourced to more skilled criminals. Listings on shadow forums are increasingly structured like advertisements designed to meet specific demands:
As a result, the barrier to entry into the cybercrime community is lowering, making it possible for individuals with no technical expertise or specialized knowledge to engage in hacking.
Another global trend of shadow markets observed in Brazil is the division of labor within the cybercriminal community, particularly in the sale of access to corporate infrastructure. Listings offering access (sale or free distribution) to Brazilian organizations account for 12% of all shadow market listings. The shift to a service-based model has increased demand for initial access, with sales (72%) far outnumbering free distributions (18%).
Skilled cybercriminals specialize in obtaining access and selling it to those who need it to carry out attacks. In the dark web, "access" refers to credentials or other means of gaining unauthorized entry into a device or service within a company's infrastructure.
Access is typically obtained through:
Attacks exploiting low digital literacy, such as phishing, brute force, or dictionary attacks targeting weak passwords, as well as malware distributed via email or messaging apps in attachments and links
Exploitation of software vulnerabilities, especially in outdated operating systems that and applications no longer receive security updates
Misconfigurations, such as open ports, insecure protocols, or poor network segmentation
For example, one listing offers access to a Brazilian DNS controller for $3,000. While no specific details about the controller are disclosed, the advertisement mentions that it provides access to user traffic. Such access could enable phishing attacks, account compromise, malware installation, or even unauthorized registration using corporate credentials.
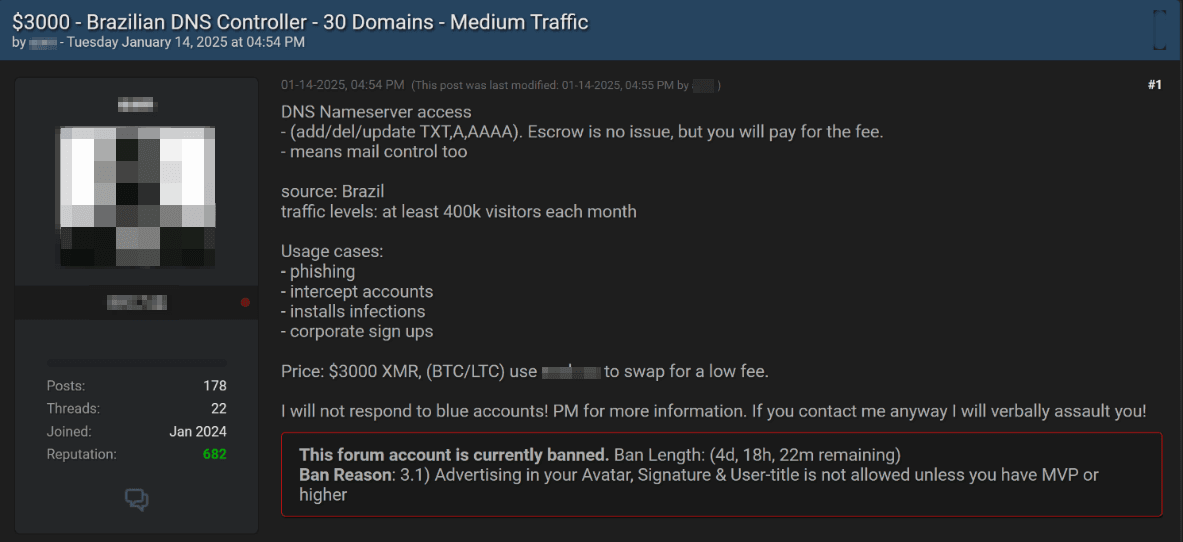
Other listings include access to the infrastructure of large manufacturing, government, and financial institutions. For instance, gaining access to the infrastructure of manufacturing companies could allow attackers to interfere with technological processes, create dangerous situations, or cause system failures.
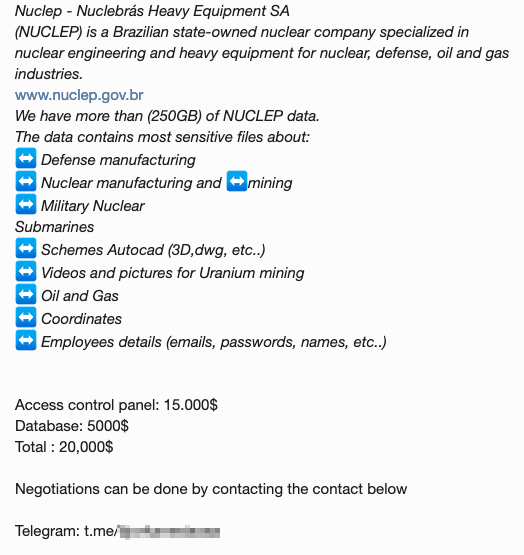
In late 2024, a shadow forum featured a listing offering stolen data and access to the control panel of Nuclep, a Brazilian company specializing in manufacturing and supplying equipment and technology for energy, oil and gas, and defense industries. The stolen data (250 GB) included sensitive information related to military and defense nuclear engineering, submarine blueprints created in AutoCAD, videos and images of uranium extraction, oil and gas exploration details, significant geographic coordinates, and employee information (names, email addresses, passwords, and more). The database was priced at $5,000, while access to the control panel was listed for $15,000. The risks associated with such access include the exposure of classified defense and military information, unauthorized interference with industrial infrastructure — causing it to fail or disrupting its proper operation — and further data compromise through prolonged access.
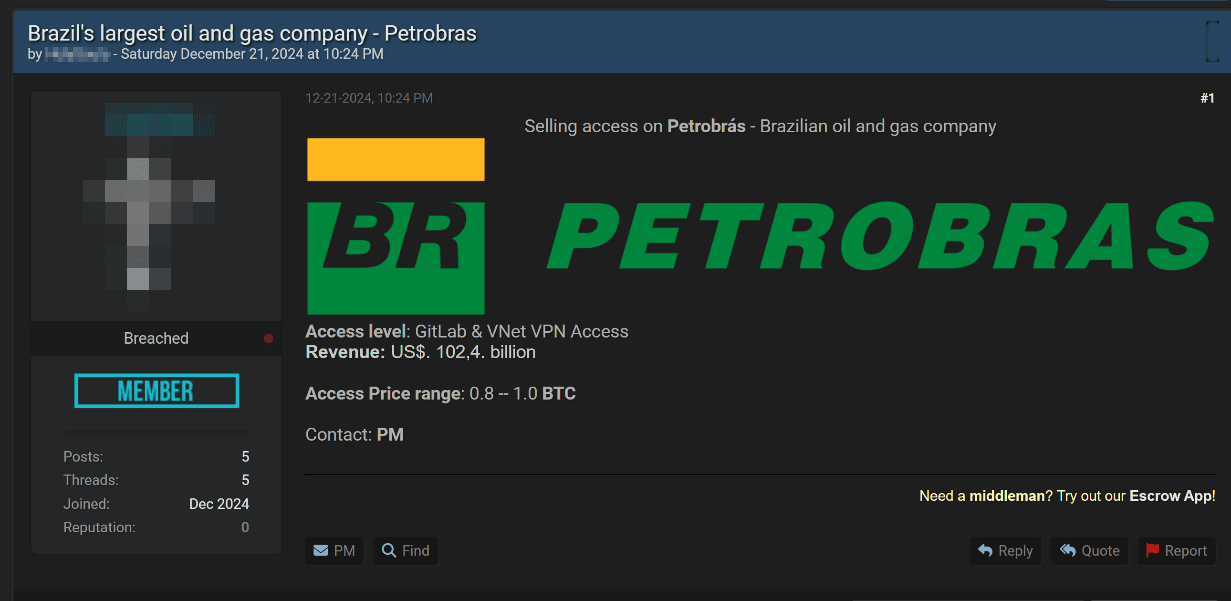
Around the same time, another listing advertised GitLab and VNet VPN access to the infrastructure of Petrobras, Brazil's state-controlled oil and gas company with an annual revenue of $104.2 billion. The price for access ranged from 0.8 BTC to 1 BTC ($83,000–$104,000).
Such access could allow attackers to obtain source code for certain solutions, potentially embedding malicious code, vulnerabilities, or backdoors. It could also expose confidential information and put related companies at risk, as attackers could use the compromised VNet VPN credentials to breach their infrastructure.
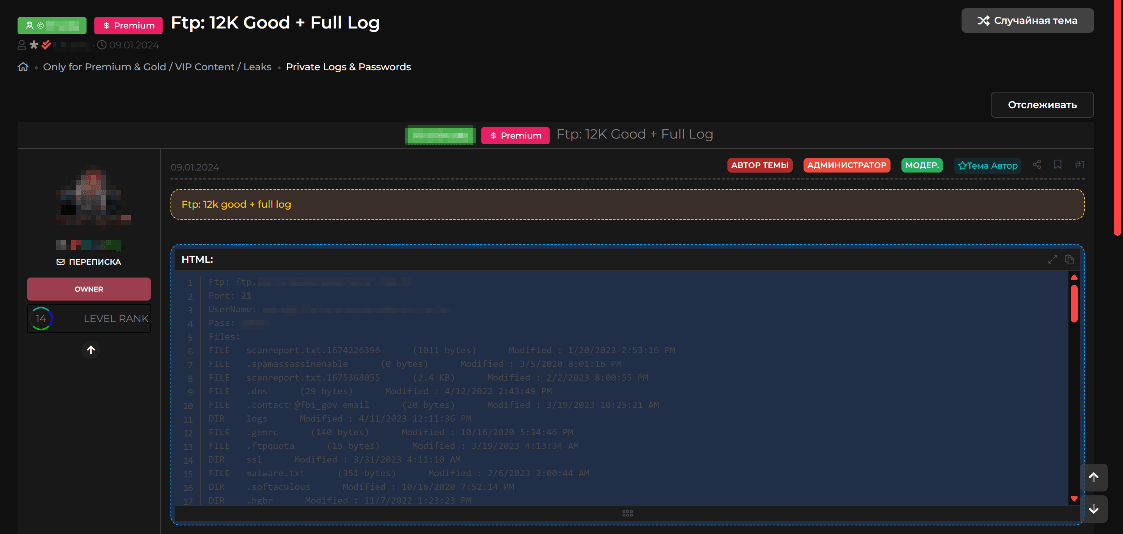
Government, financial, and healthcare institutions store large volumes of sensitive information, making them attractive targets for cybercriminals. Stolen or encrypted data could either be monetized or used for targeted cyberattacks.
For example, the Brazilian rehabilitation clinic Clinica Um Novo Amanhecer, which specializes in treating drug addiction, suffered an FTP access breach. Such access could allow attackers to intercept communication between clients and servers, alter data during transmission, or insert malicious content into files. This could critically impact patient treatment and compromise the confidentiality of their personal data and medical diagnoses.
In some cases, listings do not specify the company to which access was obtained. For instance, one listing offered access (C2, shell, cloud access, and so on) to the infrastructure of one of Brazil's largest companies, operating in finance, electricity, oil and gas, energy, and investments. The seller claimed that the company's infrastructure included 1,400 devices and over 800 employees. The price for this access was $50,000.
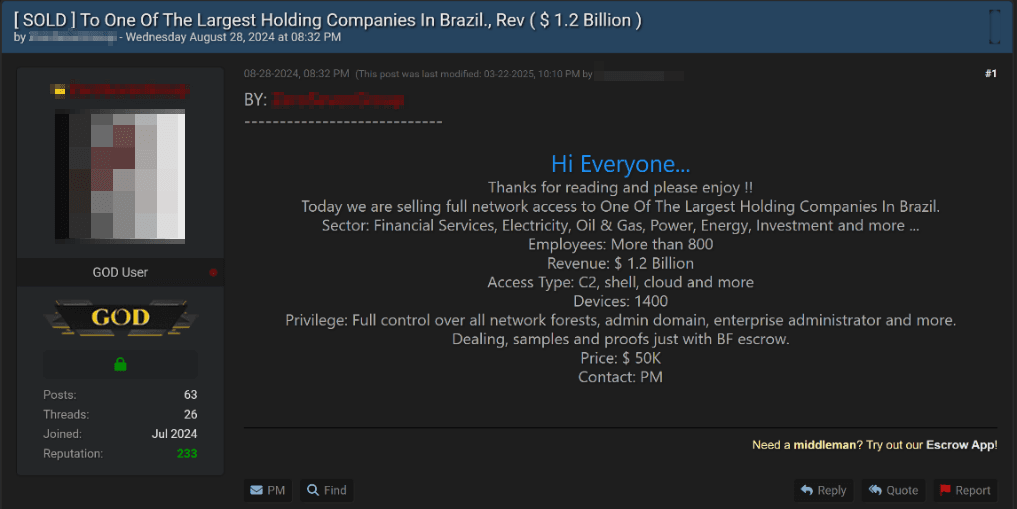
The sale of access is a highly lucrative business, with prices reaching up to $70,000 (depending on the Bitcoin exchange rate).
Free access distribution is far less common, and the data shared tends to be of lower value, often involving low-level access to web panels obtained with minimal effort, such as bruteforcing passwords. If the access holds no value to the attacker or they lack interest in pursuing a cyberattack, they may distribute it for free. Such behavior is common among hacktivists or individuals seeking to build their reputation in the shadow market.
Nearly half of the cyberattacks on Brazil's government systems in 2024, as detected by the Cyber Incident Prevention, Handling and Response Center of Brazilian Government (CTIR Gov), resulted in data breaches. This has led to an increase in shadow forum activity concerning Brazilian government institutions. More than 10% of all reviewed listings pertained to government entities.
The most common consequence of these attacks (43%) was the breach of confidential information, such as databases and credentials. This was followed by disruptions to core operations (33%), including website defacements and DDoS attacks. These findings are consistent with the key consequences of successful cyberattacks across Latin America.
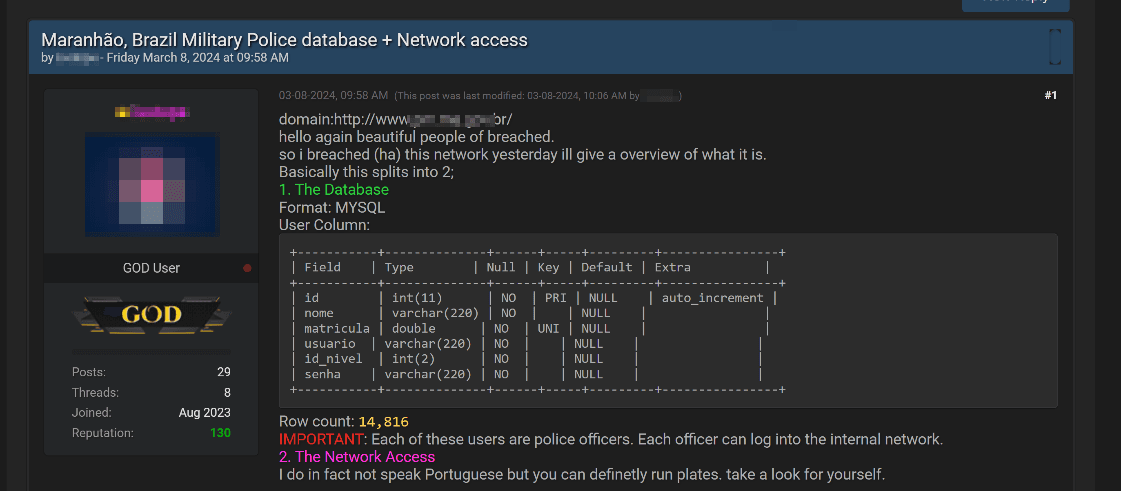
A similar pattern is seen on shadow forums, where listings for the sale or distribution of government-related personal data, documents, or access credentials make up 43% of all such listings. This surpasses the 31% share of listings related to successful defacements of government websites. For example, one listing offered a MySQL database and access to the internal network infrastructure of the military police in Maranhão state. The database reportedly contained 14,186 records, including police officers' names, registration numbers, usernames, passwords, and access levels.
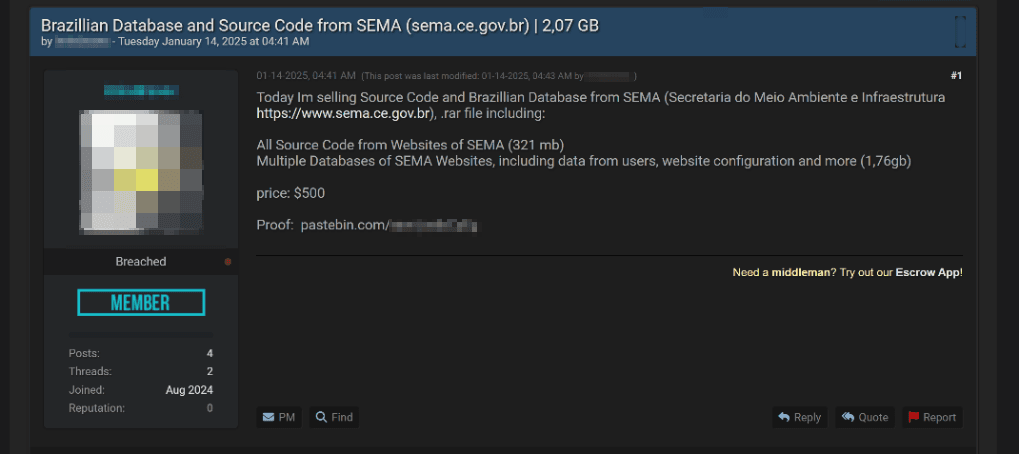
In January 2025, another listing on a shadow forum advertised the sale of a database and source code from the Central Environmental Protection Agency of Brazil (SEMA). The hackers priced the resources at $500. The 1.7 GB database contained user data, website configuration parameters, and other information, with the extracted data totaling 321 MB.
Shadow market listings for government institutions and related entities often include not only stolen data (sale or distribution) but also results of successful cyberattacks, such as website defacements, DDoS attack outcomes, and identified vulnerabilities. This indicates that Brazil's government institutions, like others worldwide, are targeted not only by financially motivated cybercriminals but also by hacktivists and novice cybercriminals seeking to build a reputation in the underground community.
For instance, in late November 2024, a shadow forum listing disclosed an SQL vulnerability on the website of Campinas, a city and municipality in São Paulo state. The author provided a query template to exploit the vulnerability, complete with instructions on where to insert the payload.
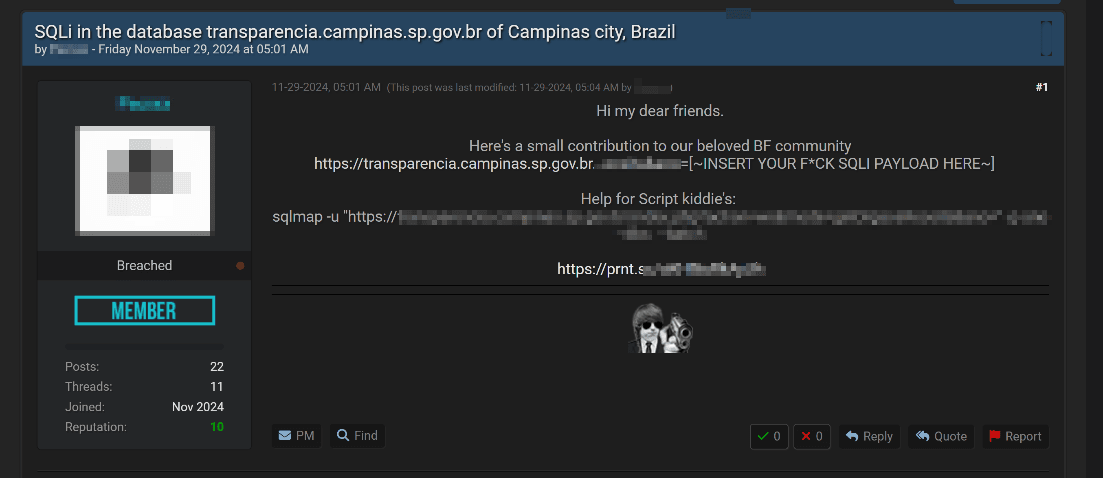
Website defacements have affected various government sites. For example, the website of Brazil's Ministry of Agriculture and Livestock was targeted, emphasizing that such attacks are often less about causing direct harm and more about making statements.
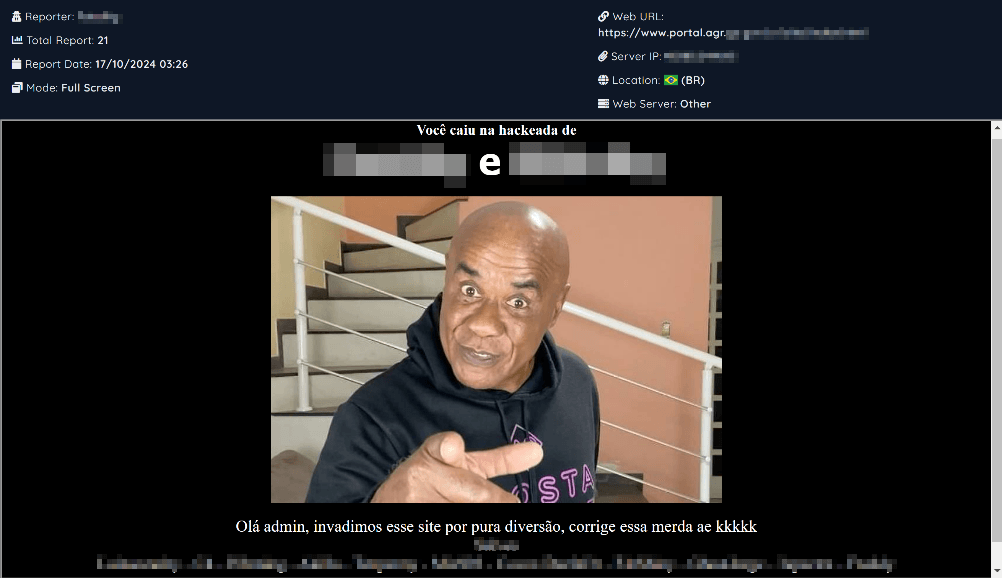
Overall, the analysis of shadow market listings pertaining to Brazilian government institutions reflects the broader trends in Latin America: data breaches and disruptions to core operations correlate with listings for the sale or distribution of databases and announcements about website defacements, DDoS attacks, or vulnerabilities.
The shadow market is filled with ads for the sale or distribution of data, including scanned documents such as passports and driver's licenses, as well as selfies (photos and videos) commonly used for account verification.
These listings may pertain to countries other than Brazil, with selfies frequently accompanying scanned documents. Selfies are widely used to verify user identities, particularly in financial and government services. In many cases, selfies are also used for two-factor authentication.
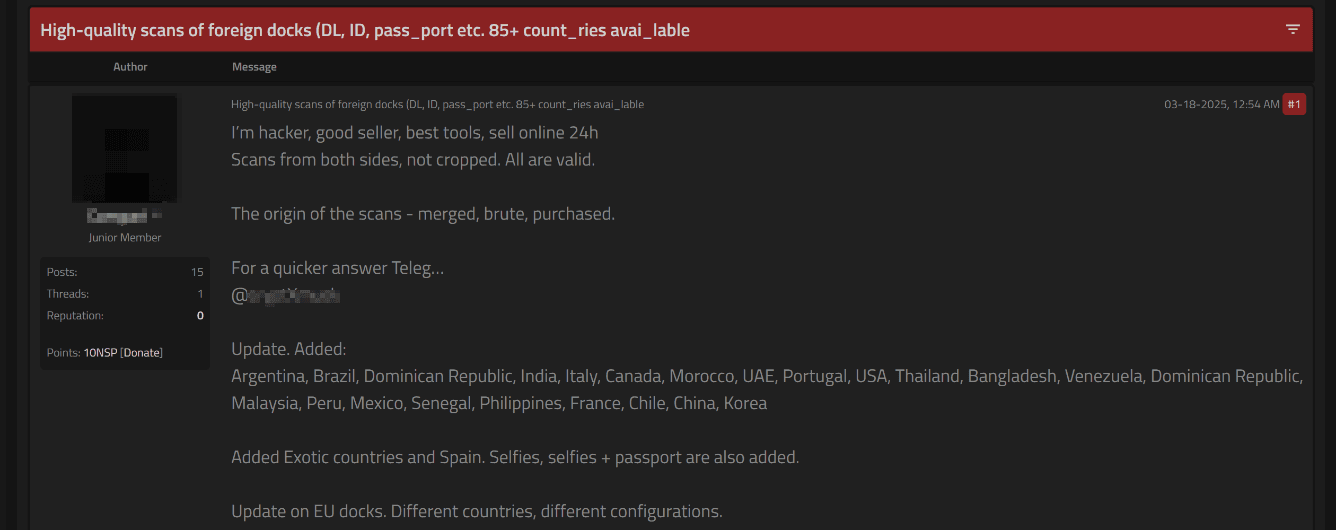
Some listings even feature photos of individuals holding their passports open, which confirms their use for account verification.
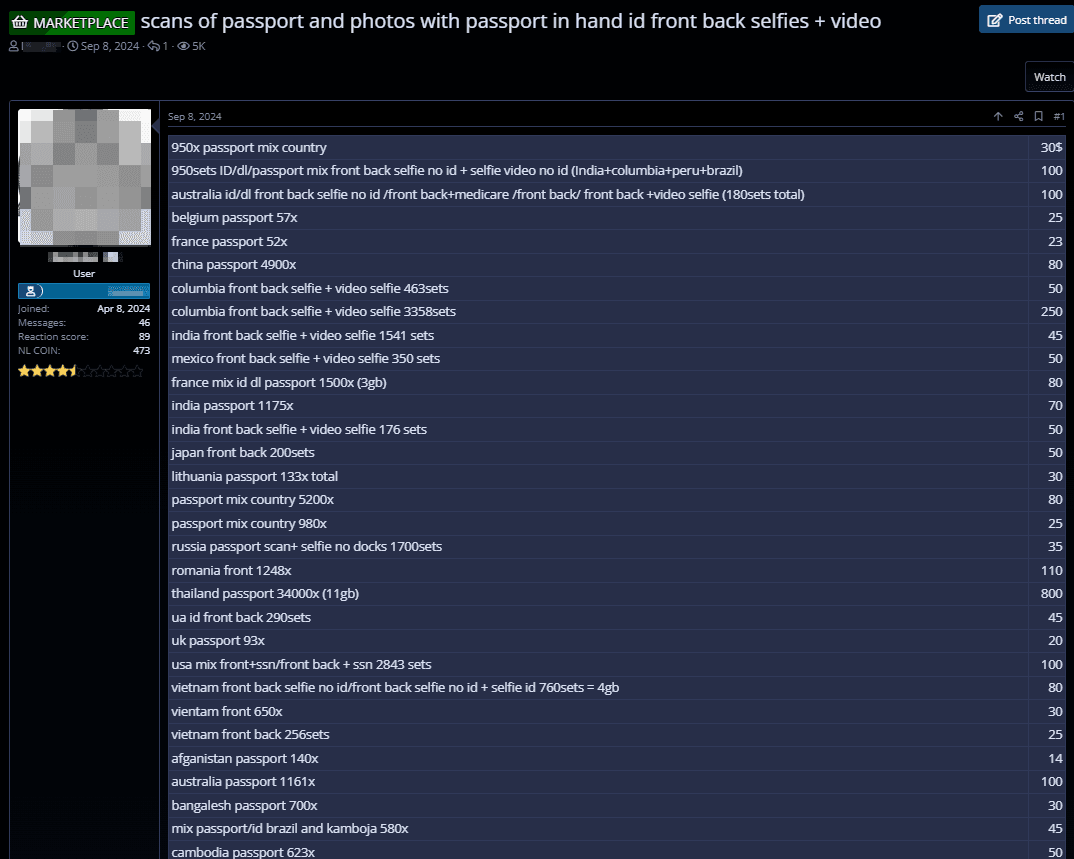
Such data can be exploited in several ways:
Brazil has seen a sharp rise in ransomware cases, with February 2025 setting a record of over 960 ransomware attacks in a single month. What's striking is that even large companies with significant cybersecurity budgets and well-resourced IT teams have fallen victim to these attacks. This highlights the challenges of Brazil's digitalization process as a developing country.
Shadow markets are filled with ads related to ransomware attacks. Among the groups frequently posting about successful attacks, three stand out as the most active:
RansomHub (14% of attacks): a successor to the infamous Knight ransomware group, RansomHub operates as a Ransomware-as-a-Service (RaaS) platform, using a prepaid model for its partners. LockBit3 (13%): known for its innovative and constantly evolving administrative panels and RaaS features, LockBit3 has a wide range of tools and tactics for deploying ransomware. ArcusMedia (6%): this group targets countries like Brazil, the U.S., Colombia, the UK, and Italy, focusing on industries such as software, finance, transportation, and telecommunications.
As seen in shadow market analyses across Latin America from 2023–2024, many listings related to Brazil include announcements of successful attacks on specific companies. This is usually done to capture public attention and showcase the extent of cybercriminal activities.
Subsequently, criminals may post an ad to sell or share the stolen data. For example, ransomware group RansomHouse demanded $6 billion following an attack on Sabesp, Brazil's largest water and waste management company, which serves 26.7 million people (60% of São Paulo state's population). A shutdown of Sabesp's operations had critical consequences for the entire country.
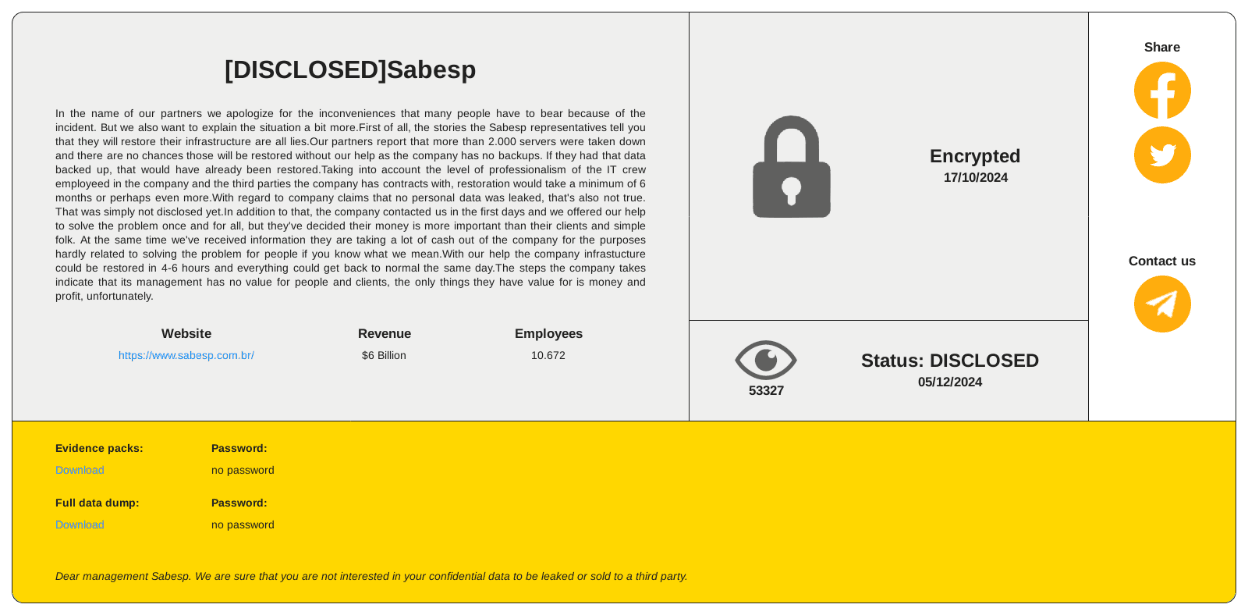
Manufacturing companies are particularly high-value targets because encrypting their data can halt technological processes and production, resulting in massive financial losses.
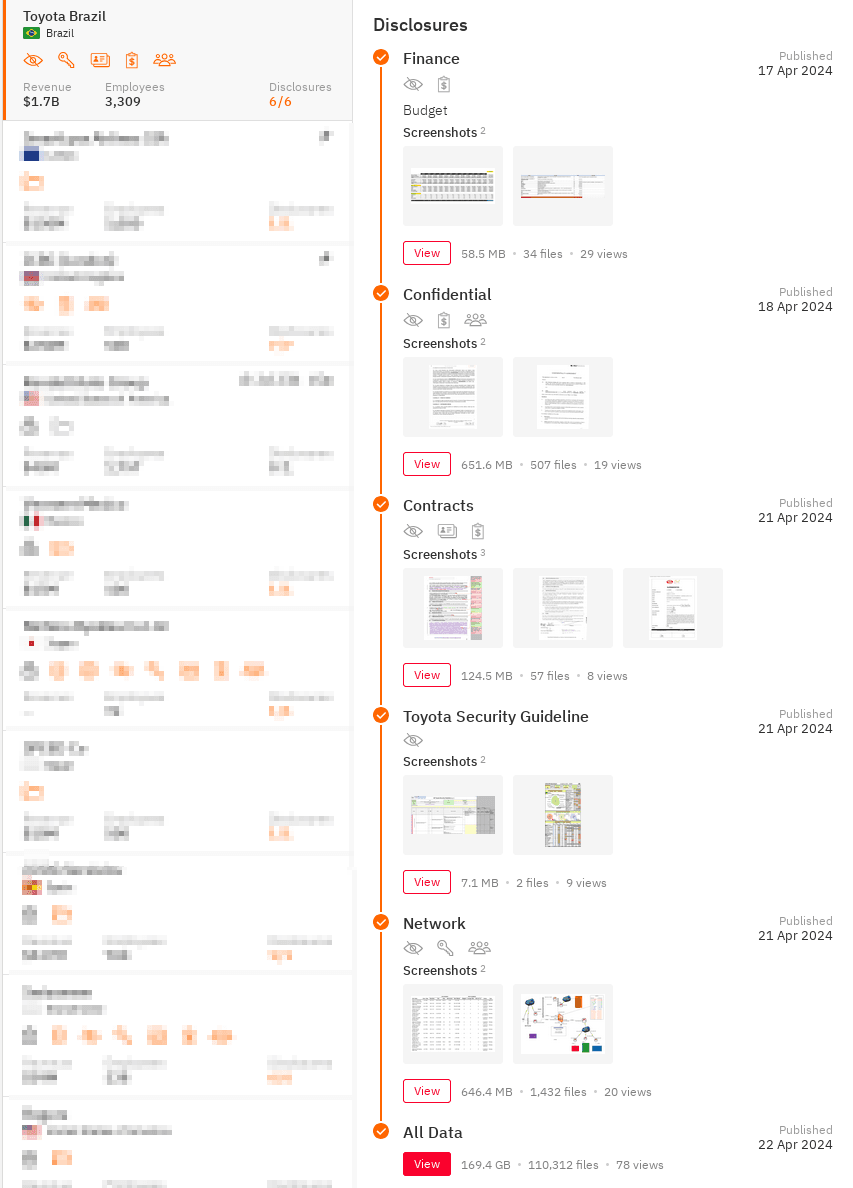
For example, with annual revenue of $1.7 billion, Toyota's Brazilian division was a top target for cybercriminals. As a result of a ransomware attack by the Hunters group, data related to the company's network infrastructure, internal security documents, contracts, financial information, and trade secrets was stolen.
Ransomware continues to be one of the most significant cyberthreats, not only for Brazil and Latin America but globally. For Brazil — a country undergoing rapid digital transformation — ensuring robust protection of its information infrastructure is vital. The current pace of digital adoption far exceeds the country's ability to educate its population on cybersecurity hygiene or train enough skilled professionals to meet the demand.
Brazil's rapid digital transformation highlights a significant contradiction: while the country is accelerating the digitization of all sectors and offering a wide array of digital services — including government, financial, and healthcare — its population's technical skills lag behind those of other nations.
This gap stems from a lack of sufficient regulatory and educational initiatives in cybersecurity. As a result, not only is the general population highly vulnerable to cyberthreats, but the government and businesses also face significant risks, with their digital infrastructure and data inadequately protected against modern cyberattacks. Over the next year, the volume of confidential data breaches in Brazil is unlikely to decrease.
As Brazil's digital landscape evolves, the shadow markets for cybercriminal services are also undergoing transformation. We anticipate the following trends in these markets:
Improving Brazil's cybersecurity landscape requires a coordinated approach, combining organizational, technical, and social measures:
The data and findings presented in this report are based on Positive Technologies own expertise, as well as analysis of publicly available resources, including government and international publications, research papers, and industry reports.
We assume that most cyberattacks are not made public due to reputational risks. As a consequence, even companies specializing in incident investigation and analysis of hacker activity are unable to quantify the precise number of threats. This research aims to draw the attention of companies and individuals who care about the state of information security to the key motives and methods of cyberattacks, and to highlight the main trends in the changing cyberthreat landscape.
This report considers each mass attack (for example, phishing emails sent to multiple addresses) as one incident, not several. For explanations of terms used in this report, please refer to the Positive Technologies glossary.
Our incident database is updated regularly. However, some incidents may be reported online long after the actual attack took place. Therefore, this report is accurate as of the date of publication.