In Q1 2020, we registered 22.5 percent more attacks than in Q4 2019. The beginning of the year was tough on the whole world. The COVID-19 pandemic messed up the global economy and the life of all ordinary people. The situation impacted the information security, too. About 13 percent of all phishing emails of Q1 2020 were related to COVID-19. Of those, about a half (44%) targeted individuals. One out of every five mailings was sent to government agencies.
Contents
Executive summary
Highlights of Q1 2020 include:
- The number of cyberincidents is growing rapidly. In Q1 2020, we detected 22.5 percent more attacks than in Q4 2019.
- The share of targeted attacks remains unchanged from Q4 2019 (67%).
- In Q1 2020, there were 23 very active APT groups. Their attacks targeted mostly government agencies, industry, finance, and medical institutions.
- About 13 percent of all phishing emails of Q1 2020 were related to COVID-19. Of those, about a half (44%) targeted individuals. One out of every five mailings was sent to government agencies.
- More than a third (34%) of all attacks on organizations using malware were attacks with ransomware. Sodinokibi, Maze, and DoppelPaymer were the most active ones. Operators of these and some other ransomware created their own websites where they publish stolen data if the victims refuse to pay the ransom.
- The share of attacks against individuals was 14 percent. Logins and passwords make up half of the data stolen. This is because malware campaigns against individuals contained a large percentage of spyware (56%).
We expect that the number of attacks against remote workstations will be growing globally. Because people are working from home now, companies may soon see an increased number of attempts to hack corporate credentials or exploit vulnerabilities in remote access systems. These threats are especially relevant for companies that have no strict password policy and no regular software updates.
Web application firewalls (WAFs) can block potential attacks against web applications on the network perimeter, including attacks against remote access systems, such as Citrix Gateway. To prevent infection of computers of the employees with malware, we recommend checking email attachments for malicious activity with sandboxes. We also recommend following the general recommendations for ensuring personal and corporate cybersecurity.
Statistics
In Q1 2020, we registered 22.5 percent more attacks than in Q4 2019. The beginning of the year was tough on the whole world. The COVID-19 pandemic messed up the global economy and the life of all ordinary people. The situation impacted the information security, too.
cyberattacks than in Q4 2019



are targeted
target individuals




Hiding from the antivirus: аttacks with malware
Over time, malware infection risks keep increasing. Cybercriminals don't stop at using a single type of malware. They use multifunctional trojans or inject compromised devices with a whole bunch of assorted malware. Hackers keep looking for ways to bypass antiviruses and security tools embedded in the OS. For instance, since early 2020 we keep seeing attempts to use the new vulnerability CVE-2020-0601 in Windows CryptoAPI for signing malware. This vulnerability allows bypassing certificate checks. Another example is SysUpdate remote access trojan. This is a unique tool developed by BronzeUnion APT group. The hackers use it to deliver payload to the devices under their control. Usually this payload is not detected by antiviruses, because the file has an indefinite format and the antivirus can't recognize it. Another example is FakeChmMsi, a malware with a complex chain for delivering the Gh0st trojan. Along the chain, DLL hijacking is used twice, complicating analysis of the malware by any antivirus. Modern malware can bypass antiviruses, firewalls, IPS, mail and web gateways, but it can be efficiently countered with sandboxes. Those are solutions allowing one to launch a file in an isolated virtual environment and analyze it for malicious activity.
The greatest number of malware attacks on corporate infrastructure came from ransomware. Individuals were mostly attacked with infostealers, keyloggers, and banking trojans.

Same as before, eight out of ten malware campaigns against organizations started with emails with attachments. Individuals risk getting their computers infected not only via emails, but also by visiting sites and downloading software from untrusted resources. For instance, in Q1 the hackers have compromised a number of WordPress sites and redirected the visitors to phishing sites spreading a backdoor disguised as a Chrome browser update. The malware was downloaded over 2,000 times.

Phishing emails about COVID-19
The hackers were quick to use the common concern about the new coronavirus for their phishing emails. According to our estimates, in Q1 2020 about 13 percent of social engineering attacks were related to the coronavirus.

Starting from the second half of January, we see an increase in the number of phishing emails related to COVID-19. The pandemic situation was used both for mass malware campaigns and for APT attacks. In Q1, Emotet, Remcos, AZORult, Agent Tesla, LokiBot, TrickBot, and many other trojans were distributed in the guise of official information about infection statistics, a vaccine, and prevention measures, allegedly coming from the authorities and medical institutions.
In February, Positive Technologies Expert Security Center (PT ESC) detected an attack from TA428 group. As a decoy, the group sent out a document with coronavirus infection statistics. By the way, in January that group used the deteriorating relations between U.S. and Iran as the topic for their emails. Malicious documents delivered a loader with encrypted Poison IVY shell code to the victim's computer.
In March, PT ESC registered four sets of phishing emails the hackers used to distribute the Chinoxy backdoor. In one of the documents, the attackers used a text related to saving the budget during the coronavirus pandemic.

Groups like TA505, Hades, Mustang Panda, APT36, Higaisa, and SongXY also sent out emails with malicious attachments related to the pandemic. We will discuss the last two in more detail in the section about attacks on government agencies.
The virus intervenes
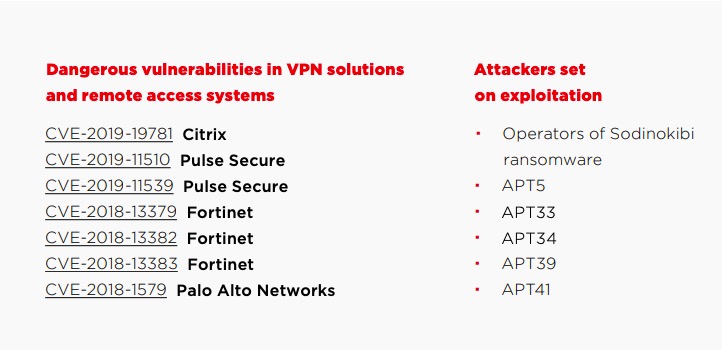
Due to the pandemic, many countries sent schoolchildren and students to study from home, and employers were instructed to send their personnel to work from home, if they could. In this situation, many companies have to use VPN to arrange remote access to their corporate network for their employees. As you know, lately the attackers have been actively exploiting vulnerabilities in VPN solutions and remote access systems, such as products by Pulse Secure, Fortinet, Palo Alto, and Citrix. We recommend immediately installing the latest updates released by those manufacturers. Otherwise, the risk of compromise is quite high. For instance, the British company called Finastra fell victim to ransomware in March because they used unpatched versions of Citrix ADC and VPN by Pulse Secure.
Because of the large number of people shifting to home office, there are now more hosts accessible for RDP connection. We expect that companies all over the world will see an increase in attacks on RDP starting in Q2 2020. For instance, the famous banking trojan TrickBot already got a new module called rdpScanDll which bruteforces credentials for RDP connection.
When more people started using Zoom videoconferencing, the hackers started paying closer attention to it, too. Over 1,700 phishing domains related to the name of the popular platform were registered in Q1 2020. Active use of Zoom app revealed a number of vulnerabilities. Specialists from Check Point discovered that the platform had a vulnerability allowing the attackers to join someone's video conference without an invite. Unsanctioned breach of Zoom online conferences was dubbed Zoom-bombing. According to the FBI, a lot of such incidents occur in the US. Recordings of thousands of video calls ended up on YouTube and Vimeo. Private calls, recordings of business meetings, doctors' sessions, and classes were made public. In addition, at the end of Q1 news came about a UNC path injection vulnerability allowing the hackers to steal Windows credentials via Zoom.
With quarantine and self-imposed isolation, there is an increased demand for takeout food and food products delivery services. The hackers used this to stage a DDoS attack against takeaway.com, demanding 2 bitcoins for stopping it. Attackers also interfered with the work of medical institutions. We will discuss these attacks later, in the Industry Specific section.
Citrix vulnerability put to use
In Q1 2020, 12 percent of malware was delivered to the companies by compromising network equipment, servers, or workstations. One of the vulnerabilities currently used to deliver malware is a vulnerability in some Citrix products (CVE-2019-19781). The vulnerability became widely known back in the end of 2019. It is a critical vulnerability allowing an unauthorized attacker to run arbitrary code. The vulnerability affected about 80,000 organizations worldwide, with most of the victims in the state sector. The manufacturer released final patches on January 24, 2020.
In Q1 2020, the APT41 group used this vulnerability in targeted attacks against government agencies, finance, telecom, industry, healthcare, and the media. In addition, vulnerability CVE-2019- 19781 was presumably exploited during attacks against the infrastructure of Potsdam and the Defence Signals Directorate in Australia.
In January, specialists from FireEye found that unknown perpetrators install a backdoor named NOTROBIN on vulnerable Citrix devices. Curiously, NOTROBIN can detect and block attempted exploitation of CVE-2019-19781 by other attackers, making sure its owners are the only ones in control of the compromised device.
Ransomware with a new blackmail strategy
In Q1 2020, there was an increase in ransomware attacks where the hackers demanded ransom for not disclosing the stolen data. The hackers now create their own sites where they publish the stolen data. Operators of Maze, Sodinokibi, Nemty, DoppelPaymer, Nefilim, CLOP, and Sekhmet already have their sites.

Operators of Sodinokibi are looking for new leverage over the compromised organizations. The hackers plan to notify the stock exchange about attacks on large companies if the latter refuse to pay the ransom. The attackers believe that the possibility of the victim's stock prices going down might be an additional reason to pay the ransom.

Industry specific
In this section, attacks on industries of special interest in Q1 2020 will be considered in greater detail.
Government


The percentage of malware and social engineering attacks against government agencies has increased significantly compared to Q4 2019. The pandemic may have been a factor. Many attackers sent emails to government agencies of various countries, with a malicious attachment related to the coronavirus infection. In January 2020, PT ESC registered two attacks by SongXY APT group. The attackers used a text in Mongolian, which very likely indicates that they target a specific region. The text contained information about COVID-19 outbreak in China. The RTF document with exploit for vulnerability CVE-2018-0798 saved an encrypted loader to the victim's hard drive, decrypted it, launched it, and then loaded the main payload.

In Q1 2020, PT ESC detected two attacks by the Higaisa group. That group attacks government agencies, diplomatic missions, and organizations promoting human rights in China, North Korea, Japan, Nepal, Singapore, Russia, and other countries. Both campaigns started with phishing emails. The first one used a text about national holidays and current news in North Korea. In the second case, the group disguised the malicious LNK file as a PDF document about COVID-19.

PT ESC also detected 14 attacks of Gamaredon group, targeting government agencies of Ukraine and Georgia. As usual, the group used template injection, a technique we discussed at the end of last year. This technique allows the hackers to deliver the malicious macro codes, which executes a VBScript (VBS). Starting mid-February, the group uses obfuscation to protect VBS from detection. The method of gaining a foothold on the infrastructure changed, too. The VBS now creates the RUN key in the Windows registry, ensuring it keeps functioning after reboot.

Industrial companies
Malware infection is still a valid threat for the industry. The greatest threats are spyware and ransomware. They made 42 percent and 28 percent of all malware attacks on industry, respectively. In Q1 2020, we saw attacks on industry with Maze, Sodinokibi, Ryuk, and DoppelPaymer ransomware.


At the beginning of the year, many cybersecurity experts turned their attention to the new ransomware called Snake, capable of deleting shadow copies and stopping processes related to ICS operation. For instance, Snake can stop the processes of GE Proficy and GE Fanuc Licensing, Honeywell HMIWeb, FLEXNet Licensing Service, Sentinel HASP License Manager, and ThingWorx Industrial Connectivity Suite. The attackers presumably want to use Snake in targeted attacks against industry. The ransomware leaves a file on the compromises computer, instructing the victim what to do next, with bapcocrypt@ctemplar[.]com set as contact email. PT ESC theorized this may be a reference to the attack on Bapco company. At the end of 2019, it was attacked with Dustman malware designed to delete data. It is possible that Dustman and Snake are related, because the samples of the two became available to the public at about the same time, and both targeted industry.
Just like government agencies, industry is targeted by many APT groups worldwide. For instance, one of the APT attacks by Bisonal group in Q1 2020 targeted Russian aerospace organizations. PT ESC determined that in that particular attack, the remote control malware (RAT) was delivered by emails with malicious RTF documents as attachments. The group created those documents using the Royal Road exploit builder.

In Russia and the CIS countries, the industry is still attacked by RTM group. PT ESC detected 29 malicious mailings by the group during the first quarter.

Healthcare
The number of attacks on healthcare has increased significantly compared to Q4 2019. This is because the cybercriminals took an increased interest in healthcare facilities currently on the front lines of coping with the coronavirus pandemic. With stress and heavy workload on the medical staff, we see more successful attacks, because the healthcare workers may not be so careful about the stream of emails they receive now.



In 78 percent of attacks on healthcare, the hackers used social engineering. Attackers would send phishing emails to convince the staff to enter corporate credentials in a fake authentication form.
Malware infection threat is just as real. In the early hours of March 13, a cyberattack by unknown perpetrators crashed the network of a large medical center in Brno (Czech Republic) testing people for coronavirus infection. A day later, Hammersmith Medicines Research, a British company preparing to test a coronavirus vaccine, was attacked by Maze ransomware. Remember that the hackers behind the Maze attacks were among the first to demand a ransom for not disclosing the data stolen before encryption. That time, the victim refused to pay and restored their system quickly. A few days later, Maze operators promised to stop attacking healthcare institutions during the pandemic. However, after that promise was made, they published the data stolen from Hammersmith Medicines Research. This proves yet again that one can never trust cybercriminals. Their promises do not guarantee that the stolen data will be recovered and that it will not end up on the Net.

About the research
In this quarter's report, Positive Technologies shares information on the most important and emerging IT security threats. Information is drawn from our own expertise, outcomes of numerous investigations, and data from authoritative sources.
In our view, the majority of cyberattacks are not made public due to reputational risks. The result is that even organizations that investigate incidents and analyze activity by hacker groups are unable to perform a precise count. This research is conducted in order to draw the attention of companies and ordinary individuals who care about the state of information security to the key motives and methods of cyberattacks, as well as to highlight the main trends in the changing cyberthreat landscape.
In this report, every mass attack (where the attackers send out a phishing email to many addresses, for instance) was considered as one incident. Terms used in this report:
A cyberthreat is a combination of factors and circumstances that create the risk of information security compromise. We look at cyberthreats in terms of the actions of malefactors in cyberspace who attempt to breach an information system in order to steal money or data, or with other intentions potentially causing harm to government, business, or individuals. Attacker actions may be directed against the target company's IT infrastructure, workstations, mobile devices, other equipment, or at people as a factor in cyberspace.
A cyberattack consists of unauthorized actions targeting information systems and their users by cybercriminals leveraging techniques and software to obtain access to information, impair the normal functioning or availability of systems, or to steal, alter, or delete information.
A mass attack is a cyberattack against a wide range of companies or individuals. In a mass attack, attackers may not restrict themselves to a single industry, or may even ignore the industries of their targets entirely—their objective is to compromise as many victims as they can.
A targeted attack is a cyberattack targeting a specific company, a certain industry, or a limited number of individuals. A targeted attack usually involves reconnaissance to gather information about the target.
An APT attack (advanced persistent threat attack) is a well-organized and wellplanned multistage targeted attack. APT attacks are performed by criminal groups (APT groups) consisting of highly skilled people. Because of this, APT groups have significant financial resources and technical capabilities.
An attack target is the target of unauthorized actions by cybercriminals. For instance, this could be web resources, computers, servers, network equipment, mobile devices, or the IoT. People can be an attack target too, if the attackers use social engineering.
Attack methods are the set of techniques used by attackers to achieve their goal.
Hacking means exploitation of vulnerabilities and security flaws to gain access to resources or information. For greater granularity, some hacking methods have been placed in separate categories. For instance, bruteforcing credentials to accessible services is considered separately from exploitation of vulnerabilities in web applications.