Contents
- Executive summary
- Growth of attacks amid the pandemic
- Pitfalls of remote working
- Sophisticated malware hiding techniques
- Ransomware attacks: million-dollar losses
- Supply chain attacks: hit to stock price and damage to reputation
- Medicine: first victims among patients and return to pen and paper
- Industrial sector: actuation of risks at critical facilities
- About the research
Executive summary
2020 year in review
- The number of unique incidents grew by 51 percent compared to 2019. Seven out of ten attacks were targeted. Medical and government institutions were the most tempting targets for attackers.
- Hacking as an attack method against organizations showed an upward trend throughout the year. The total increase was 24 percentage points (10 percentage points more than in 2019). On the dark web, access-for-sale schemes became increasingly popular, with a surge of interest in website hacking. All this can be explained by the mass shift of companies to working from home.
- The number of malware attacks grows every year. 2020 saw an increase in such attacks by 54 percent compared to 2019. Malware developers devised elaborate methods for concealing their malicious actions and refined malware delivery techniques, turning their attention to vulnerabilities on the network perimeter. Attacks against individuals were mainly performed using spyware and banking trojans, whereas organizations were increasingly attacked by ransomware.
- Ransomware was used in 45 percent of all malware-related attacks on organizations. Instead of performing mass attacks, ransomware operators started to deliberately choose their targets. They also increased the ransom amounts, created new websites for publishing stolen data for sale, and started using DDoS attacks to blackmail victims.
- The number of industrial incidents increased by 91 percent compared to 2019. In most cases, attackers used ransomware. The share of hacking as an attack method grew by 2.6 times in comparison to 2019. There were attacks against critical infrastructures that led to power outage, as well as attempts to disrupt water supply systems.
- Medical institutions are in first place by number of ransomware attacks and third by total number of attacks in 2020. As a result of some attacks, medical systems went down and patients were denied emergency care.
- The year was further marked by supply chain attacks. The most high-profile incidents happened to Blackbaud and SolarWinds. As a result of these attacks, Blackbaud faced 23 consumer class actions, and SolarWinds' stock took a dip.
To protect against cyberattacks, we advise following our recommendations for personal and corporate cybersecurity. In light of recent attacks aimed at exploiting vulnerabilities in IT infrastructure, we urge companies to pay attention to protecting their network perimeter, install patches without delay, and adopt an automated vulnerability management process. Companies should also deploy modern security tools, including web application firewalls, network traffic analysis, and SIEM. To prevent attacks related to delivery of malware by email, we recommend checking attachments in a sandbox, a special virtual environment designed for analyzing file behavior. To create an efficient security system, it is vital to adopt a risk-oriented approach and test the feasibility of unacceptable business risks. The optimal solution involves testing risks on a cyber-range, where it is possible to model attacks without causing harm to real infrastructure.
Growth of attacks amid the pandemic
In 2020, the number of incidents rose by 51 percent compared to 2019, and 86 percent of all attacks were aimed at organizations. Criminals seemed to be more interested in government and medical institutions, as well as industrial companies.
70 percent of attacks were targeted
14% of attacks are directed against individuals

Pitfalls of remote working
The COVID-19 pandemic forced companies to shift to home working and push their internal services to the network perimeter, changing the cyberthreat landscape all around the world. Only a handful of companies already accustomed to remote working were in a position to tackle all security challenges; the rest had precious little time to think through and implement appropriate protection measures.
Attackers immediately started looking for vulnerabilities on corporate perimeters, including in solutions for remote working, probing their robustness. For example, vulnerabilities in Pulse Secure VPN, Citrix ADC, Citrix Gateway, and Cisco ASA firewall were actively exploited. The Netwalker, Clop, and REvil ransomware operators used the vulnerable services to deliver their malware. On the whole, the share of hacking as an attack method on organizations increased by 10 percentage points against 2019, reaching 24 percent.
In at least 4 percent of attacks leveraging vulnerabilities in software on the network perimeter, hackers exploited the CVE-2019-19781 vulnerability in Citrix ADC and Citrix Gateway, which allowed bypassing authentication mechanisms and executing arbitrary code. In our 2019 report, we anticipated an increase in the number of incidents involving this vulnerability, but many companies ignored our warning and did not install updates.

The equally dangerous CVE-2019-11510 vulnerability in the VPN solution from Pulse Secure was often exploited in 2020. The vulnerability allowed an unauthenticated user to get user logins and passwords in cleartext. For example, it was used in an attack to steal credentials for more than 900 servers of various companies. Hackers shared all the stolen data on the dark web.
Most frequently exploited vulnerabilities in 2020:
- CVE-2019-19781 (Citrix ADC и Citrix Gateway)
- CVE-2017-11882 (Microsoft Office)
- CVE-2019-11510 (Pulse Secure VPN)
- CVE-2020-11651 and CVE-2020-11652 (SaltStack Salt)
- CVE-2020-14882 (Oracle WebLogic)
- CVE-2019-0708 (RDP)
Since Q2 2020, we have observed an increase in the number of attacks aimed at stealing corporate credentials of employees. To achieve this goal, attackers hacked web resources to steal databases with credentials, faked authentication forms, delivered spyware in corporate networks, and bruteforced passwords to connect to services on the network perimeter. In August, for instance, fraudsters sent victims links to legitimate documents uploaded to a fake website imitating the Google Cloud Platform interface. To view the document, victims had to log in with their Microsoft Office 365 corporate credentials.
Another important trend of 2020 was the growing popularity of the access-for-sale model, targeting companies' servers. Even if hackers have yet to develop an attack further than exploiting a vulnerability and obtaining server access, they can easily sell this access on a dark web forum. As a result, not only a company's IT infrastructure can suffer, but also its website, which is its corporate face to the world. Since March 2020, we have noticed a surge of interest in website hacking. We believe the reason for this is 2020's global switch to remote working.
Sophisticated malware hiding techniques
The number of malware incidents grew by 54 percent compared to 2019. For the last two years, ransomware has remained the leader among all malicious software used in attacks against organizations. In attacks against individuals, spyware and banking trojans were the primary culprits.
In attacks on organizations, the main vectors for delivering malware remain email (71%) and compromise of computers, servers, and network equipment (24%); in attacks on individuals, hackers prefer using email and websites (32% each).
In 2020, attackers got more sophisticated in hiding their actions, and malware often had functions for concealing the infection and further operation. If previously all hackers had to do was hide from antivirus software, today, thanks to a general increase in companies' security awareness, cybercriminals also have to bypass sandboxes. At the very least, this entails scanning the runtime environment. Malware developers are constantly refining methods for evading protection and can even use multiple methods in one product. According to our research, sandbox evasion techniques were most frequently found in remote access tools and loaders.
The Zeppelin ransomware implemented a simple technique for hiding from static analysis in a sandbox: for some time after infection, it stops its malicious activity. Malware posing as a plugin for Autodesk 3ds Max checked whether Task Manager or Performance Monitor applications were running on the victim's computer. Attackers also made active use of obfuscation to complicate code analysis for automatic tools and infosec experts.
Ransomware attacks: million-dollar losses
From quarter to quarter in 2020, we saw steady growth in ransomware attacks against organizations. At the end of Q4, it turned out that more than half of malware attacks involved ransomware.
Most active ransomware (2020)
- Netwalker
- REvil
- Maze
- Ryuk+Conti
- DoppelPaymer
Scrupulous choice of victims
In 2020, ransomware operators truly excelled themselves. In line with the 2019 trend of shifting from mass campaigns to targeted attacks, they became more discriminate in their choice of victims. The factors of choice included the company's financial state, the importance of the industry, and the potential consequences of the attack for the victim.
Medical and government institutions (17% and 16%, respectively), as well as industrial companies (15%), bore the brunt of ransomware attacks.
Data theft and double ransoms
At the end of 2019, we recorded some isolated cases of ransomware attacks aimed at stealing data and encrypting infrastructure. In 2020, the strategy of demanding a double ransom for decrypting data and keeping stolen information private became a real trend. The reason for this is that infosec experts started to rely on backup systems to resist such attacks. Companies that use backup systems did not have to pay hackers for a decryptor, thus alleviating consequences of attacks. This approach did not sit well with attackers, which is why throughout 2020 they created new ransomware websites (for example, Ranzy Locker, Avaddon, and Mount Locker), where they published stolen information whose owners had refused to pay a ransom to get it back.
New ways of manipulation
Ransomware operators not only blackmailed victims with threats to disclose the stolen data, but also performed DDoS attacks in case victims refused to pay or negotiate. Some also formed new alliances with other gangs, trying to profit by their affiliation with criminals higher up the pecking order.
Insatiable appetites
What really struck us was how much hackers demanded as a ransom. According to CrowdStrike, the average ransom sum in 2020 reached $1.1 million. The sad truth is that attackers have good reason to ask for yet bigger sums, as many companies agree to pay for restoring encrypted data, as did, for example, the University of California, San Francisco ($1.14 million), a Canadian insurance company ($1 million), and U.S.-based travel management firm Carlson Wagonlit Travel ($4.5 million).
Service downtime and huge recovery costs
The consequences of ransomware attacks can be sweeping, including both financial and reputational losses. Sometimes, services can be disrupted for more than several days. A notable example is the attack on Garmin in Q3 2020. Even if a company immediately detects and stops an incident, losses can reach up to millions of dollars, as happened with IT services provider Cognizant, which estimated the damage in the range of $50 million to $70 million, and Sopra Steria, which suffered losses of between €40 million and €50 million.
Supply chain attacks: hit to stock price and damage to reputation
Supply chain attacks caught the attention of the entire IT world in 2020. Such attacks target a less protected company to access its customers. The consequences are far-reaching and mainly include reputational loss and customer outflow, as well as financial damage from fines by regulatory bodies and compensation to clients.
The most high-profile incidents happened to Blackbaud and SolarWinds. In a ransomware attack on cloud services provider Blackbaud in May, hackers absconded with data belonging to the company's clients. The company paid a ransom and hoped that the malefactors would not use the stolen information; however, trusting the hackers proved wishful thinking. One after another, Blackbaud's clients started to report data compromise. Blackbaud made the mistake of not notifying its clients of the data theft and not reporting the attack to the regulatory authorities. Only in mid-July did the company finally acknowledge the attack. The victims included charities, non-profits, educational institutions, foundations, and universities from the U.S., Canada, the UK, and the Netherlands. As a result of the attack, Blackbaud was named as a defendant in 23 consumer class actions alleging harm from the incident.
The damage in the December attack on SolarWinds was far more significant. The incident affected government, educational, medical, consulting, technology, and telecom entities in the U.S., Europe, Asia, and the Middle East. After the attack became public, SolarWinds' shares tumbled 40%, and the stock price has yet to recover. Worryingly, attackers managed to steal penetration testing tools from cybersecurity firm FireEye. The stolen software will likely be leveraged in future campaigns.
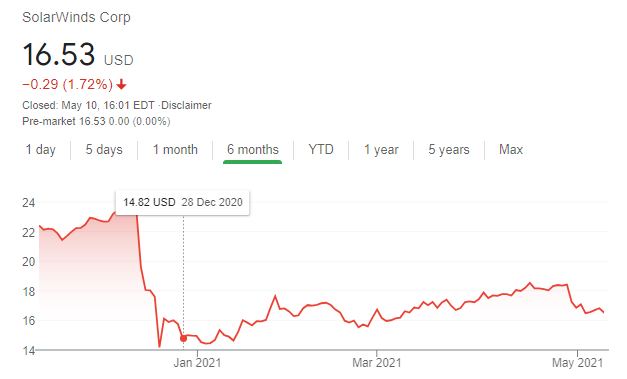
Other supply chain attacks hit software and hardware providers of medical institutions and developers of software for financial companies.
Medicine: first victims among patients and return to pen and paper
In 2020, the number of attacks on medical institutions grew by 91 percent compared to 2019. The share of attacks on healthcare accounted for 9 percent of all security incidents. Amid the COVID-19 pandemic and overloaded health systems worldwide, hackers added fuel to the fire by disrupting the availability of medical information systems. Following several attacks on hospitals, France allocated €1 billion to strengthen the country's cyberdefenses. Of all the attacks in 2020 in France, 11 percent were on hospitals.
In most cases, cybercriminals used social engineering (66%) and hacking (21%) as attack methods. Malware was used in 68 percent of attacks. Ransomware was used in 81 percent of malware-related attacks.
The consequences of ransomware attacks can be devastating. In 2020, the total damage caused by ransomware attacks against medical institutions in the U.S. was put at $20.8 billion. In this field, it is not only financial consequences that matter, but also failure to offer medical assistance, as happened with Universal Health Services and the University of Vermont Medical Center. UHS employees could not access patients' prescriptions and analysis results, read diagnostic data, and provide urgent medical care, as all the necessary data was stored electronically and encrypted by the attackers. At the University of Vermont Medical Center, clinicians had to recreate chemotherapy protocols from memory, as the system recovery required time that the patients did not have. Sometimes, when a hospital cannot provide urgent medical care, patients need to be diverted to other clinics, which may have tragic consequences, as happened in Düsseldorf, Germany.
Hackers targeted not only clinics on the front line in the fight against the pandemic, but also companies involved in the production and supply of vaccines, including laboratories, logistics and pharmaceutical firms (Fareva and Dr. Reddy's), as well as the European Medicines Agency (EMA), which approves COVID-19 vaccines.
Industrial sector: actuation of risks at critical facilities
The number of attacks against industrial companies almost doubled compared to 2019 (an increase of 91 percent).
In most cases, industrial companies were attacked by ransomware operators, such as RansomExx, Netwalker, Clop, Maze, Ragnar Locker, LockBit, DoppelPaymer, and Snake. An important characteristic of the Snake ransomware is that it deletes shadow copies before starting the encryption process and has functions for stopping ICS-related processes. Huber+Suhner and Honda had to halt work as a result of cyberattacks.
The share of financially motivated attacks in this field increased to 36 percent due to the growing popularity of ransomware (26 percentage points more than in 2019). Hacking as an attack method was used 2.6 times more often than in 2019.
Industrial companies were also attacked by many APT groups. TinyScouts, a new group that targets energy companies in Russia, was discovered in Q3. CIS countries still suffer from attacks by the RTM group: in 2020, the PT Expert Security Center detected over 100 phishing emails sent by this group.
Actuation of risks in the industrial sector can lead to global consequences. In a cyberattack on water infrastructure in Israel, hackers planned to modify chlorine levels in water supplies to civilians, which could have led to mass poisoning. In India, a power outage caused by a cyberattack disrupted the stock exchange, hospitals, and transportation system in several cities.
Predicting the feasibility of the most dangerous risks and estimating their consequences is difficult, as even the most experienced specialists cannot guarantee that all protection mechanisms will work faultlessly. Penetration tests are not enough to provide a sufficient assessment of current risks, because real infrastructures cannot be disrupted during such tests. To simulate an attack without affecting real-life systems, a cyber-range can be used. This provides a safe environment where experts can get the fullest possible picture of whether certain risks can be triggered (for example, oil storage overflow), protection mechanisms will respond in time, and infosec teams will timely detect and stop an incident.
About the research
In this annual report, Positive Technologies shares information on the most important and emerging IT security threats. Information is drawn from our own expertise, outcomes of numerous investigations, and data from authoritative sources.
In our view, the majority of cyberattacks are not made public due to reputational risks. The result is that even organizations that investigate incidents and analyze activity by hacker groups are unable to perform a precise count. This research is conducted in order to draw the attention of companies and ordinary individuals who care about the state of information security to the key motives and methods of cyberattacks, as well as to highlight the main trends in the changing cyberthreat landscape.
In this report, each mass attack (for example, when attackers send a phishing email to multiple addresses) is counted as a single incident. Terms used in this report are defined in the glossary on the Positive Technologies site.
Get in touch
will contact you shortly