
Beleii Artem
Senior Analyst, International Analytics Group, PT Cyber Analytics

Beleii Artem
Senior Analyst, International Analytics Group, PT Cyber Analytics
The rapid digitalization of Southeast Asia is driving economic growth while also boosting illegal online activities. The widespread adoption of internet technologies, mobile connectivity, and anonymous digital tools has fueled the rise of underground platforms and illicit trade.
This report examines the cybercrime landscape on the dark web in Southeast Asia during the second half of 2024 and the first half of 2025. It focuses on the following countries: Brunei, Cambodia, Indonesia, Laos, Malaysia, Myanmar, Philippines, Singapore, Thailand, and Vietnam.
Study objectives:
The study covers current cyberthreats for 2024–2025, using Positive Technologies' expertise, reports from leading cybersecurity vendors, data from key dark web forums, as well as information from reputable open sources and Telegram channels used by cybercriminal groups and hacktivists.
Over 300 Telegram channels and dark web forums were analyzed, focusing on Southeast Asia. The study covers the period from September 1, 2024, to May 1, 2025.
The research covered forum posts and Telegram messages on the following topics:
This study aims to raise awareness among companies, government organizations, and individuals interested in the current state of cyberthreats on the dark web in Southeast Asia. Definitions of terms used in this report are available in the glossary on the Positive Technologies website.
Our incident database is updated regularly. However, some incidents may be reported online long after the actual attack took place. Therefore, this report is accurate as of the date of publication.
Southeast Asia has experienced a sharp rise in cybercriminal activity in recent years. Research shows that the number of cyberattacks in the region doubled in 2024 compared to 2023.
Why cybercrime in Southeast Asia is growing:
Over 20% of global cyberattacks in 2024 targeted the Asia-Pacific region. The most affected countries include Indonesia, Malaysia, Vietnam, Thailand, the Philippines, and Singapore, with Indonesia and Malaysia ranking highest in incident reports on dark web forums and stolen data marketplaces. High activity levels in these countries highlight both their cybersecurity challenges and the growing interest they attract from cybercriminals.
The primary drivers of increasing cyberthreats in Southeast Asia are rapid digitalization, the growing number of internet users and online services, and geopolitical tensions between certain nations, including their involvement in economic and political alliances. Over the past two years, 67% of reported cybersecurity incidents in Southeast Asia occurred in 2024, driven by the rapid shift of businesses and government services online without adequate cybersecurity measures. This transformation has made the region increasingly attractive to financially motivated attackers.
The region's rapid development has not gone unnoticed by neighboring states, which also have economic interests in Southeast Asia. APT attacks in the region rose by 58% from 2023 to 2024, largely due to cyberespionage and sabotage linked to regional conflicts. A wide variety of cybercriminal groups are targeting Southeast Asia, ranging from those focused on stealing crypto assets[SK1] [AB2] to advanced APT groups conducting cyberespionage.
Local hacktivist groups such as R00TK1T, ETHERSEC TEAM CYBER, and RipperSec have carried out DDoS attacks, defaced government websites, and leaked sensitive data. Their targets include both domestic institutions and foreign organizations tied to geopolitical adversaries. For example, a Telegram post from R00TK1T contained threats of cyberattacks against Malaysian citizens and the government (see screenshot).

Cybercrime in Southeast Asia predominantly targets financial institutions and government agencies. According to Positive Technologies, 92% of attacks in the region focus on organizations, while just 8% affect individuals. The most impacted sectors are manufacturing (20% of attacks), the public sector (19%), and financial institutions (13%). Attack trends differ by country. In Indonesia, financial services and online retail were the primary targets, while in Malaysia, the banking sector was hit hardest. Government agencies across the region are also frequently targeted. Data from dark web forums shows that in 2024, government entities were the most mentioned victims in posts related to Southeast Asia (12.4%). Over the last six months, the situation has shifted slightly: while government agencies remain among the top targets (13.1%), financial services (18.5%) and education (14.7%) have taken the lead in mentions on dark web forums.
Two-thirds of cyberattacks in the region result in the theft of sensitive data. Personal data (34% of dark web posts) and commercial information (26%) are the most targeted.
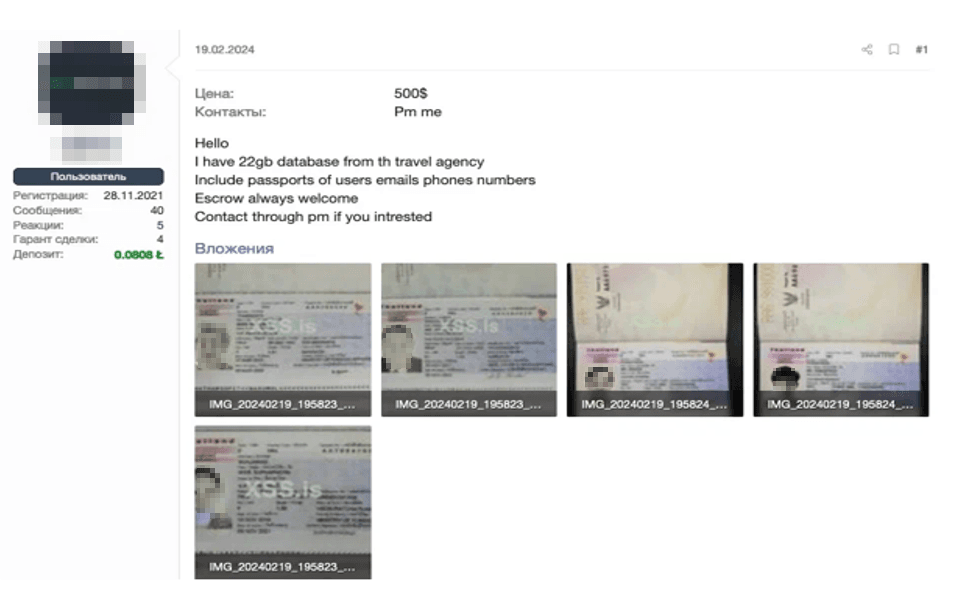
Cybercriminals are mainly financially motivated, profiting from the sale of stolen data, fraud, or blackmail. Dark web listings often advertise stolen user data, including personal details, photos, scanned documents, and screenshots. For instance, data from a breached Thai travel agency was offered for sale, complete with document scans (see Figure 7 below). Some listings, however, are not for profit—hackers or hacktivists sometimes distribute stolen databases for free, making them accessible to other malicious actors.
The cybercrime ecosystem in Southeast Asia is a dynamic network of illegal goods and services. Dark web marketplaces operate like legitimate e-commerce platforms, offering network access, phishing tools, and exploits. These platforms feature rating systems, transaction guarantees, and even technical support.
The demand for illegal digital assets remains high due to the increasing digitization of businesses. RDP access, VPN credentials, and administrator accounts are particularly sought after and frequently used in attacks. Analysis of pricing, seller geography, and product specialization shows that cybercriminal markets adapt to threats faster than many security defenses. Advanced Persistent Threat (APT) groups, in particular, clearly demonstrate this adaptability, as demonstrated by recent attacks. Companies struggled to adapt their defenses to the evolving tools of cybercriminals, while multilayered, targeted attacks disrupted the operations of some cybersecurity departments.
Understanding the structure and dynamics of these markets is essential for developing effective cybersecurity strategies, predicting threats, and identifying vulnerabilities in organizational infrastructures.
Key dark web segments in Southeast Asia:
Analysis of these segments revealed that they are closely interconnected, forming a cohesive cybercriminal ecosystem both within and beyond dark web forums.
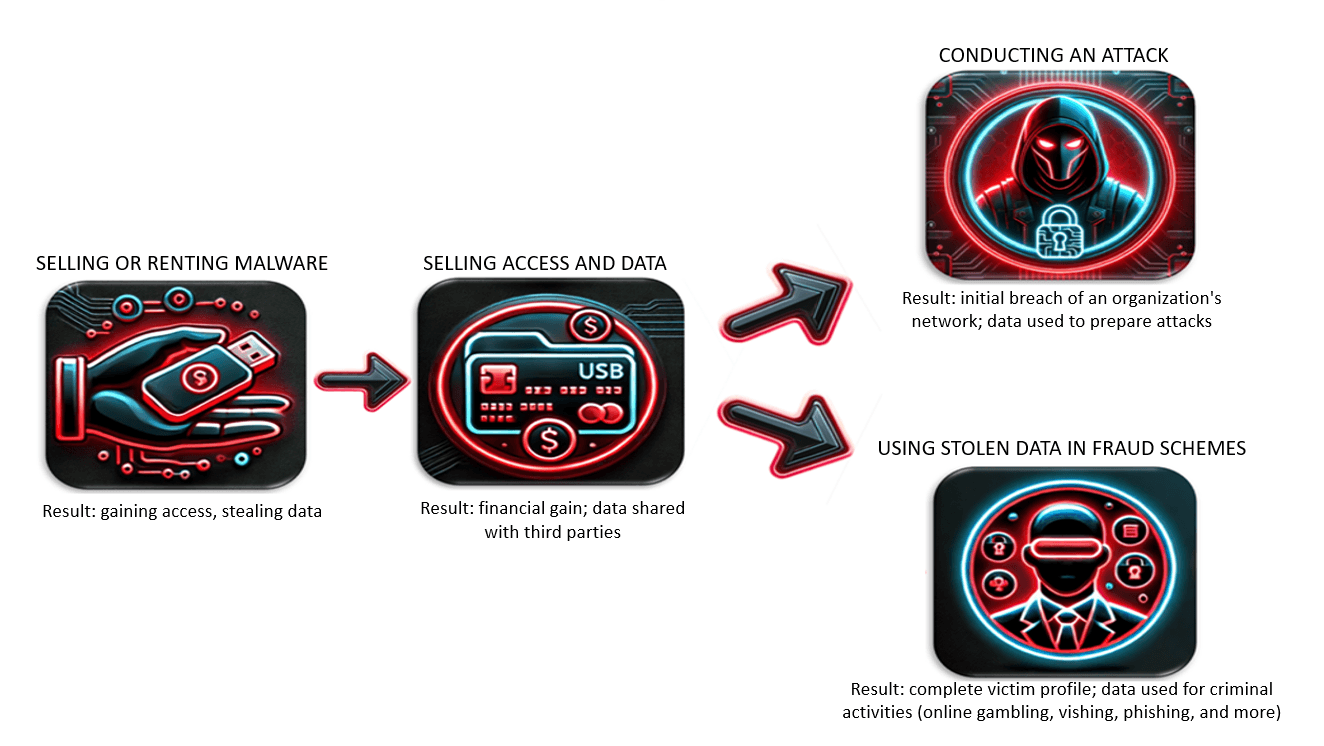
Each segment has a direct or indirect role in advancing the cybercriminal supply chain of illegally acquiring, selling, and exploiting confidential information.
Below is an analysis of each segment, detailing the frequency and scale of incidents, approximate pricing, key platforms, as well as profiles of actors and emerging threats.
The sale and distribution of malware on the dark web is global, with cybercriminals in Southeast Asia typically using the same forums and marketplaces as their counterparts worldwide. The region has not seen any notable cases of locally developed malware for sale. While major APT groups active in Southeast Asia may create their own tools for attacks, these are rarely offered on public forums. Instead, independent cybercriminals heavily rely on widely available tools, with infostealers and banking trojans being the most common, targeting credentials and financial data.
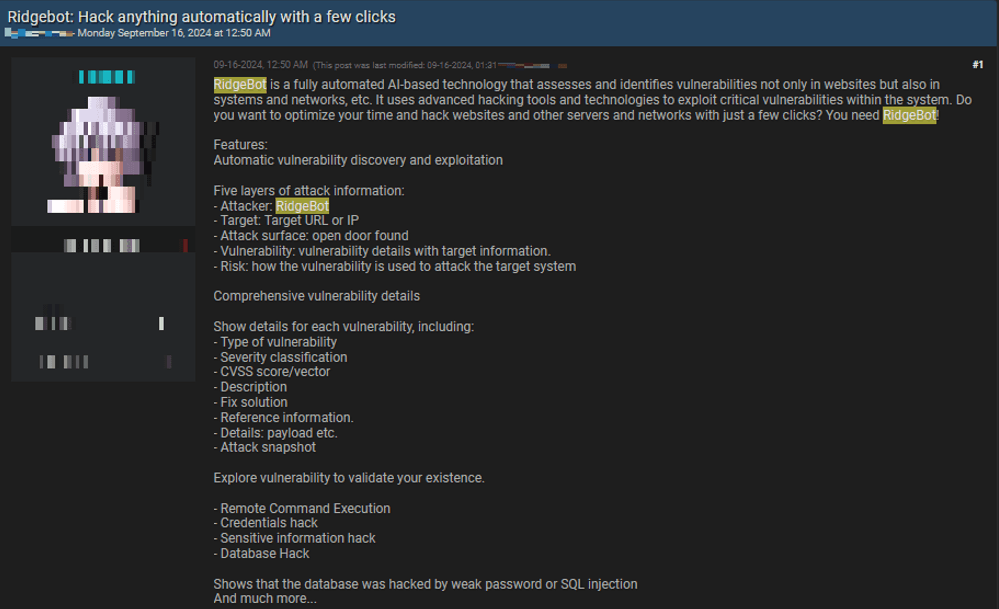
Dark web advertisements often feature malicious software for sale, such as malware source codes, ransomware variants, and exploit kits. For example, an ad for selling RidgeBot malware includes a detailed description of its functionality (see Figure 9 below). However, most transactions in this segment are service-based (Malware-as-a-Service, or MaaS), offering services like malware deployment, botnet rentals, and more. According to Positive Technologies, malware-related posts on Southeast Asian underground forums are relatively rare, with stolen data and access sales dominating. Access credentials, often obtained through malware, are then sold as standalone products.
The Figure below shows the percentage distribution of mentions of the most popular malware tools in forum posts. The most frequently used infostealers in the region are RedLine, META, and Raccoon.
1. RedLine
Type: infostealer
2. META Stealer
Type: infostealer
3. Raccoon Stealer
Type: infostealer
4. XClient Stealer
Type: infostealer
5. NodeStealer
Type: infostealer
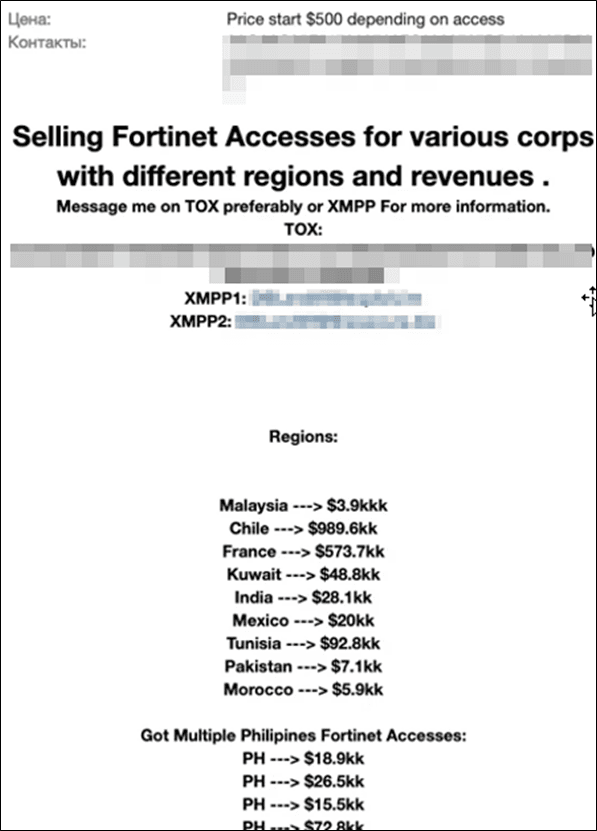
Infostealers and remote access trojans (RATs) are widely used in cyberattacks across Southeast Asia. These tools enable the theft of employee credentials, leading to further compromise of corporate resources. Cybercriminals in the region typically focus on using widely available malware rather than developing unique local tools. As a result, malware often serves as a means to an end, with stolen data and access credentials being sold on forums. The distribution of malware campaigns in Southeast Asia is diverse. Alongside global cybercriminal groups operating internationally, local groups often target neighboring countries. Such activities are often classified as APT attacks but remain deeply tied to the dark web ecosystem. For example, stolen cryptocurrency is laundered through mixers—services that obscure illegal cryptocurrency transactions by blending them with legitimate ones. Similarly, compromised accounts and access credentials are sold on underground markets, often through large initial access brokers who offer such listings worldwide. One such broker, for instance, provides a wide selection of countries to choose from, with a particular focus on the Philippines.
Malware in Southeast Asia's dark web ecosystem serves as a foundation for other types of cybercrime. The effective use of infostealers and RATs directly contributes to data leaks and access sales. In the following sections, we will examine these two interconnected segments in greater detail.
Another significant segment of Southeast Asia's underground forums is the market for access and associated cybercriminal services. In 2024, about 14% of corporate network access listings for sale globally were tied to the Asia-Pacific region. These listings include access to compromised accounts and systems, offers to hack specific targets for a fee, botnet rentals for DDoS attacks, phishing services, and more. In recent years, Initial Access Brokers (IABs) have played a pivotal role in the cybercrime ecosystem. These brokers breach organizations or exploit stolen credentials, then sell access (doe example, accounts, VPN and RDP credentials, or web shells) to other cybercriminals on forums.
The buyers are typically financially motivated groups or ransomware operators seeking to infiltrate victims' networks. Research shows that in 2024, at least 96 active access brokers were selling credentials to compromised organizations worldwide. On certain local forums in Southeast Asia, hackers offer services like email account breaches, social media hacks, and attacks on competitors. These services are often paid for in local currencies. However, for major cybercriminal operations, these platforms are secondary. Most transactions occur on international forums, where payments are made in cryptocurrency.
Listings on dark web forums offer nearly every type of access originating from Southeast Asia, including:
In many cases, access is sold to companies located in Indonesia, Malaysia, Vietnam, and Thailand.
During the analyzed period, RDP access was the most commonly advertised type of access on the dark web, overtaking VPN access, which had previously been dominant during a similar period. Interestingly, domain email accounts in Vietnam nearly entered the top three, reflecting a growing focus of attackers on multipurpose accounts linked to numerous services.
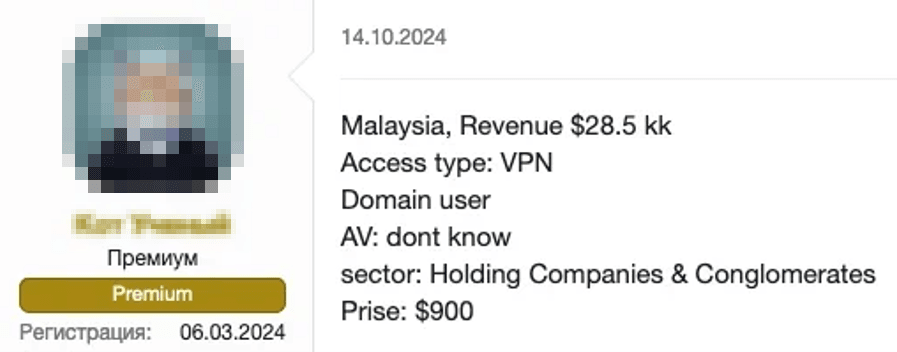
The sale of access primarily takes place on specialized English-language forums—many of which are closed to new users—or within private chat groups. Brokers list items such as: "VPN access to Company X (Malaysia), domain admin, price $2,000." One listing featured VPN access to a small unknown Malaysian company (see Figure 13 below).
Another listing on the same forum offered administrator-level access to an Indonesian financial organization with annual revenues exceeding $80 million. The criminals provided GlobalProtect client access, and the cost of the listing was notably low compared to the company's revenue. Since attackers often use a company's revenue to determine ransom demands, the potential profit from the attack would far exceed its initial cost.
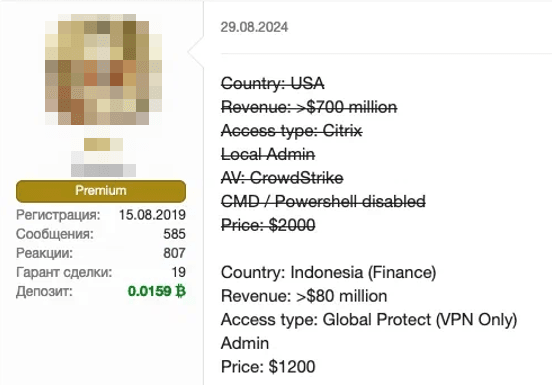
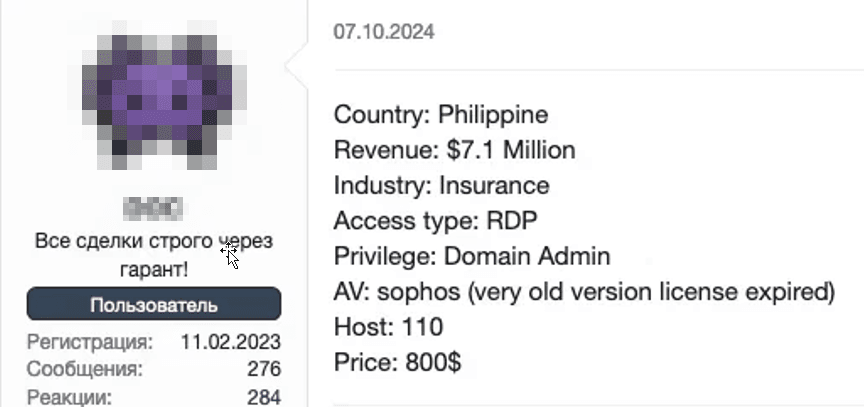
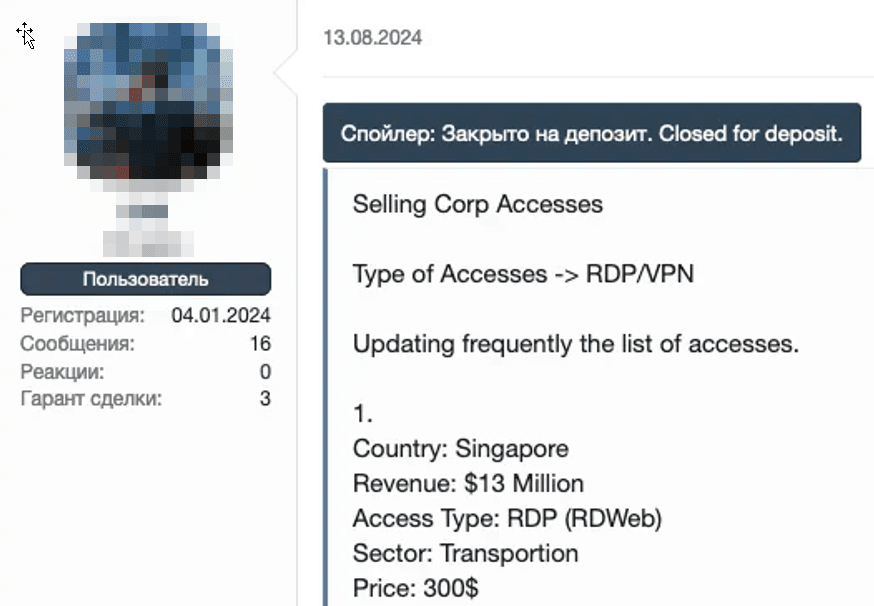
Listings offering RDP and VPN access span all sectors and vary widely in price. Sellers often include additional details about the compromised systems and sometimes offer multiple types of access simultaneously. The listing below sells RDP access to a Philippine insurance company, noting that the system was running outdated antivirus software with an expired license. This highlights how some companies in the region fail to update their software and security systems (see Figure 15). Another listing featured RDP and VPN access to the network of a Singaporean transportation company (see Figure 16).
Dark web forums are used by local hackers, hacktivists, and APT groups interested in purchasing access to systems. The connection between local cybercriminals and prominent APT groups is often simple: local actors obtain initial access and sell it to interested parties. In analyzed listings, frequent mentions were made of groups such as APT32, Lazarus, APT41, DarkHydrus, and Kimsuky, all of which are active in Southeast Asia.
Another trend is the hiring of hackers for targeted attacks. On local forums in Malaysia and Indonesia, listings such as "Will hack an account, price negotiable" are common. However, more sophisticated operations, such as industrial espionage, are usually conducted through closed channels or intermediaries. These services indicate the rise of hacker-for-hire teams in the region. Often, these are former cybersecurity professionals who have turned to illegal activities. Their expertise makes them harder to track, but the results of their work are evident—whether in the form of rare data appearing on the dark web or highly targeted attacks that remain undisclosed because they were commissioned and the stolen information was not publicly released.
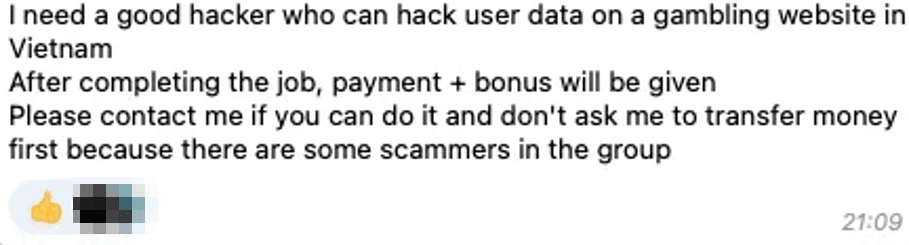
In 2025, the number of access listings is expected to grow further. Dozens of cases have already been recorded in the first quarter. For Indonesia, the Philippines, and Malaysia, which lead in the number of incidents, this means that more local companies' data is likely to become merchandise on underground markets, and the demand in this market continues to grow.
The analysis of statistics and current trends allows for the following predictions in the near future:
Without stronger defenses and international cooperation, Southeast Asia will remain a hotspot for cybercrime. The region's share of global cyberattacks is likely to exceed 25%, meaning one in four attacks worldwide will target Southeast Asia.
Southeast Asia is one of the world's most targeted regions for cybercrime. Based on the statistics above, Indonesia and Malaysia are at the forefront of this trend, frequently suffering from data breaches, ransomware, and cyberespionage. The region's threat landscape has several characteristics:
Current threats and trends: data breaches in the financial and government sectors will continue to grow. Financial institutions and government agencies remain prime targets, with incidents often hushed up, delaying detection. New breaches are likely to coincide with major events—elections, referendums, and summits—where leaked data could influence politics. Commercially, oversaturation may drive down the value of leaked data, such as repeatedly exposed Indonesian ID cards. As a result, hackers may shift focus to niche categories like medical records (including health histories and vaccination data) or biometric databases (such as fingerprints and passport photos). These types of data are already appearing on the dark web and are highly valued due to their rarity and potential for harm.
Organizations operating in Indonesia, Malaysia, and other Southeast Asian countries must implement comprehensive security measures. Below are practical recommendations tailored to the region's specific cyberthreat landscape:
Ensure sensitive data is encrypted during storage and transmission.
Deploy data loss prevention (DLP) systems.
Limit employee access to data on a need-to-know basis.
Regularly review access rights and disable unused accounts.
Use multifactor authentication (MFA) for all external logins and critical internal systems.
3. Reinforce network perimeters and update infrastructure. Conduct audits of publicly accessible services (websites, VPN gateways, email servers) to identify known vulnerabilities. Disable or secure outdated protocols. Pay special attention to updating network boundary devices, such as routers and firewalls. Use network segmentation to isolate critical services from the office network and external access.
4. Be prepared for ransomware attacks. In addition to preventing infiltration, have a response plan in case of encryption:
Regularly back up critical data and store backups in isolated environments.
Monitor ransomware trends and patch vulnerabilities commonly exploited by attackers.
5. Train employees in cybersecurity practices. With phishing and social engineering being common attack vectors, train staff to recognize suspicious emails, messages, and calls.
6. Establish an incident response plan and notification protocol. Prepare a protocol for responding to data breaches, including whom to notify (regulators, customers) and when.
7. Collaborate with external experts and share information. Join industry cybersecurity alliances and share indicators of compromise (IOCs). Many attacks follow similar patterns, so learning from others in your industry can help close vulnerabilities in advance. INTERPOL and CERT ASEAN operate in the region—stay in touch with them for the latest warnings and updates.
8. Deploy advanced technologies:
Implement IDS/IPS and a SIEM system to detect traffic anomalies.
Use endpoint detection and response (EDR) tools to identify malware on endpoints, especially given the rise of infostealers.
Enforce mandatory multifactor authentication for customers using online services.
9. Secure supply chains. Assess the cybersecurity of contractors, particularly those with access to your systems or data. Include cybersecurity requirements in contracts. Attacks via less secure partners are a real threat, as evidenced by recent cases.
10. Integrate cybersecurity into business processes. Company leaders must treat cyberrisks as key business risks. Develop a corporate cybersecurity policy and conduct a cyberrisk assessment to analyze the financial impact of potential attacks. Preventive investments in security are much cheaper than covering the damages caused by incidents.
Nearly every organization in Southeast Asia is a target for cybercriminals. Thorough preparation, proactive dark web monitoring, and rapid response are the foundation of effective cybersecurity. Implementing these recommendations can significantly reduce risks and protect both your company and your customers' data from ending up on the dark web.